Detection method for malicious act in Android application
A detection method and behavior technology, applied in the field of communication, can solve the problem of high false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
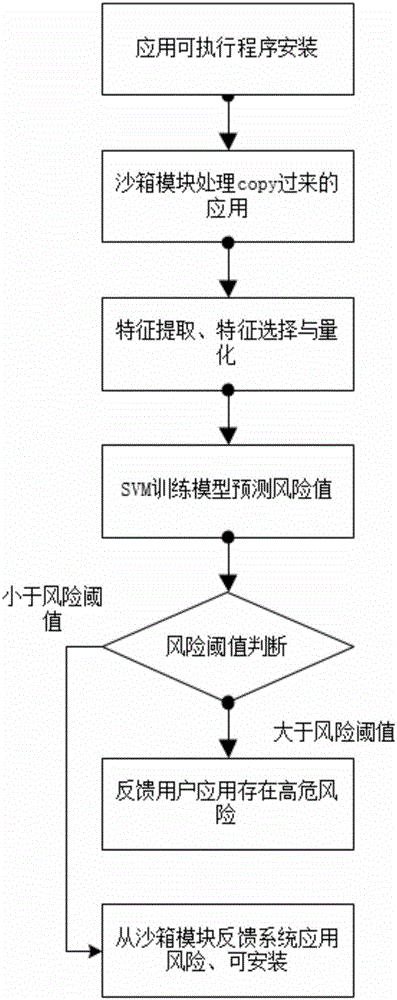
[0037] A method for detecting malicious behaviors of Android applications, comprising the following steps:
[0038] 1) start the Android smart terminal, and install the application executable program in the terminal;
[0039] 2) copying the executable program to the sandbox module;
[0040] 3) In the sandbox module, feature extraction is performed on the executable program;
[0041] 4) using the feature as the input unit of the trained SVM module, and obtaining the predicted risk value;
[0042] 5) If the predicted risk value is greater than or equal to the safety threshold, feed back to the Android smart terminal; if the predicted risk value is less than the safety threshold, install the executable program.
[0043] The feature extraction in step 3) includes static feature extraction and dynamic feature extraction, the features extracted by the static feature extraction are URIS and EMAILS, and the dynamic feature extraction is realized by network capture.
[0044] Step 4)...
Embodiment 2
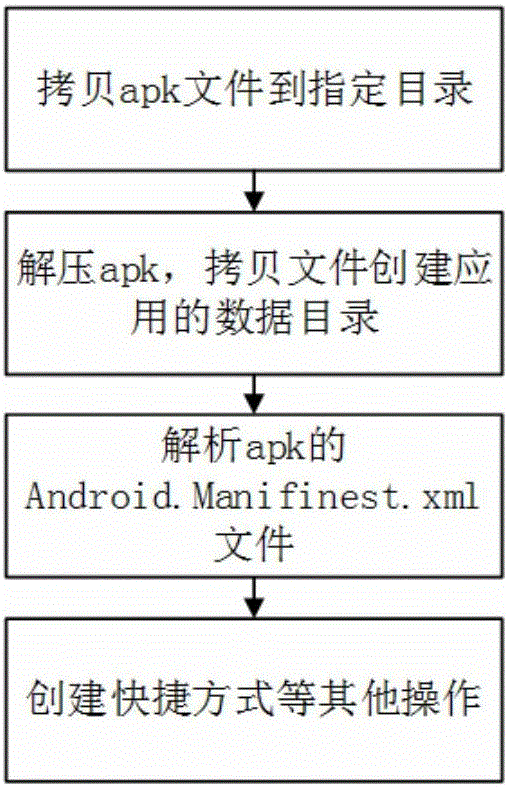
[0061] On the basis of Embodiment 1, a method for detecting malicious behaviors of Android applications includes the following steps:
[0062] 1) start the Android smart terminal, and install the application executable program in the terminal;
[0063] 2) copying the executable program to the sandbox module;
[0064] 3) In the sandbox module, analyzing and decompressing the executable program;
[0065] 4) If the format of the executable program is wrong or decompressed and identified during the analysis and decompression, the error message will be fed back to the user, otherwise, enter the next step;
[0066] 5) Analyze the digital certificate of the executable program, compare the obtained result with the blacklist, if the blacklist hits, then determine that it is a virus application, and feed back to the user, otherwise enter the next step;
[0067] 6) Analyzing the configuration file of the executable program, calculating the primary policy weight, if the weight exceeds t...
Embodiment 3
[0072] On the basis of the foregoing embodiments, a system for detecting malicious behaviors of Android applications that implements the foregoing method includes the following structure:
[0073] Copy the module to copy the executable program;
[0074] The communication module is used for uploading the copy of the executable program copied by the copy module and feeding back the results of malicious behavior monitoring;
[0075] The control module is used for the user to input parameters, run detection scripts, calculate primary strategy weights and view detection results;
[0076] The storage module is used to store samples, blacklists, and weight thresholds, and supports users to create, add, modify, delete, and query;
[0077] A comparison module, configured to compare the primary strategy weight with the weight threshold;
[0078] The sandbox module is used to carry out malicious behavior detection to the copy of the executable program; the sandbox module includes a sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com