A terminal device and its file management method
A terminal device and file management technology, applied in the direction of digital data protection, etc., can solve the problem that local files cannot be safely managed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] The invention of this application proposes that when managing the files on the terminal device, security mode management can be introduced, that is, after entering the security mode, the user can choose the corresponding file to hide, encrypt and other settings, so as to ensure the security and privacy of user files sex.
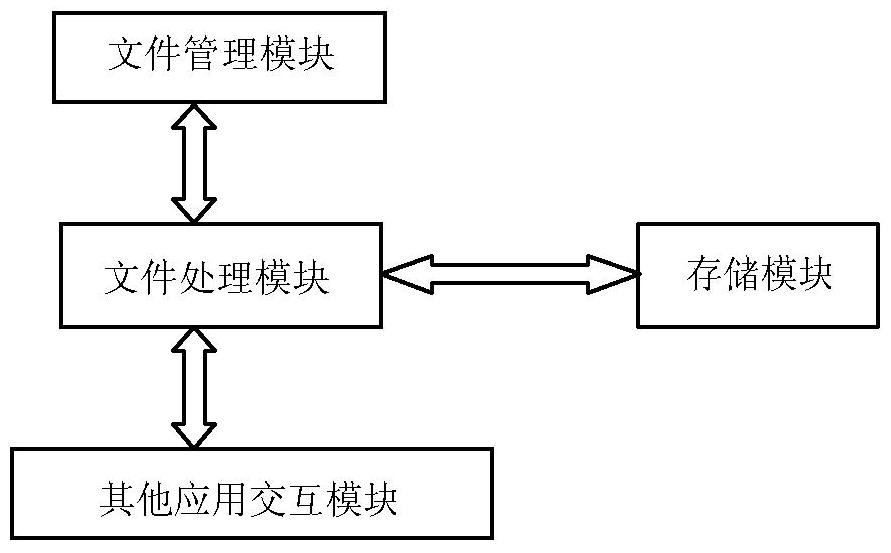
[0030] Based on the above ideas, this embodiment provides a terminal device capable of setting a security mode for a file, which at least includes a file management module and a file processing module connected to each other.
[0031] The file management module, when the terminal device enters the file management security mode, calls the file processing module to perform corresponding security management operations on the specified single or multiple files according to the instructions initiated by the user;
[0032] Wherein, the security management operation includes at least concealment and / or encryption operation.
[0033] Specifically, the file m...
Embodiment 2
[0049] This embodiment provides a file management method of a terminal device, which mainly includes the following operations:
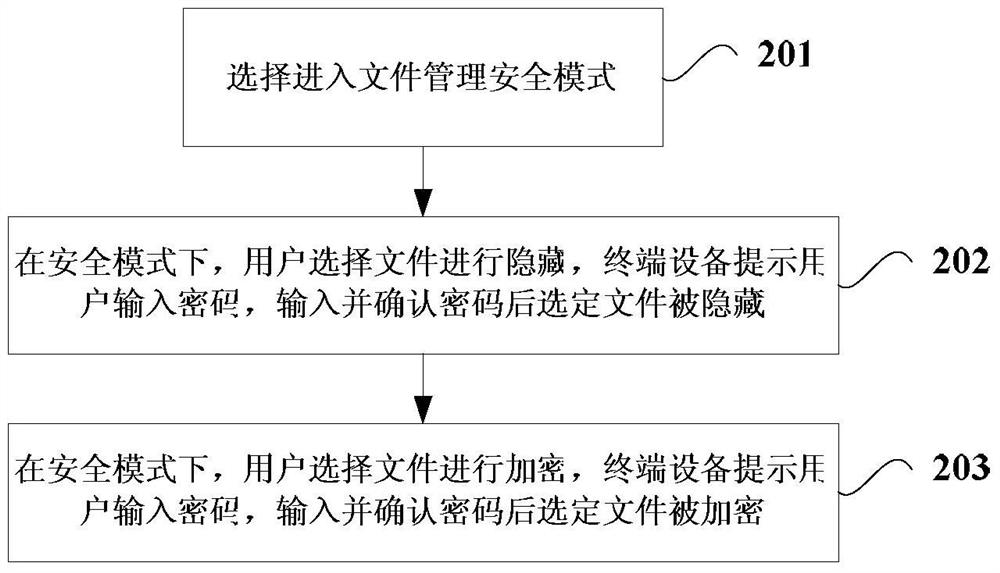
[0050] When the terminal device enters the file management security mode, the terminal device performs corresponding security management operations on the specified single or multiple files according to the instructions initiated by the user;
[0051] Wherein, the security management operation includes at least concealment and / or encryption operation.
[0052] In addition, the terminal device also provides the user with security management options, through which the user initiates an instruction, wherein the security management options at least include hiding and / or encryption options.
[0053] Specifically, when the user initiates an instruction through the hiding option, the terminal device also prompts the user to enter a password, and after the user enters the password and confirms the password, the hidden operation is performed on the specified ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com