Weblogic deserialization vulnerability scanning detection method and device
A vulnerability scanning and deserialization technology, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve problems such as vulnerability to attacks, and achieve the effect of reducing manual intervention and convenient installation and use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
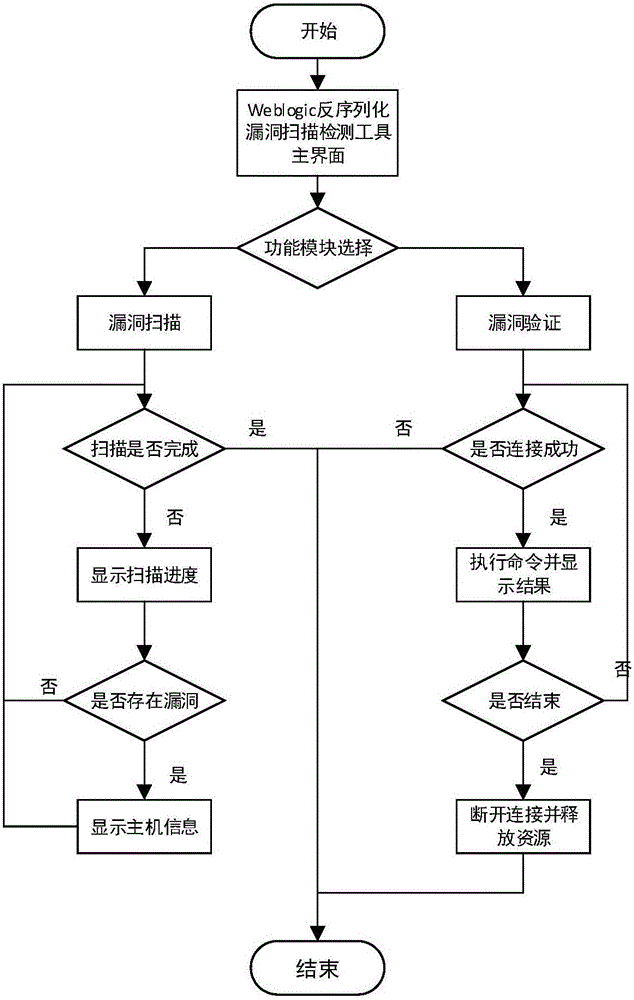
[0098] Such as Figure 1-3 As shown, a Weblogic deserialization vulnerability scanning detection method provided in this embodiment includes the following steps:
[0099] S1: Obtain the document to be detected;
[0100] S2: Start the weblogic deserialization vulnerability scanning detection tool;
[0101] S3: Scan the document to be detected for vulnerabilities;
[0102] S4: Determine whether the document to be detected has a vulnerability, and if so, output the vulnerability information of the host;
[0103] S5: If not, return to the step to continue scanning until the end of scanning.
[0104] Also includes the following steps:
[0105] S61: Perform vulnerability verification on the document to be detected;
[0106] S62: judging whether the document to be detected is connected successfully, if not, then end;
[0107] S63: if successful, execute the command and display the result;
[0108] S64: judge whether to end the verification process, if not, return to the step t...
Embodiment 2
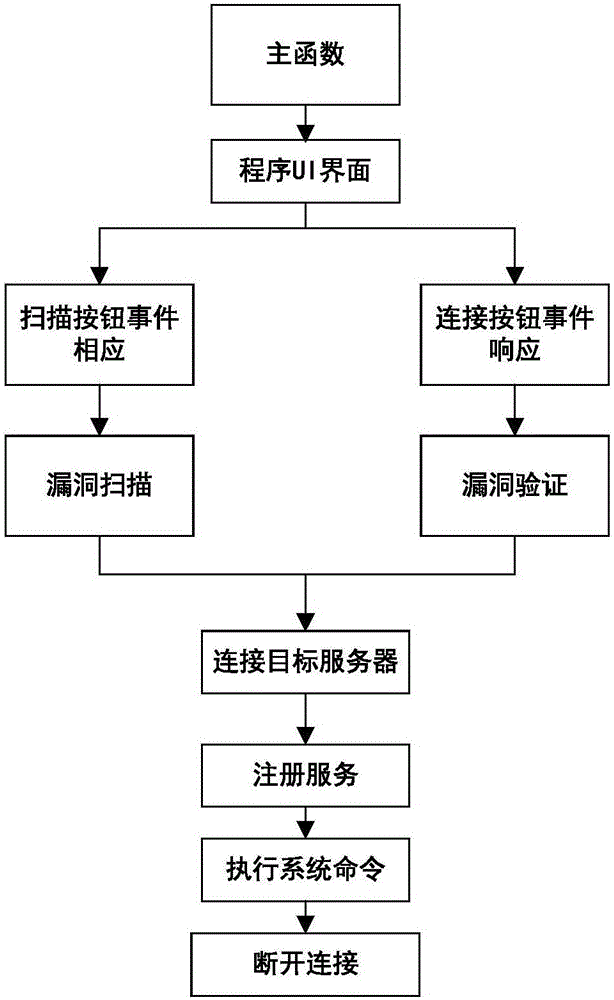
[0180] Such as figure 2 As shown, the Weblogic deserialization vulnerability scanning detection method provided in this embodiment is used for vulnerability scanning and vulnerability verification: firstly call the main function and entry point of the Weblogic deserialization vulnerability scanning detection tool program; then initialize the Weblogic deserialization vulnerability scanning The main interface of the detection tool; generate the button on the main interface of the Weblogic deserialization vulnerability scanning detection tool; select the thread of the vulnerability scanning module, or select the thread of the vulnerability verification module; connect to the server and register the function; execute the command function; finally release the connection function. Weblogic deserialization vulnerability scanning detection supports multi-host address and multi-port vulnerability scanning. Friendly interface, low requirements for personnel ability, suitable for any pe...
Embodiment 3
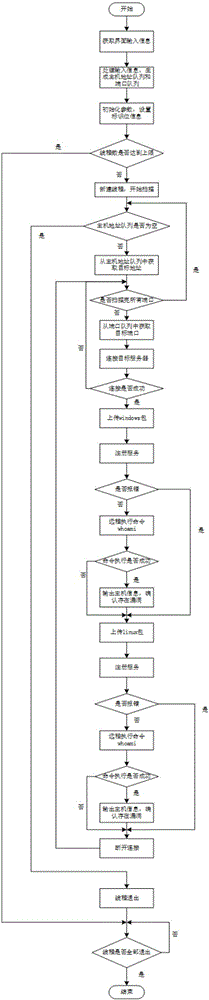
[0204] In this embodiment, a tool generated by Weblogic deserialization vulnerability scanning detection scans a target server as an example for illustration.
[0205] 1. Vulnerability scanning
[0206] (1) Double-click "run.bat" to start the self-developed weblogic_unserialize_tool tool and select the "Vulnerability Scanning" module;
[0207] (2) Enter the scanning address range and port range, and set the scanning thread, for example: the address range is "192.168.56.101,192.168.56.102", the port range is "7000-7010", and the thread is set to 5;
[0208] (3) Click the "Scan" button to scan, and the tool will display the scanning progress and the host information with vulnerabilities;
[0209] 2. Vulnerability verification
[0210] (1) Select the "vulnerability verification" module, enter the target host information, and select the operating system, for example: the target host IP is "192.168.56.102", the port is "7001", and the operating system is "Windows";
[0211] (2) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com