Strategy customization-based Android mobile phone security protection system and protection method thereof
A security protection technology for Android mobile phones, applied in security devices, telephone communications, electrical components, etc., can solve problems such as software management troubles, high bills, leakage, etc., and achieve effective protection strategies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0036] see Figure 1-5 , a strategy-customized security protection system for Android mobile phones, including a mobile phone anti-theft module, a communication guard module, a traffic statistics module, a process management module and a system optimization module, a process management module and a system optimization module;
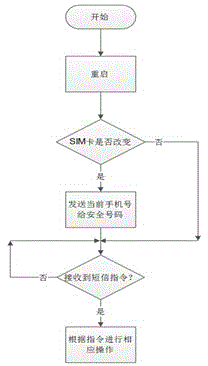
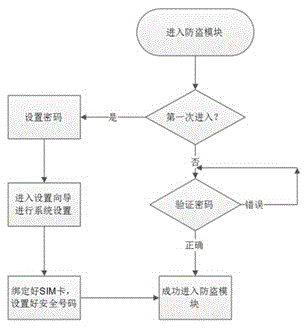
[0037] The mobile phone anti-theft module is used to protect the user's address book, short messages and important information. The mobile phone anti-theft module adopts SharedPreferences to store passwords, and inserts a key whose key value is password into the config.xml file under Sdcard to store passwords.
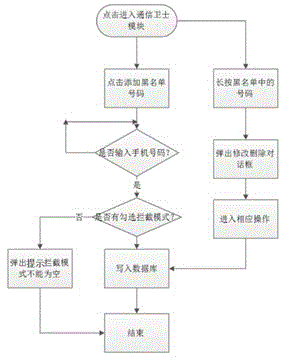
[0038] The communication guard module realizes the protection and control of mobile phone communication data. The communication guard module intercepts system short message broadcasts, uses AIDL to o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com