Authentication method for cloud-based low-cost radio frequency identification ntru
A radio frequency identification and authentication method technology, which is applied in the field of cloud-based low-cost radio frequency identification NTRU authentication, can solve the problems of high label calculation complexity, insecurity, and impact on applications, so as to improve deployment and management costs and simplify the authentication process , the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
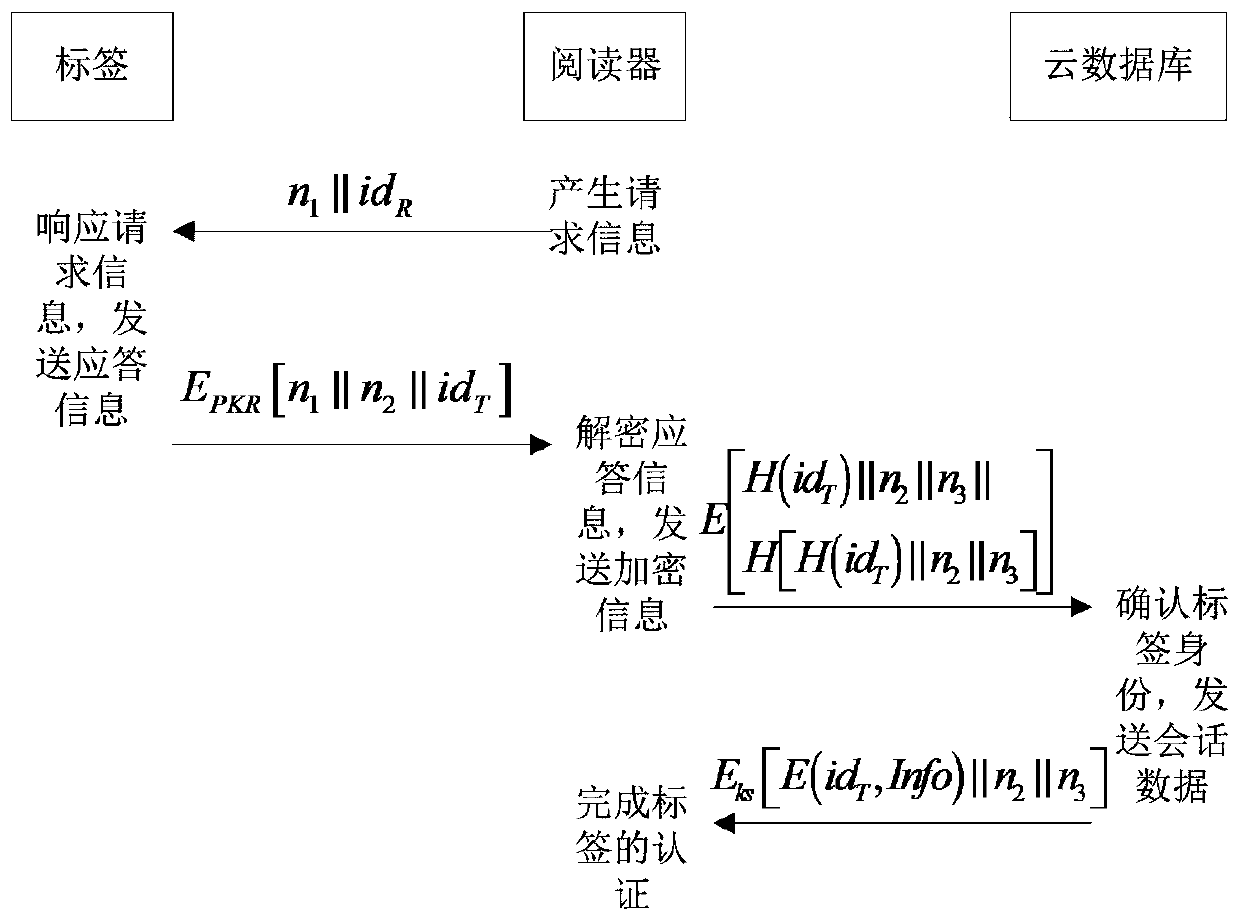
[0037] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0038] Step 1, the reader sends request information to the tag.
[0039] (1a) The reader generates the random number n of the first reader 1 .
[0040] (1b) The reader assigns its identity id R and the first reader random number n 1 Sent to the tag as request information.
[0041] Step 2, the tag responds to the request information, and then sends the response information to the reader.
[0042] (2a) The tag is received by the reader identity id R Find the reader id inside the tag R Corresponding public key PK R Whether it exists, if so, then execute step (2b), otherwise the communication ends.
[0043] (2b) Tag generates tag random number n 2 .
[0044] (2c) The tag passes the reader's identity id R Corresponding public key PK R , for the first reader random number n 1 , label random number n 2 and tag identity id T Encrypt to get the response...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com