Remote unlocking method and device
A remote unlocking and unlocking technology, applied in the field of communication, can solve the problems of uncontrollable and difficult management of intelligent terminals, and achieve the effect of high security and convenient control and management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
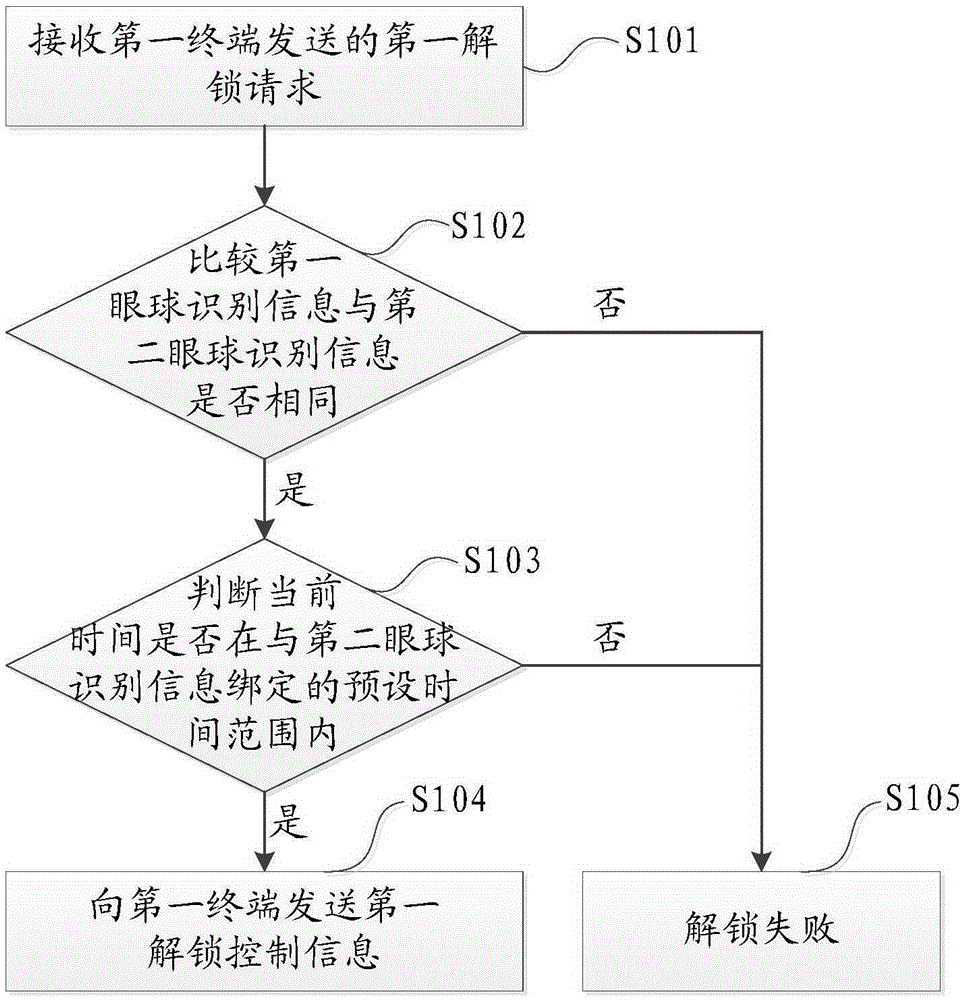
[0038] In order to be able to perform remote unlocking, this embodiment provides a remote unlocking method, which can be applied to network-side devices, such as servers, etc., such as figure 1 shown, including the following steps:
[0039] Step S101, receiving a first unlocking request sent by a first terminal, the first unlocking request carrying first eyeball identification information of a current first user of the first terminal.
[0040] Specifically, the first unlock request is used to request the server to generate first unlock control information to unlock the first terminal; the first eyeball identification information includes information such as iris, sclera, and eyeball rotation track, and can be Identification information for the left eye and / or identification information for the right eye.
[0041] In this embodiment, the eyeball identification information can be obtained through the camera device on the user terminal, for example, the user's eyeball can be pho...
Embodiment 2
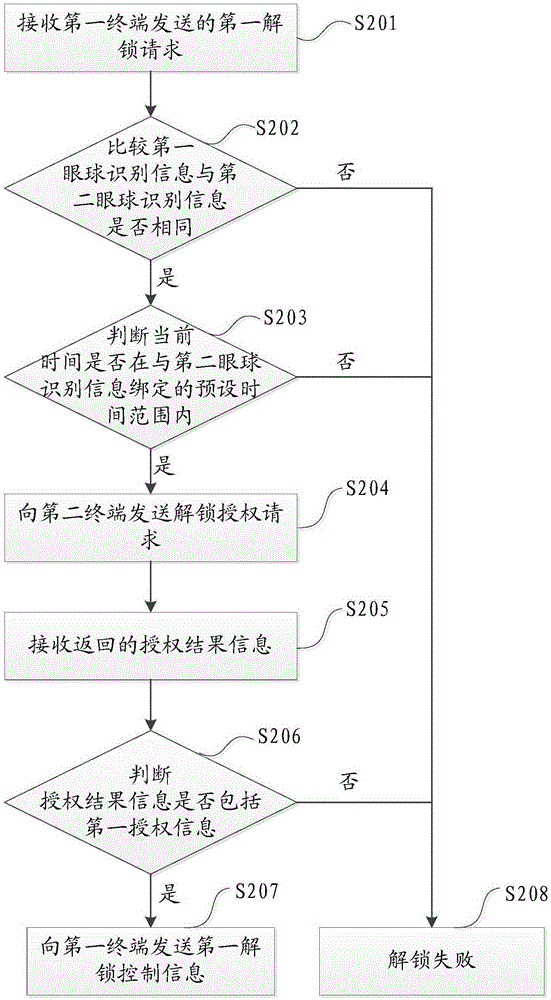
[0059] Such as figure 2 As shown, this embodiment provides a remote unlocking method, which can be applied to network-side devices, such as servers, and includes the following steps:
[0060] Step S201, receiving a first unlocking request sent by a first terminal, the first unlocking request carrying first eyeball identification information of a current first user of the first terminal.
[0061] For example, the server receives a first unlock request sent by a first terminal, where the first unlock request carries iris information or sclera information of the current user.
[0062] Step S202, matching the first eyeball identification information with the second eyeball identification information, the second eyeball identification information is the eyeball identification information of the first user pre-stored on the server, if the matching is successful, then execute step S203, if If the matching fails, step S208 is performed, that is, the unlocking fails.
[0063] For ex...
Embodiment 3
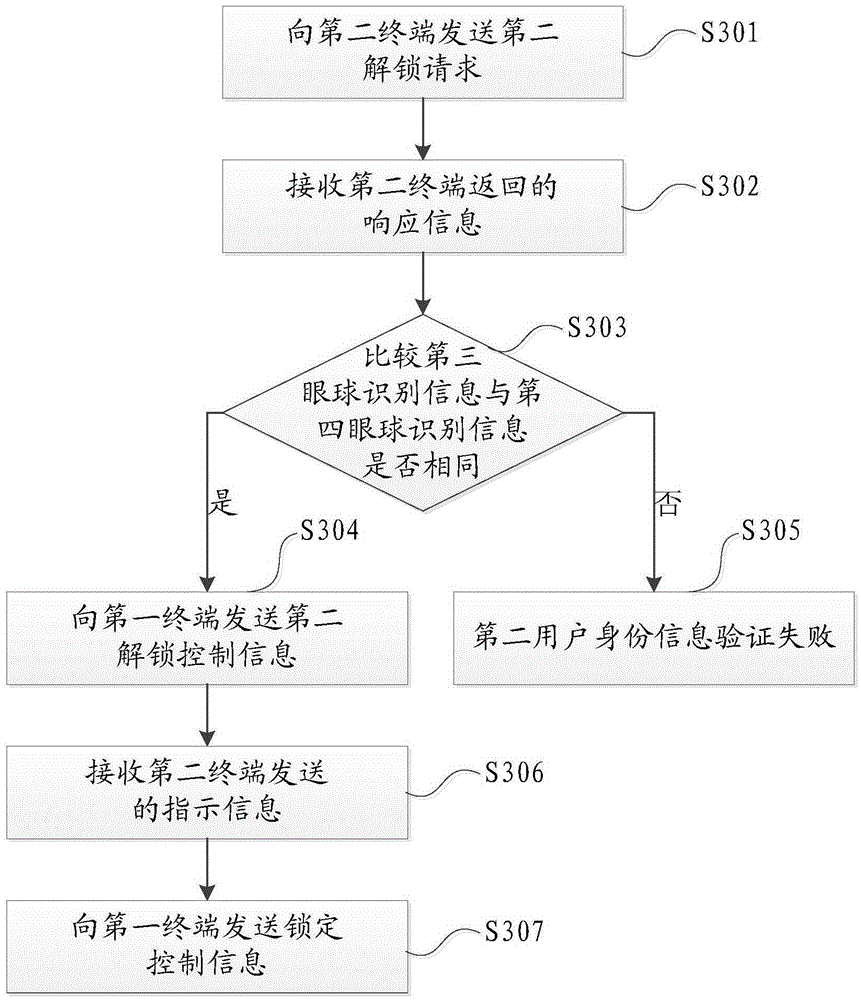
[0080] Such as image 3 As shown, this embodiment provides a remote unlocking method, on the basis of Embodiment 1 or Embodiment 2, the following steps may also be included:
[0081] Step S301, when the time is not within the preset time range, send a second unlocking request to the second terminal. The second unlocking request is used to request the server to generate second unlocking control information to unlock the first terminal.
[0082] Step S302, receiving the response information returned by the second terminal according to the second unlocking request, the response information including: first authorization information allowing the first terminal to be unlocked, and the current second user's first authorization information of the second terminal; Three-eye recognition information.
[0083] Specifically, the third eyeball identification information includes iris, sclera, eyeball rotation trajectory and other information, and may be left eyeball identification inform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com