A CC attack defense method and its defense system
A blacklist and server technology, applied in the field of defense against CC attacks, it can solve problems such as inability to effectively protect server network security, slow opening of normal request pages, and bandwidth blockage, so as to reduce the number of HTTP requests, increase attack costs, and prevent attacks. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
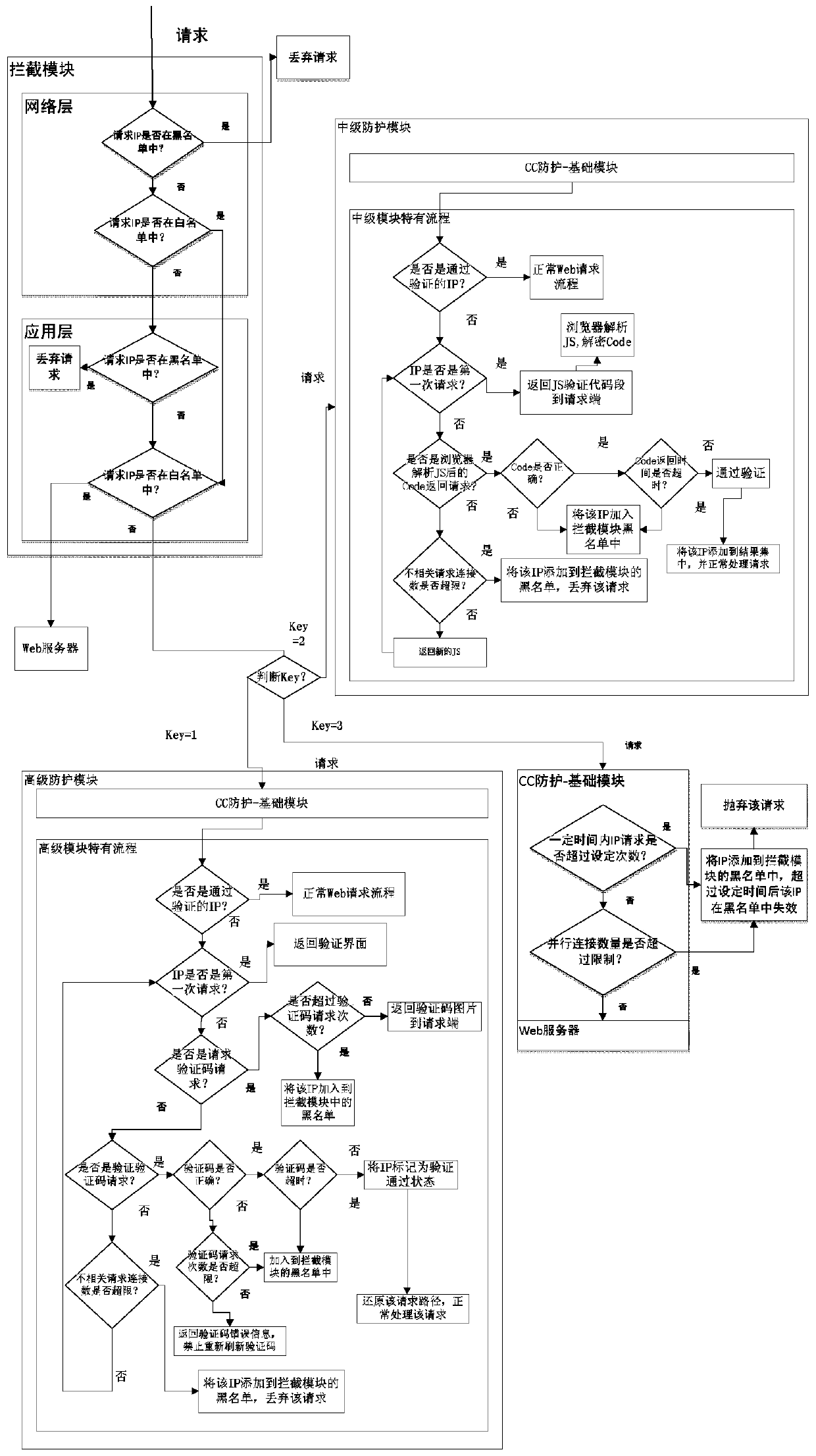
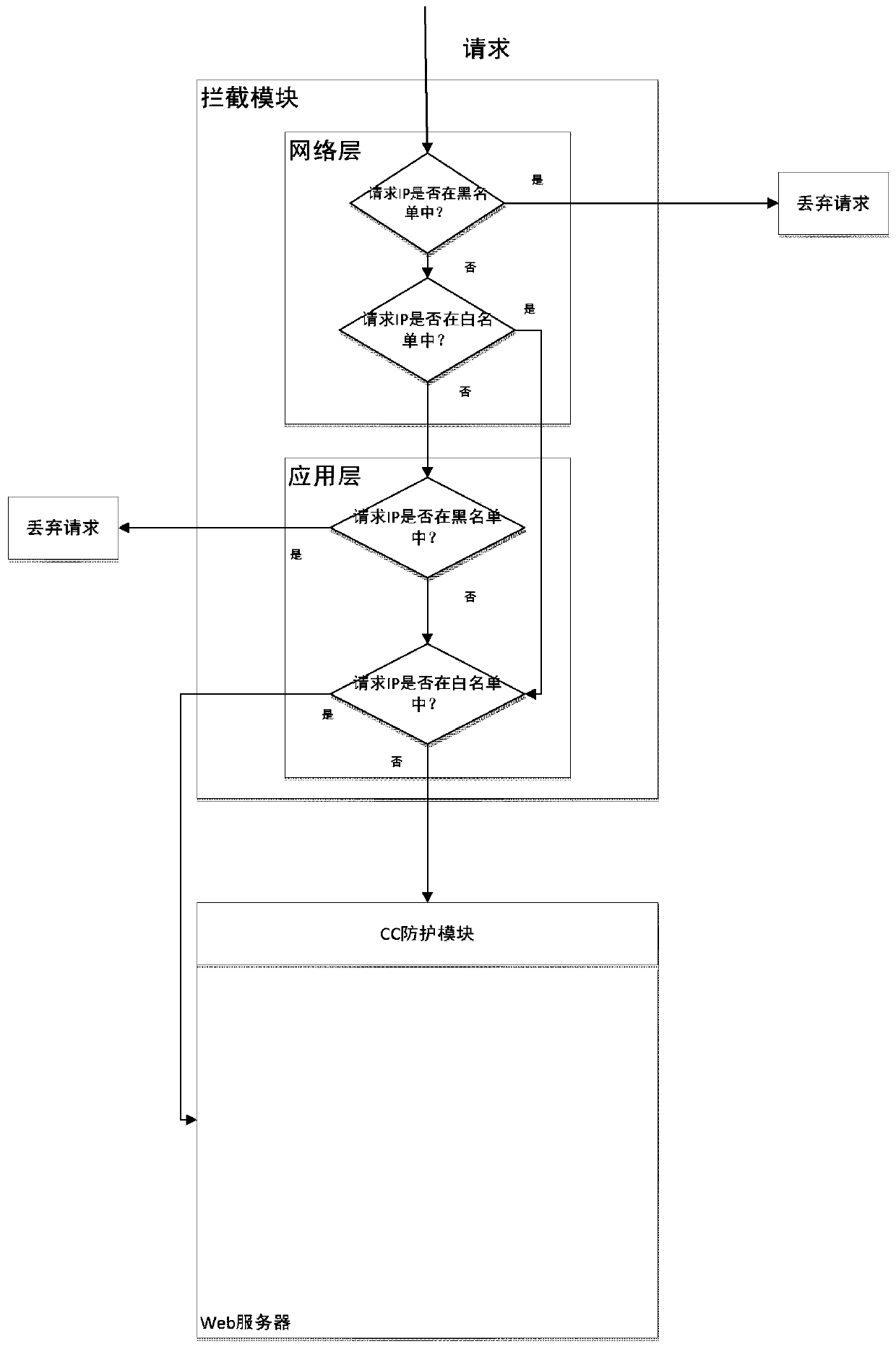
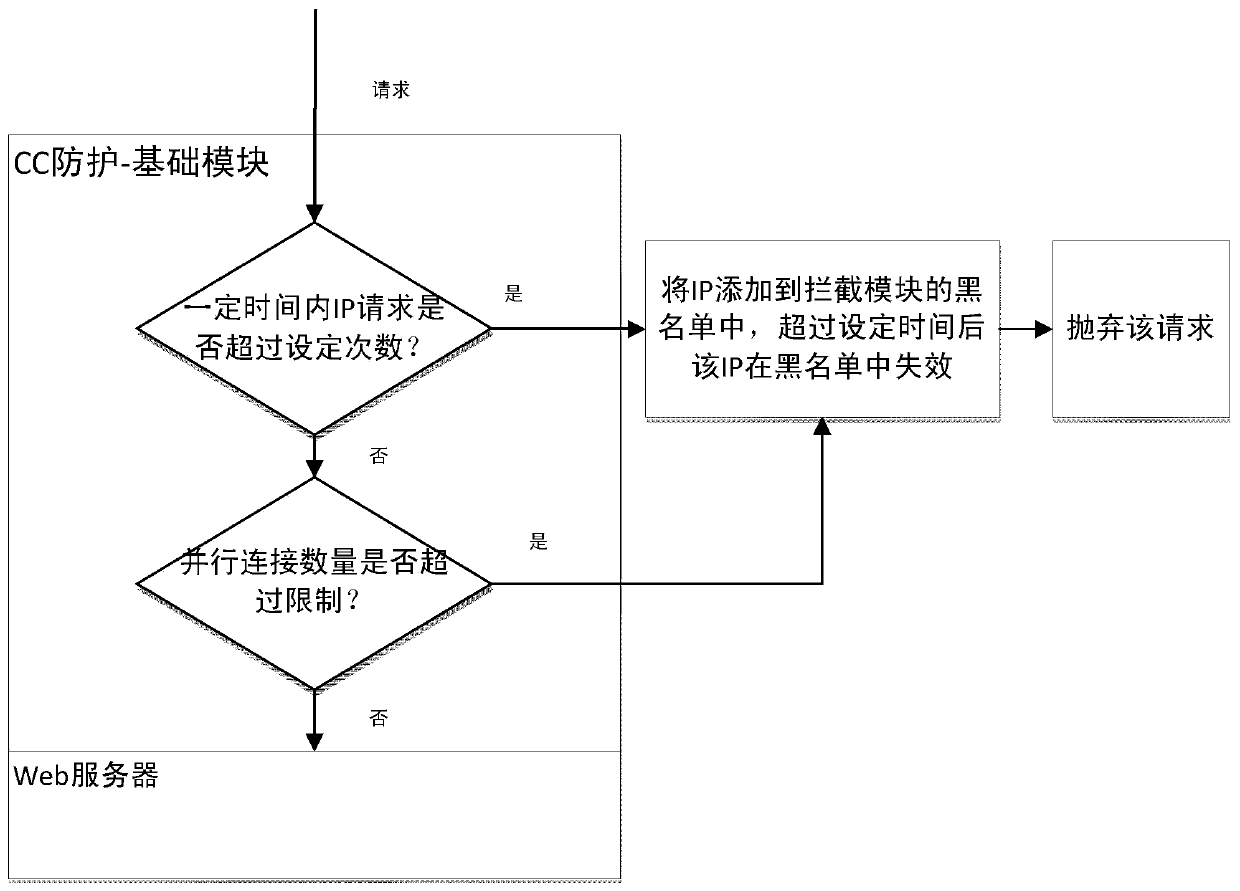
[0103] Embodiment 1: If a single IP access reaches y times every x seconds, the implementation of CC attack protection is triggered, as follows:
[0104] 1) The Admin sets the CC protection level on the M side as the basic protection, and sets the basic protection parameters as follows: a single IP every x seconds, if the access reaches y times, or more than z parallel connections are established, the time to lock the IP is v minutes;
[0105] 2) Hackers use httpd's own ab tool to send attack commands to the server:
[0106] . / ab-n / -c m http: / / 192.168.1.47 / login.jsp, the parameter -n of this command means to send m requests, -c means to resume m parallel connections.
