A Method of Mining Vulnerabilities of Industrial Control Network Protocols Based on Counter Samples
An industrial control network and vulnerability mining technology, applied in transmission systems, electrical components, etc., can solve problems such as high redundancy and inefficiency, and achieve the effect of improving vulnerability mining capabilities and capturing exceptions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
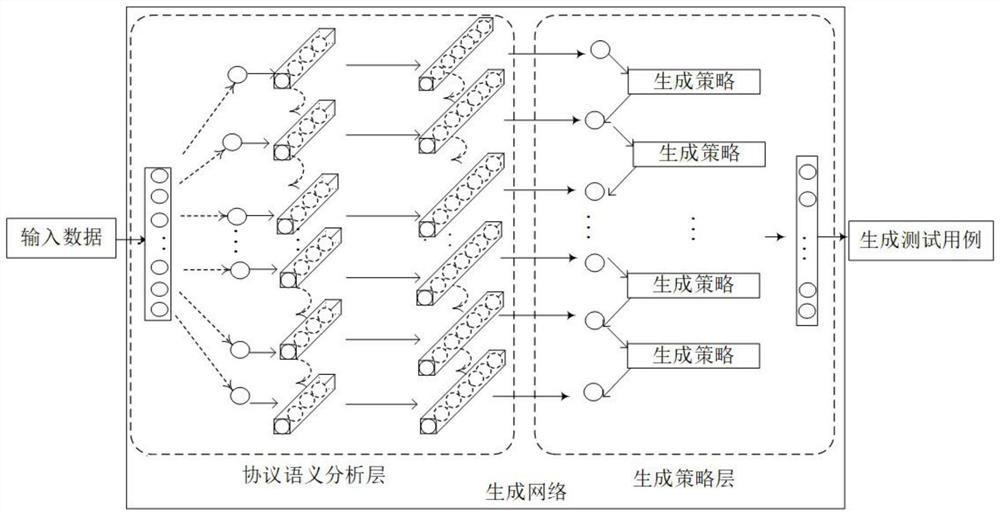
[0021] figure 1 It is a schematic structural diagram of the generation model of the industrial control network protocol based on the anti-sample algorithm in the present invention.
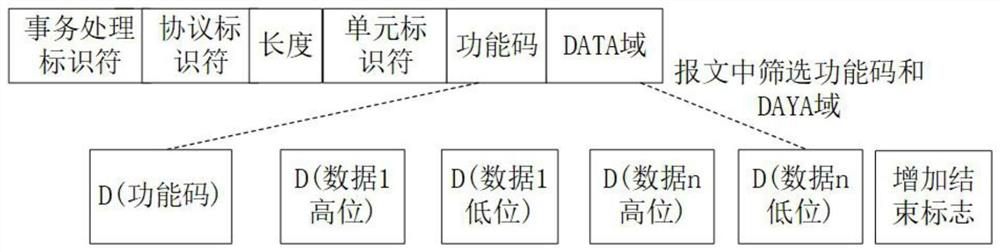
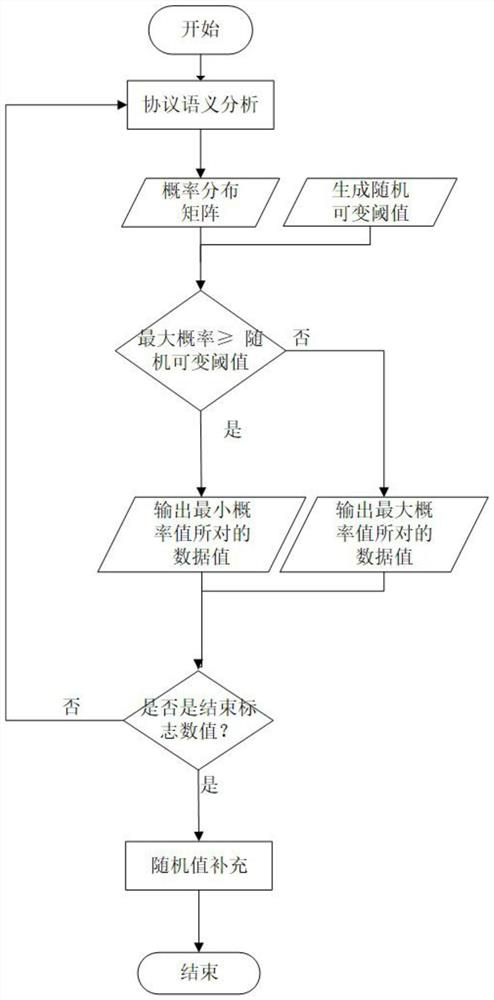
[0022] The generation model consists of two parts: input-output layer and generation network. The generation network constitutes the main part of the generation model, including the protocol semantic analysis layer and the generation strategy layer. The generation strategy layer outputs the probability distribution of the current time step according to the protocol semantic analysis layer. The relationship completes the anti-sample generation strategy, and the protocol semantic analysis layer outputs the probability distribution relationship of the next time step message data value according to the message data value generated by the generation strategy laye...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com