System and method for SQL injection prevention
An anti-injection and legality technology, applied in the transmission system, electrical components, etc., can solve the problems of poor defense against SQL attacks, prone to errors, and high cost, so as to improve accuracy, service efficiency, and increase security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described in detail below in conjunction with examples, but the implementation of the present invention is not limited thereto.
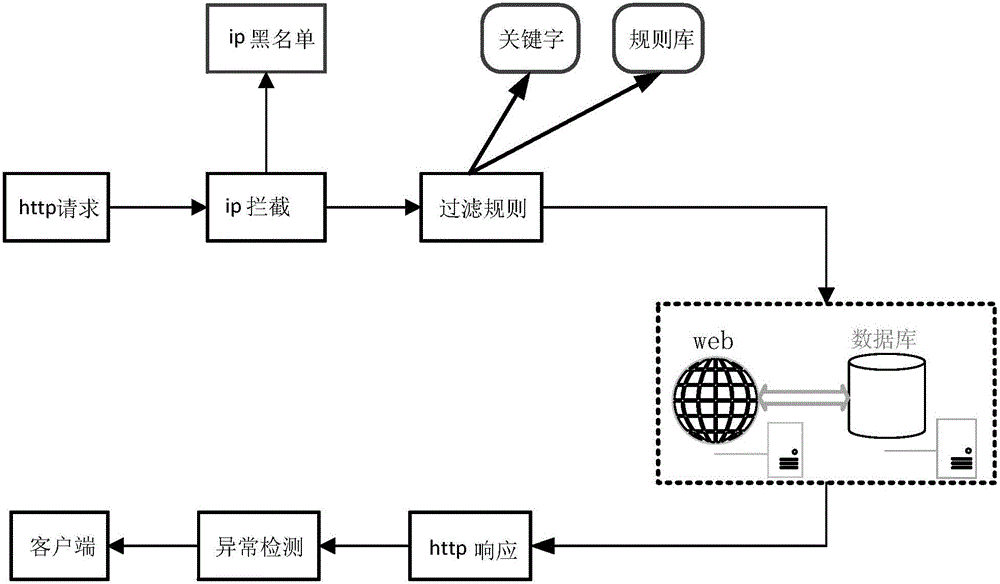
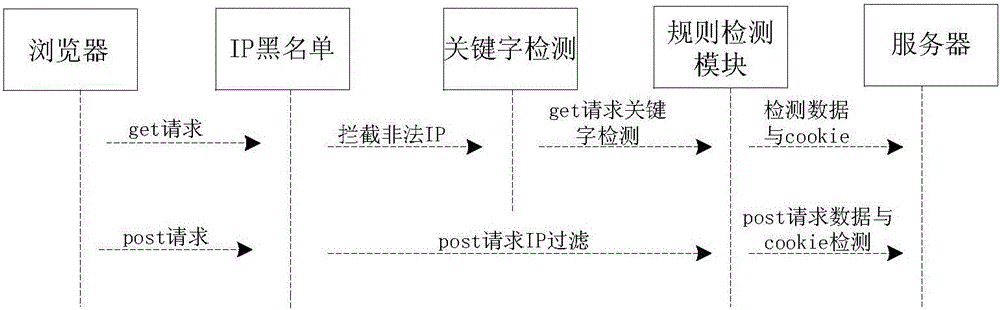
[0029] The database is the core part of the server. Due to the negligence of programmers or improper parameter configuration, many newly developed systems may have SQL injection vulnerabilities. At the same time, some previously developed systems have SQL injection vulnerabilities, which are difficult to repair in the later stage, and are expensive to repair. In order to solve the security problems of existing SQL injection or SQL hidden danger systems, the present invention designs a SQL injection prevention system , It includes IP blacklist filtering module, request rule detection module and http response interception module. The specific implementation principles are as follows:
[0030] The overall idea of the design of SQL anti-injection: SQL anti-injection system design a complete set of security detec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com