Application security testing method, device and system
A technology for security testing and application programs, applied in the field of communication, can solve problems such as false negatives and false negatives, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] In this embodiment, the application program security test is completed by using only the terminal device as an example.
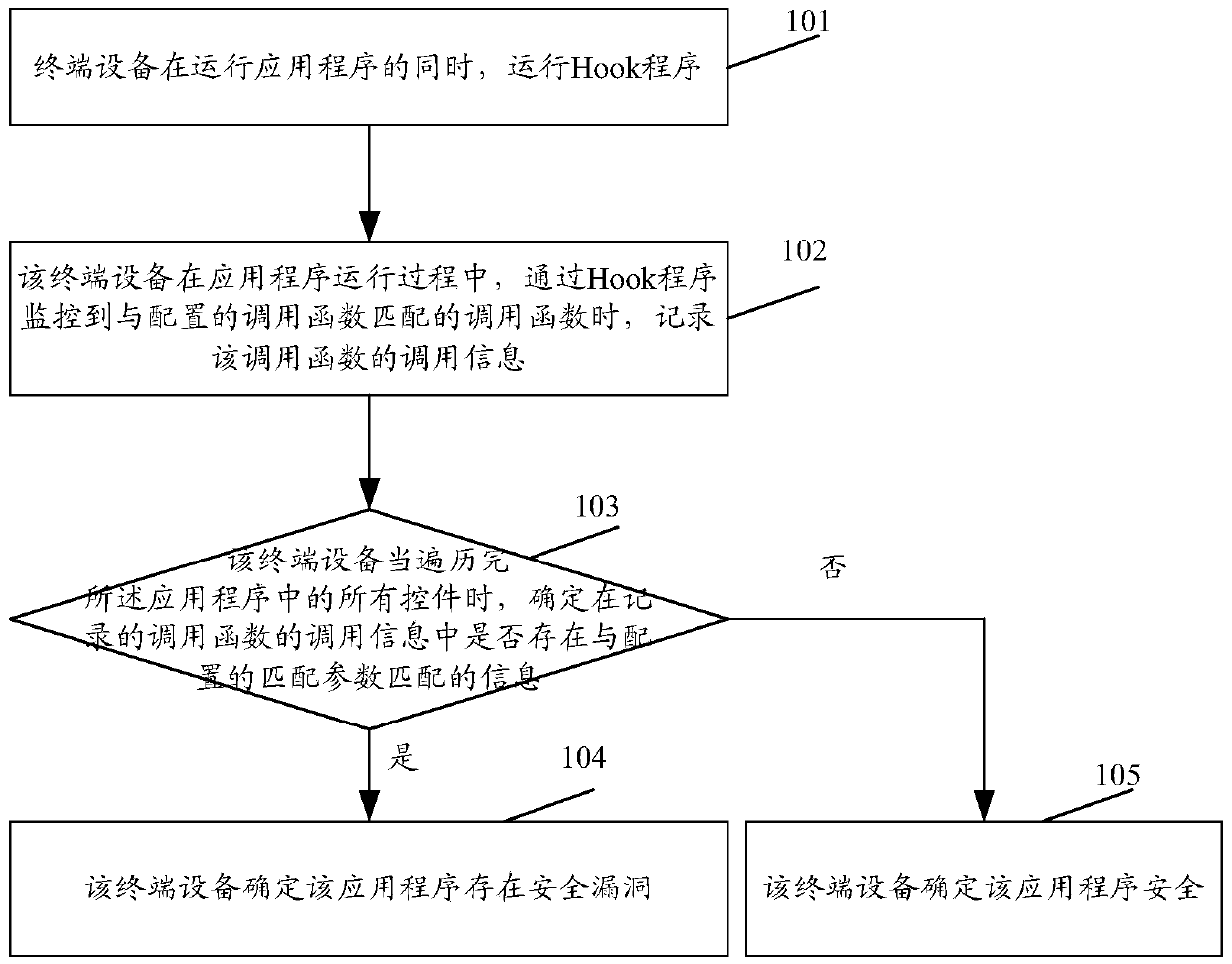
[0041] see figure 1 , figure 1 It is a schematic diagram of the application program security testing process in Embodiment 1 of the present application. The specific steps are:
[0042] Step 101, the terminal device runs the Hook program while running the application program.
