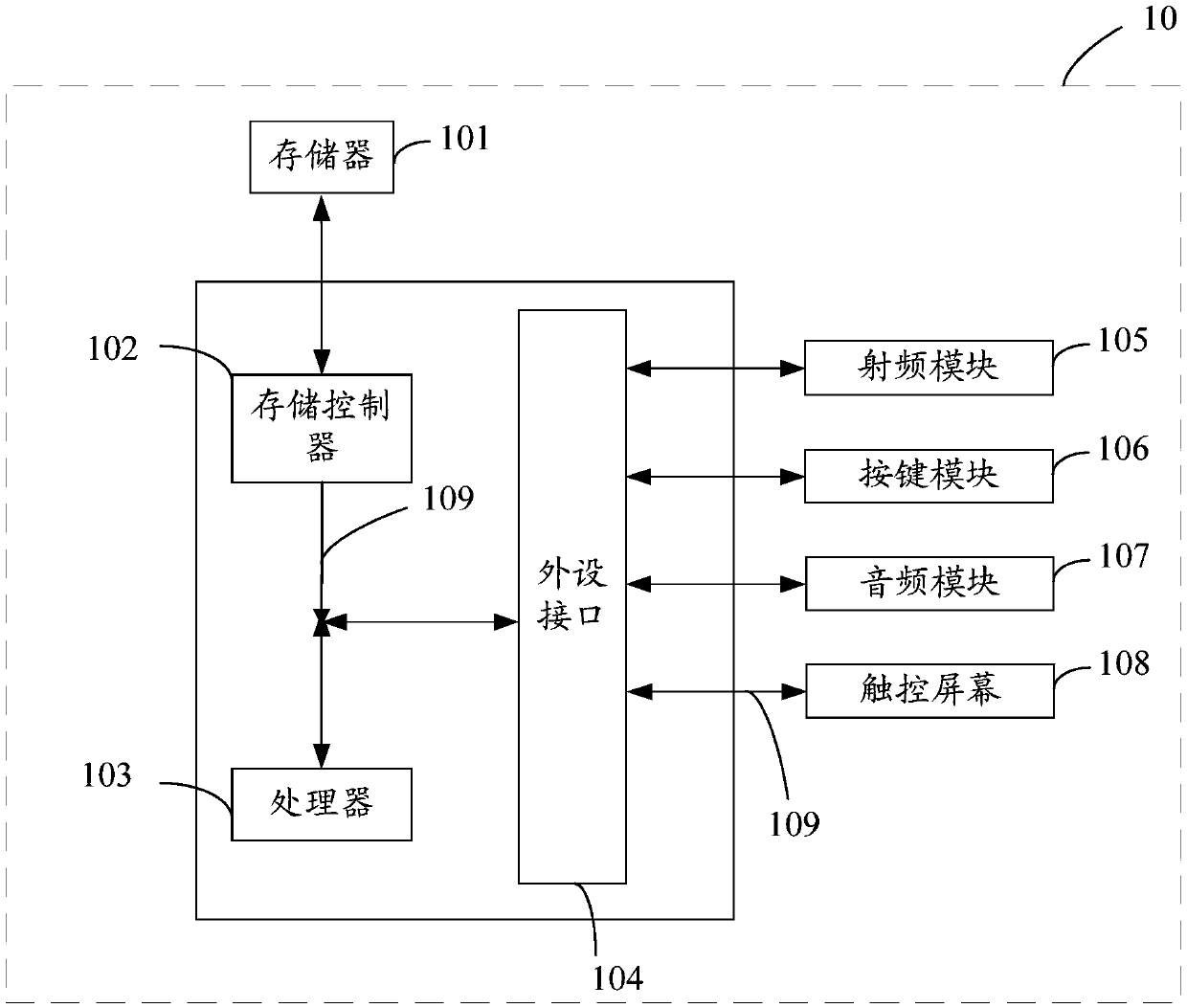
Patents
Literature
103results about How to "Shielding differences" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
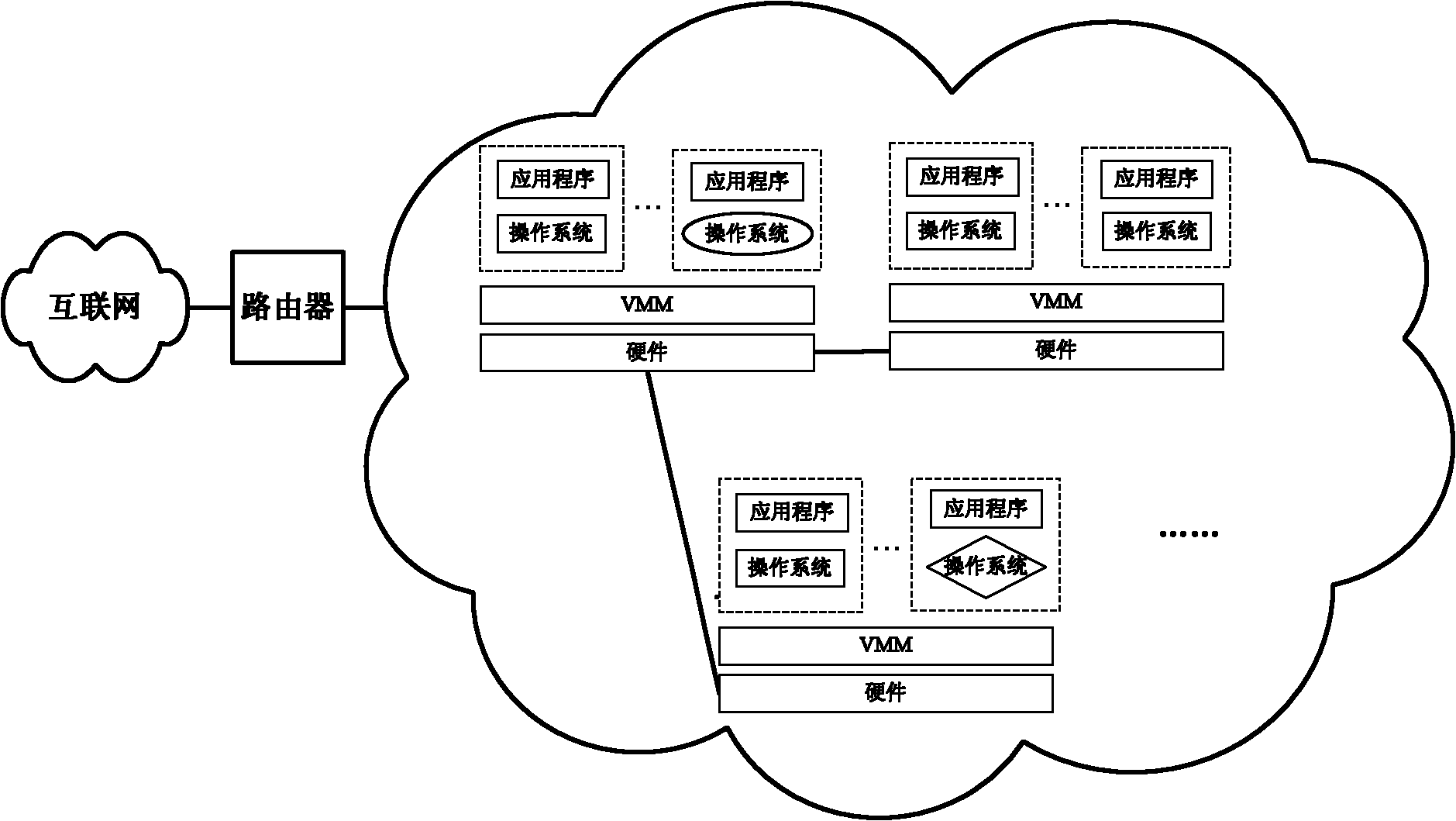
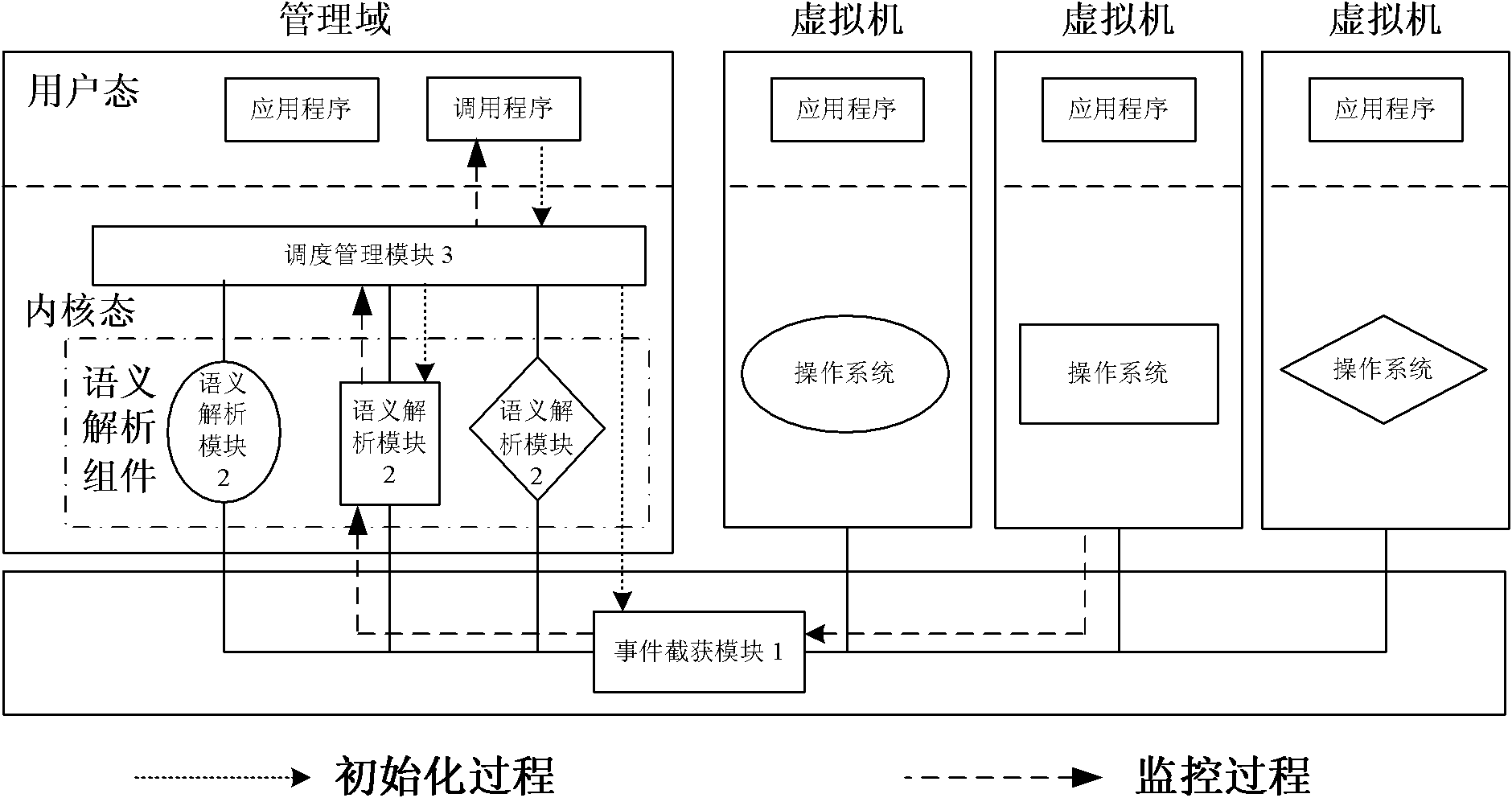
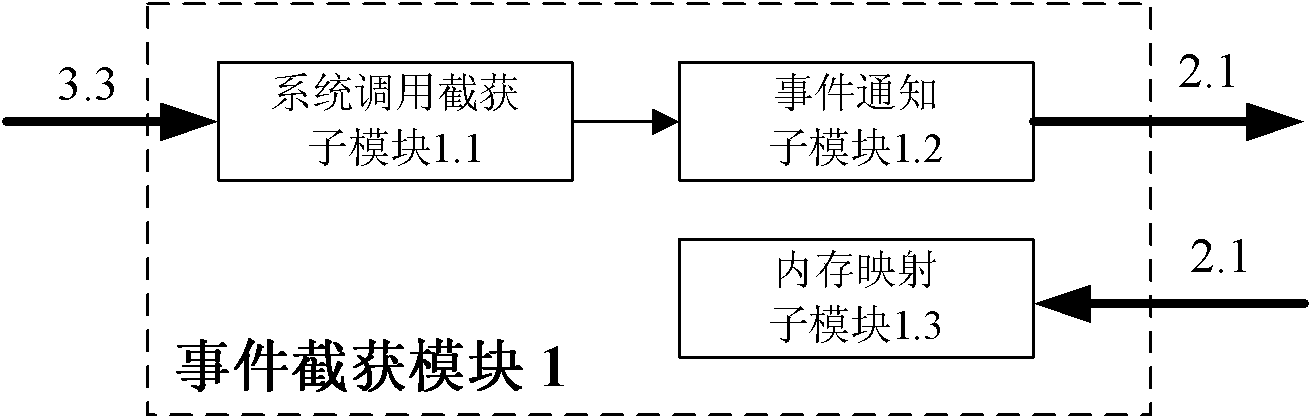
Universal virtual machine monitoring system based on driving
InactiveCN101923507AImplement general monitoringEffective monitoringHardware monitoringOperational systemMonitoring system
The invention relates to a universal virtual machine monitoring system based on driving, and the system comprises an event interception module, a semantic meaning analysis module and a scheduling management module. The event interception module and the semantic meaning analysis module are separated, wherein the event interception module intercepts a system call in a virtual machine on a virtual machine manager and then informs the semantic meaning analysis module in a management domain. The semantic meaning analysis module comprises definitions of key data structures of a kernel of the virtual machine, and the semantic meaning analysis module needs to be matched with the event interception module in the process of recovering the semantic meaning. The semantic meaning analysis module recovers the semantic meaning of the intercepted virtual machine related information, thus restoring operating system grade semantic meaning. The scheduling management module transmits all monitoring information to the monitoring system and provides a unified monitoring interface for the monitoring system. The system achieves the aim of monitoring operating systems of all types in unification and shields the differences of the operating systems in the virtual machine, thus realizing the universality of the monitoring function.
