Abnormal access log mining method based on website picture and apparatus thereof
A log and website technology, applied in the field of abnormal access log mining based on website portraits, can solve problems such as low efficiency and unrecognizable problems, and achieve high processing efficiency and high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
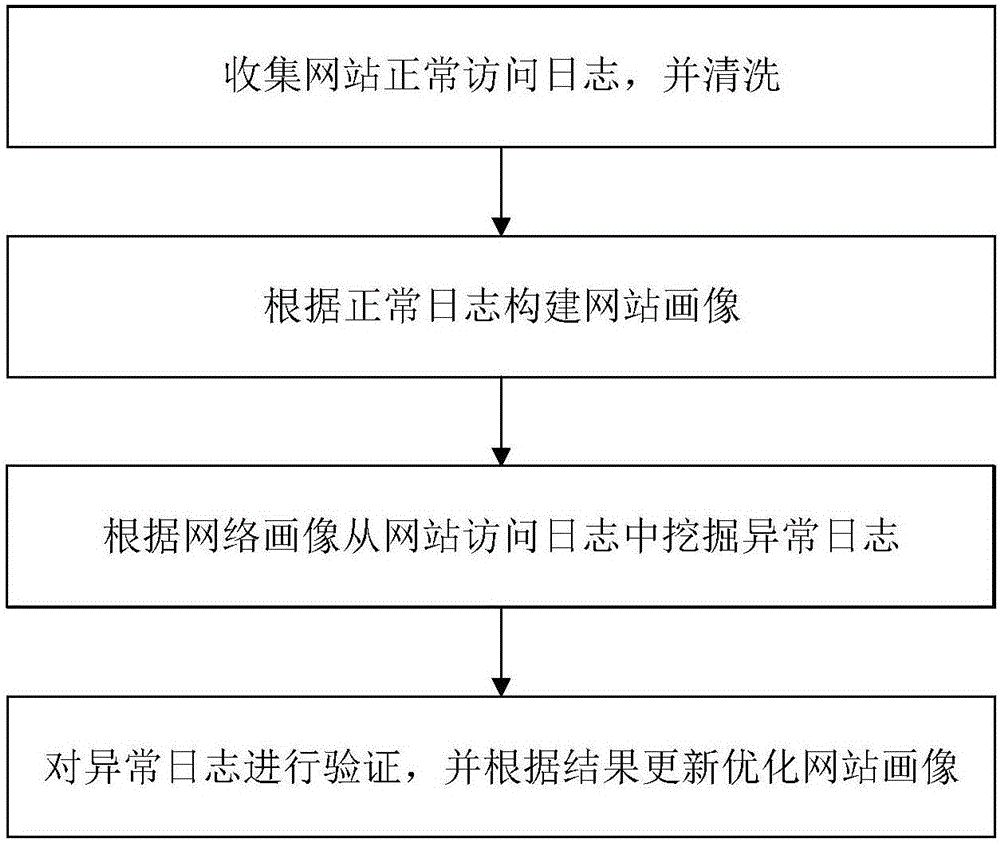
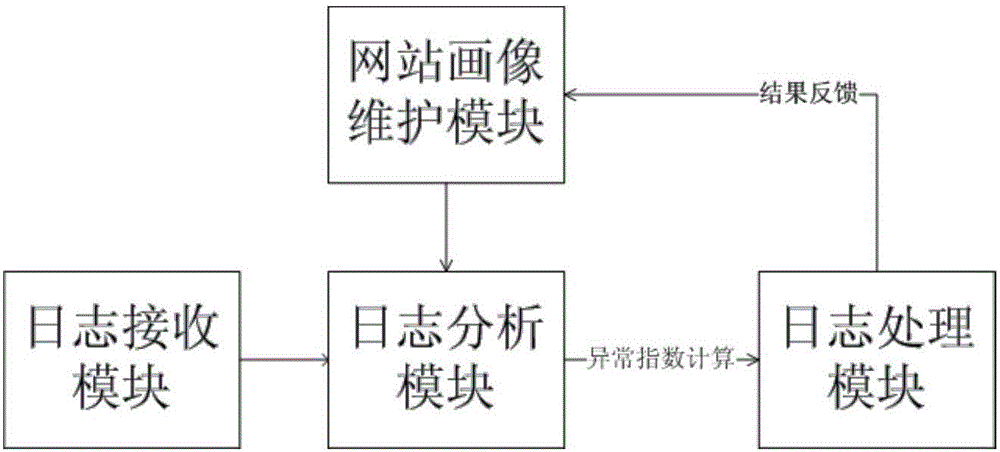
[0021] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. The present invention describes website visits by constructing a website portrait of the target website (a multi-dimensional tagged portrait model that describes website features abstracted based on information such as the directory structure of the website, dynamic and static page distribution, and page parameter types). If it exceeds the normal range of the website profile, it can be considered as an abnormal log. Then verify the exception log, feedback and study the verification results, and update the website portrait.
[0022] like figure 1 As shown, the specific description is as follows:
[0023] Step 1: Collect the access logs of the target website within a certain period from the website server or CDN node, clean the access logs, and obtain normal access logs.
[0024] Step 2: Build a website portrait of the target website b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com