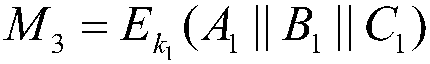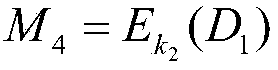Ownership Transfer Method of Radio Frequency Identification Tags Based on Quadratic Residue
A radio frequency identification tag and secondary residual technology, applied in the field of communication and information security, can solve problems such as not supporting mobile readers, delaying protocol authentication time, increasing tag cost, etc., to overcome high cost, poor flexibility, and convenience The effect of management and maintenance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
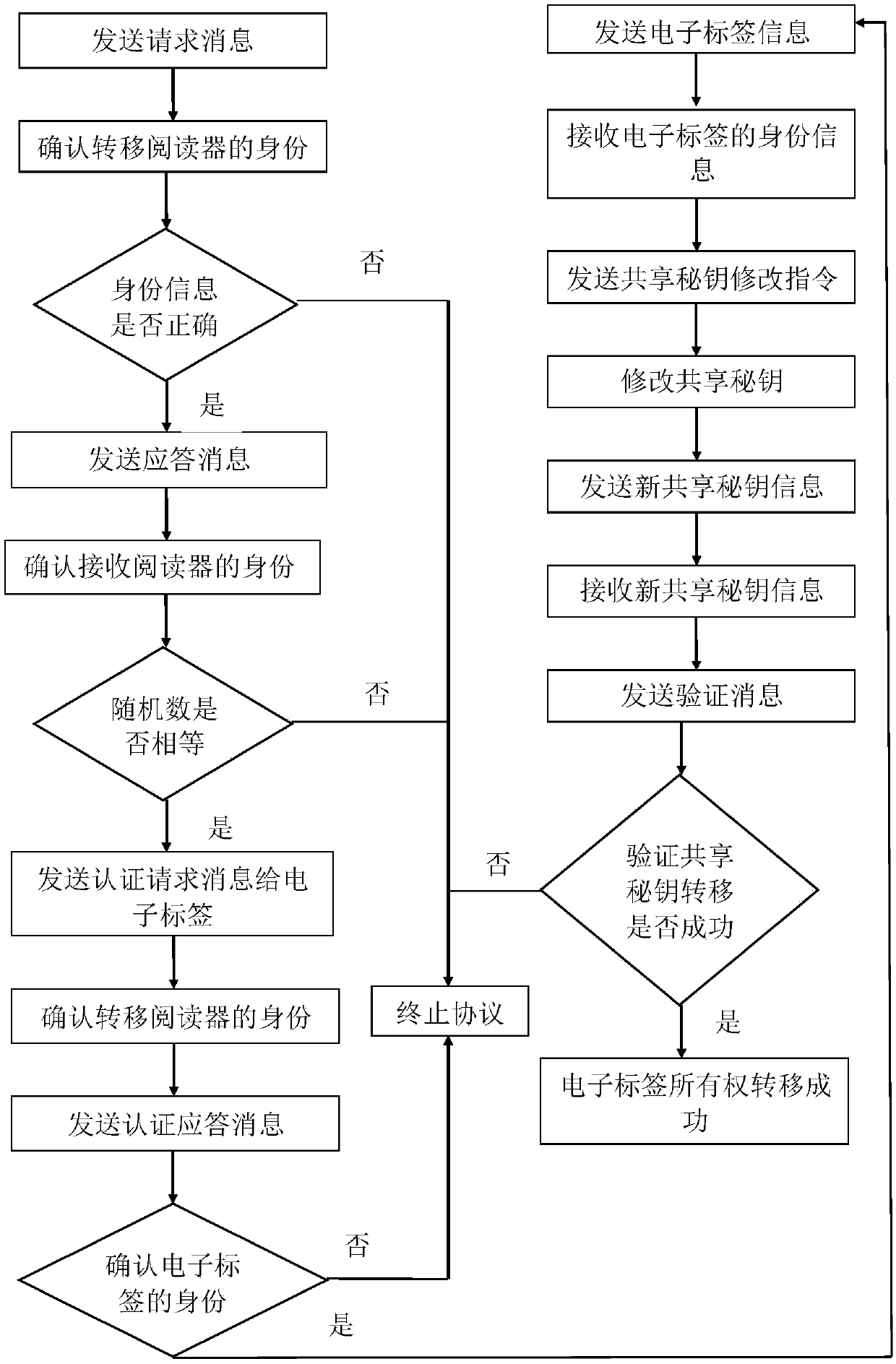
[0073] Attached below figure 1 , to further describe the specific steps of the present invention.
[0074] Step 1, send a request message.
[0075] The transfer reader generates a random number N 1 .
[0076] The transferring reader queries the identity information of the receiving reader from the database.
[0077] Using the modulus formula of the quadratic remainder, calculate the modulus of the identity information of the receiving reader and the random number generated by the transferring reader, and obtain the encrypted request message.
[0078] The modulo formula of the quadratic remainder is as follows:
[0079] m 1 =(A||B) 2 mod n 1
[0080] Among them, M 1 Indicates the encrypted message, A indicates the identity information of the receiving reader, || indicates the message cascade operation, B indicates the random number generated by the transfer reader, (·) 2 Represents square operation, mod represents modulo operation, n 1 Indicates the public key of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com