Terminal and method and device for terminal to identify pseudo base station
A terminal identification and pseudo base station technology, which is applied in the field of terminals and its identification of pseudo base stations, can solve problems such as high implementation cost, insufficient conditions, and user impact, and achieve reduced identification and prevention costs, strong applicability, and low software development complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
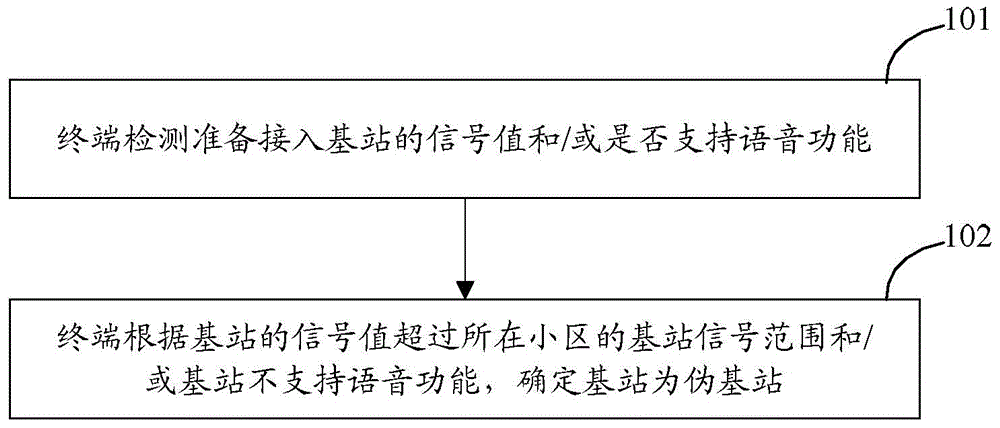
[0041] In the embodiment of the present invention, the terminal detects the signal value of the base station to be accessed and / or whether it supports the voice function, and determines that the base station is a pseudo base station when the signal value of the base station exceeds the base station signal range of the cell where it is located and / or the base station does not support the voice function .
[0042] The present invention will be further described in detail below with reference to the accompanying drawings and specific embodiments.
[0043] The embodiment of the present invention implements a method for a terminal to identify a pseudo base station, such as figure 1 As shown, the method includes the following steps:
[0044] Step 101: The terminal detects the signal value of the base station to be accessed and / or whether the voice function is supported;
[0045] The detecting the signal value of the base station to be accessed may be: detecting the broadcast signa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com