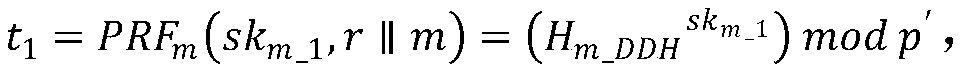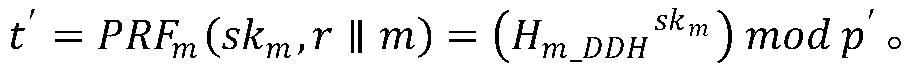An authenticated proxy re-encryption system and method based on symmetric cryptography
A proxy re-encryption and symmetric cipher technology, applied in the field of proxy re-encryption systems, can solve problems such as security threats, practical discounts, and inability to verify message reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
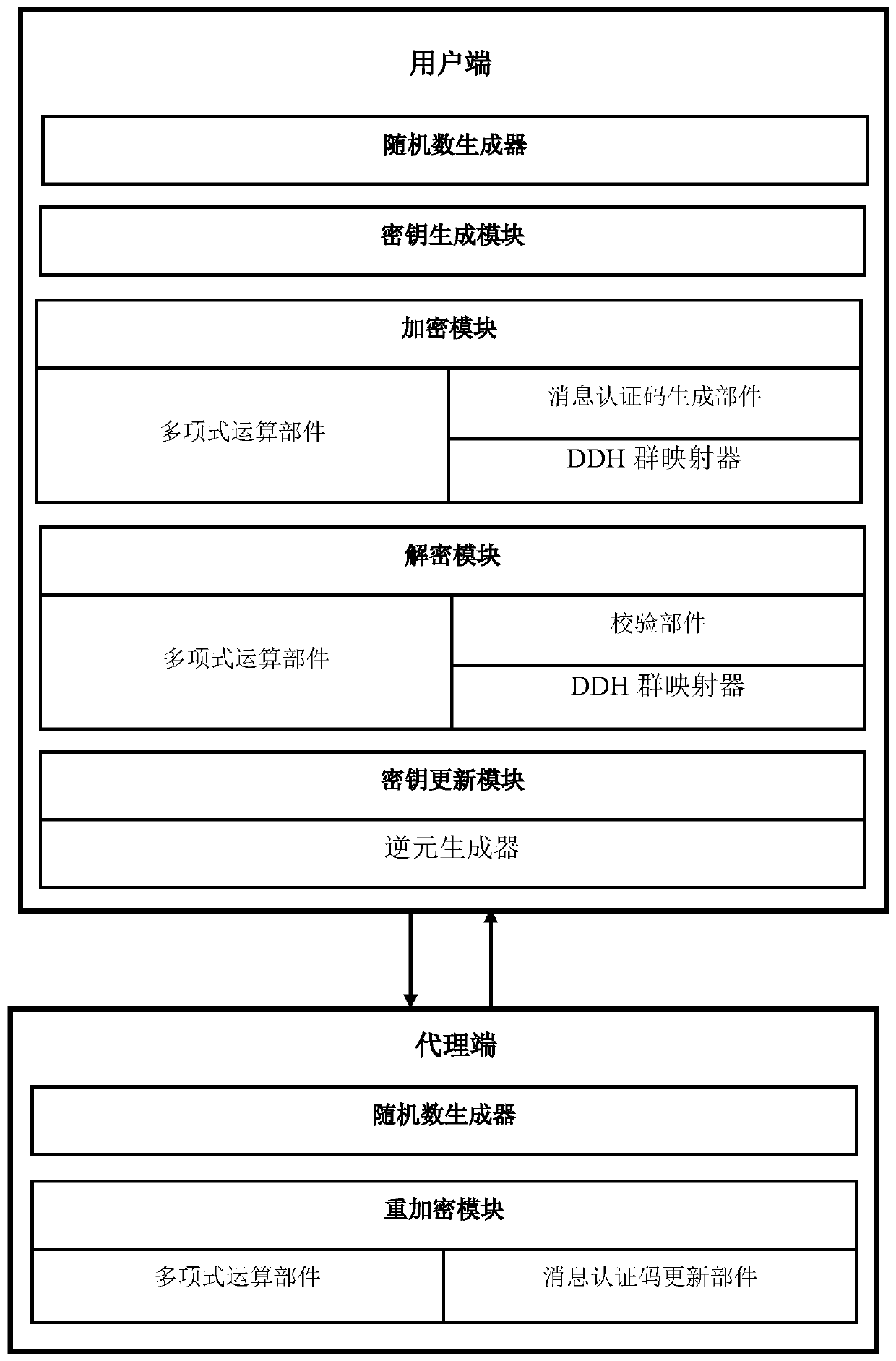
[0076] This embodiment discloses an authenticated proxy re-encryption system based on symmetric cryptography, as shown in the attached figure 1 As shown, the system includes:
[0077] 1) Client
[0078] The client is used to initiate a re-encryption request to the agent. It includes random number generator, key generation module, encryption module, decryption module and key update module. When the data needs to be re-encrypted, the random number generator first generates a random number, uses the key generation module to generate a new encryption key and a new authentication key, and then generates a re-encryption key and authentication key through the key update module The key is changed, and then the random number, the re-encryption key and the authentication change key are sent to the re-encryption module of the agent. In addition to being able to initiate a re-encryption request to the agent, the client can also encrypt and decrypt data.
[0079] Random number generato...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com