Method and device for reducing operation amount in SM3 password hashing algorithm
A technology of hash algorithm and calculation amount, which is applied in the direction of encryption device with shift register/memory, secure communication device, digital transmission system, etc., and can solve the problems of large total delay and affecting the operation speed of cryptographic algorithm, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
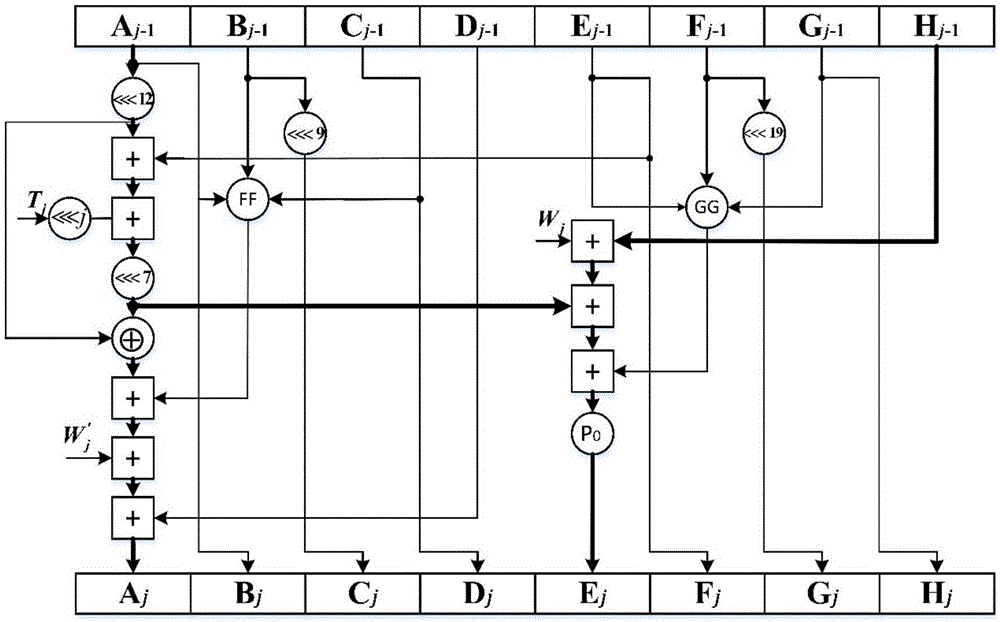
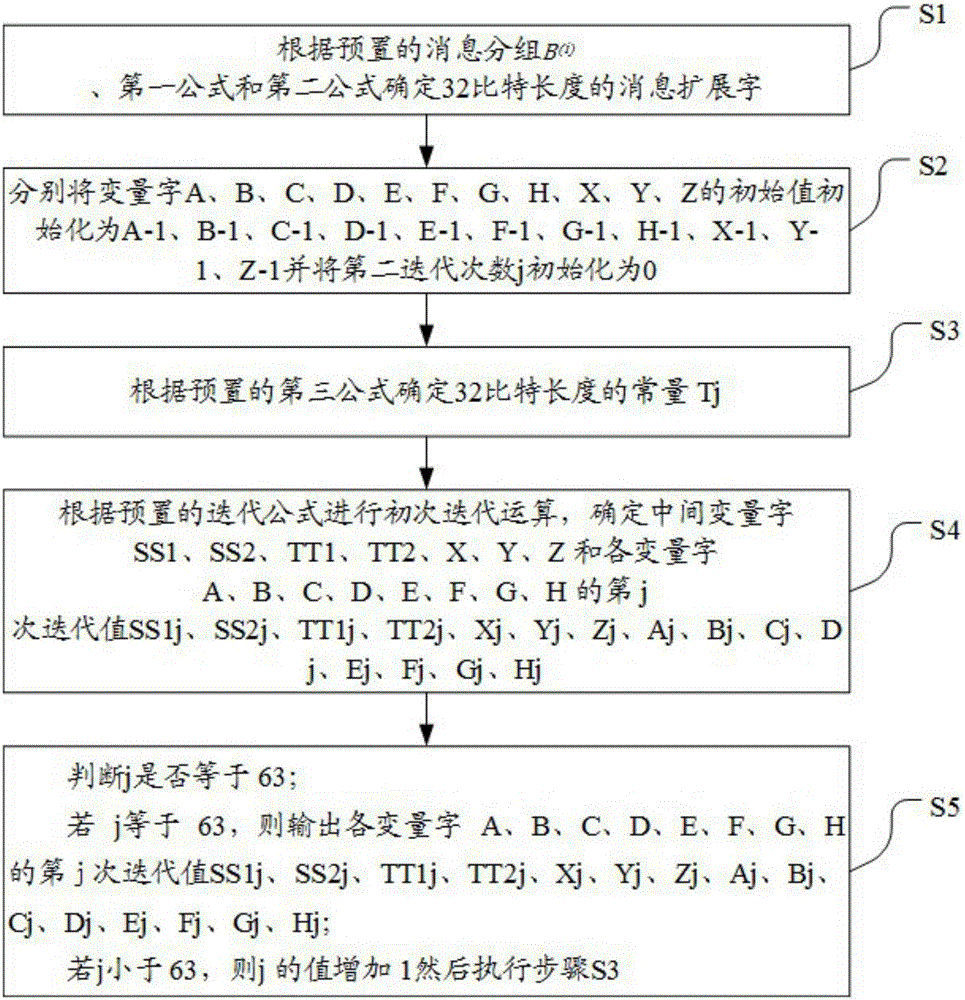
[0114] see figure 2 , the embodiment of the present invention provides a first embodiment of a method for reducing the amount of computation in the SM3 cryptographic hash algorithm, including:
[0115] S1, group B according to the preset message (i) , the first formula and the second formula determine the message extension word W of 32 bit length 0 -W 67 , W′ 0 -W' 63 , the first formula is The second formula is where i is the first iteration number, is the replacement function;
[0116] In the embodiment of the present invention, it is first necessary to group B according to the preset message (i) , the first formula and the second formula determine the message extension word W of 32 bit length 0 -W 67 , W′ 0 -W' 63 , the first formula is The second formula is where i is the first iteration number, is the replacement function, W 0 -W 67 , W′ 0 -W' 63 refers to W 0 to W 67 , W′ 0 -W' 63 means W' 0 to W' 63 .
