Device and method for intercepting voice calls
A technology for voice calls and interception devices, applied in security devices, telephone communication, wireless communication, etc., can solve problems such as affecting the use of terminal data services, insufficient interception, etc., to speed up scene recovery, improve user experience, and intercept fast. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
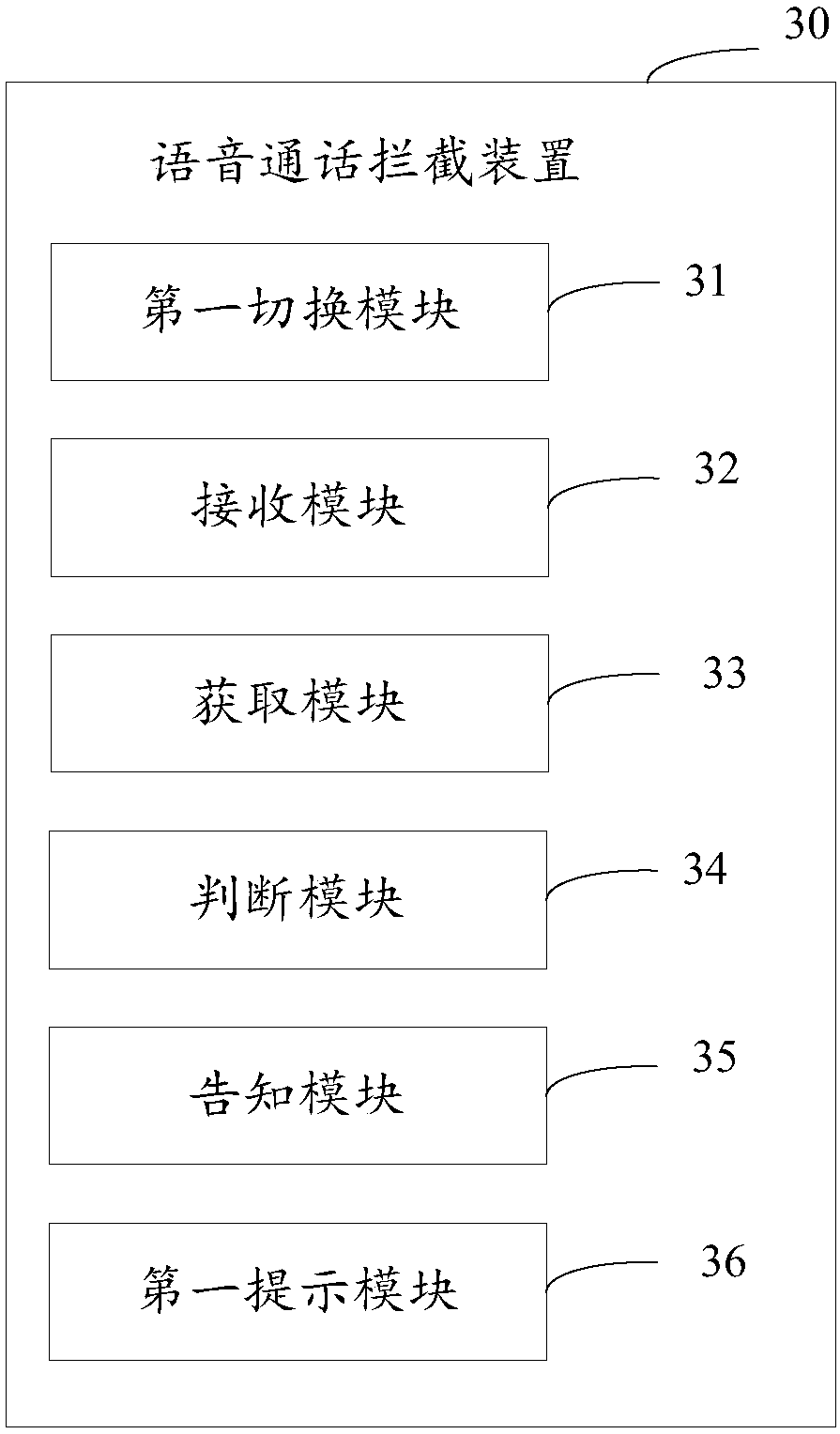
[0077] This embodiment provides a voice call interception device, which can be applied to a terminal, and the device is used to intercept harassing calls, image 3 is the block diagram of the device, such as image 3 As shown, the device 30 may include the following components:
[0078] The first switching module 31 is configured to establish a connection with the base station after receiving a broadcast message from the base station;
[0079] In this embodiment, after the base station near the called terminal receives the request from the calling party to call the called party, it broadcasts a message to find the called party. After receiving the broadcast message from the base station, the called party responds and authenticates with the base station. After exchanging information such as rights, establish a connection with the base station. Optionally, the terminal switches the network back from 3G or 4G to the 2G state, that is, in this embodiment, the terminal may be in ...
no. 2 example
[0092] This embodiment provides another voice call interception device, which includes:
[0093] The first switching module is configured to establish a connection with the base station after receiving a broadcast message from the base station, and switch the current network of the terminal to 2G;
[0094] The receiving module is used for receiving the voice establishment request from the base station;
[0095] An acquisition module, configured to acquire an incoming call number according to a voice establishment request;
[0096] The second switching module is used to switch the current network from 2G to 3G or 4G after obtaining the caller number according to the voice establishment request;
[0097] It should be noted that, in the first embodiment above, after the called party obtains the calling number, it needs to keep the network fallback state, that is, the 3G or 4G state falls back to the 2G state, but in this embodiment, after obtaining the calling number After the ...
no. 3 example
[0107] In this embodiment, a voice call interception method based on process control is proposed by analyzing the initiation and establishment process of the voice call, and researching the harassment interception method based on the application layer of the traditional terminal. In this embodiment, after the voice establishment request of the harassing number arrives at the user's terminal, the bottom layer of the user terminal splits the signaling to obtain the harassing number itself, and then compares it with the harassing phone number in the terminal's harassing database. If the current incoming call is a harassment number, no link will be established with it. Otherwise, the user will be reminded of the incoming call. The following is an example combined with the attached Figure 4 The method for intercepting a voice call provided by the present invention will be described below.
[0108] First, user B's number is set as a nuisance number by user A, such as Figure 4 As ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com