False link interception method, device and system
An interception device and fake technology, applied in the field of fake link interception methods and systems, can solve the problems of inability to comprehensively protect user network security, false interception, and low accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
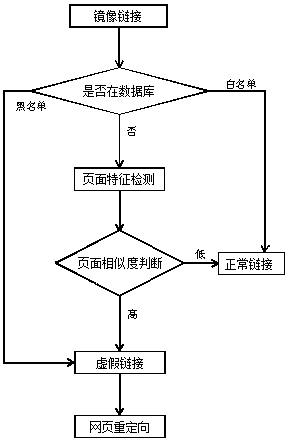
[0014] Such as figure 1 As shown in the process of intercepting false links based on page similarity judgment, the server determines whether the link is in the server's database after obtaining the mirror image of the link accessed by the client. The database of the server includes a blacklist and a whitelist of links. If the link is in the whitelist of the database, it means that the link is a normal webpage link, and the server allows users to access the webpage; if the link is in the blacklist of the database, It shows that the link is a false link, the server intercepts the user's access to the webpage, and returns the homepage of the website to the user's client through webpage redirection technology. If the link is not in the database, the server compares the webpage pointed to by the obtained link with the pre-stored normal webpage, and judges whether the link is a fake link according to the similarity between the two pages.
[0015] Taking the page of Taobao as an exa...
Embodiment 2
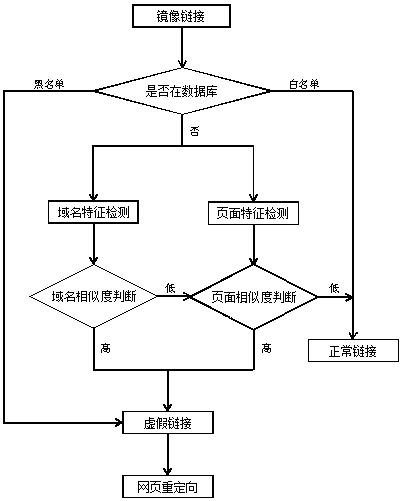
[0021] Such as figure 2 As shown in the process of intercepting false links based on domain name and page similarity judgments, the server determines whether the link is in the server's database after obtaining the mirror image of the link accessed by the client. The database of the server includes a blacklist and a whitelist of links. If the link is in the whitelist of the database, it means that the link is a normal webpage link, and the server allows users to access the webpage; if the link is in the blacklist of the database, It shows that the link is a false link, the server intercepts the user's access to the webpage, and returns the homepage of the website to the user's client through webpage redirection technology. If the link is not in the database, the server compares the link with the domain name corresponding to the regular webpage, and judges whether the link is a fake link according to the comparison result combined with the page similarity obtained by the webpa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com