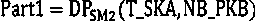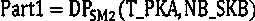An asynchronous key agreement method and device for secure instant messaging
A key agreement and key technology, which is applied in digital transmission systems, data exchange networks, electrical components, etc., can solve the problems of no confidentiality at all before and after messages, protection keys being deciphered, and no secrecy at all.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
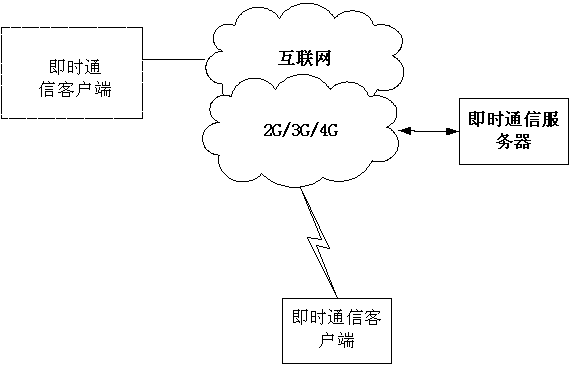
[0116] The asynchronous key agreement method includes four processes: an initial key agreement process, a key chain parent rolling process, a key chain child rolling process, and a session key protection key generation process. Before each real-time encrypted communication, the session key WK is temporarily generated, and then the key agreement is carried out according to the following three-step process:
[0117] Step 1: First execute the initial key agreement process to generate N_CC, and then execute the key chain parent roll process to generate N_CC and N_SC. The temporary public-private key pair used in the key chain parent rolling process in this step is the basic public-private key pair NB_SK / NB_PK for key negotiation.
[0118] Step 2: If the recipient is online, execute the key chain parent rolling process to generate new N_CC and N_SC. The temporary public-private key pair used in this key chain parent rolling process is temporarily generated each time, and the tempor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com