Data encryption method and device, data decryption method and device, and data processing system
A data and encrypted technology, applied in the field of communication, can solve the problems of multi-central processing units, affecting processing efficiency, data storage speed, etc., to achieve the effect of reducing the number of calls, reducing CPU operations, and improving processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
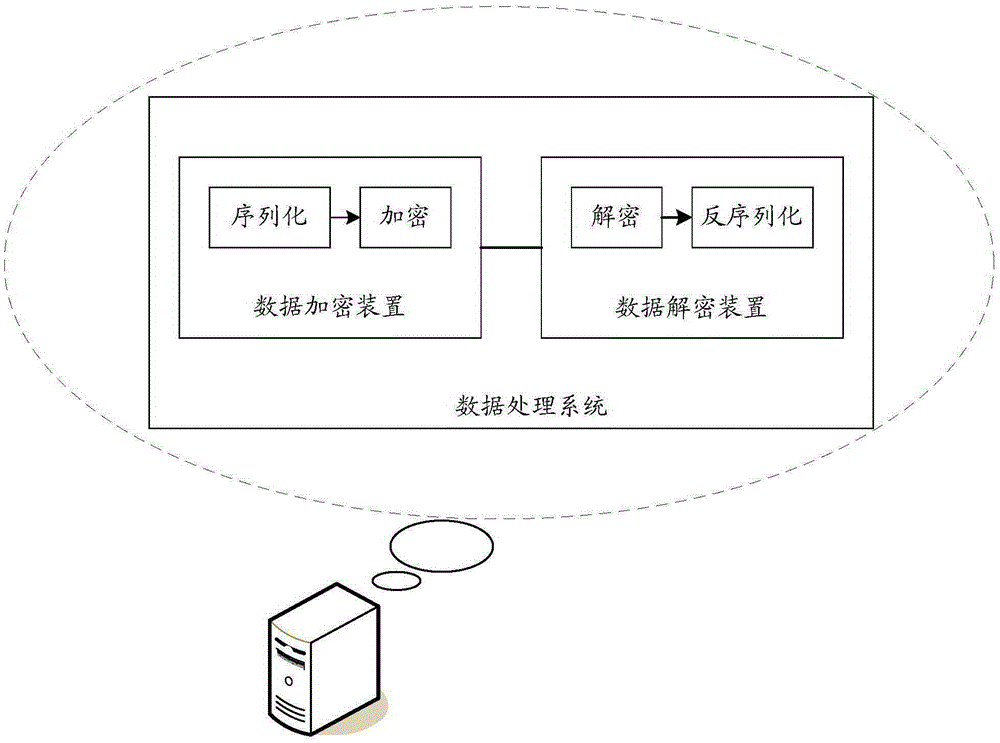
[0047] This embodiment describes the perspective of the data encryption device, and the data encryption device may specifically be integrated in devices such as terminals, servers, or storage devices.
[0048] A method for encrypting data, comprising: obtaining original relational data that needs to be encrypted; determining attributes that need to be encrypted in the original relational data; using a serialization algorithm to serialize the attributes that need to be encrypted to obtain serialized data; Encrypt the serialized data with a preset encryption algorithm to obtain encrypted data; store the encrypted data as an attribute of the original relational data to obtain encrypted relational data.
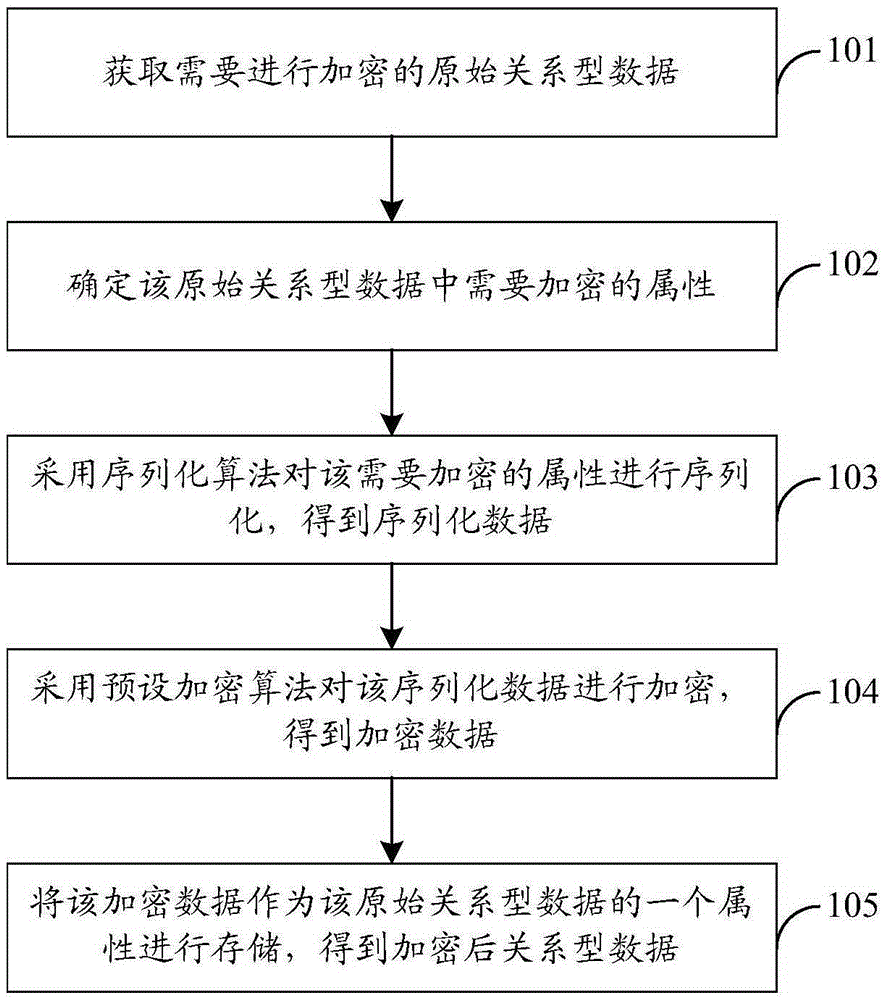
[0049] Such as Figure 1b As shown, the specific flow of the data encryption method can be as follows:
[0050] 101. Obtain the original relational data that needs to be encrypted.