[0117] S2, respectively initialize...
no. 2 example
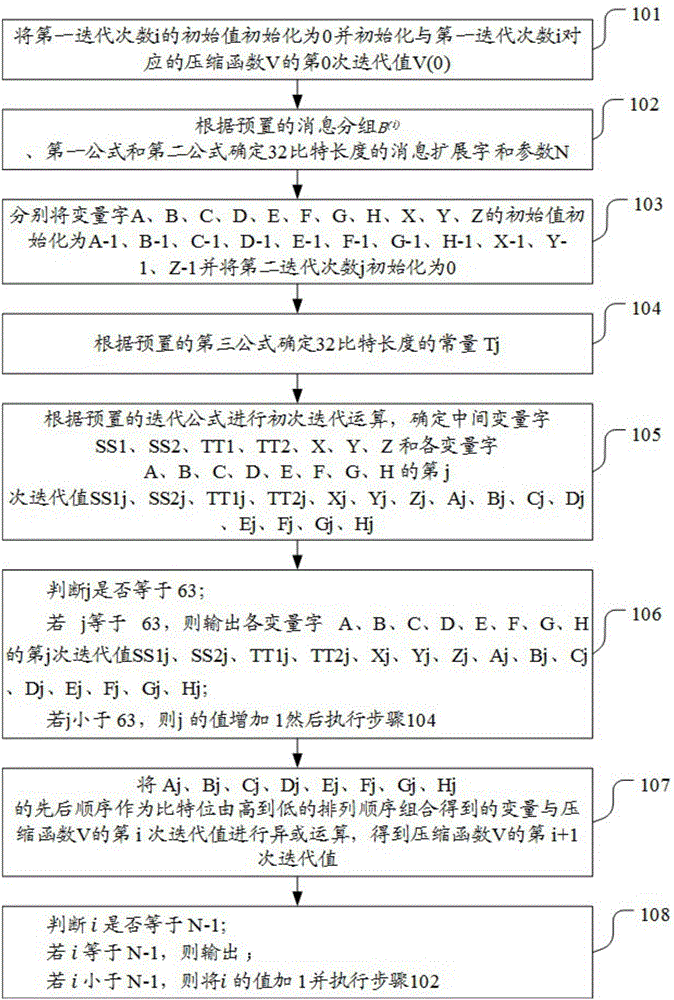
[0150] see image 3 and Figure 4 , the embodiment of the present invention provides a second embodiment of a method for reducing the amount of computation in the SM3 cryptographic hash algorithm, including:
[0151] 101. Initialize the initial value of the first iteration number i to 0 and initialize the 0th iteration value V(0) of the compression function V corresponding to the first iteration number i;
[0152] In the embodiment of the present invention, it is first necessary to initialize the initial value of the first iteration number i to 0 and initialize the 0th iteration value V(0) of the compression function V corresponding to the first iteration number i, V (0) It is expressed in hexadecimal 7380166f4914b2b9 172442d7da8a0600a96f30bc 163138aa e38dee4d b0fb0e4e.
[0153] 102. Group B according to the preset message (i) , the first formula and the second formula determine the message extension word W of 32 bit length 0 -W 67 , W′ 0 -W' 63 and parameter N, the fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com