Double-factor authentication method based on double convolutional and cycle encoding
An authentication method and convolutional coding technology, which is applied in the field of identity recognition and authentication, can solve problems such as theft, copying, and loss, and achieve the effect of high security and high authentication accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
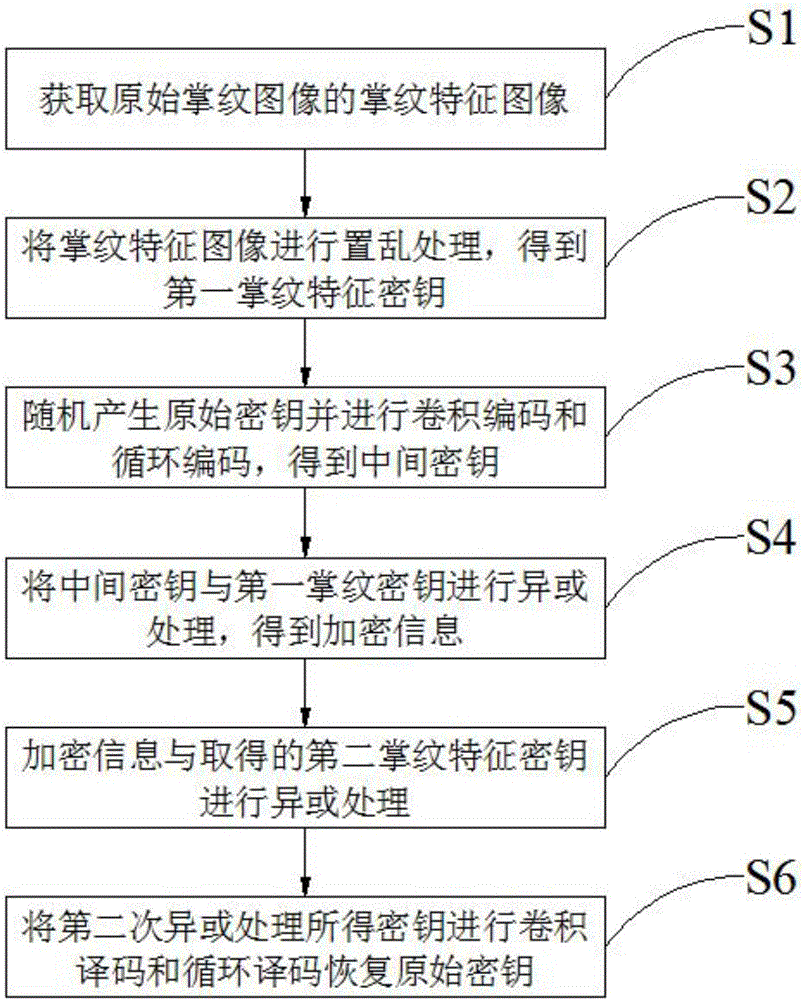
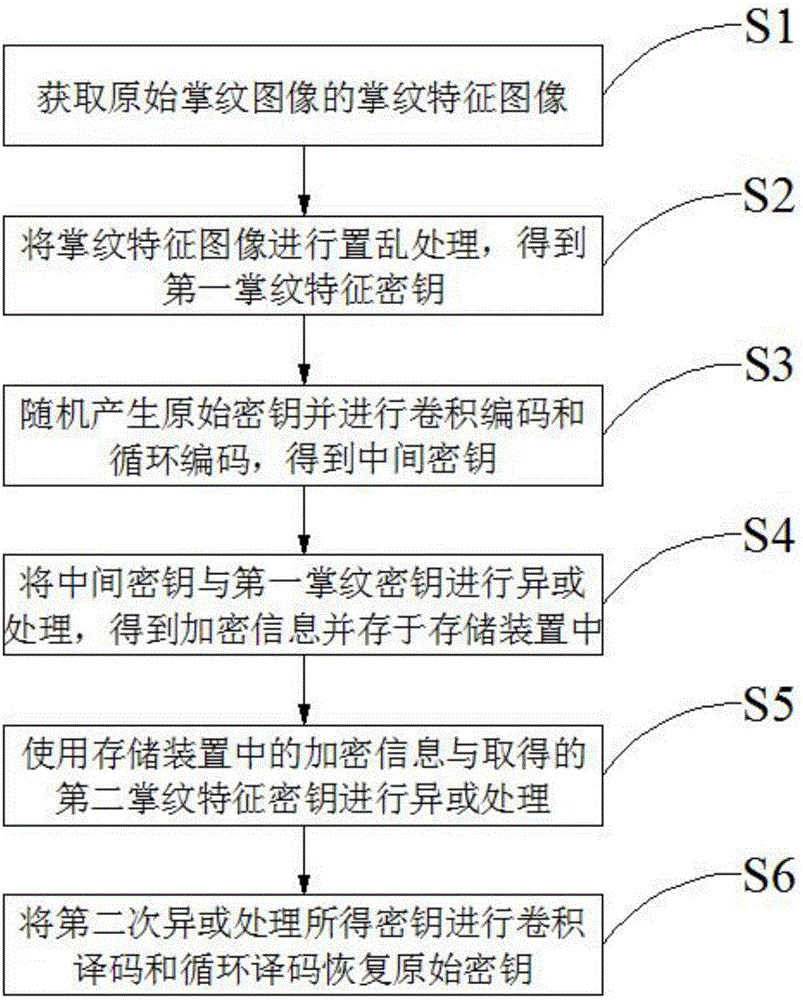
[0032] Embodiment 1 of the present invention is described below:
[0033] Embodiments of the present invention are as figure 1 shown, including the following steps:
[0034] S1: Obtain the palmprint feature image of the original palmprint image; specifically, it is to collect the original palmprint image, convert the original palmprint image into a binary image, extract the outline of the outer edge of the palm in the binary image, and detect the index finger and middle finger The corner points formed between the ring finger and the little finger, and the original palmprint image is corrected by these two corner points to obtain the palmprint ROI area, that is, the palmprint feature image. The correction operation can use the following process: take the line connecting the two corner points as the vertical axis, draw a vertical line from the midpoint of the two corner points to the vertical axis, use the vertical line as the horizontal axis, and take the intersection of the v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com