Method for carrying out security management on security element and communication system
A security unit and security management technology, applied in wireless communications, security devices, electrical components, etc., can solve problems such as high error probability, sneak traffic, and inability to achieve smooth user experience, reducing network communication and ensuring security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
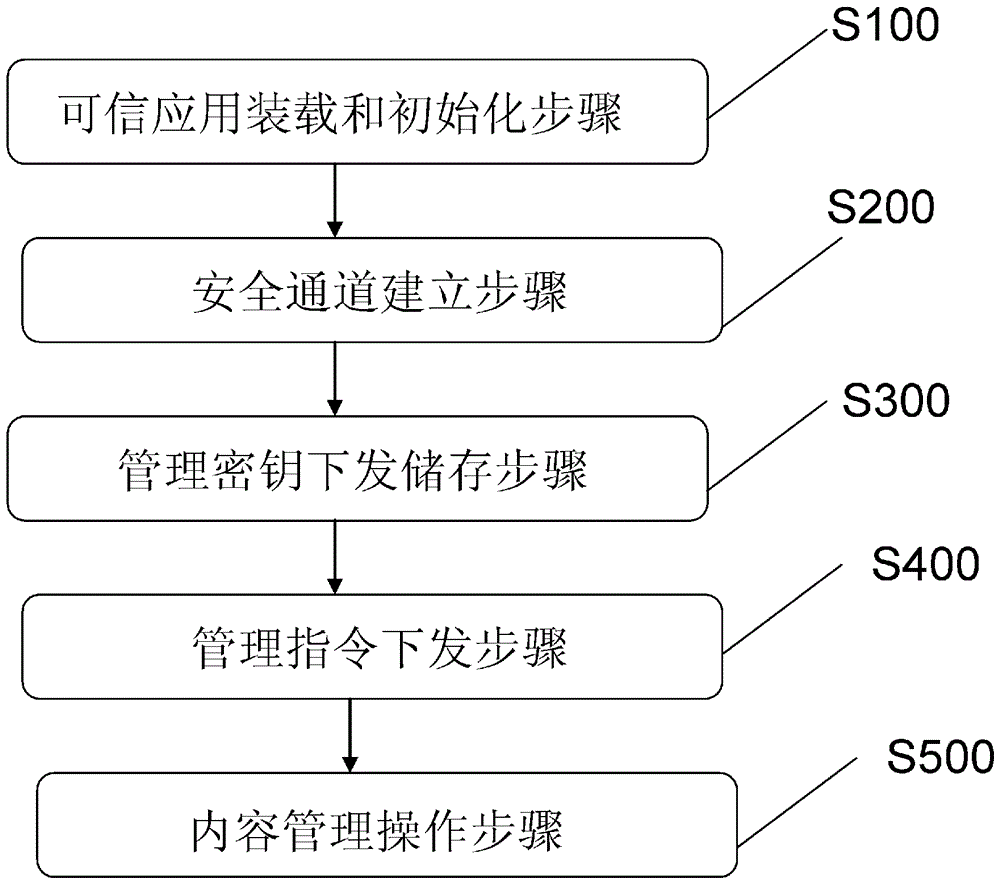
[0031] Introduced below are some of the various embodiments of the invention, intended to provide a basic understanding of the invention. It is not intended to identify key or critical elements of the invention or to delineate the scope of protection.
[0032] The purpose of the present invention is to solve the problem that the content management of the security unit must be connected to the Internet in real time. The present invention can realize that the user only needs to connect to the network once to perform unlimited content management operations on the terminal device on the basis of ensuring security. This can reduce network communication with the trusted server management server, and there is no need for the trusted service management server to issue specific content management instructions except for necessary state synchronization.