[0107] 3) Admin sets the parameters of the basic protection module as: x=10, y=10, z=10, v=10;
[0108] 4) The hacker uses the ab tool to send a request, the command is: . / ab-n 20http: / / 192.168.1.47 / login.jsp, the command is to send 20 (m=20) requests to the server whose IP address is 192.168.1.47 , at this t...
Embodiment 2
[0109] Embodiment 2: A single IP establishes more than z parallel connections to trigger CC attack protection, and the specific implementation is as follows:
[0110] 1) If Admin sets the parameters of the basic protection module to: x=10, y=100, z=10, v=10; here, try to set a large parameter for y to prevent the CC attack protection from being triggered by the number of visits and skip it CC protection triggered by the number of concurrent connections.
[0111] 2) At this time, the command sent by the hacker using the ab tool is . / ab-c 20http: / / 192.168.1.47 / login.jsp, which is to establish 20 concurrent accesses to the web application whose server IP is 192.168.1.47, At this time, m>z(20>10), the number of parallel connections of a single IP exceeds 10, the basic protection module will add the IP that sent the ab command to the blacklist in the interception module, and the IP will be blacklisted within 10 minutes. The list is valid, that is, the IP will be locked for 10 minu...
Embodiment 3
[0116] Example 3: Implementing the Advanced Protection Module:
[0117] 1) Admin sets the CC protection level to advanced protection on the M side, and sets the protection parameters as: a single IP every x seconds, if the access reaches y times, or if more than z parallel connections are established, the IP will be locked for v minutes, and the verification will pass. The previous single IP is allowed to access at most q times, and the verification code is allowed to refresh the maximum number of times f times. A single verification code is valid within g seconds, and a single IP is saved for s minutes. After passing the verification, a single IP is valid for r hours after passing the verification.
[0118] 2) At this time, the set parameter values are: x=10, y=9999, z=9999, v=10, q=10, f=3, g=60, s=10, r=1, the current parameters are as far as possible Make the unique process of advanced protection effective, so the values of x, y, z, and v can be the maximum value. If the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com