Owner:HUAZHONG UNIV OF SCI & TECH
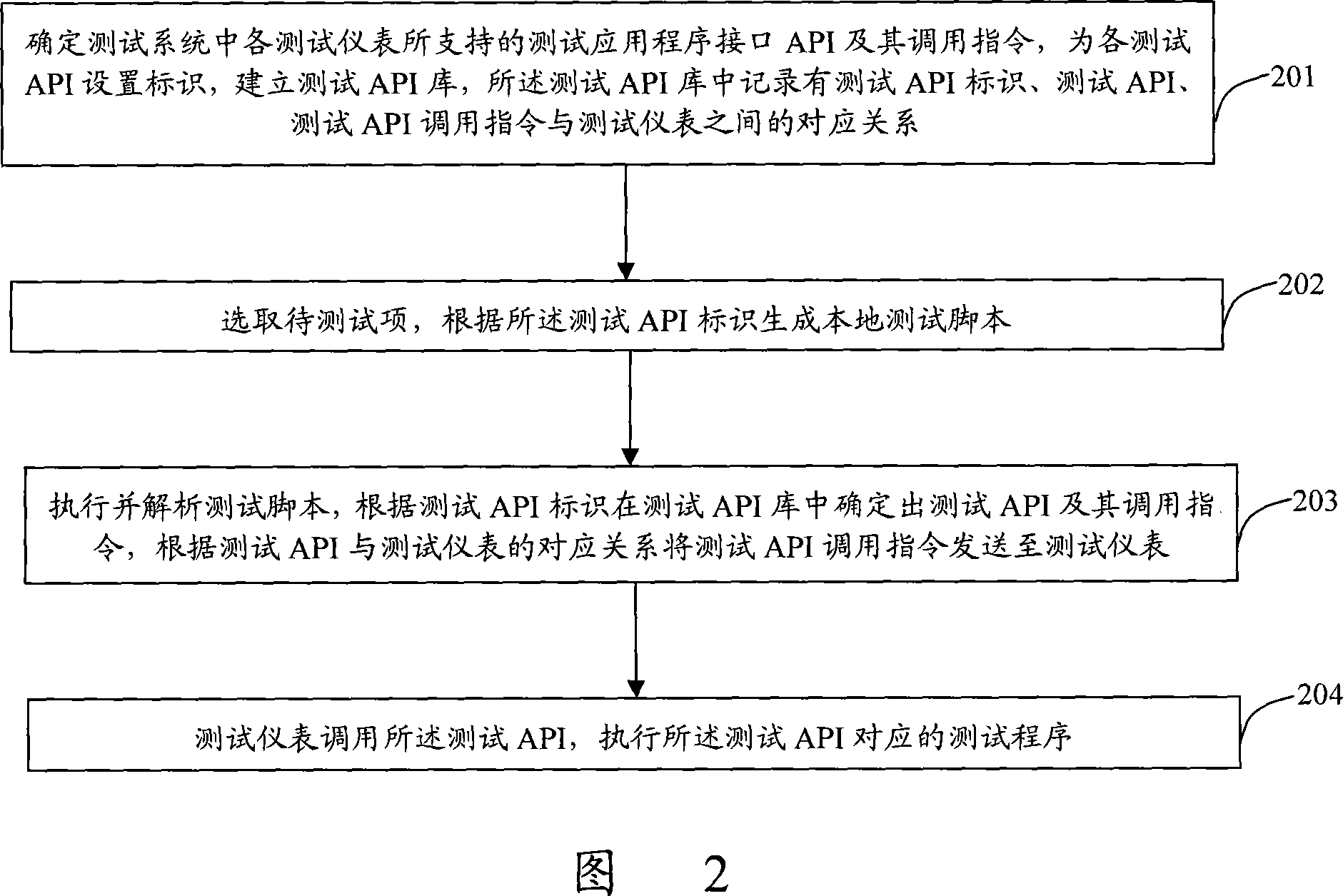
Automatic testing method based on application program interface
ActiveCN101227345AShielding differencesEasy to useRadio/inductive link selection arrangementsData switching networksTest scriptApplication programming interface
The invention discloses an automatic testing method which is base on an application program interface, which relates to a measuring and testing technique which is based on a test instrumentation, and is put forward for solving miscellaneous testing methods which are based on test instrumentation at present. The proposal which is adopted comprises assuring test application program interface API and call instruction thereof which are supported by each test instrumentation in a testing system, setting marks for each test API, establishing test API base, testing the corresponded relationship between the test API base which is recorded with test API mark, test API and test API call instruction and test instrumentation, choosing a tested term, generating local test script according to the test API mark, executing and analyzing the test script, assuring the test API and call instruction thereof, sending the test API call instruction to the test instrumentation according to the corresponded relationship between the test API and the test instrumentation, calling the test API by the test instrumentation, and executing the corresponded test procedure of the test API. The invention achieves simple operation and low maintenance cost.
