Virtual machine isolation method and device
A virtual machine and configuration unit technology, applied in the field of communication, can solve the problem that the data center cannot be isolated and protected, and achieve the effect of improving application flexibility and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
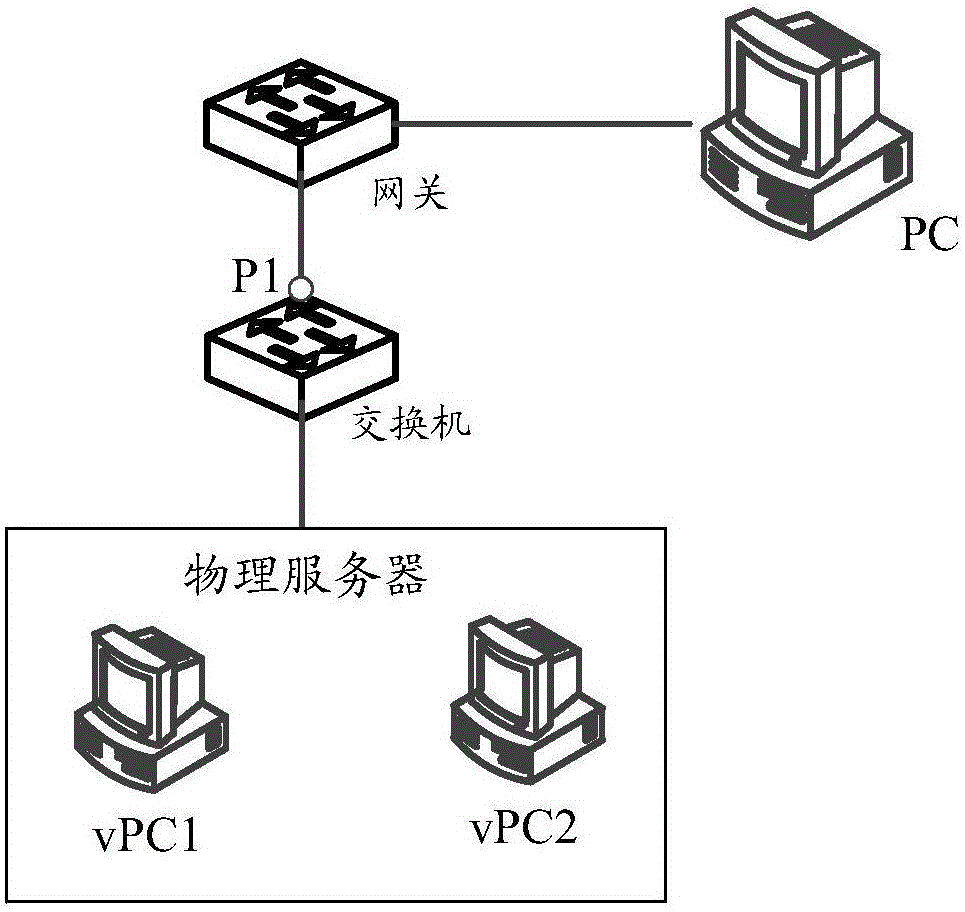
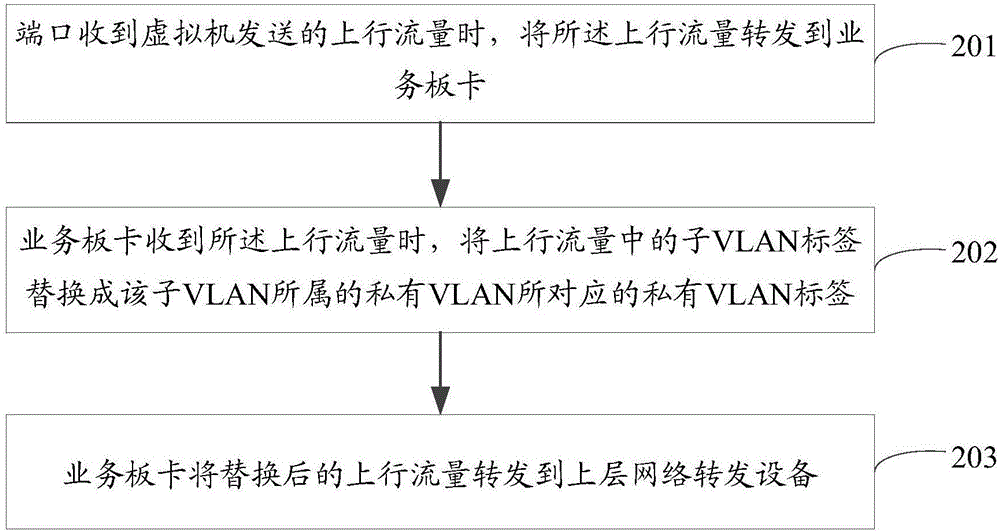
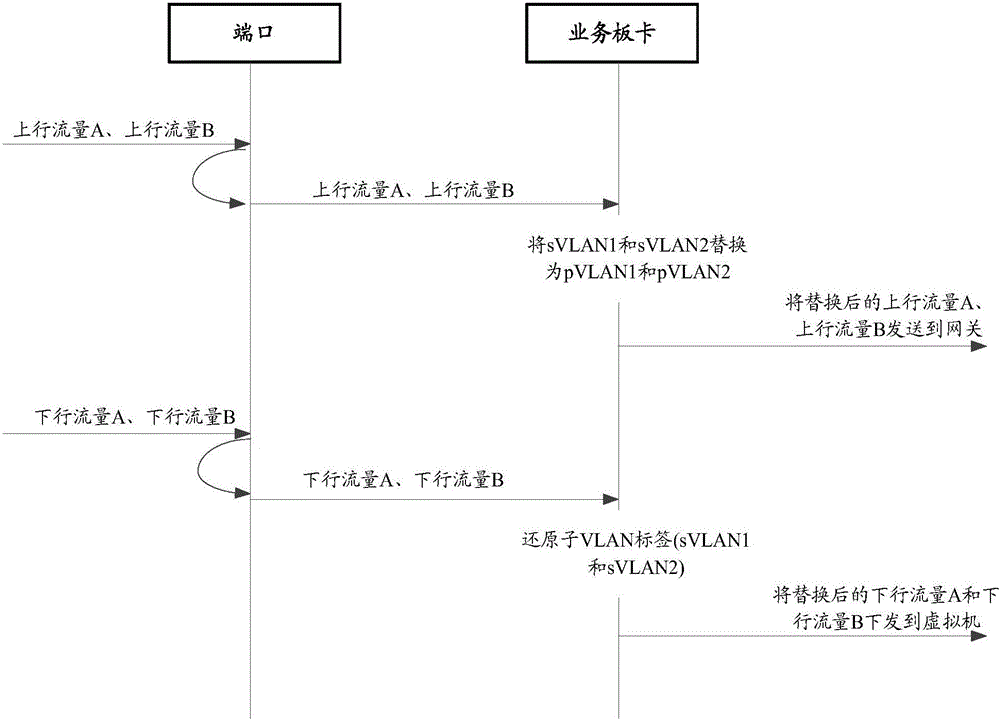
[0040] Please refer to figure 1 , is a schematic diagram of a network in the prior art, wherein one side of the gateway is connected to the user's PC, and the other side is connected to the switch, the switch is connected to the physical server, and vPC1 and vPC2 are virtual machines in the physical server. Because vPC1 and vPC2 provide services for different tenants or services, for communication security reasons, traffic between VMs is not allowed to communicate directly at Layer 2. To isolate traffic between vPC1 and vPC2, you need to configure private VLANs for each virtual machine on the physical server and switch. In the prior art, after the traffic in the private VLAN is transparently transmitted to the switch, the switch will send it to the gateway through the promiscuous port P1 to realize the communication between the virtual machine and the gateway. However, the promiscuous port P1 is usually bound to a private VLAN, so the traffic sent by the virtual machine to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com