Call processing method and apparatus
A technology of call processing and call request, applied in the direction of telephone communication, electrical components, branch equipment, etc., it can solve problems such as falling on friends, mobile phones falling on the desk of the office, exposure of personal privacy information of the owner, etc., to avoid privacy The effect of information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
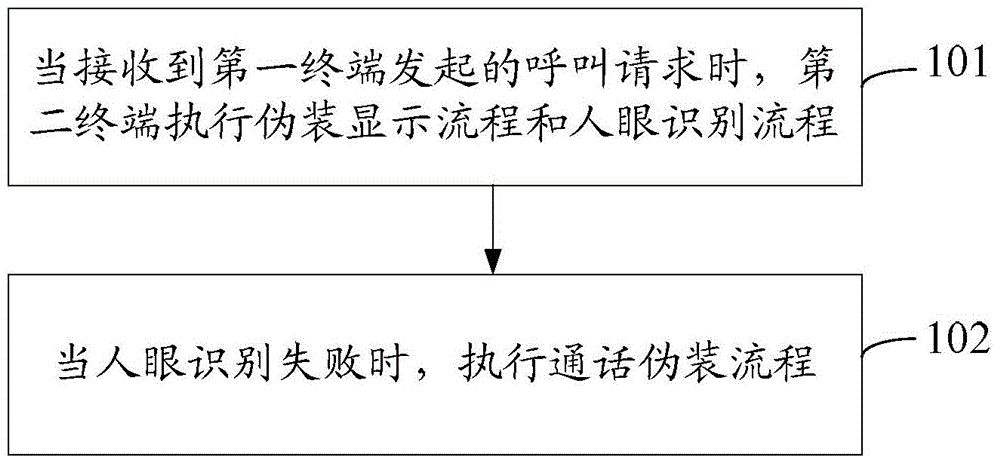
[0050] Embodiment 1 of the present invention provides a call processing method, such as figure 1 As shown, the method includes the following steps:
[0051] Step 101: When receiving a call request initiated by the first terminal, the second terminal executes a masquerade display process and a human eye recognition process;
[0052] In this step, the first terminal refers to a terminal included in the preset list of the second terminal; the preset list is used to store information of sensitive contacts, and the information may be identification information used to identify a contact; for example , phone number, contact name, etc.; therefore, before this step, the second terminal needs to pre-set the preset list, for example, the second terminal user can set one or more contacts in the second terminal as required for sensitive contacts. Therefore, the first terminal is the sensitive contact set for the user of the second terminal.
[0053] When receiving the call request init...
Embodiment 2
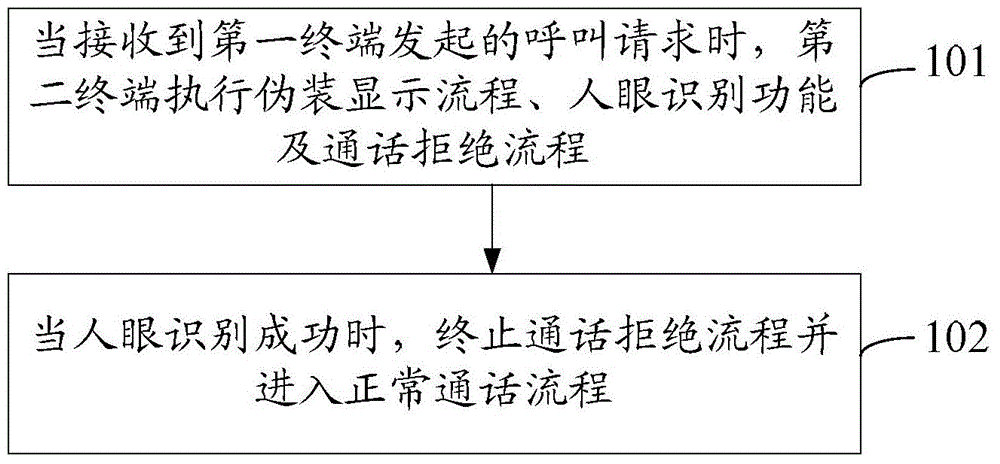
[0064] Embodiment 2 of the present invention provides a call processing method, such as figure 2 As shown, the method includes the following steps:
[0065] Step 201: When receiving a call request initiated by the first terminal, the second terminal executes a masquerade display process, a human eye recognition process, and a call rejection process;
[0066] In this step, the first terminal refers to a terminal included in the preset list of the second terminal; the preset list is used to store information of sensitive contacts, and the information may be identification information used to identify a contact; For example, phone numbers, names of contacts, etc.; therefore, before this step, the second terminal needs to pre-set a preset list, for example, the user of the second terminal can add one or more contacts in the second terminal to Set as a sensitive contact. Therefore, the first terminal is the sensitive contact set for the user of the second terminal.
