A method for distributing private network user numbers based on call forwarding service
A technology of call forwarding and user number, applied in communication supplementary services, network data management, electrical components, etc., can solve the problems of number segment or number leakage, number leakage, security threats, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
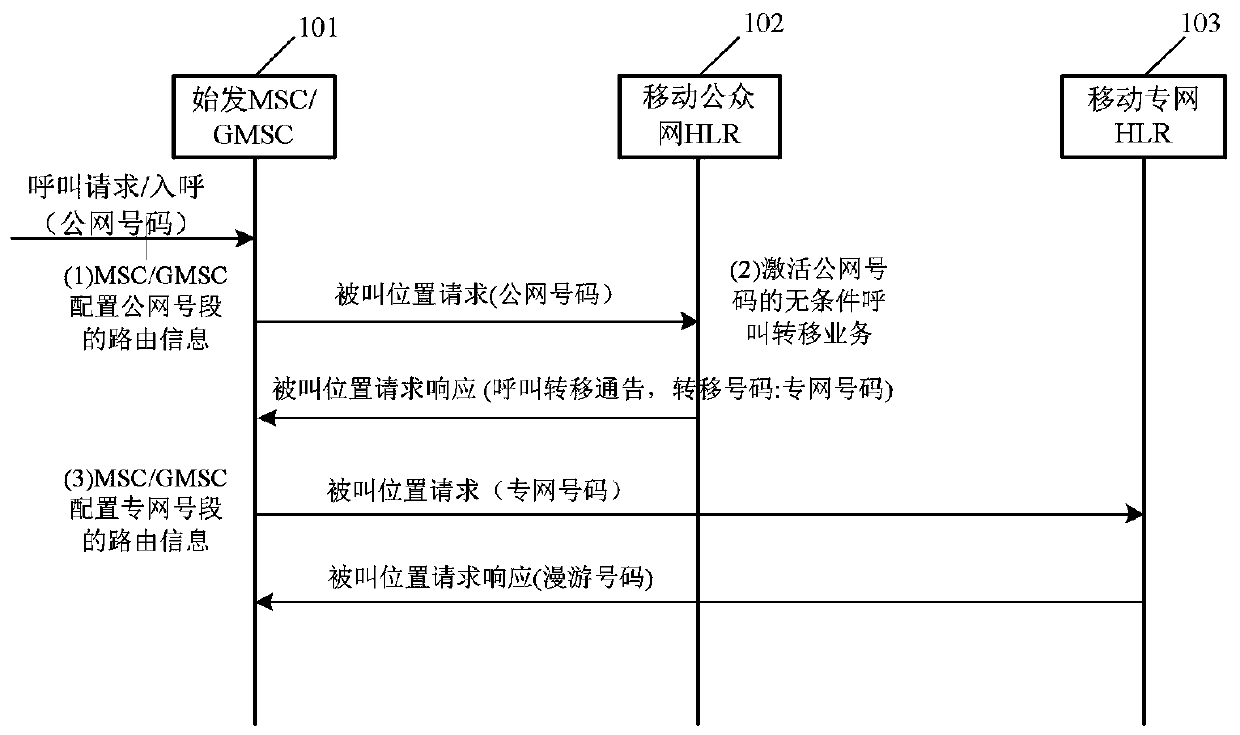
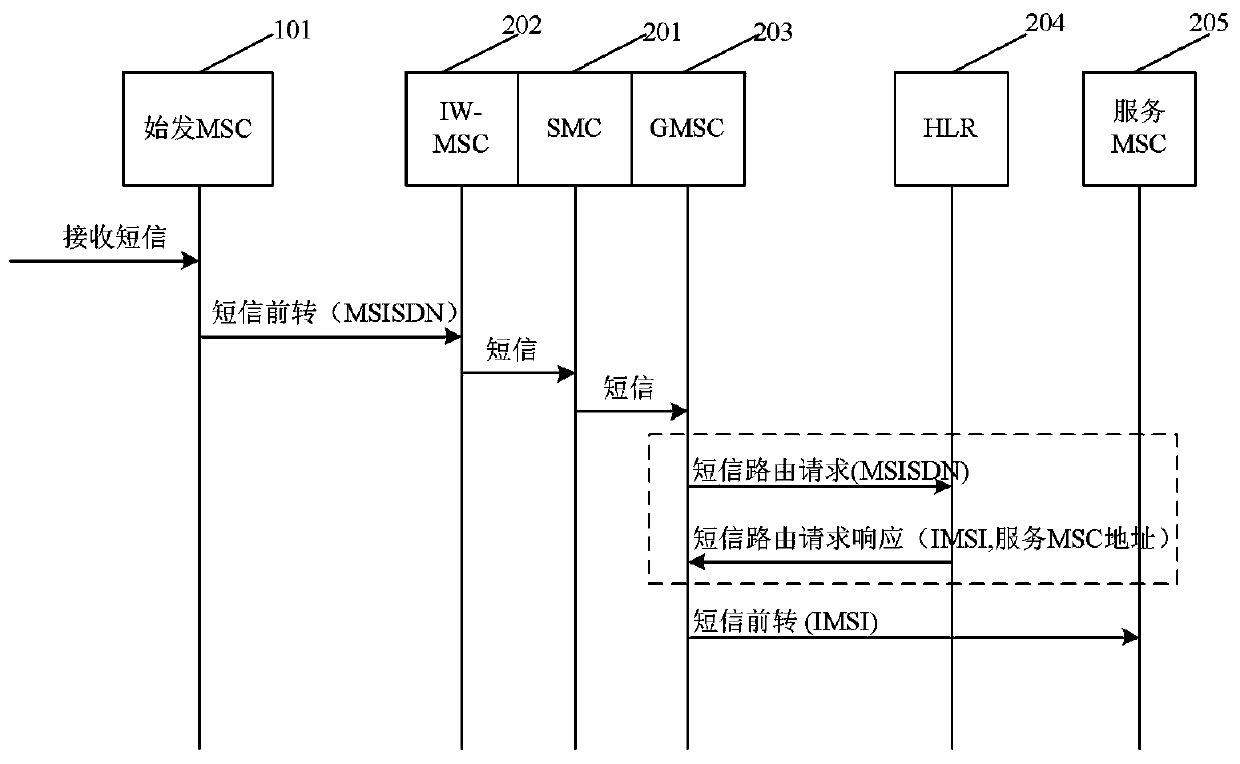
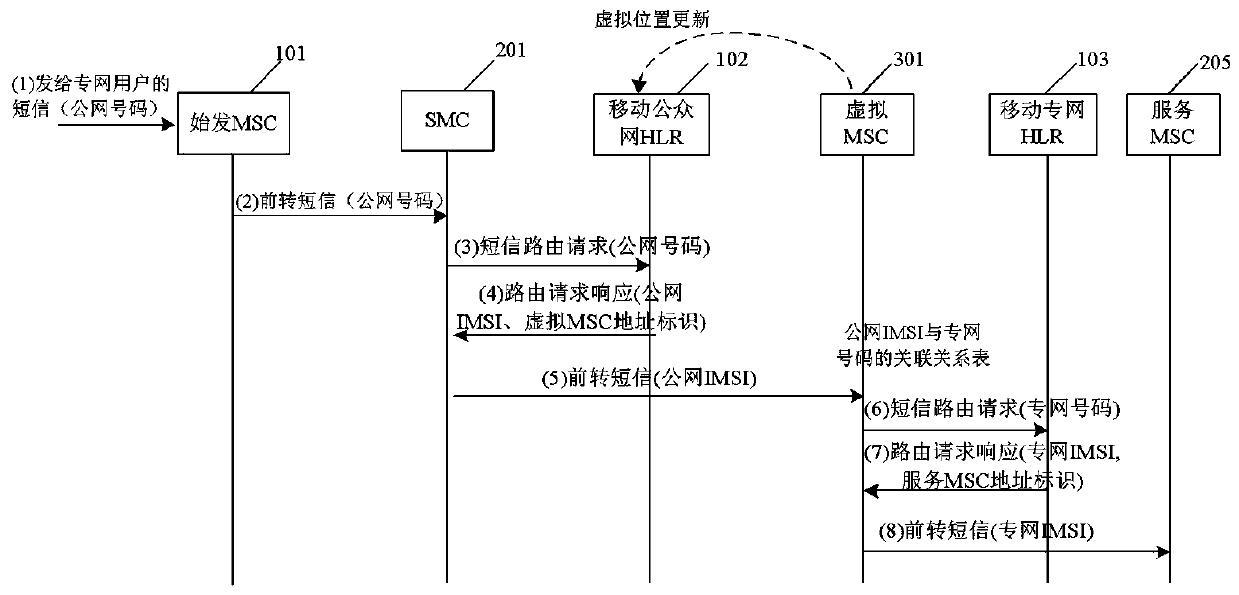
[0031] Embodiment 1, combining Figure 1-Figure 3 , a method for breaking up private network user numbers based on call forwarding service, the method for breaking up private network user numbers based on call forwarding service comprises the following steps:
[0032] Step 1: Assign two MSISDN number resources and two IMSI resources to each mobile private network user, wherein, the MSISDN number resources include the private network MSISDN number and the public network MSISDN number, and the IMSI resources include the private network IMSI and the public network IMSI; The network MSISDN number is not disclosed to all users, and the public network MSISDN number is disclosed to the public as the mobile phone number assigned to the mobile private network user;
[0033] Step 2: In the mobile private network, establish the association relationship between the private network MSISDN number of the mobile private network user and the public network MSISDN number, and the association re...
Embodiment 2
[0047] Example 2, combined with Figure 1-Figure 3 , the present invention is based on the embodiment of the method for breaking up private network user numbers based on the call forwarding service, which specifically includes the following steps:
[0048] Step 100: Each mobile private network user occupies two MSISDN number resources and two IMSI resources. The two MSISDN numbers include a private network MSISDN number (hereinafter referred to as the private network number), and a public network MSISDN number (hereinafter referred to as the public network number); the two IMSIs include a private network IMSI and a public network IMSI. Among them, the private network number has a fixed number segment (such as 160xxxxxxxx), which is allocated and managed by the mobile private network operation department, and the private network number belongs to a certain HLR of the private network (called the private network HLR); the public network number has no fixed number segment , alloc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com