Terminal abnormity detection method
A technology of anomaly detection and detection method, which is applied in the direction of digital transmission system, data exchange network, closed-circuit television system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] It should be noted that, in the case of no conflict, the following technical solutions and technical features can be combined with each other.
[0035] The specific embodiment of the present invention will be further described below in conjunction with accompanying drawing:
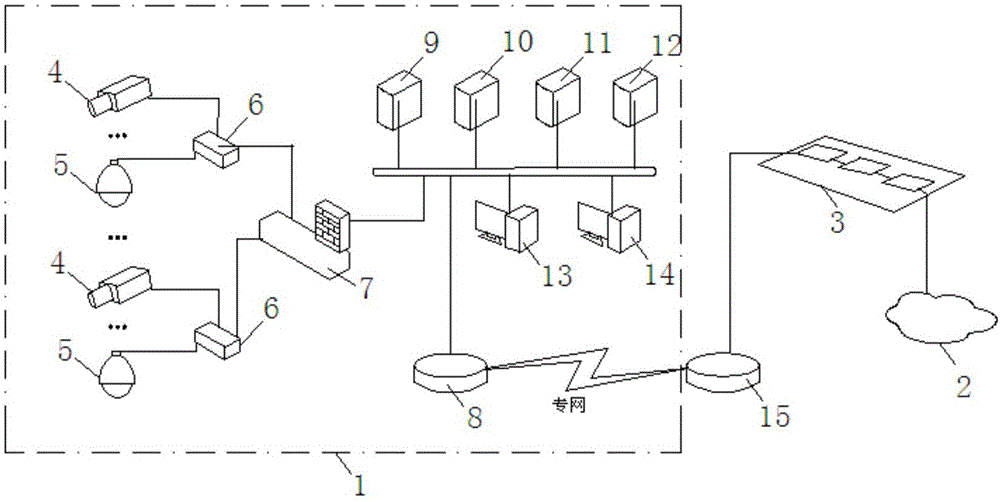
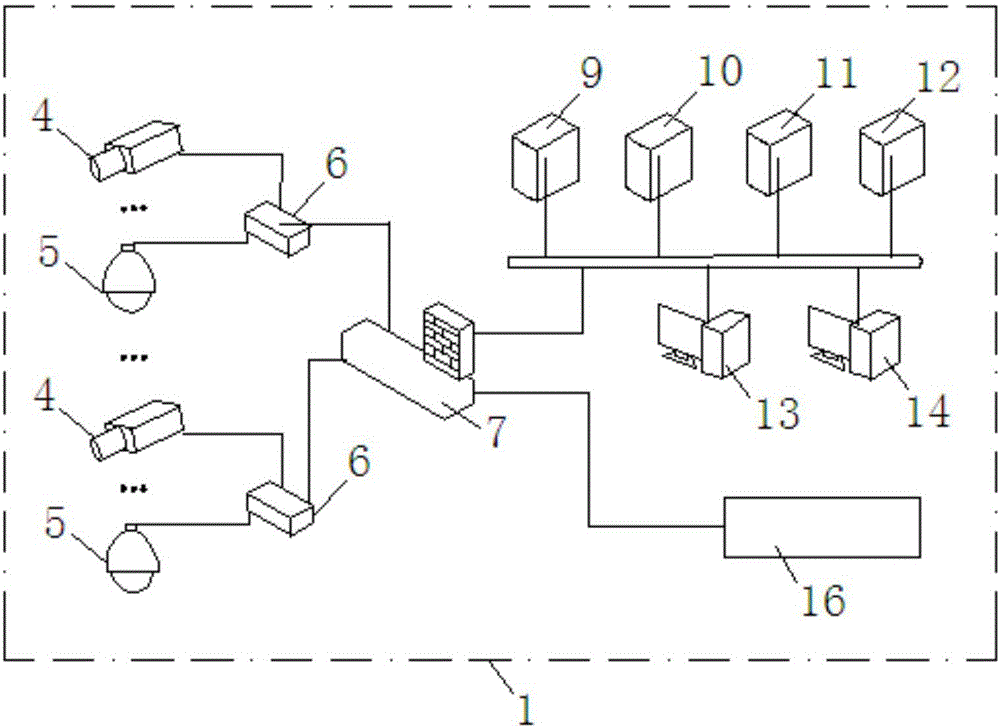
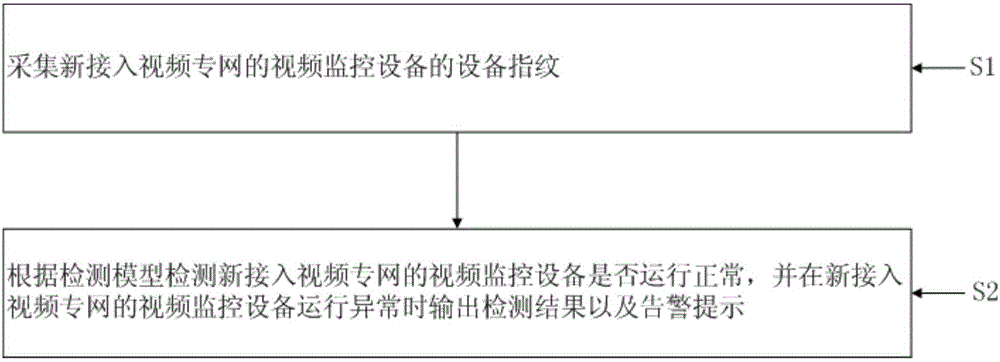
[0036] Such as Figure 2-3 As shown, a terminal anomaly detection method is suitable for network access detection of a private video network, where at least one video surveillance device is connected to the private video network; each video surveillance device has a unique device fingerprint, and the device fingerprint is the same as that of the video surveillance device The set of feature items corresponding to the operating system;
[0037] Collect the device fingerprint of at least one video surveillance device before the detection method and establish a fingerprint sample library, preset at least one decision rule, define the fluctuation range of each decision rule according to the fingerprint...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com