[0067] Whe...
Embodiment 3
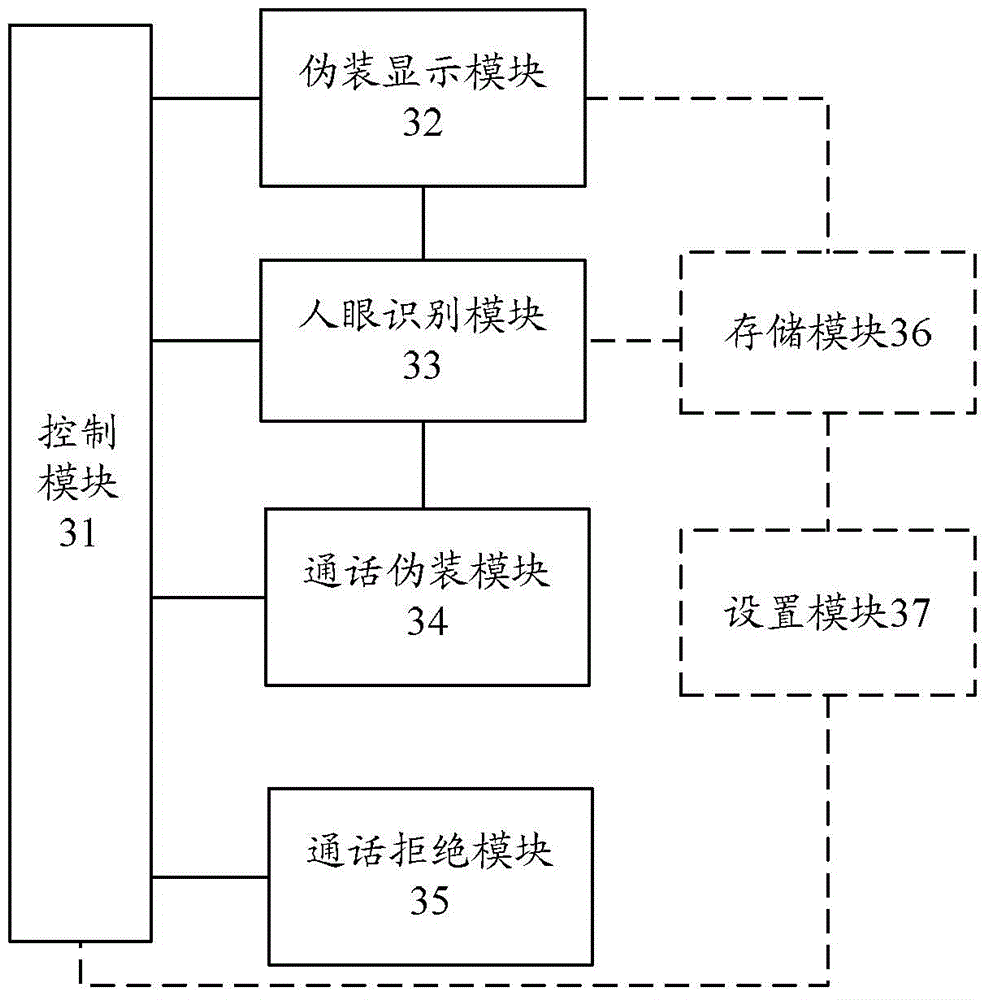
[0078] Embodiment 3 of the present invention provides a call processing device, which is located on the second terminal, such as image 3 As shown, the device includes: a control module 31, a masquerading display module 32, a human eye recognition module 33, a call masquerading module 34, and a call rejection module 35; wherein,
[0079] The control module 31 is configured to trigger the masquerade display module 32 to execute the masquerade display process when receiving the call request initiated by the first terminal, trigger the human eye recognition module 33 to execute the human eye recognition process, and when the human eye recognition fails and the first When the call between the terminal and the second terminal is established, the call masquerading module 34 is triggered to execute the call masquerading process; or,
[0080] The control module 31 is configured to trigger the masquerade display module 32 to execute the masquerade display process, trigger the human eye...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com