A login control method and device capable of preventing violent cracking
A control method and anti-violence technology, applied in the field of anti-violence cracking login control method and device, can solve problems such as poor user experience, increased user authentication, and high complexity, so as to improve user experience, prevent brute force cracking, and prevent login The effect of the attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
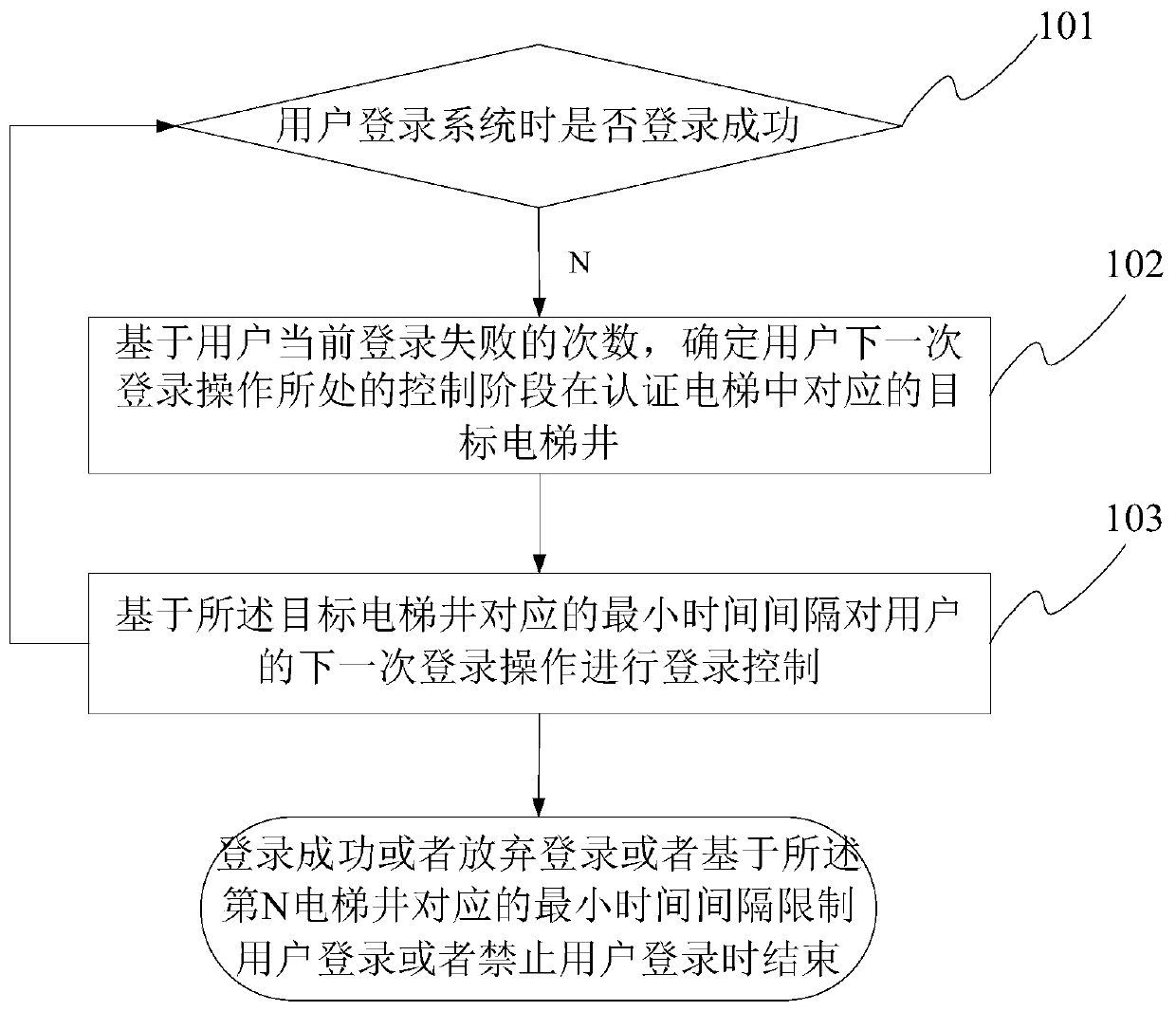
[0069] refer to figure 1 , is a schematic flowchart of the login control method for preventing brute force cracking provided in Embodiment 1 of the present application, as shown in figure 1 As shown, the login control method for preventing brute force cracking includes the following steps:
[0070] Step 101, judging whether the user logs in to the system successfully or not.
