Access control method for neighbor service, and ProSe UE
A technology for access control and access level restriction, applied in the field of communications, which can solve problems such as increased network load and interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
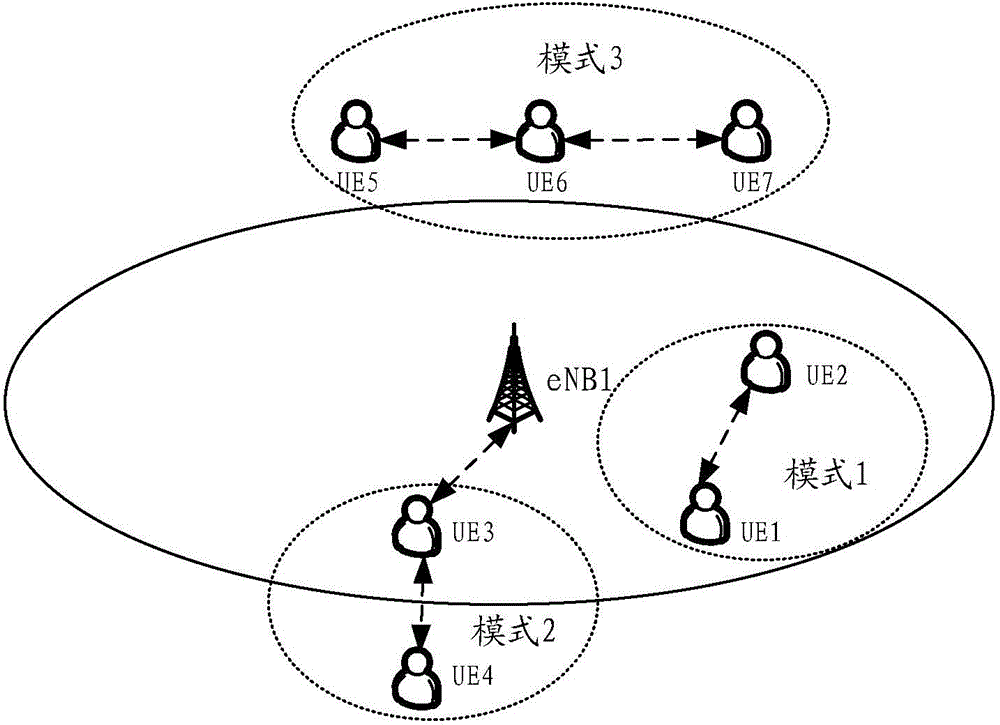
[0196] This example describes the process of using the AC value of the cellular ACB mechanism to access a cell when ProSeUE initiates competition for resources for D2D communication and / or applies for access to the network. The method of accessing a cell by initiating competition for resources is the first resource allocation method in D2D communication; the method of accessing the network based on application is the second resource allocation method in D2D communication. In the second resource allocation mode, in order to be able to apply for resources to the eNB for data transmission of D2D communication, etc., the ProSeUE needs to access the network and enter the connected state.
[0197] When ProSeUE needs to perform D2D communication and the network is relatively congested, the network needs to control the competition initiation and / or access application preparation. ProSeUE uses the AC value in the ACB mechanism set in the cellular network to initiate contention and / or c...
