A realization method of finger vein fusion fuzzy treasury
A technology of fuzzy treasury and implementation method, applied in the field of cryptography and biometric identification, to achieve the effect of increasing the number, high implementation efficiency, and strong security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below with reference to the accompanying drawings.
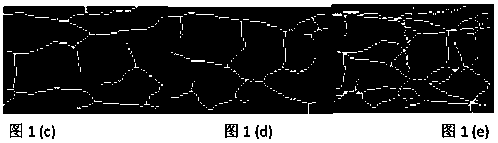
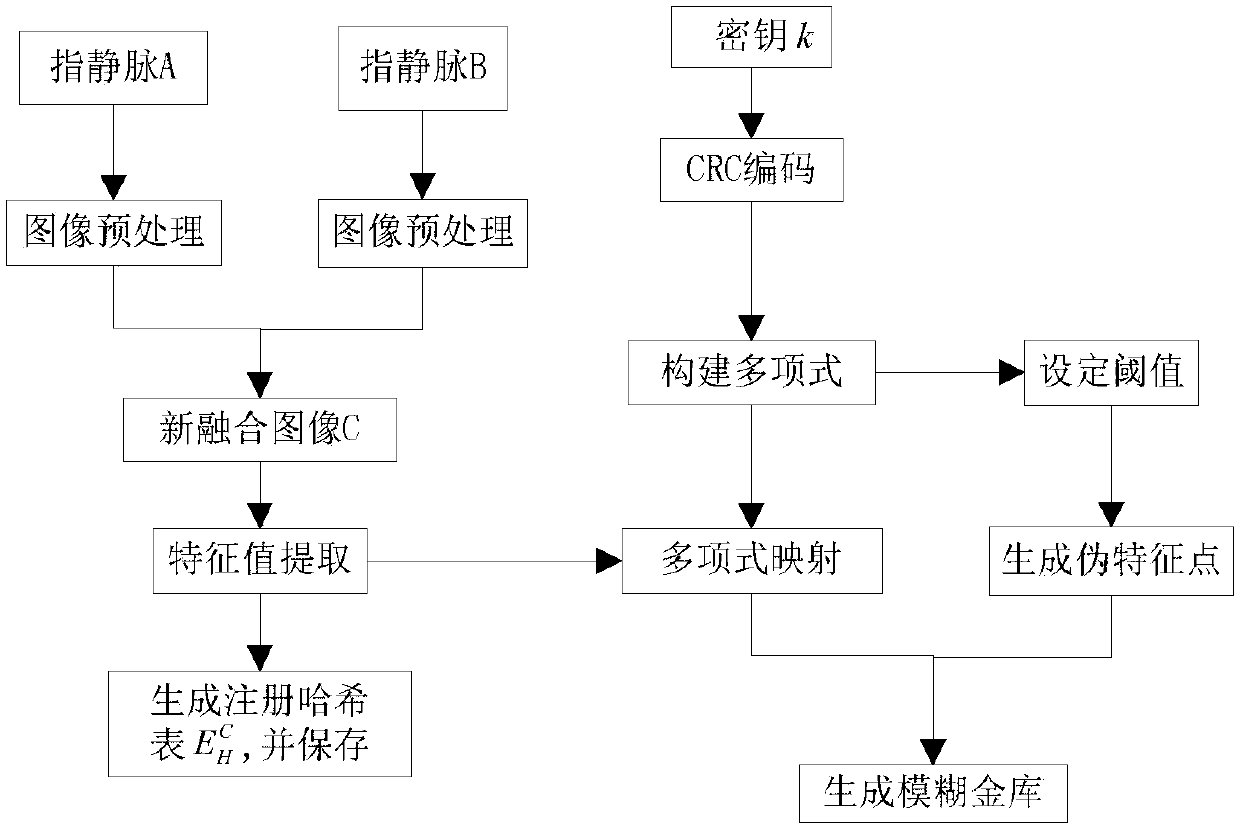
[0038] A method for realizing a finger vein fusion fuzzy vault mainly includes three parts: the first step is to fuse the finger vein skeleton information on the finger vein A and the finger vein B images to obtain the vein skeleton image C, and extract the feature points to obtain a feature information set And extract its characteristic information set. The second step is to use the locking algorithm to bind the key to be protected with the feature set in the first step to generate a finger vein fusion fuzzy vault. The third step is to use the verified query finger veins A' and B' to fuse the finger vein skeleton information to obtain the vein skeleton image C', extract the feature information, and use the unlocking algorithm to extract the key from the finger vein fuzzy vault.
[0039] The described fusion of the finger vein skeleton information on the finger vein A a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com