[0051] Among them, the original relational data refers to the relational data before encryption...
Embodiment 2
[0072] In this embodiment, description will be made from the perspective of a data decryption apparatus, and the data decryption apparatus may specifically be integrated in a device such as a terminal, a server, or a storage device.
[0073] A method for decrypting data, comprising: obtaining encrypted relational data that needs to be decrypted; determining encrypted data in the encrypted relational data; using a preset decryption algorithm to decrypt the encrypted data to obtain decrypted data; Deserialization algorithm deserializes the decrypted data to obtain deserialized data; stores the deserialized data as attributes of relational data respectively to obtain original relational data.
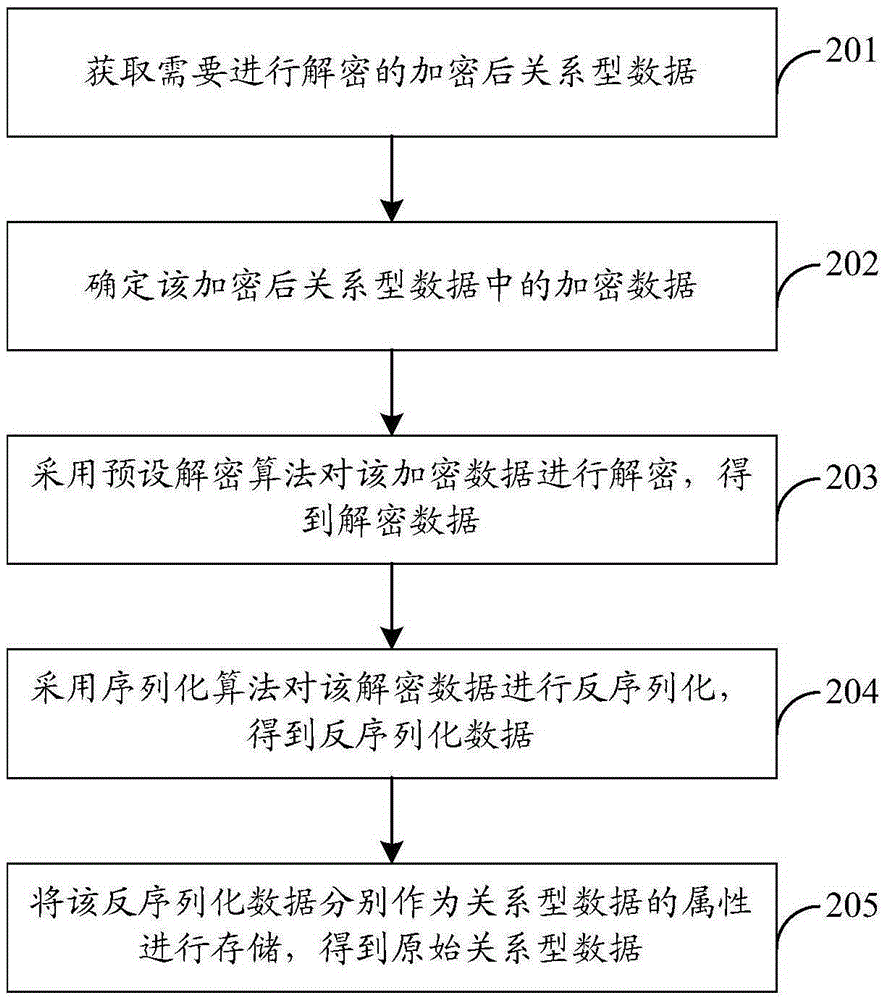
[0074] Such as figure 2 As shown, the specific flow of the data decryption method can be as follows:
[0075] 201. Obtain encrypted relational data that needs to be decrypted.
[0076] Wherein, the encrypted relational data is obtained by encrypting the original relational data. For a s...
Embodiment 3
[0095] According to the methods described in Embodiments 1 and 2, examples will be given below for further detailed description.
[0096] In this embodiment, the serialization algorithm is specifically the protobuf algorithm as an example for illustration, and the details can be as follows:
[0097] (1) Encryption;
[0098] Such as Figure 3a As shown, a data encryption method, the specific process can be as follows:
[0099] A301. The data encryption device acquires the original relational data that needs to be encrypted.
[0100] For example, after receiving the encryption request, the original relational data that needs to be encrypted is obtained according to the instruction in the encryption request, for example, the original relational data that needs to be encrypted can be obtained from a local or other storage device, and so on.
[0101] Among them, the original relational data refers to the relational data before encryption, and the relational data refers to the da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com