Multi-factor user authentication method capable of flexible configuration
A technology of user authentication and authentication method, which is applied in the field of information security, can solve problems such as no longer meeting security requirements, and achieve the effect of preventing users from violent cracking and facilitating expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
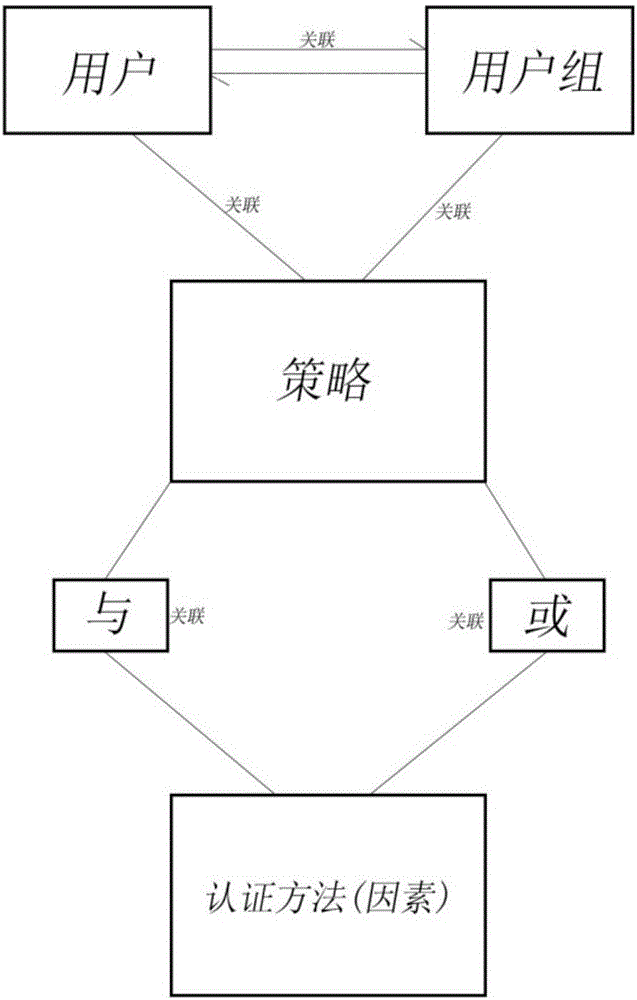
[0030] Such as figure 1 , users can belong to a group or be independent. The advantage of belonging to a group is that when a group is associated with a policy, all users under the group will inherit the group's policy.
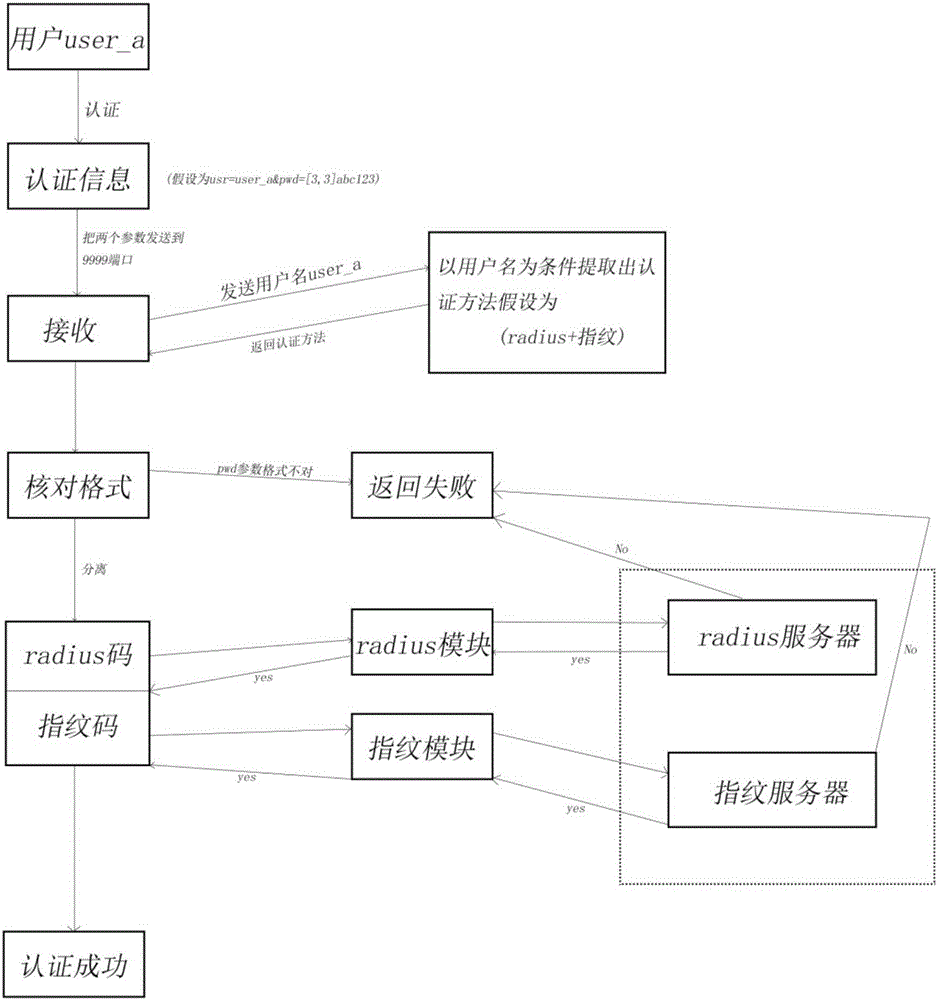
[0031] Assume that user user_a is associated with policy A, and policy A contains two authentication methods (both two-factor authentication) radius+fingerprint. The user enters the user name user_a on the website, the radius code is abc, and then presses the fingerprint device, assuming that the fingerprint device reads that the user's fingerprint code is 123.
[0032] Then submit to the background web server through the web form and then get usr=user_a&pwd=[3,3]abc123 from the combination of the web server and send it to the port 9999 of the MFA server (combined with figure 2 ). When the MFA receives the data, it will first parse out the usr parameter and use this as a condition to find out the policy associated with the user_a user ( figure 1 The assoc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com