[0071] In this application, the user is a general term for users who normally use systems such as the Industrial Internet, Information Internet, and Telecommunications Internet, and users who perform brute force cracking on the login authentication and authorization systems of these systems.
[0072] When users log in to systems such as the Industrial Internet, Information Internet, and Telecom Internet, in order to prevent their login authentication and authorization systems from being brute force cracked, and thus prevent systems such as the Industrial Internet, Information Internet, and Telecom Inter...
Embodiment 2
[0090] In Embodiment 2 of the present application, the login control method for preventing brute force cracking may further include the following processing steps:
[0091] When the user fails to log in for the first time, record the user information and / or user client information, so that when it is necessary to restrict or prohibit the user from logging in later, based on the recorded user information and / or user client information, restrict or Prohibit users and / or user clients from logging into the system.
[0092] For example and not limitation, the user information may be a user account, and the user client information may be an IP (Internet Protocol Address, Internet Protocol Address) of the user client.
[0093] When the user fails to log in for the first time, user information and / or user client information can be recorded, such as user account number and / or user client IP, etc. Based on the recorded user information and / or user client information, restrict / prohibit ...
Embodiment 3
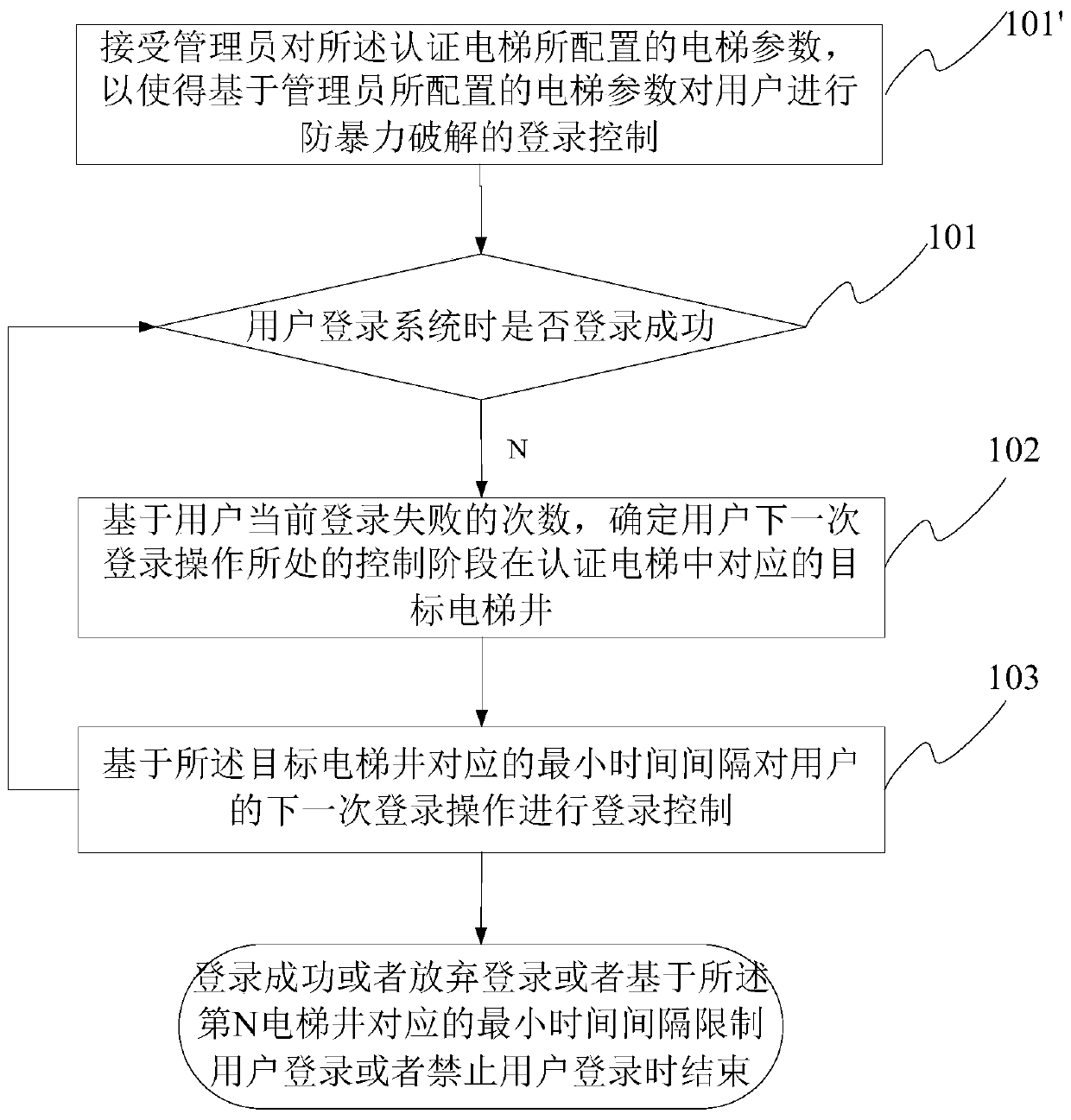
[0096] refer to image 3 Shown is a schematic flowchart of a login control method for preventing brute force cracking. In Embodiment 3 of the present application, the login control method for preventing brute force cracking may further include the following steps:
[0097] Step 101', accepting the elevator parameters configured by the administrator for the authenticated elevator, so that based on the elevator parameters configured by the administrator, the login control of preventing brute force cracking is performed on the user;
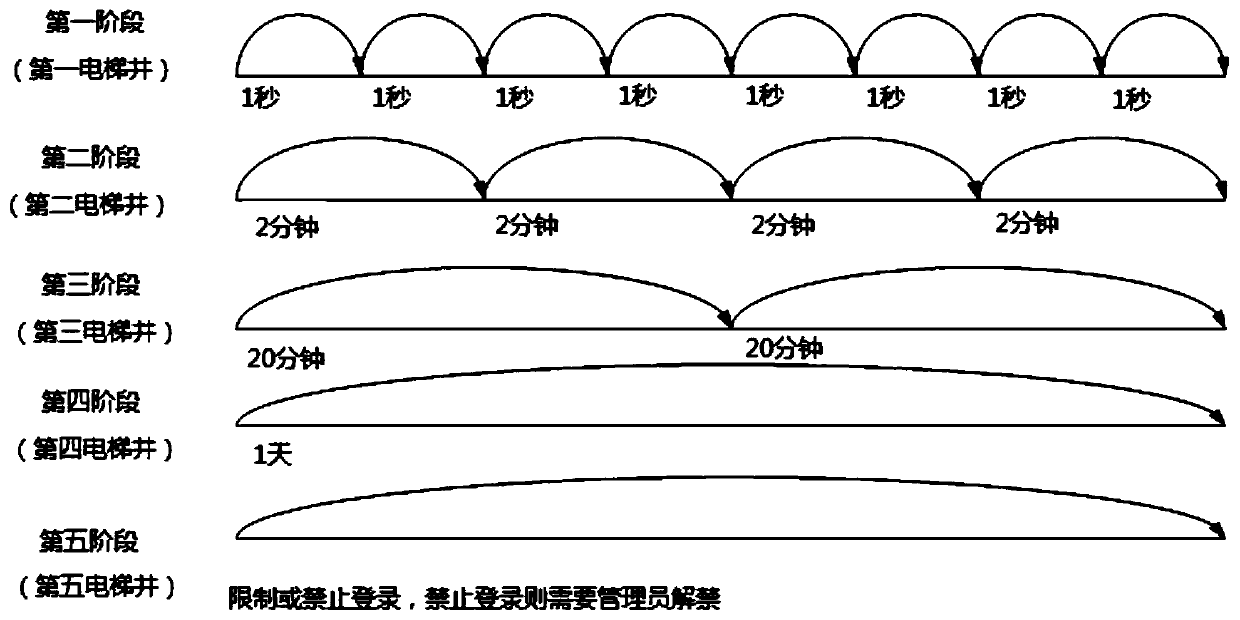
[0098] Wherein, the elevator parameters include at least one of the following parameters:
[0099] The number of elevator shafts, the number of login failures corresponding to each elevator shaft, and the minimum time interval allowed for re-login after login failures corresponding to each elevator shaft.
[0100] In this application, various elevator parameters such as the number of elevator shafts corresponding to the authenticated elevator, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com