[0043] In this step, the terminal device can pass automated testing, manual testing, or use the application to make the application run
[0044] Whether you are using the application or testing the application, you need to traverse all the controls in the entire application, that is, all the corresponding user interfaces (UserInterface, UI); of course, if you only need to determine whether there is a security in a certain part of the application Vulnerabilities, just run a certain part of the program.
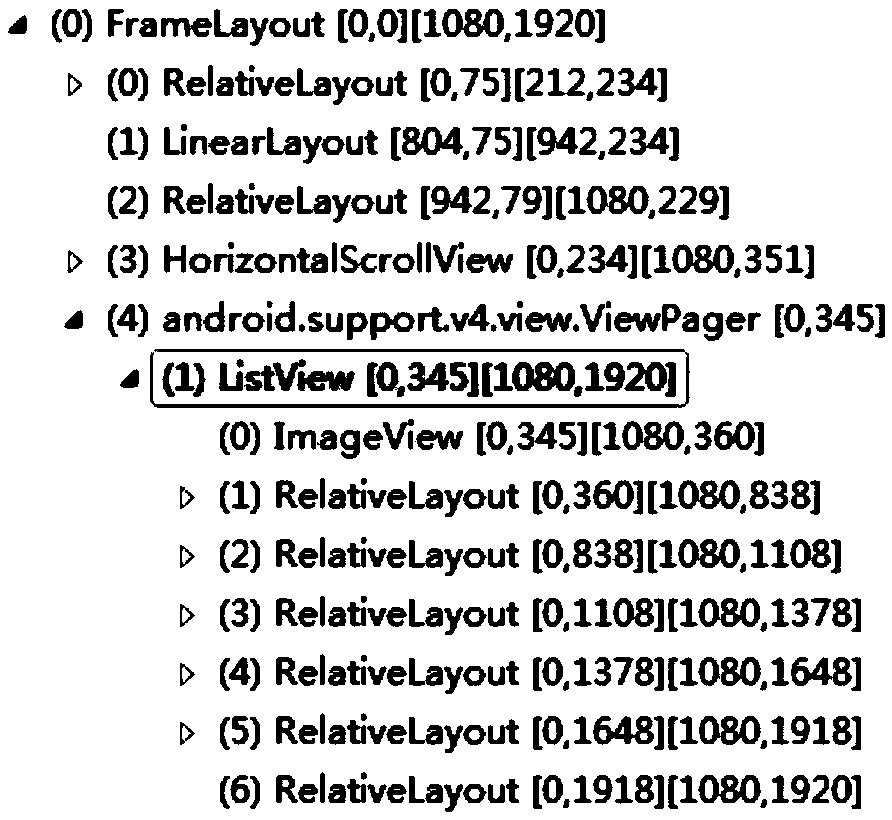
[0045] When performing automated testing on an application, various a...
Embodiment 2
[0080] In this embodiment, a combination of the testing device and the device under test is used to complete the security test of the application program. The test device here can be a PC, etc.; the device to be tested, such as a mobile phone, a tablet, etc.
[0081] In this embodiment, the application program and the Hook program run on the device under test, and the device under test and the test device can communicate wirelessly or through a USB interface.
[0082] For example, when testing the android program, the ADB server program is usually installed on the device under test (terminal device) using the android program, then the ADB client program is installed on the test device, and the ADB client is used to call the uiautomator program of the android system, namely Information about the applications running on the terminal device can be obtained.
