Encryption and decryption method and device for distributed storage system communication protocol
A technology of distributed storage and system communication, applied in the encryption field of decryption method and device, communication protocol of distributed storage system, can solve problems such as ciphertext cracking, and achieve the effect of improving security and increasing the difficulty of being cracked.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
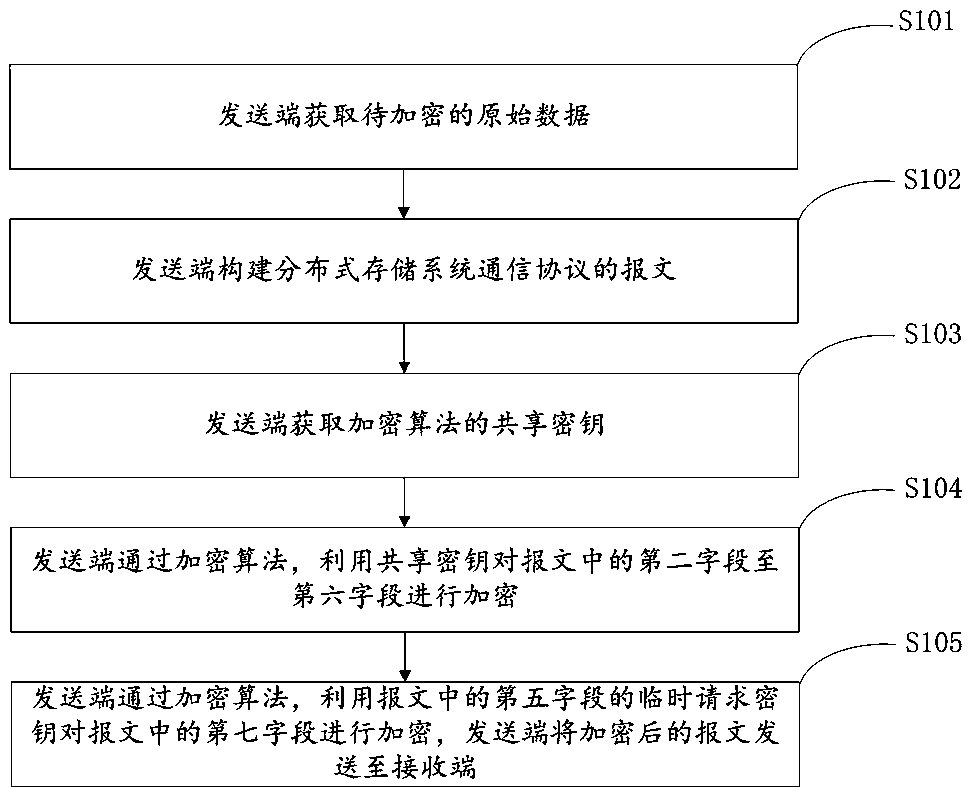
[0063] Please refer to figure 1 , an encryption method for a distributed storage system communication protocol, comprising the following steps:
[0064] Step S101: The sender obtains the original data to be encrypted.
[0065] Step S102: The sender constructs a message of the communication protocol of the distributed storage system, and the message of the communication protocol of the distributed storage system includes seven fields, wherein the first field is a random number occupying one byte, and the second field is a random number occupying one byte. A four-byte magic number, the third field is the length value of the fourth field, which occupies one byte, the fourth field is random length and random content garbage text, the fifth field is the temporary request key, and the sixth field is Temporary response key, the seventh field is the original data to be encrypted on the sender.
[0066] It is worth noting that the seven fields of the message of the distributed storag...