example 2
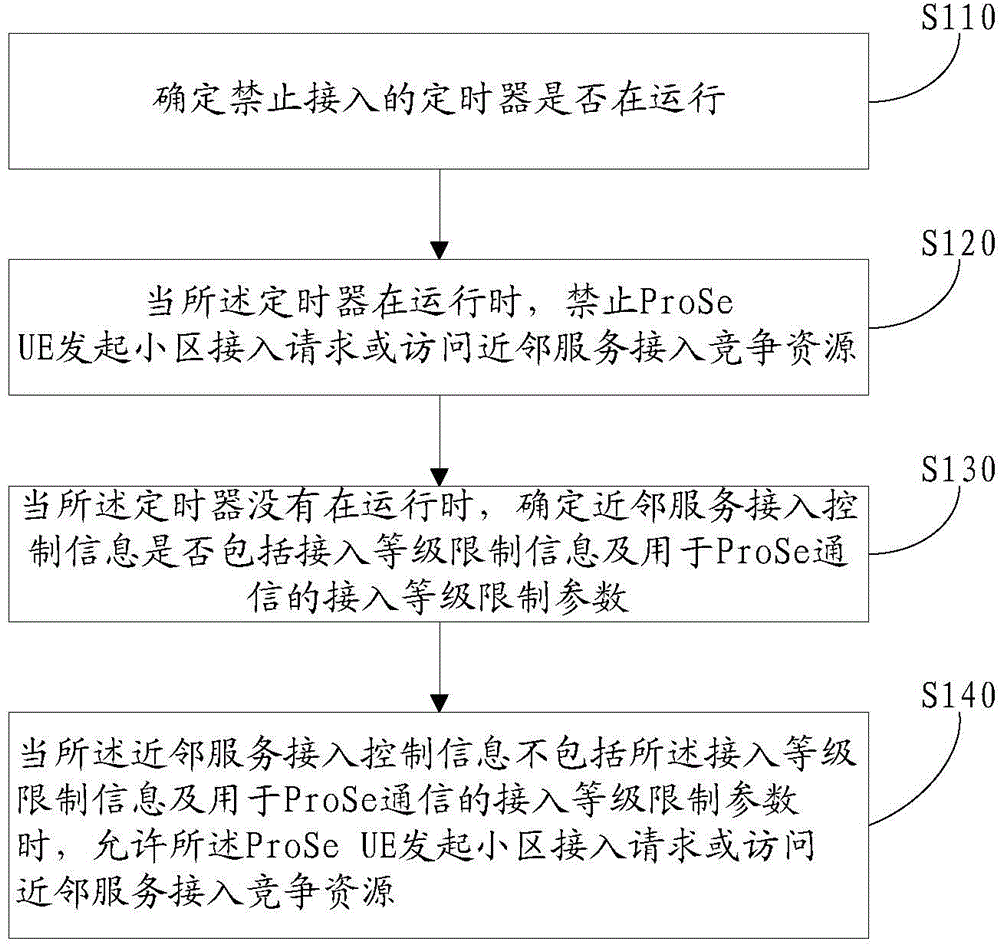
[0208] like Image 6 As shown, the ProSeUE described in this example uses the cellular ACB mechanism when preparing for D2D communication to initiate competition for resources and / or to apply for access to the network. AC values include:
[0209]Step S101: Determine whether T302 or Tbarring is running. The T302 and the Tbarring are the access barring timers described in the foregoing embodiments. When the T302 or Tbarring is running, go to step S108; when the T302 or Tbarring is not running, go to step S102. The running of Tbarring or T302 indicates that the access barring timer is valid, and the access barring time is not over yet. The non-running of Tbarring or T302 indicates that the access barring timer is invalid, the access barring time has expired or the access barring timer has not been started.
[0210] Step S102: Determine whether the access control information received from the base station includes ac-BarringInfo and ac-BarringForProSeComm; if yes, go to step ...
example 3
[0219] Example 3: When the ProSeUE needs to perform D2D discovery, the ProSeUE needs to obtain resources through competition. In the second resource allocation mode, in order to be able to apply for resources from the eNB to perform D2D discovery data transmission, etc., the ProSeUE needs to access the network and enter the connected state. When the network is relatively congested, the network needs to control the initiation of competition and / or the preparation for applying for access. When ProSeUE performs D2D discovery, it sets configuration information based on the EAB mechanism, then the ProSeUE configured with EAB makes an initial emergency call, and the ProSeUE with the AC value of ProSe communication ranging from 11 to 15 will ignore any EAB information broadcast by any network. If the network does not broadcast EAB information, ProSeUE will perform ACbarring to perform access control on the allocated competing resource pool / cell. If the EAB information broadcast by t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com