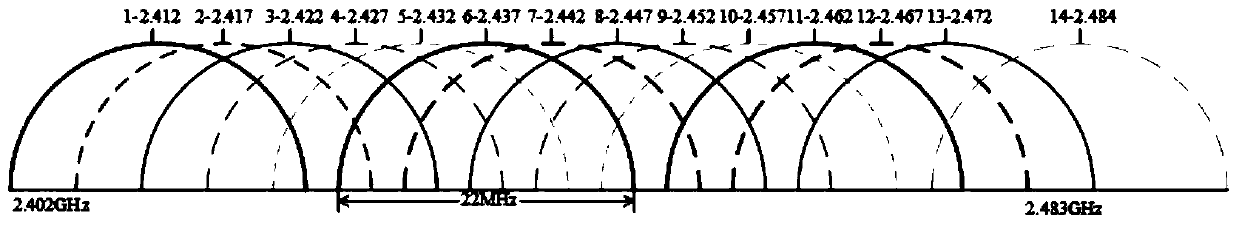
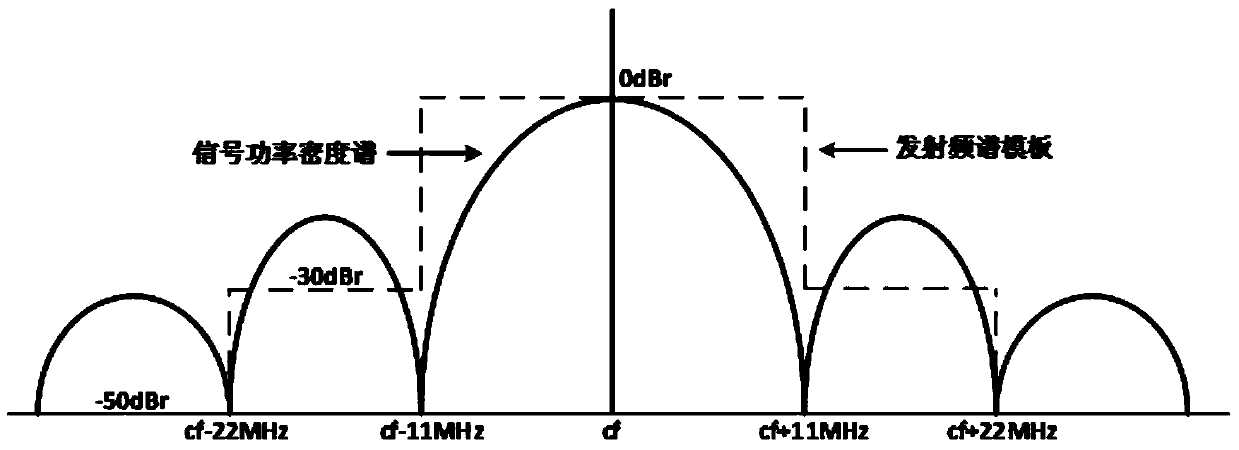
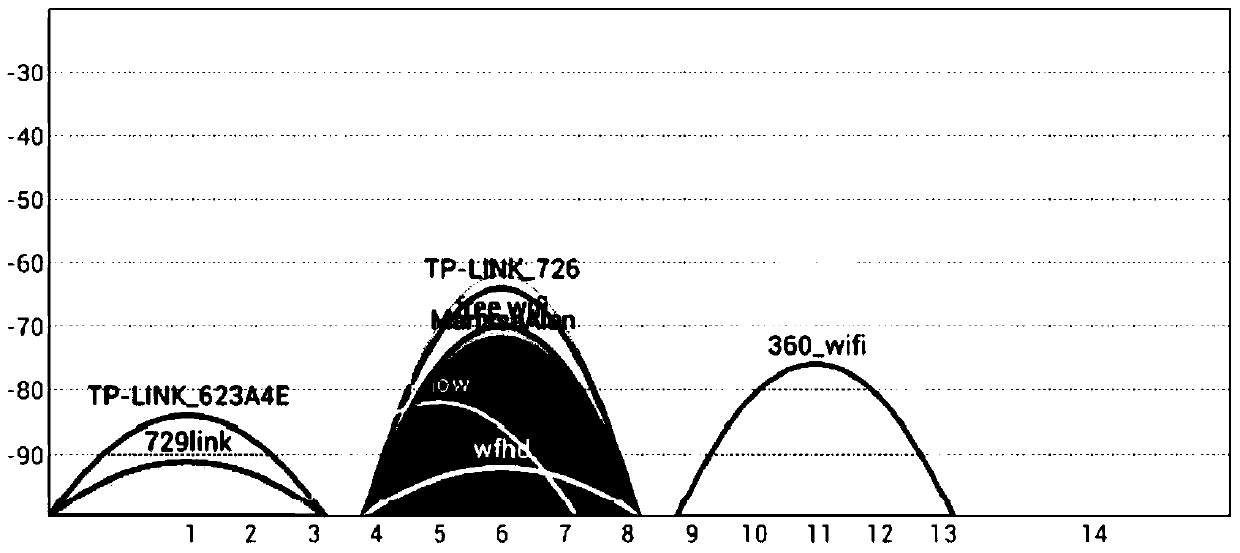
A method of protecting user behavior privacy based on channel interference
A channel interference and channel technology, applied in wireless communication, transmission systems, electrical components, etc., can solve problems such as information theft, and achieve the effect of resisting attackers' behavior of identifying user privacy, protection effectiveness, and good results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] Existing communication systems regard channel interference as harmful and use various techniques to eliminate the interference. The existing research on wireless interference is divided into three categories: the first category is the research on the interference mechanism, this part of the research mainly focuses on the reasons for the interference phenomenon, and provides the basis for the following two types of research; the second type of research is on interference avoidance This part of the research is dedicated to finding an effective interference avoidance method; the third type of research is the research on the coexistence of interference. If the interference cannot be effectively avoided, the interference and the real data communication sender and receiver will have to share Spectrum resources, this part of the research is dedicated to how to improve the communication performance of the transceiver.
[0048] The present invention does the opposite, because th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com