Log processing method and log processing electronic equipment
A technology for processing electronic equipment and processing methods, which is applied in the field of log processing, and can solve the problems of inability to track, unable to locate error information, and low error checking efficiency, so as to achieve the effect of accurate error positioning and improving error checking efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
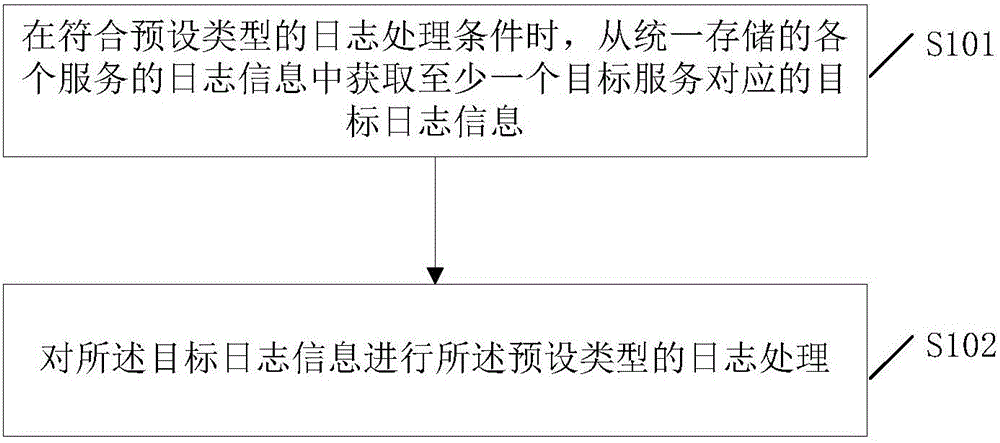
[0044] refer to figure 1 , figure 1 It is a flow chart of Embodiment 1 of a log processing method provided by this application. The method is applicable to but not limited to log processing in a microservice environment, such as figure 1 As shown, the log processing method may include the following steps:
[0045] S101: Obtain target log information corresponding to at least one target service from the uniformly stored log information of each service when a preset type of log processing condition is met.
[0046] Wherein, the log processing condition of the preset type may be:
[0047] A log analysis time of a preset type for at least one target service is reached; or,
[0048] A log analysis request of a predetermined type is received for at least one target service; or,
[0049] A preset log push time for at least one target service is reached; or,
[0050] A log view request was received for at least one target service.
[0051] The preset type of log analysis can be ...
Embodiment 2
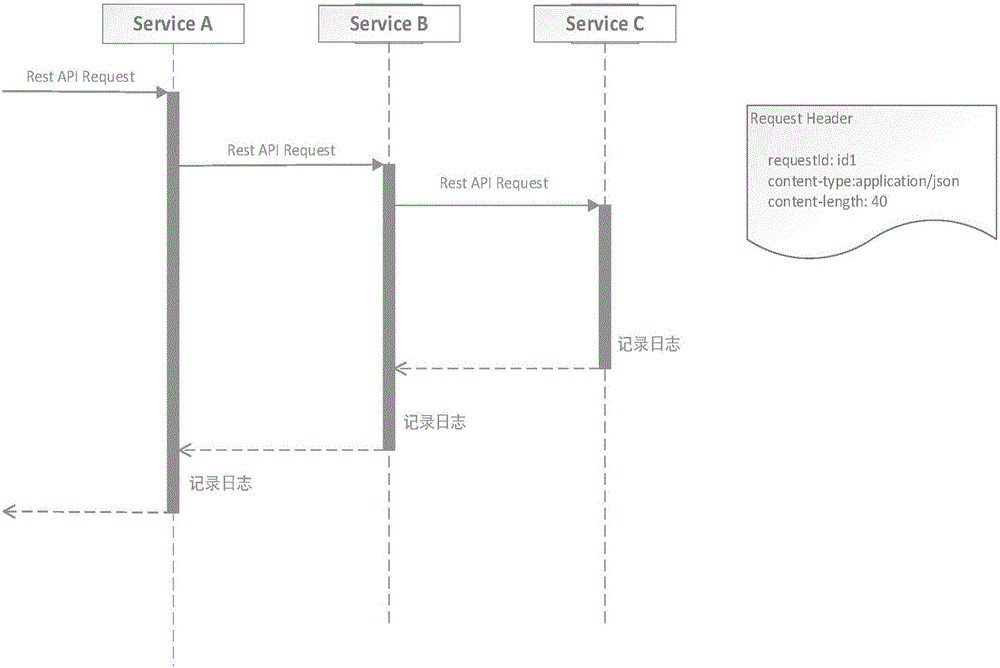
[0060] This embodiment provides a record storage and access solution for multi-service log information involved in the penetration access in the penetration access scenario.
[0061] Specifically, refer to image 3 The schematic diagram of log recording during penetrating access between multiple services is shown. When an API call performs penetrating access between multiple services, the log information during penetrating access to each service is recorded in a timeline manner. Wherein, the access ID (identification number, Identity) of this penetration access is specifically added in the request information of the API penetration access, such as specifically, the access ID can be added at the head of the access request information; on this basis, In the process of API penetrating access to multiple services, the access ID is added to the log information generated when API penetrating access to each service, so that for one penetrating API access, the log information finally ...
Embodiment 3
[0068] refer to Figure 5 , Figure 5 It is a flow chart of Embodiment 3 of a log processing method provided by this application. In this embodiment, when the log processing condition of the preset type is: reaching the log analysis time of the preset type for at least one target service or receiving When a preset type of log analysis request for at least one target service is received, the step S102 can be implemented through the following steps:
[0069] S501: Perform log analysis of the preset type on the target log information corresponding to the at least one target service to obtain a log analysis result;
[0070] S502: Push the log analysis result.
[0071] After obtaining the log information of at least one target service from the unified storage data of multi-service log information, the obtained log information of at least one target service may be processed accordingly based on actual log processing requirements.
[0072] Specifically, based on the log informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com