Embodiment 2
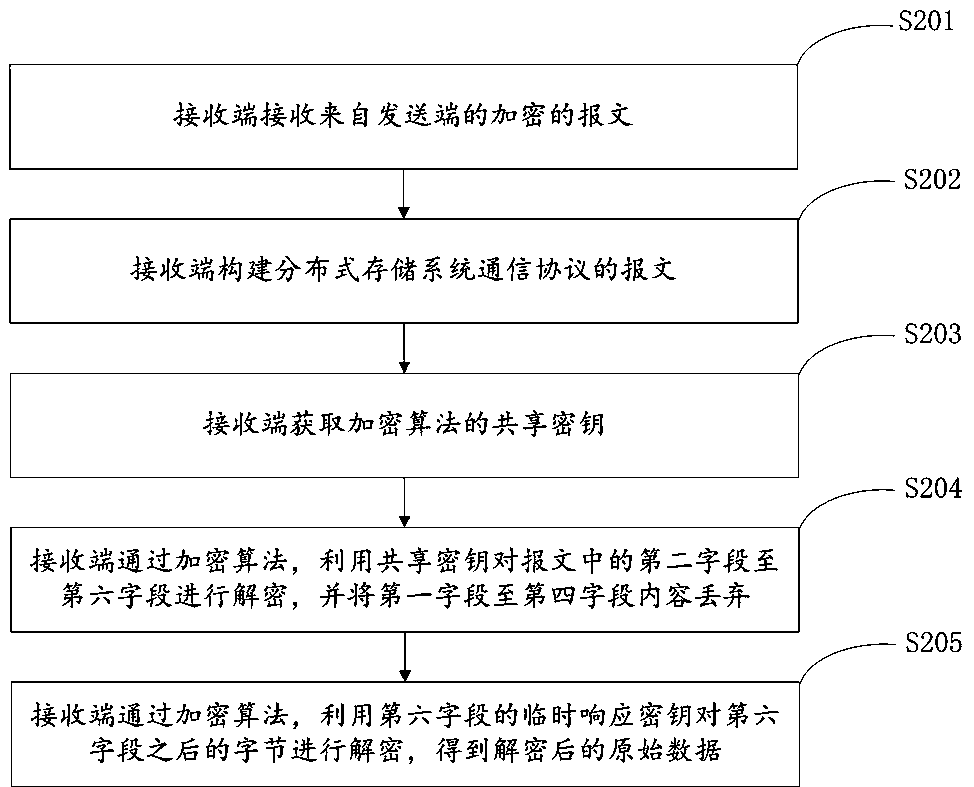
[0077] Please refer to figure 2 , a decryption method of a distributed storage system communication protocol, comprising the following steps:
[0078] Step S201: the receiving end receives the encrypted message from the sending end.
[0079] Step S202: The receiving end constructs a message of the distributed storage system communication protocol. The message of the distributed storage system communication protocol includes seven fields, wherein the first field is a random number occupying one byte, and the second field is a random number occupying one byte. The four-byte magic number 0x195E8FF1, the third field is the length value of the fourth field, which occupies one byte, the fourth field is garbage text with random length and random content, the fifth field is the temporary request key, and the sixth field It is the temporary response key, and the seventh field is the original data to be decrypted on the receiving end.
[0080] Step S203: the receiving end obtains the...
Embodiment 3
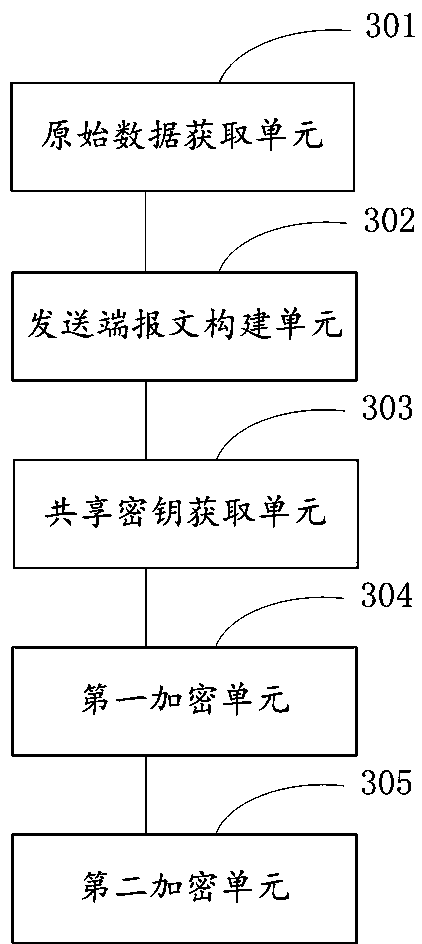
[0091] Please refer to image 3 , an encryption device for a distributed storage system communication protocol, comprising the following units:
[0092] An original data obtaining unit 301, configured for the sending end to obtain the original data to be encrypted;
[0093] The message construction unit 302 at the sending end is used for the sending end to construct a message of the distributed storage system communication protocol. The message of the distributed storage system communication protocol includes seven fields, wherein the first field is a random field occupying one byte. number, the second field is a magic number that occupies four bytes, the third field is the length value of the fourth field that occupies one byte, the fourth field is garbage text with random length and random content, and the fifth field is a temporary request key, the sixth field is the temporary response key, and the seventh field is the original data to be encrypted on the sender;
[0094] S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com