Method and system for improving data transmission security
A technology for data transmission and security, applied in the field of network communication, can solve the problems of low security, easy cracking of data transmission methods, security loopholes, etc., to achieve the effect of improving security, ensuring security and effectiveness, and increasing the degree of protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
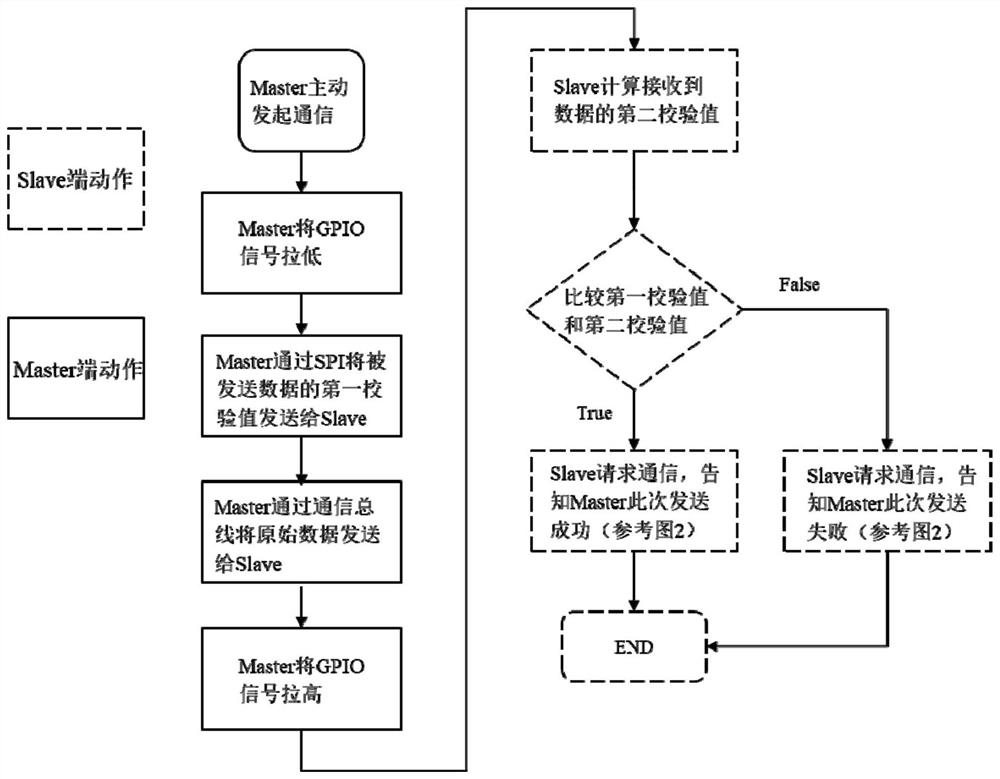
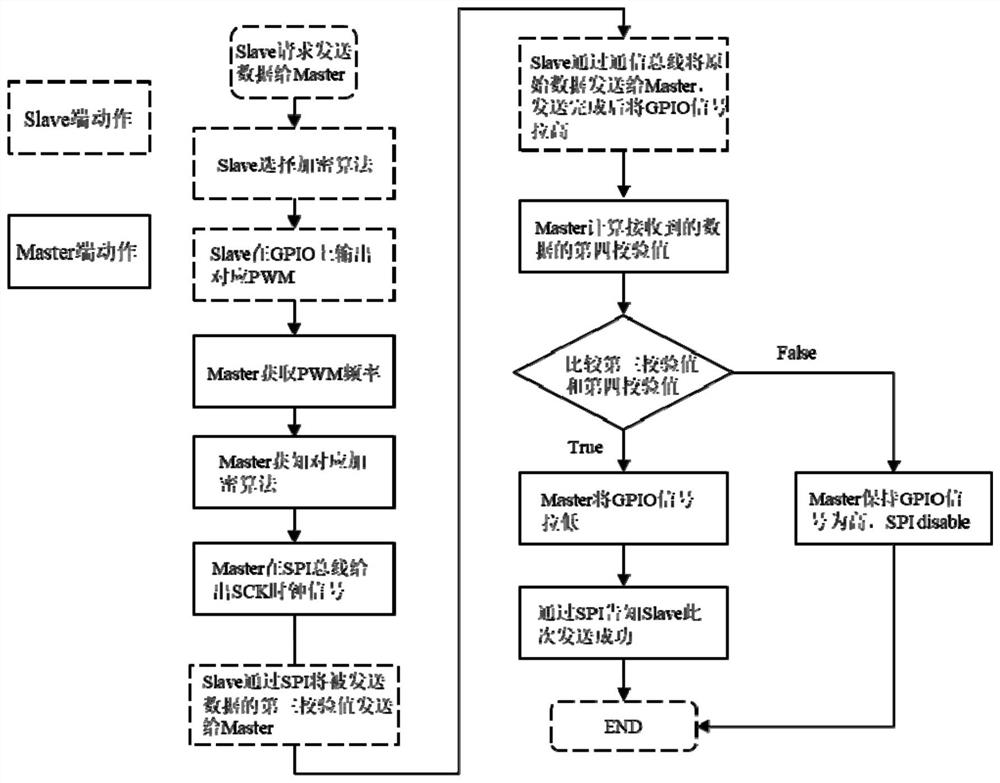
[0048] like figure 1 with figure 2 , The present embodiment discloses a method for improving the security of data transmission, comprising:
[0049] S100: The Master and Slave terminal end connected via a data communication bus and GPIO (General Purpose Input Output Interface), SPI bus (full-duplex synchronous serial bus);
[0050] SPI communication is a full duplex communication mode, the transmission rate is 10Mbps general application, SPI bus includes four signal lines, particularly for the MOSI (master out / slave input data lines), the MISO (Master In / Slave Out data line), the SCK (serial clock line) and CS (from the enable signal line device, chip select), an end of the communication master device must be set to both, from one end of the device, a master device from a plurality