Owner:ZTE CORP
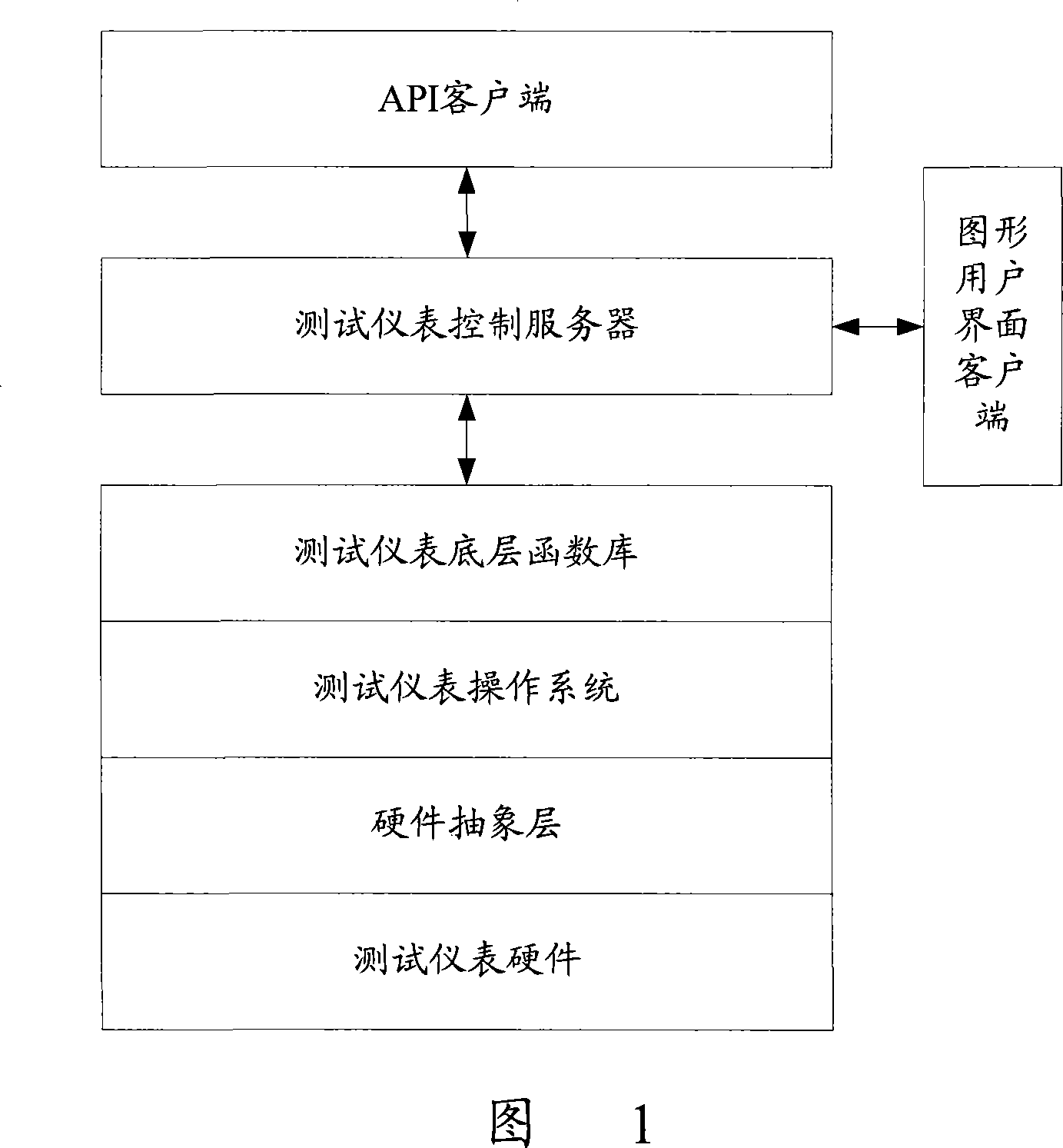
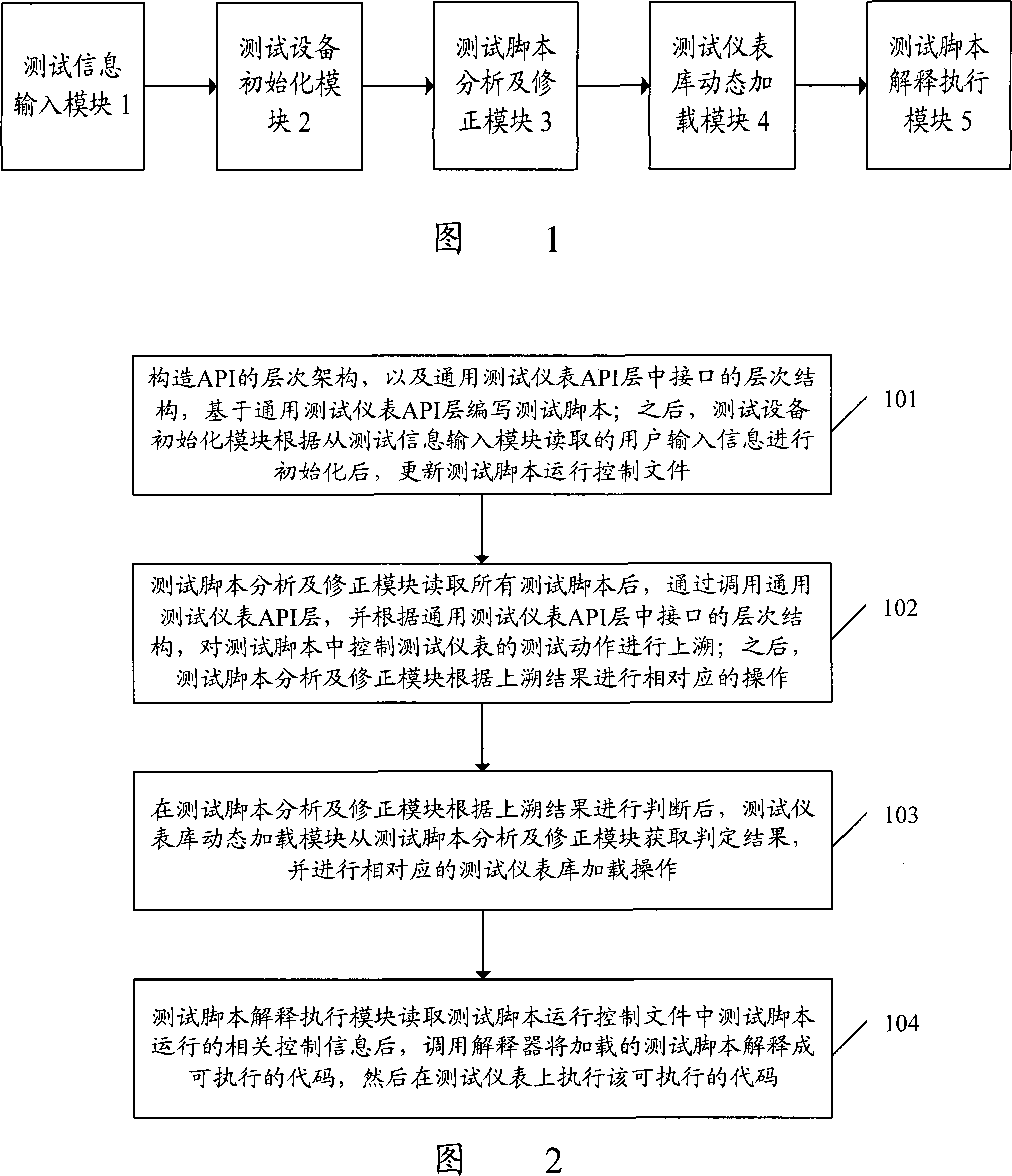
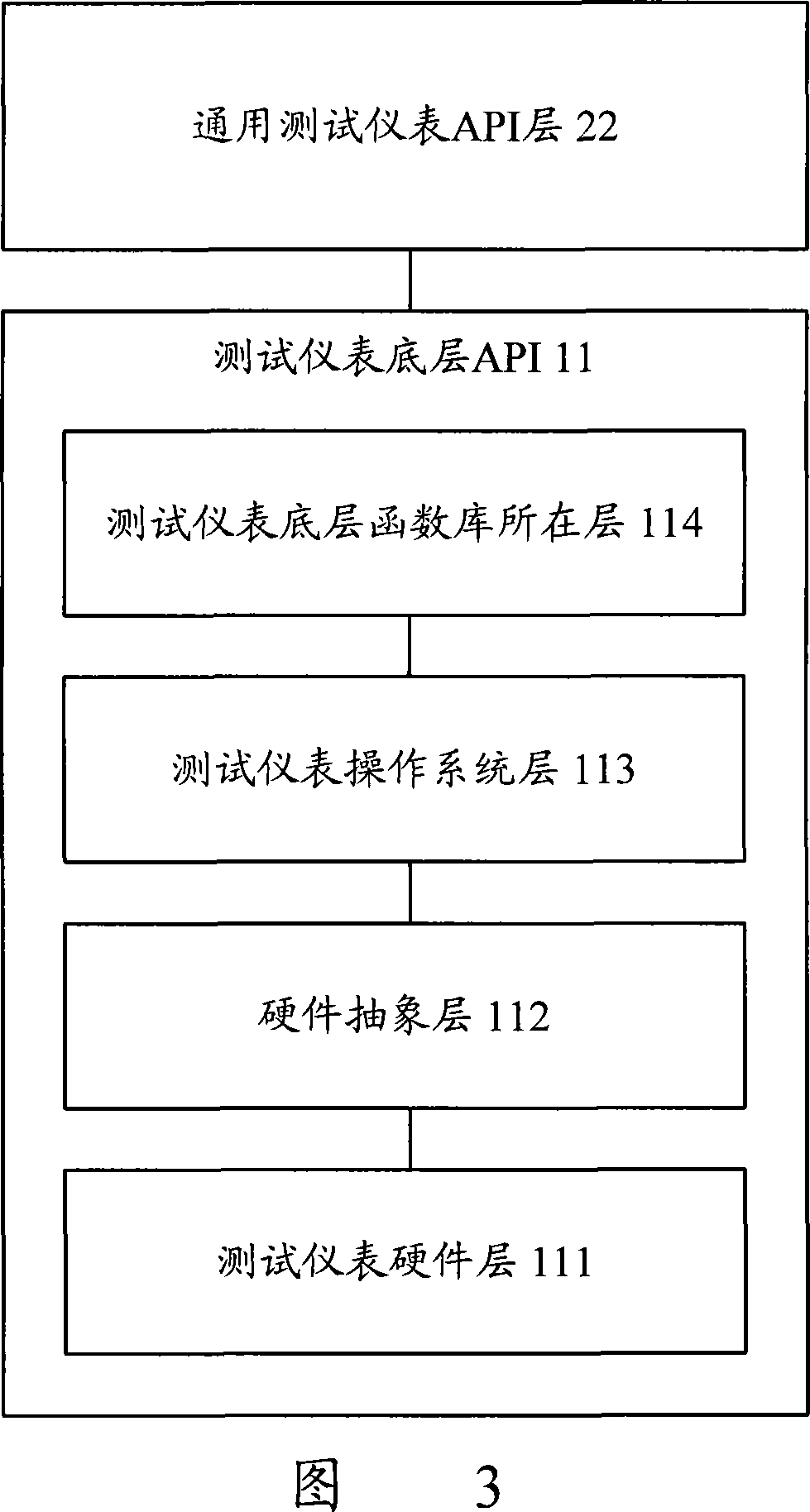
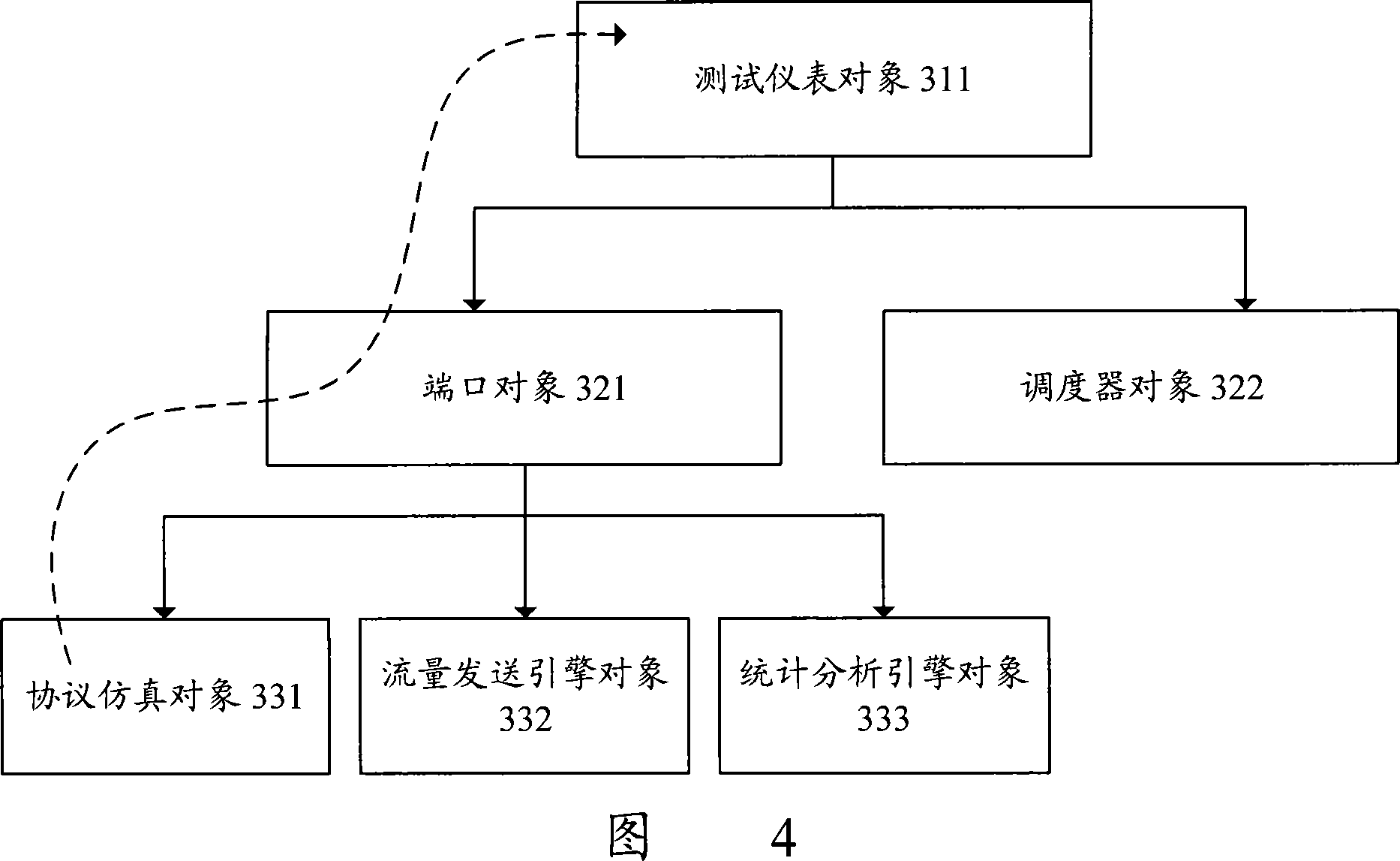
Test equipment and method based on universal test meter API
ActiveCN101247292AImprove writing efficiencyImprove versatilityRadio/inductive link selection arrangementsData switching networksTest scriptLevel structure
The invention discloses a test equipment based on the general test meter application programming joint. The equipment comprises a test information input module, a test equipment initializing module, a test script explanation executing module, a test script analysis and amendment module, and a test meter base dynamic load module. Wherein, the test script analysis and amendment module is used for tracing the test action controlling test meter in the test script by transferring the general test meter application program joint (API) layer, according to the level structure of the joint in the general test meter API layer. The test meter base dynamic load module is used for obtaining judgment result from the test script analysis and amendment module, with corresponding load operation of test meter base. The invention further discloses a test method based on the general test meter application programming joint. By adopting the test equipment and method of the invention, the test instrument is enabled to satisfy the requirement in using efficiency for favorable and rapid operation test.
Owner:ZTE CORP
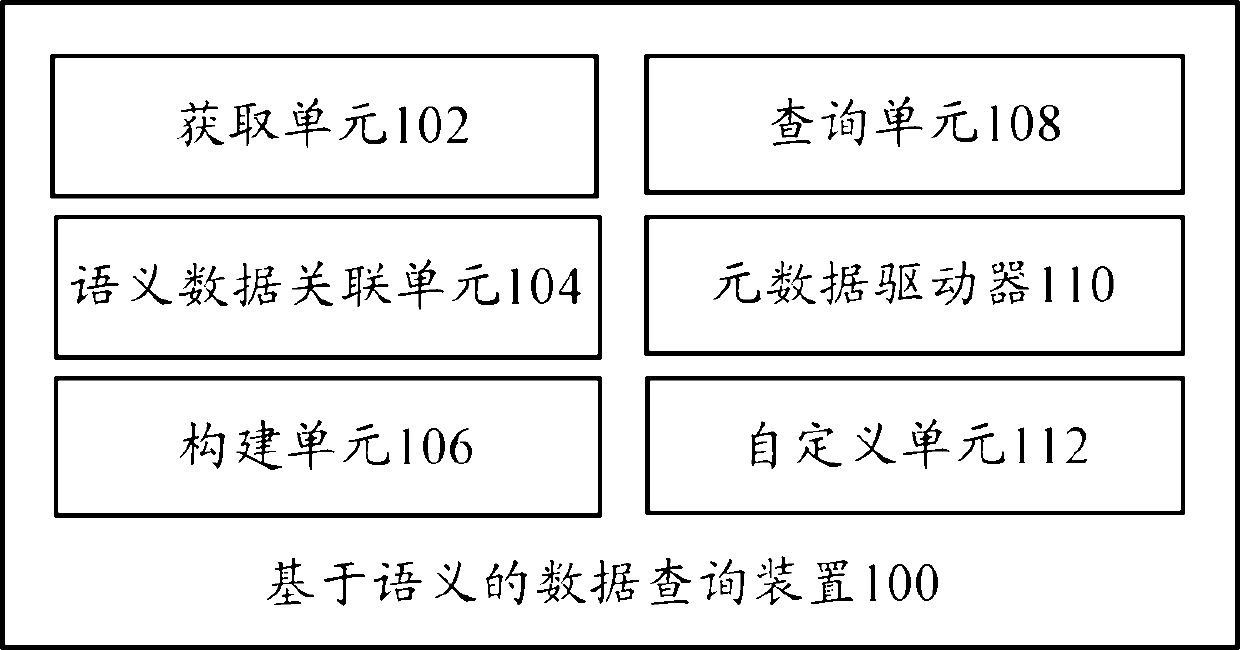
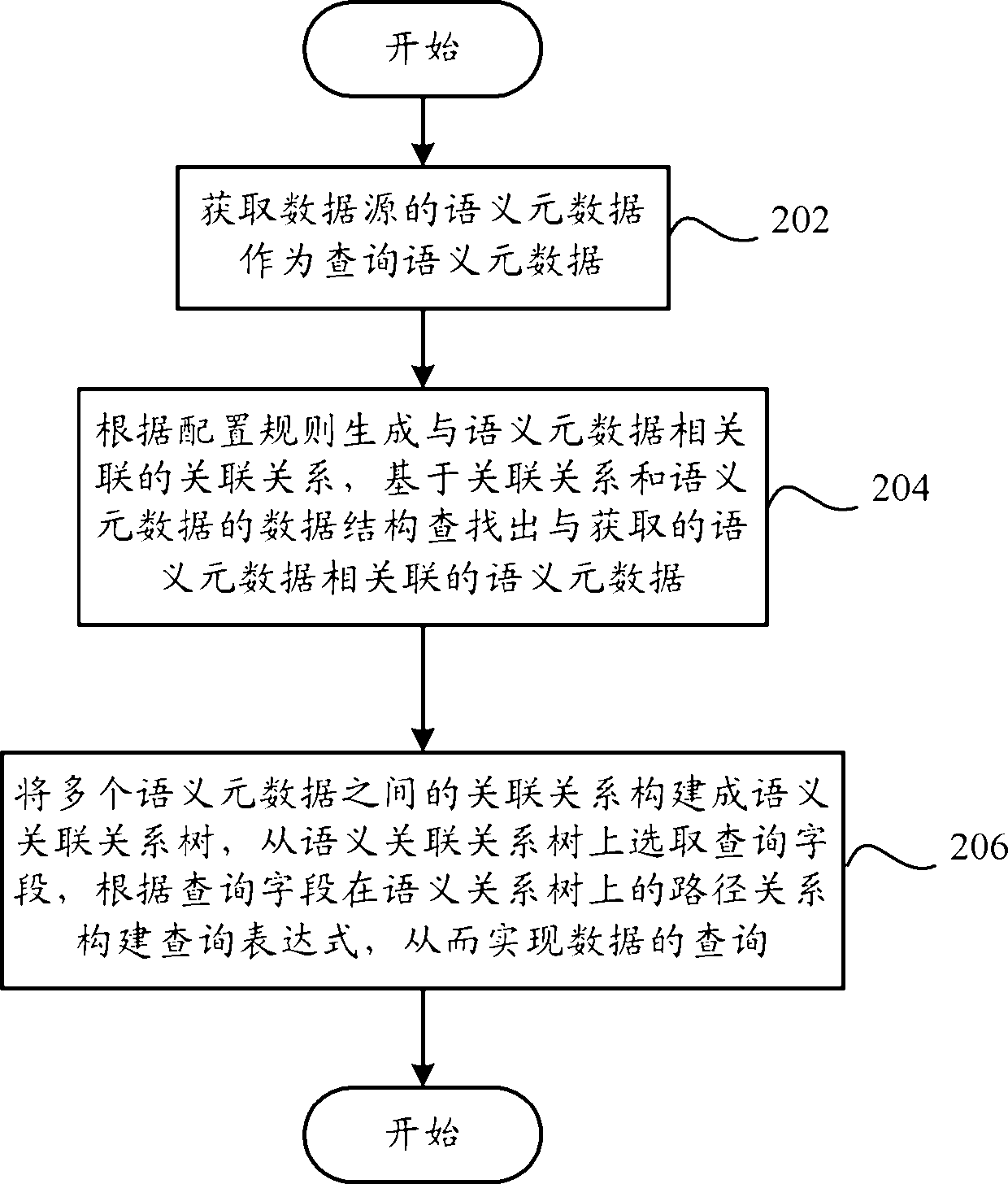
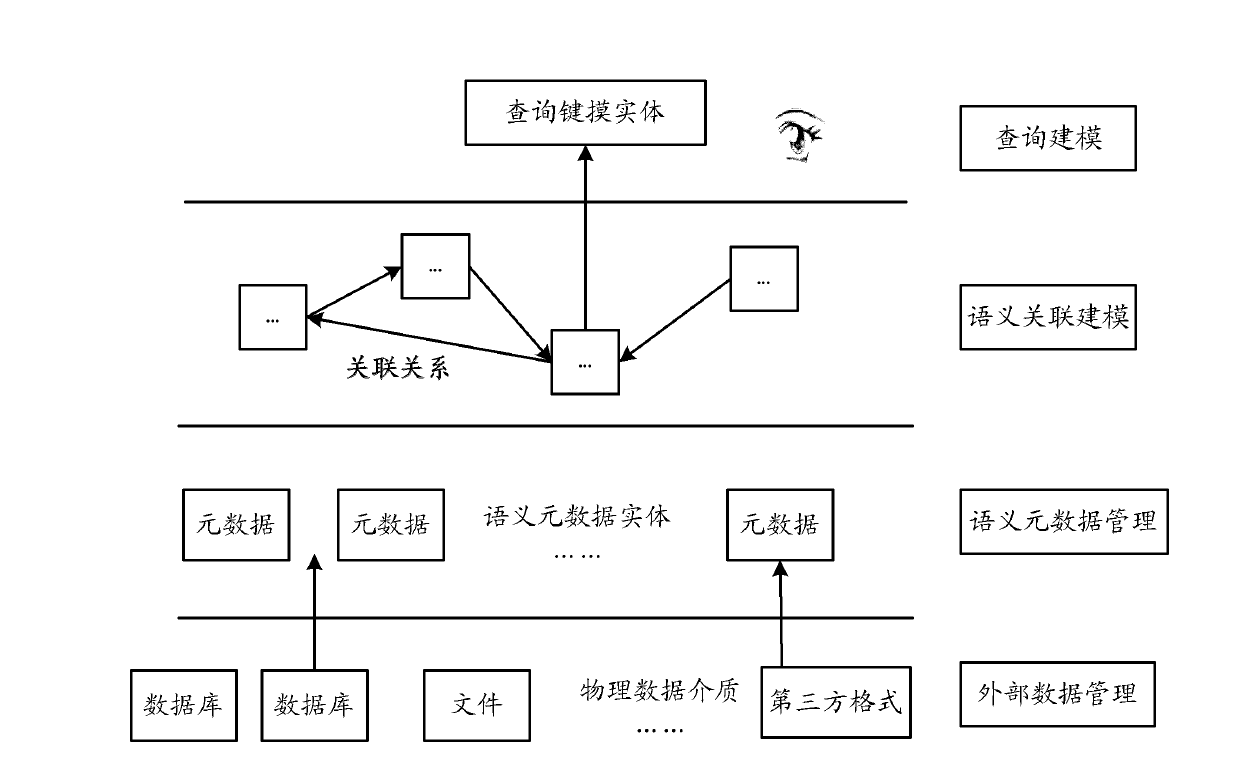
Data query device and data query method based on semanteme
InactiveCN102591952AShielding differencesReduce difficultySpecial data processing applicationsData queryMetadata
