Network equipment risk assessment method
A technology for network equipment and risk assessment, applied in the field of network security, to achieve the effect of eliminating ambiguity, eliminating ambiguity transmission, and having strong applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
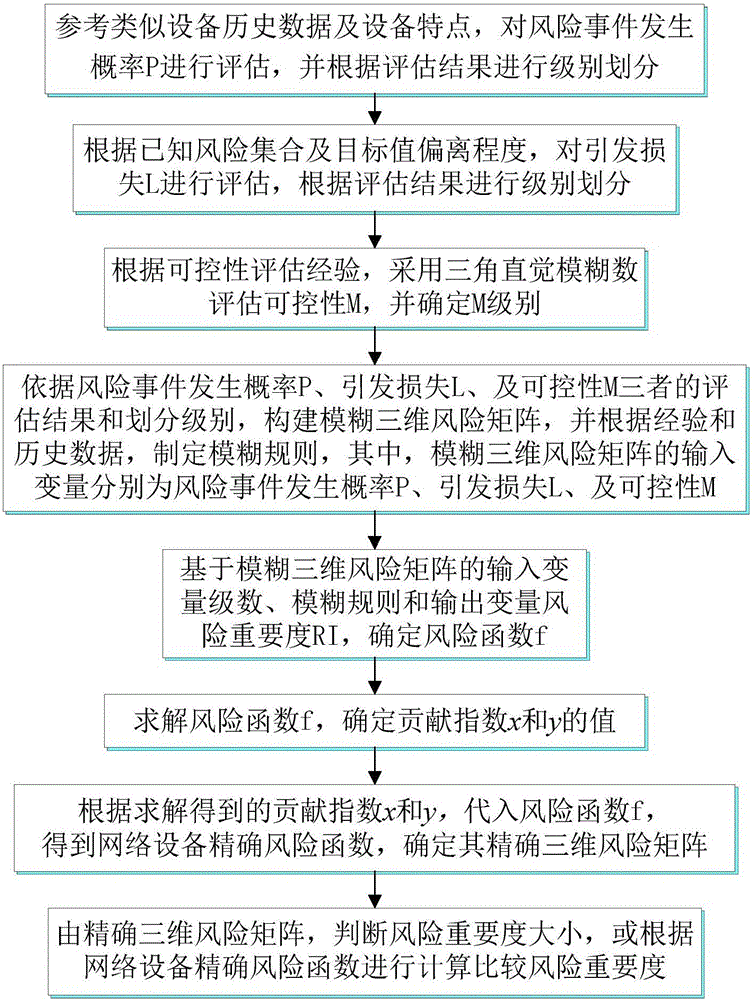
[0065] Embodiment one, see figure 2 As shown, a network equipment risk assessment method includes the following steps:
[0066] Step 1. With reference to the historical data and characteristics of similar equipment, evaluate the risk event probability P, and classify according to the evaluation results;
[0067] Step 2. Evaluate the induced loss L according to the known risk set and the degree of deviation from the target value, and classify according to the evaluation results;
[0068] Step 3. Evaluate the controllability M by using the triangular intuitionistic fuzzy number according to the controllability evaluation experience, and determine the M level;
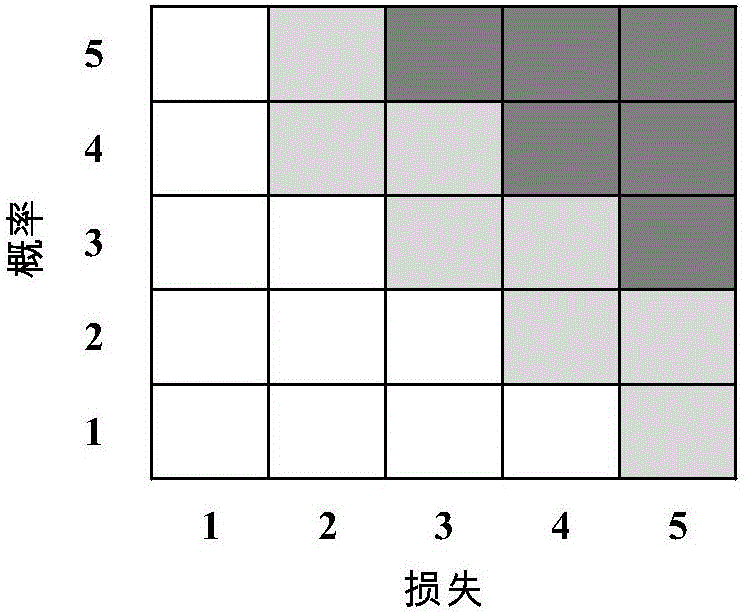
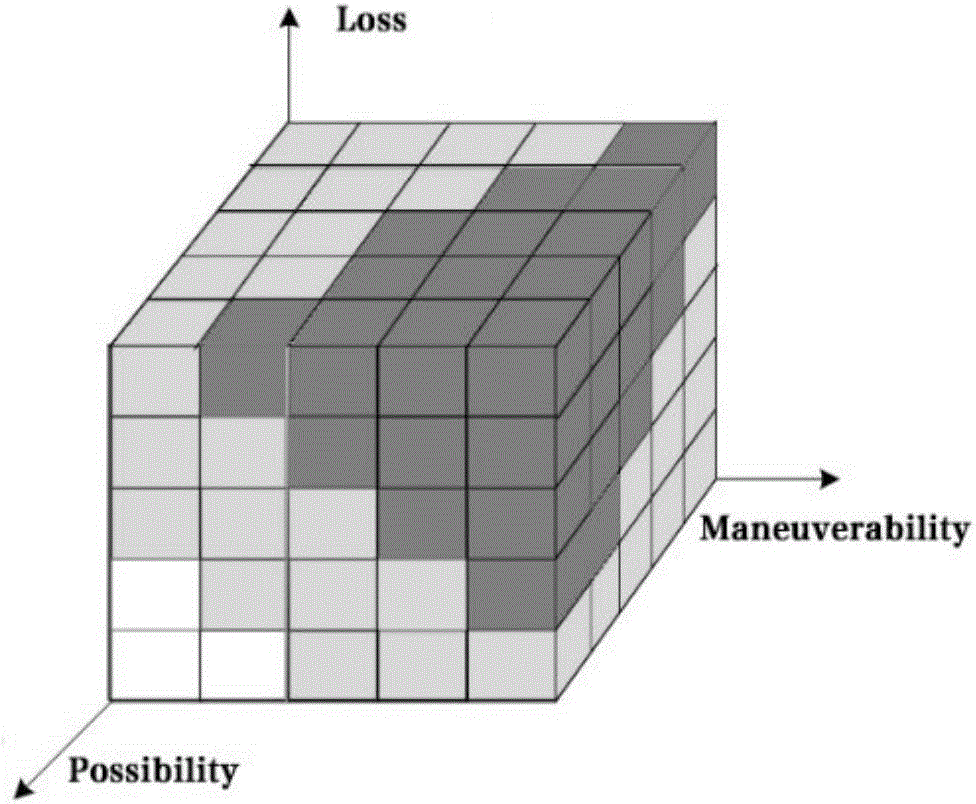
[0069] Step 4. Construct a fuzzy three-dimensional risk matrix based on the evaluation results and classification levels of risk event occurrence probability P, induced loss L, and controllability M, and formulate fuzzy rules based on experience and historical data. Among them, fuzzy three-dimensional risk The input va...
Embodiment 2
[0075] Embodiment two, see Figure 2-8 As shown, a network equipment risk assessment method includes the following contents:
[0076] Step 1. With reference to the historical data and characteristics of similar equipment, evaluate the risk event probability P, and classify according to the evaluation results;
[0077] Step 2. Assume that the occurrence of risk causes the target value to change from C 0 Deviate to C, then its degree of deviation Δ is:
[0078] Δ=|C-C 0 |
[0079] The induction loss L is expressed as:
[0080]
[0081] , where R is the known risk set, y is any risk in R, and L∈(0,1] is obtained to determine the division level of L;
[0082] Step 3. Evaluate the controllability M based on the controllability evaluation experience and use the triangular intuitionistic fuzzy number, and determine the M level, including the following contents:
[0083] Step 3.1. Collect empirical data for controllability judgment, display it in the form of triangular intuit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com