Application traffic analyzing method and device
A technology for application traffic and analysis methods, applied in the field of application traffic analysis methods and devices, can solve problems such as inability to analyze the macroscopic analysis of the same type of pages or modules, and achieve the effect of strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
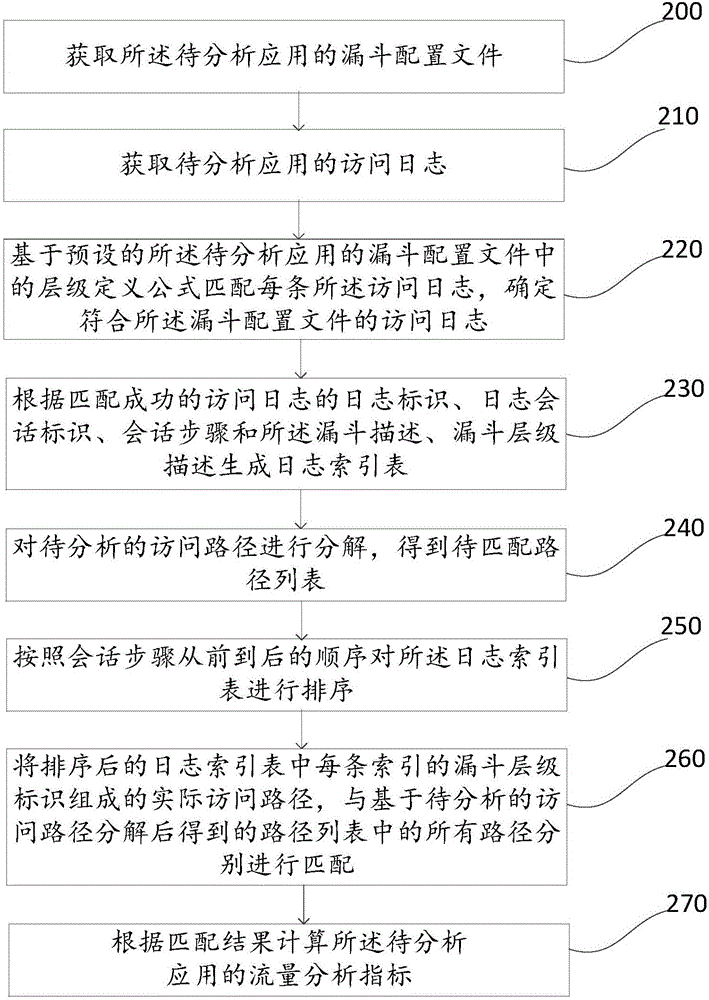
[0027] An application traffic analysis method disclosed in this application, such as figure 1 As shown, the method includes: Step 100 to Step 130.
[0028] Step 100, obtaining the access log of the application to be analyzed.
[0029] The log data of the application is stored in the distributed file system, and the log system will collect the log data of the application, and the log data includes logs of all users accessing the application. The log data usually includes: user identification (id), application identification, analysis object identification, access time of the analysis object, and the upstream and downstream relationship of the accessed analysis object (ie, the jump relationship of the page or module), etc. Then, the log system extracts the log data of each session belonging to a certain user from the log data of the application to be analyzed according to preset rules, and generates a session-related access log. Wherein, the access log of a session of a certai...
Embodiment 2
[0042] An application traffic analysis method disclosed in this application, such as figure 2 As shown, the method includes: Step 200 to Step 270.
[0043] Step 200, acquiring the funnel configuration file of the application to be analyzed.
[0044] During specific implementation, maintenance personnel or business personnel configure the configuration file of the funnel of the application through a preset graphical user interface. Funnel refers to the user conversion rate model between different steps in the application process, which is used to analyze the depth of user access to the application and the efficiency of each step. target efficiency. Obtaining the funnel configuration file of the application to be analyzed includes: obtaining a funnel description and a funnel level description of the application to be analyzed configured through a graphical user interface, wherein the funnel level description includes at least: a funnel level identifier, the The analysis obje...
Embodiment 3
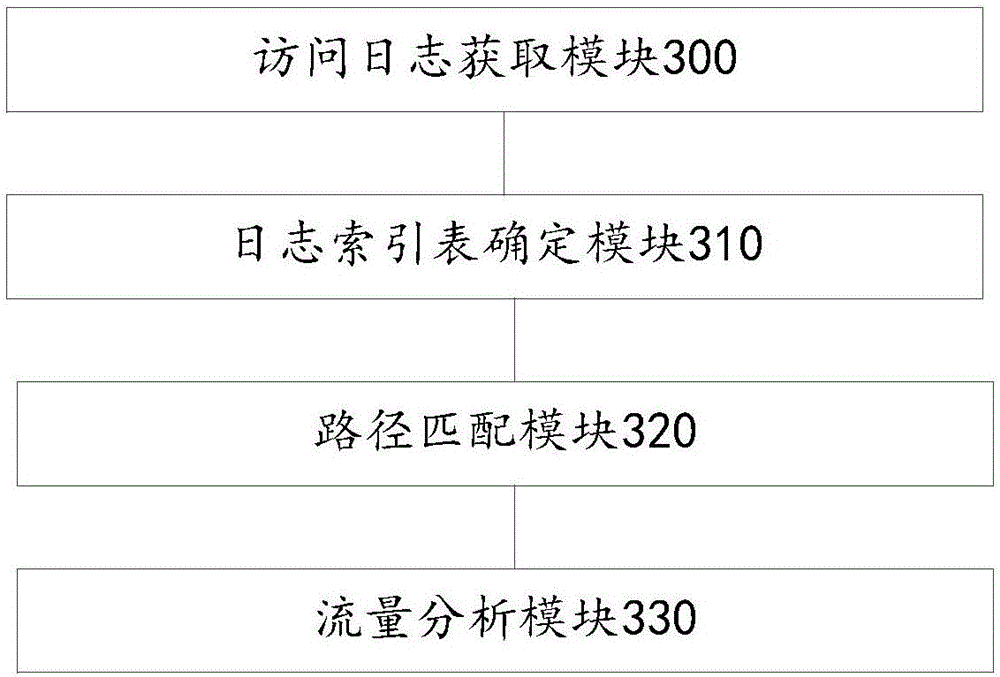
[0080] Correspondingly, an application flow analysis device disclosed in this application, such as image 3 As shown, the device includes:
[0081] An access log acquisition module 300, configured to acquire an access log of the application to be analyzed;
[0082] The log index table determination module 310 is configured to match each of the access logs obtained by the access log acquisition module 300 based on the preset funnel configuration file of the application to be analyzed, and determine the value of the access log conforming to the funnel configuration file. log index table;
[0083] The path matching module 320 is configured to match the actual access path determined according to the log index table based on the path list obtained after decomposing the access path to be analyzed;
[0084] A traffic analysis module 330, configured to calculate a traffic analysis index of the application to be analyzed according to the matching result of the path matching module 32...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com