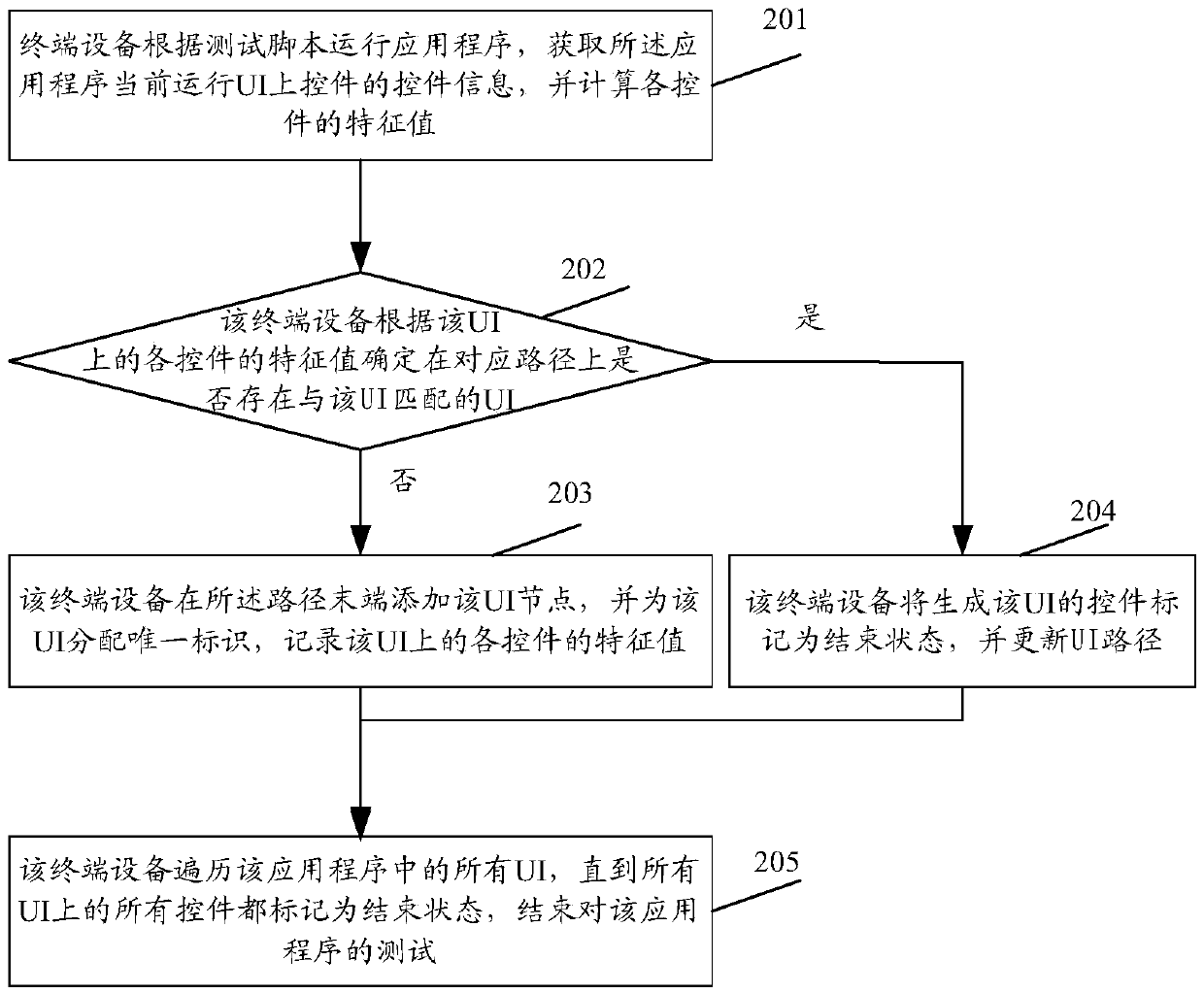
[0083] see Figure 5 , Figure 5 It is a schematic diagram of the application program security testing process in the s...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap