Unmanned aerial vehicle access control method based on attribute authentication
An access control and drone technology, applied in the field of information security, can solve problems such as the inability of access control methods to adapt, and achieve the effects of flexible and fine-grained access control, ensuring communication security, and realizing anonymous access.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention is described in detail below in conjunction with accompanying drawing:
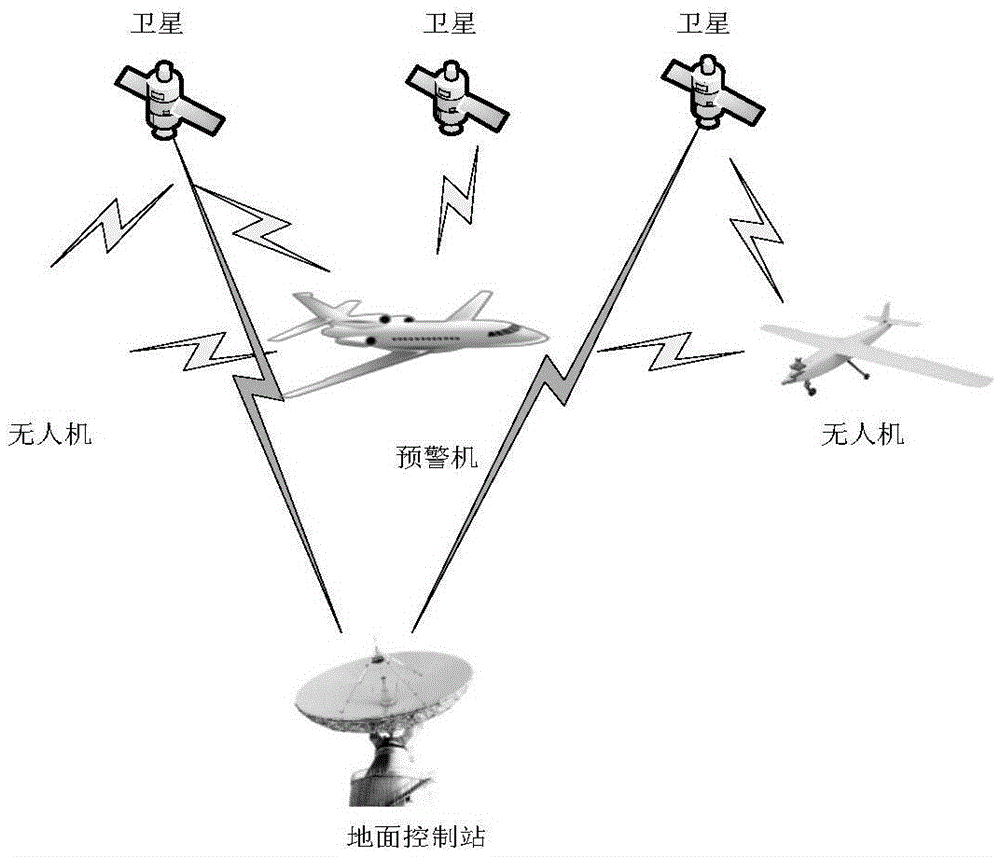
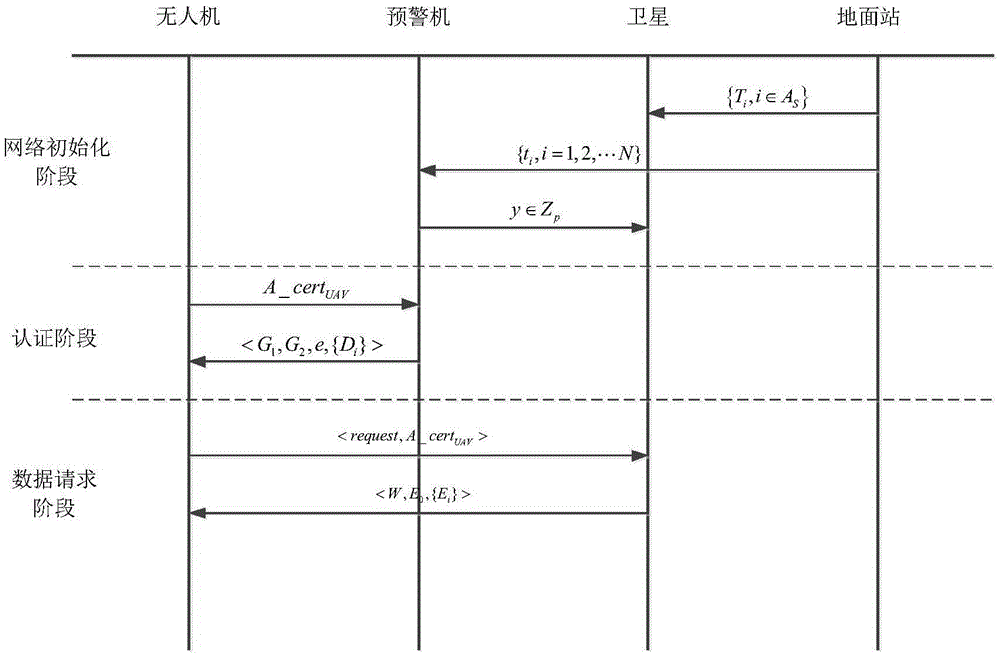
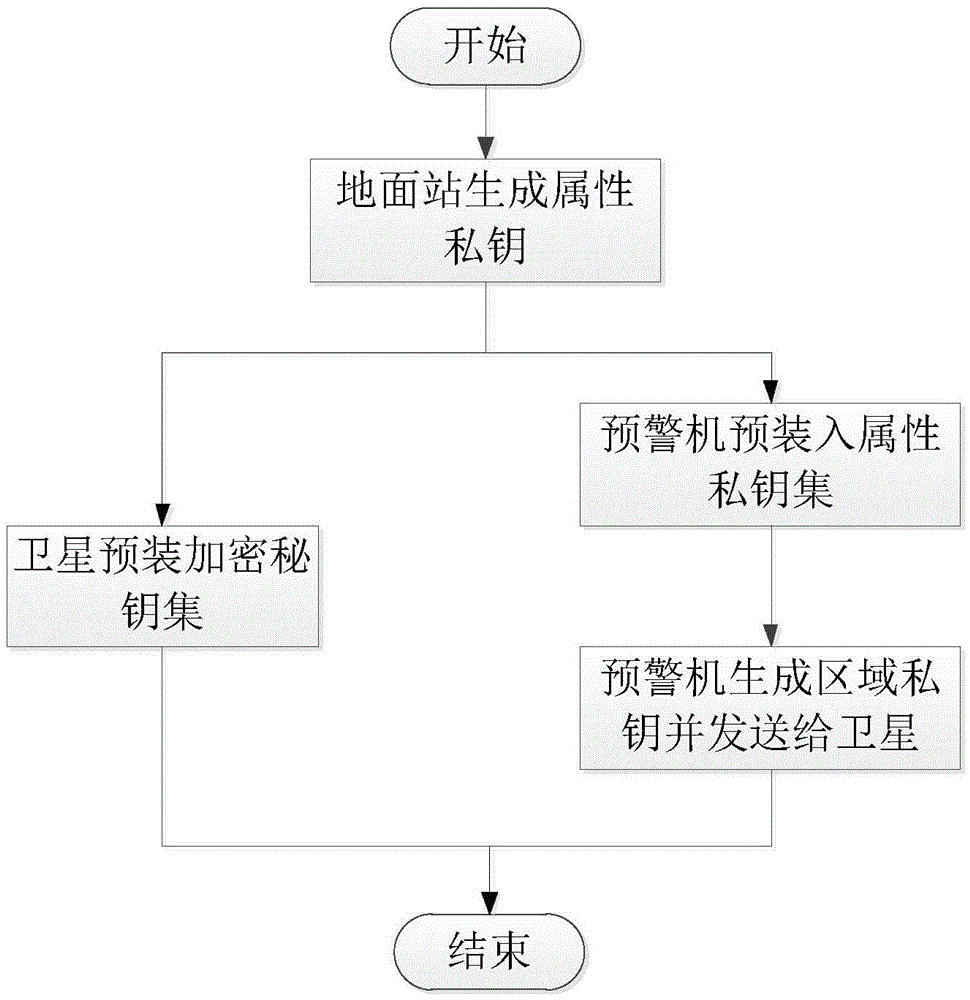
[0039] refer to figure 1, the UAV communication system used in the present invention consists of four parts: UAV, early warning aircraft, satellite and ground station, wherein the UAV is the subject of access control, and uses its own attributes as the basis for accessing satellite data, and its attributes refer to The characteristics that can distinguish drones; the early warning aircraft is the center of the drone fleet, providing attribute authentication functions for drones in its monitoring area, and performing monitoring tasks for satellites; satellites provide data services for drones, The detected data is the object of access control; the ground station is the basis of the entire UAV communication network, providing overall monitoring and control. The relationship between the subjects is as follows: UAVs can communicate through satellites or early warning aircraft; ea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com