of devices can be docked, a plurality of slave devices can share the MOSI, MISO, SCK, but each CS pin is different from the device; All operations must be initiated by the master device, the master ...
Embodiment 2
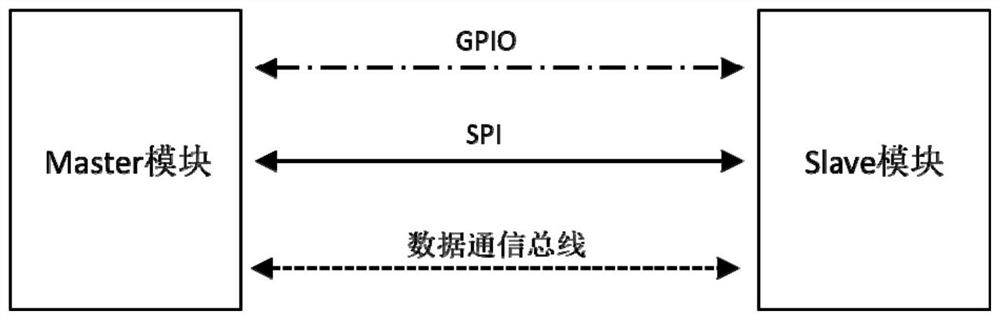
[0085] like image 3 Shown, for improving the security of the data transmission system, comprising a module Master, Slave module, the GPIO (general purpose input output interface), the SPI bus (full-duplex synchronous serial bus) and the data communications bus; Master and Slave Modules module GPIO, SPI bus and data communication bus.
[0086]Means for Master Master initiates communication terminal, carries out the following operations:
[0087] The Master side down GPIO signal, sent via the MOSI SPI bus to a first check value Slave module, transmits data via a data communication bus to the interaction module and pulled Slave Master terminal GPIO signal;
[0088] Master module is further configured to, when an encryption algorithm to obtain Slave client request to initiate a communication calculating frequency based on the PWM signal received index number, and the clock signal SCK sent on SPI bus; Master index number corresponding to the terminal according to the encryption algorit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com