A file protection method and device
A file and file operation technology, applied in the field of system security, to achieve the effect of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
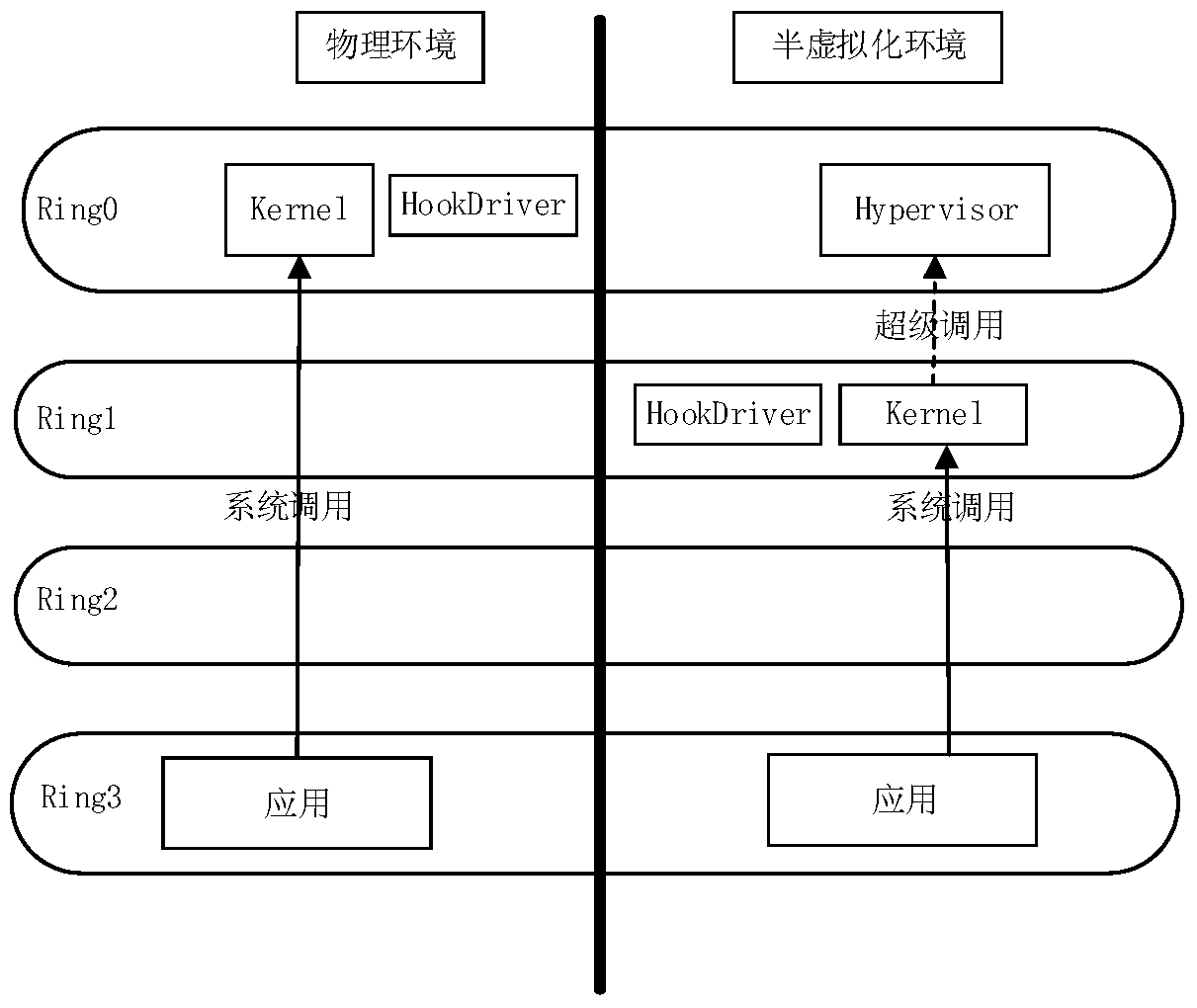
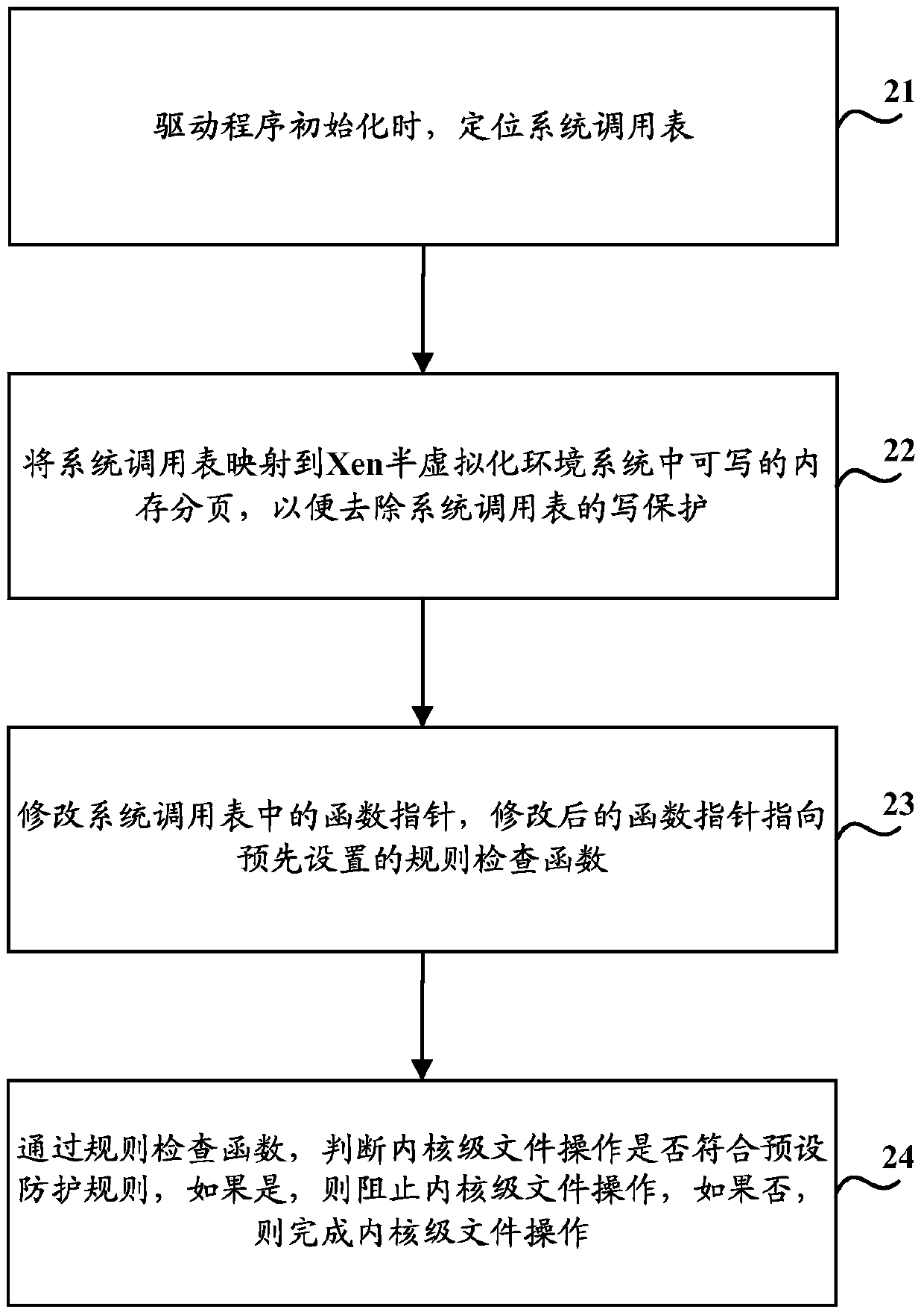
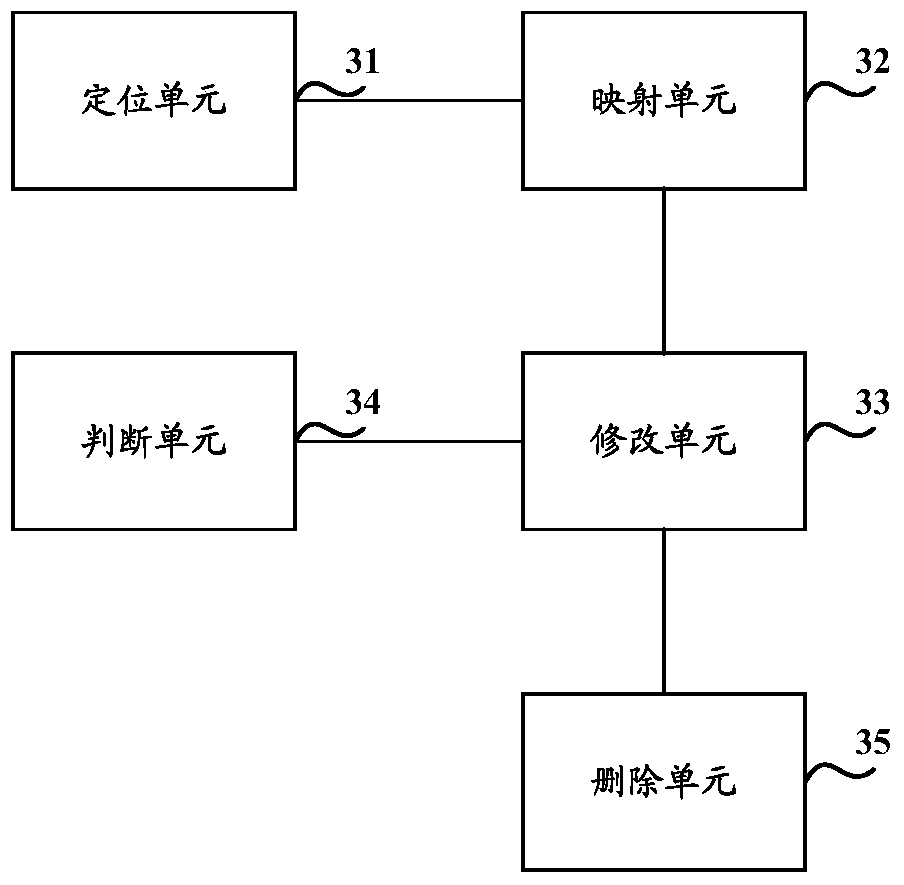
[0053] First of all, it needs to be explained that Intel processors implement access control through the Ring level, which is divided into four layers: Ring0 layer, Ring1 layer, Ring2 layer, and Ring3 layer. Ring0 layer has the highest authority, and Ring3 layer has the lowest authority. According to Intel's original concept, the application program works at the Ring3 layer and can only access the data of the Ring3 layer; the operating system works at the Ring0 layer and can access the data of all layers; while other drivers are located at the Can access the data of this layer and the lower layer. But the current operating system (OS), including Windows and Linux, only uses two layers—Ring0 layer and Ring3 layer, respectively to store operating system data and application data, and drivers (including device drivers and non-device drivers) all run on Ring0 level, and the location of the kernel (Kernel) is also at the Ring0 level. In the Xen paravirtualized environment system,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com