A method, device and system for enterprise security management
An enterprise security management and enterprise technology, applied in the field of enterprise security management, can solve the problems of not being able to fully guarantee the security control of mobile terminals, increasing the hidden danger of enterprise information security, and increasing the risk of leaking sensitive information of the enterprise.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
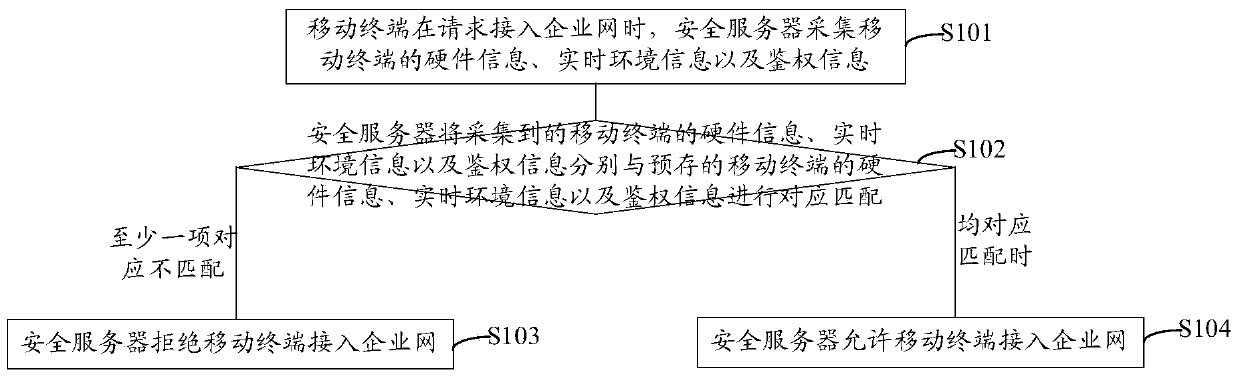
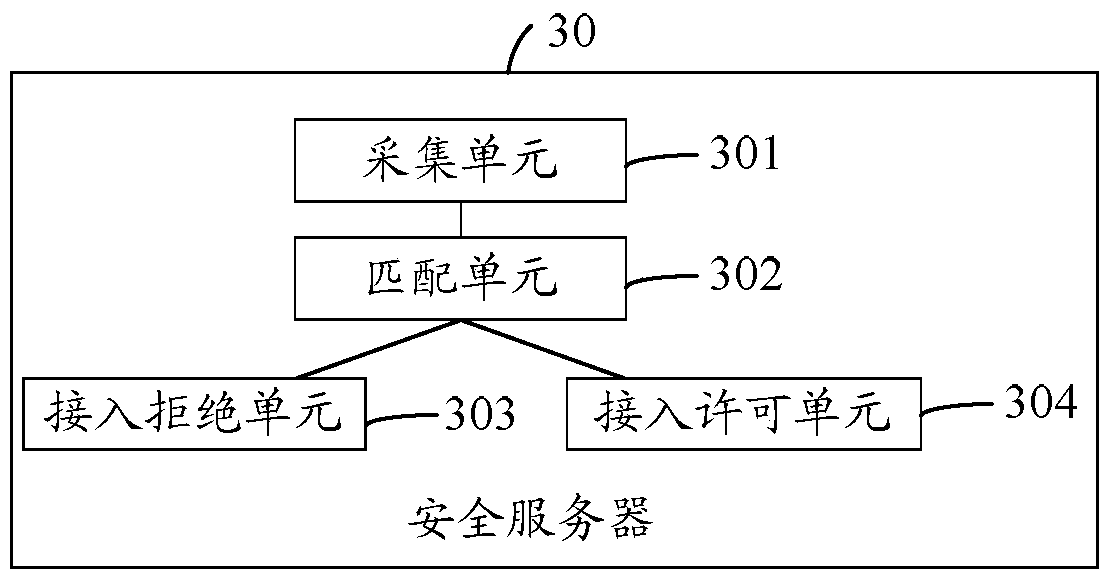
[0049] see figure 1 , which shows an application scenario of the technical solution of the embodiment of the present invention, in which a security server 1 and a mobile terminal 2 for processing enterprise business are included; the basic idea of the embodiment of the present invention is: the security server 1 Combining the unchangeable hardware information of the mobile terminal 2 itself and the current real-time environment information of the mobile terminal 2 to control the access of the mobile terminal 2 for enterprise business processing; The enterprise-related data cached in the business processing process is controlled, so that not only can the security control of the mobile terminal 1 be carried out in an all-round way, reduce the security risks of enterprise infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com