Method and device for identifying access attacks
A technology of identification and sequence, applied in the field of network security, can solve problems such as maintenance problems, high cost, increase in computational complexity and system complexity, and achieve the effects of good versatility, shielding differences, and effective identification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
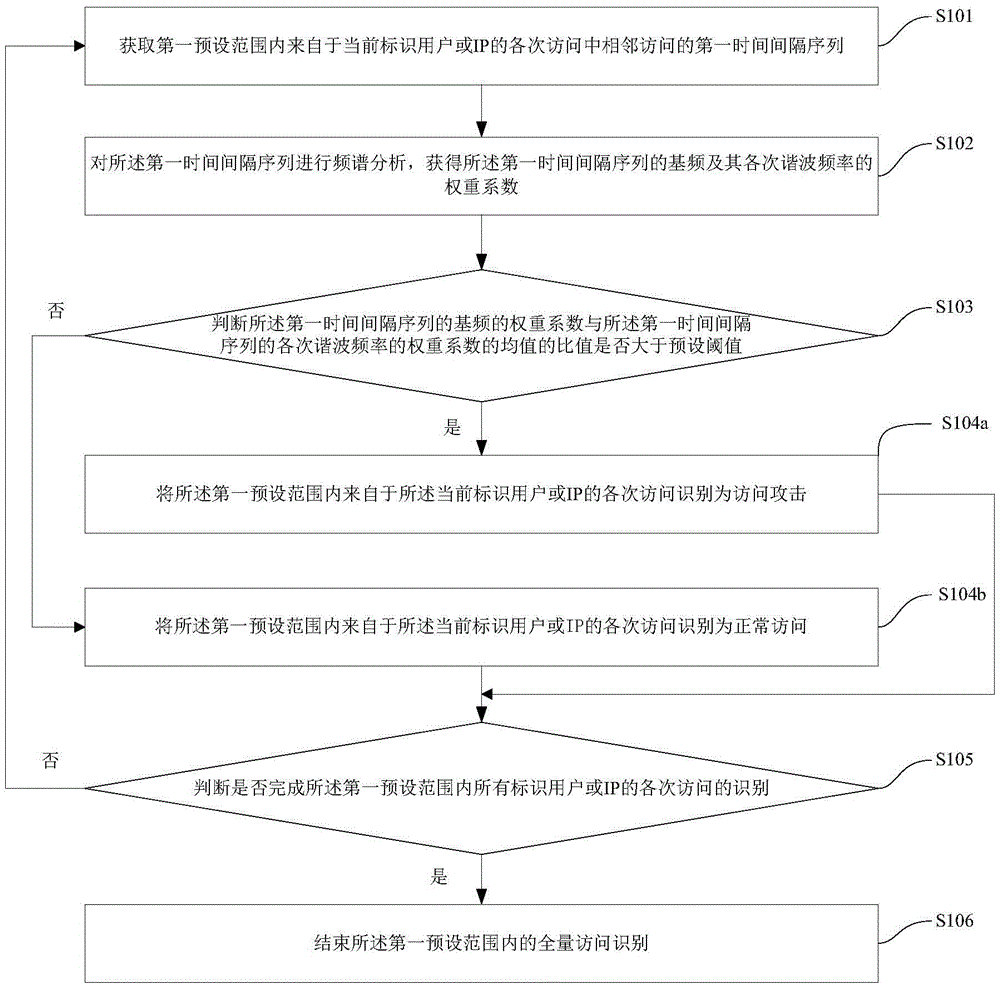
[0026] In order to make the purposes, technical solutions and advantages of the embodiments of the present application more clearly understood, the embodiments of the present application will be described in further detail below with reference to the embodiments and the accompanying drawings. Here, the exemplary embodiments and descriptions of the embodiments of the present application are used to explain the embodiments of the present application, but are not intended to limit the embodiments of the present application.
[0027] The inventor of the present application found that access attacks are generally initiated by network robots, and the time interval of these access attacks initiated by network robots is generally periodic, that is to say, the access characteristics of network robots are usually: every adjacent The time interval between the two visits is fixed, such as Figure 4 shown. However, even if the visit of a certain source has a very obvious periodicity in ti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com