Method and system for defending distributed denial of service (DDoS) attack
A denial of service attack, distributed denial technology, applied in the field of network security, can solve problems such as failure of defense methods and server downtime
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] see figure 1 Shown is a specific embodiment of a method for defending against distributed denial-of-service attacks described in this application, including:
[0055] Step 101, detecting the IP address that accesses the network within the set time slice, and comparing the detected IP address with the legally permitted access IP address stored in the legal IP records of the database to determine the rate of increase in the number of new IP addresses per unit time;
[0056] Step 102, perform further operations according to the increase rate of the number of new IP addresses per unit time:
[0057] When the increase rate of the number of new IP addresses per unit time is less than the set first speed threshold, it is determined that there is no attack, and the processing method when not under attack is executed, and the service is normally provided;
[0058] When the increase rate of the number of new IP addresses per unit time is greater than the set first speed threshol...
Embodiment 2
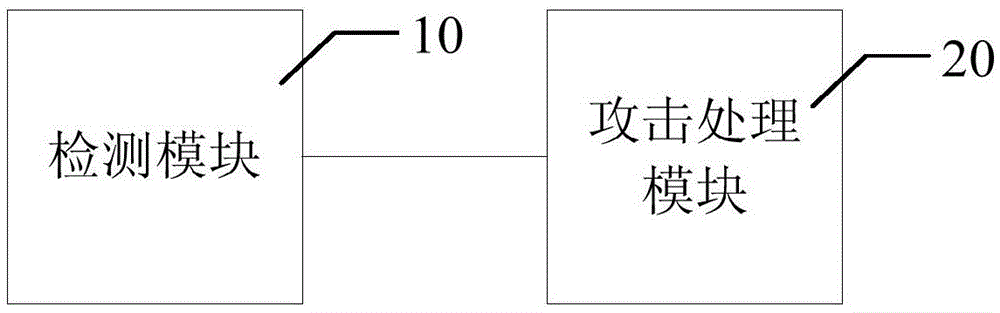
[0070] On the basis of Embodiment 1, the present invention also provides a system for defending against distributed denial-of-service attacks capable of implementing the method of Embodiment 1 above, the system comprising:
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap