An Attacker-Centric Security Protocol Verification Method
A verification method and security protocol technology, applied in the field of computer security protocol verification, can solve problems such as explosion, increase of state space, and redundancy of expansion methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] Embodiment 1: An attacker-centric security protocol verification method, the method includes the following steps:
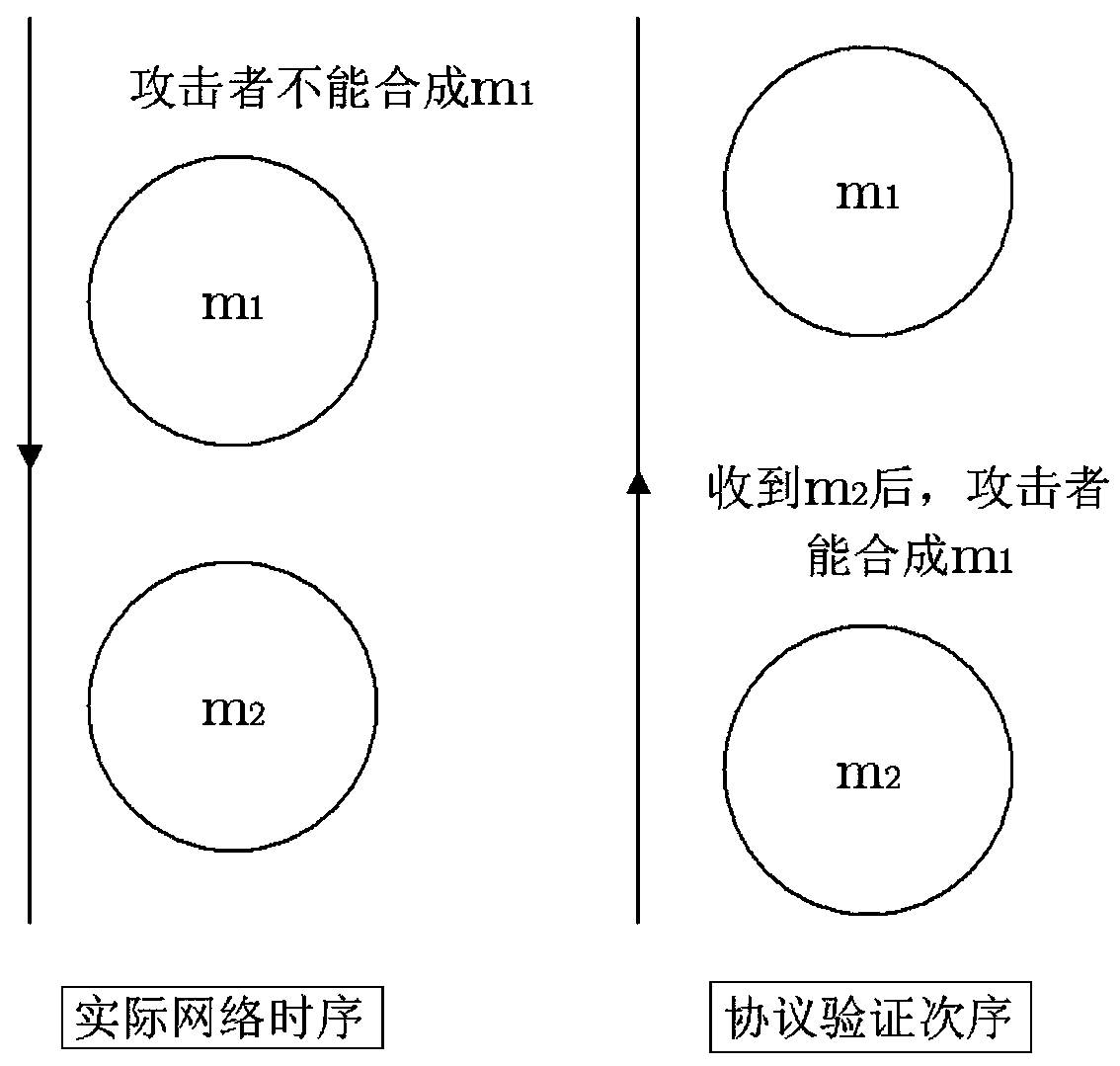
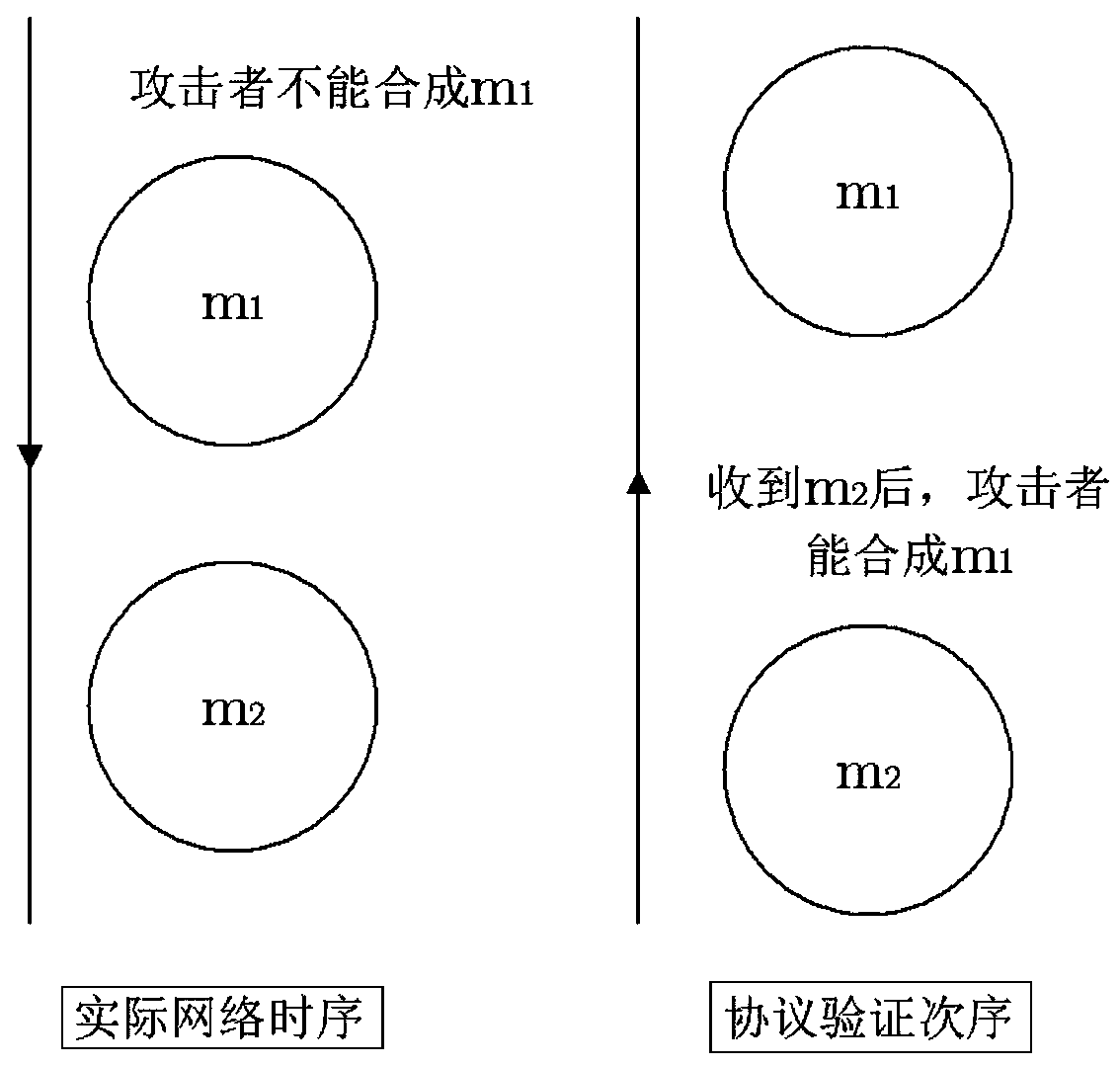
[0057] Step 1: Model the behavior of the legal subject and the attacker during the operation of the protocol, verify the target according to the protocol, and set the initial state. The initial state is set to contain only one role instance; protocol: expressed as a state set and a state The transition set, and the various behaviors of the attacker and the messages between the protocol participants are considered into this state set and state transition set, traversing the entire state space, and checking whether a certain state of interest can be reached.
[0058] The modeling mainly includes: (1) According to the Dolve-Yao model, the message sent by the subject can be regarded as received by the attacker regardless of whether the destination party is an attacker, and all the messages received by the subject can be regarded as sent by the attacker; therefo...
Embodiment 2
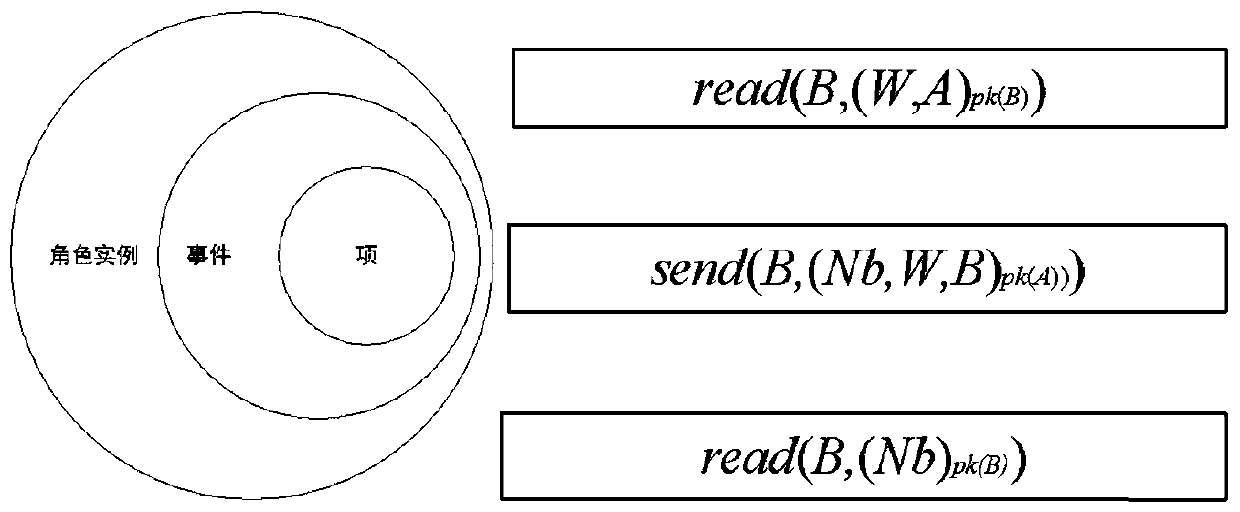
[0098] Embodiment 2: An attacker-centric security protocol verification method, first of all, it is necessary to model the legal subject and the attacker's behavior in the protocol operation process, the behavior of the legal subject can be described as a role instance; the attacker's behavior It mainly includes adding knowledge and attacker reasoning, respectively expressed as addTerm AtK (m) and core (m).
[0099] The attacker will intercept a large number of new messages to obtain new knowledge. There are a large number of repeated subitems in these message items. In order to simplify the attacker's knowledge set, the present invention formulates the following attacker knowledge addition rules to remove the same non-decomposable subitems.
[0100] R1:
[0101] R2:
[0102] R3:
[0103] R4:
[0104] R5:
[0105] On the basis of the attacker's knowledge, the attacker's reasoning mainly solves two problems: one is to judge whether the attacker can generate the t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com