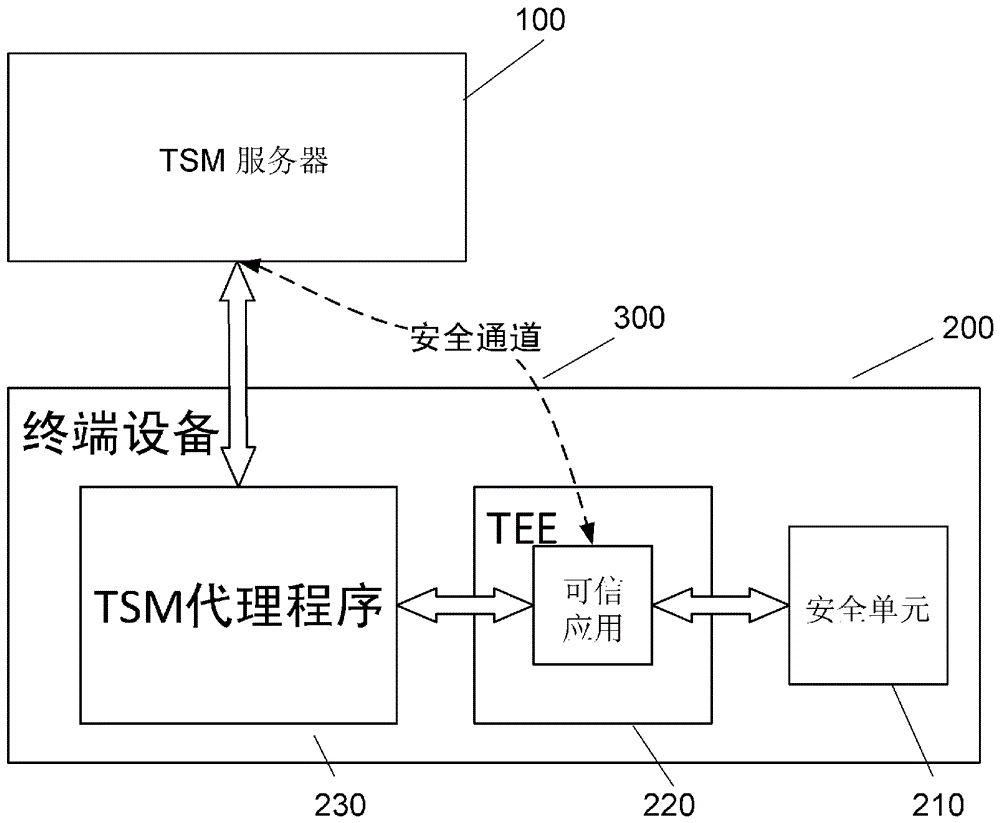
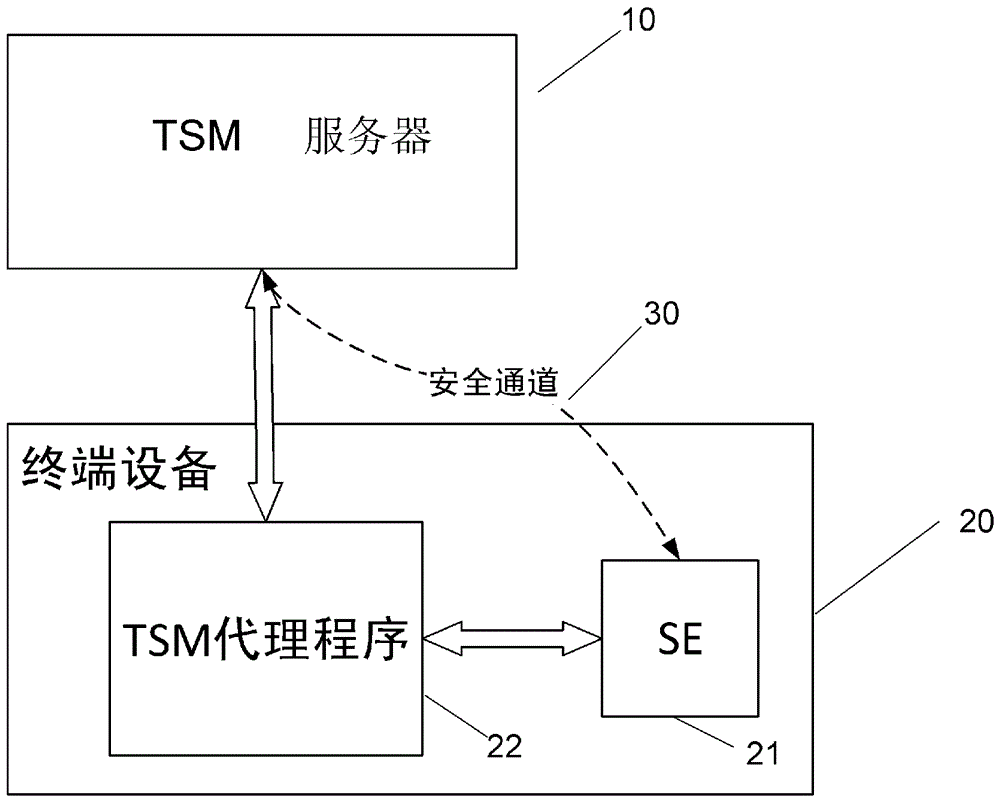
[0033] figure 2 A communication system for content management of a security unit of the present invention is illustrated.
[0034]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com