The invention provides a data query device based on semantem. The device comprises: an acquiring unit, a semantic data association unit, an establishing unit, and a query unit, wherein the acquiring unit is used for acquiring the semantic metadata of a data source as semantic metadata for query; the semantic data association unit is used for generating an association associated with the semantic metadata according to configuration rules and searching the semantic metadata associated with the acquired semantic metadata based on a data structure of the association and the semantic metadata; the establishing unit is used for establishing a semantic association tree from the associations among multiple semantic metadata; and the query unit is used for selecting a query field from the semantic association tree established by the establishing unit and establishing a query expression according to a path relationship of the query field on the semantic association tree, so that the data can be queried. Accordingly, the invention provides a data query method based on the semanteme. Through the technical scheme, the difference of the underlaying data is shielded, the query modeling difficulty is reduced, the modeling efficiency is increased and the expandability is also guaranteed.
Owner:YONYOU
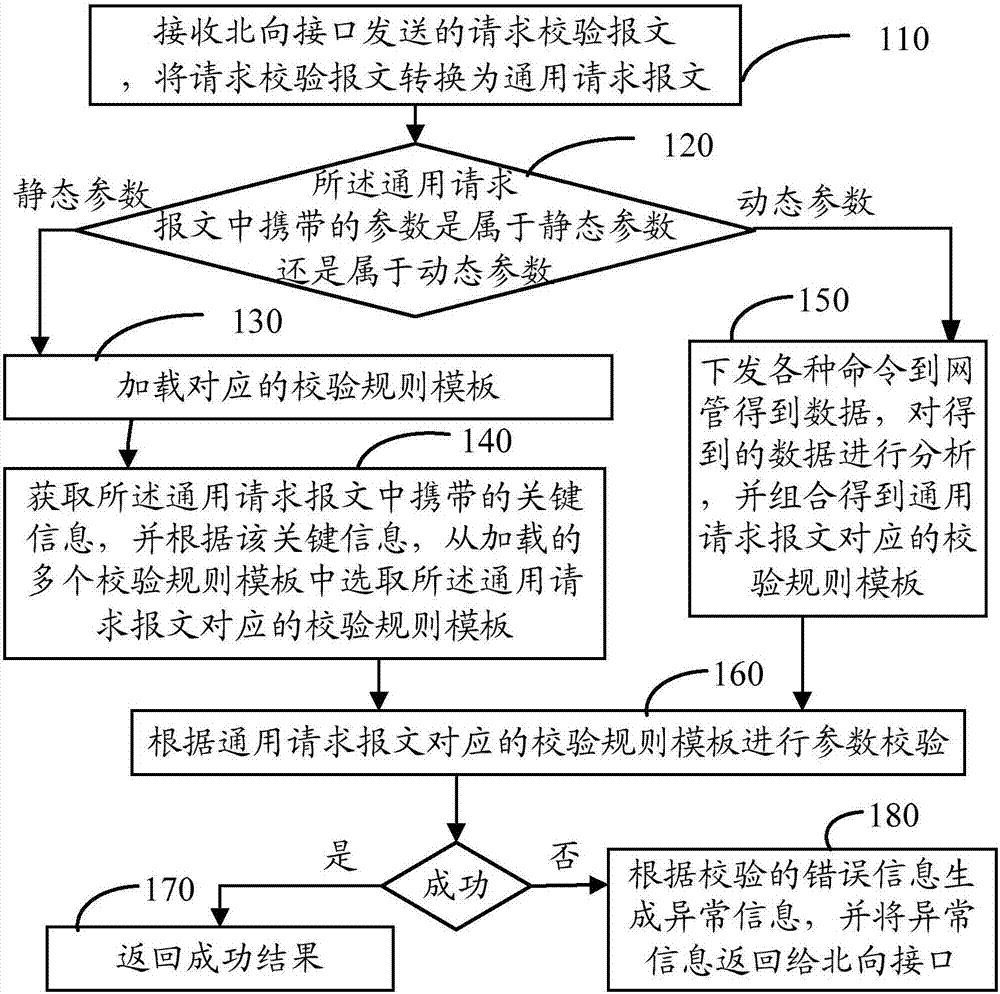
Parameter verification method and device and network management server
InactiveCN107579836AReduce maintenance costsImprove development efficiencyData switching networksNetwork managementData combination
The invention discloses a parameter verification method and device and a network management server. The method comprises the steps of distinguishing whether the parameters carried in a universal request message belong to static parameters or dynamic parameters; when the parameters are static parameters, selecting a verification rule template corresponding to the general request message from a plurality of preset verification rule templates; when the parameters are dynamic parameters, obtaining the verification rule template corresponding to the universal request message according to the data combination obtained by the network management. According to the scheme, a parameter verification scheme is provided, and the code reuse rate is high. When the parameter verification scheme is appliedto different equipment, a corresponding verification rule template can be selected from a plurality of preset verification rule templates, or a corresponding verification rule template is obtained through dynamic combination, and parameter verification is completed according to the verification rule template, so that the development of the northbound interface is easy to add. The difference of various equipment is shielded, and the maintenance cost of codes is reduced.
Owner:ZTE CORP
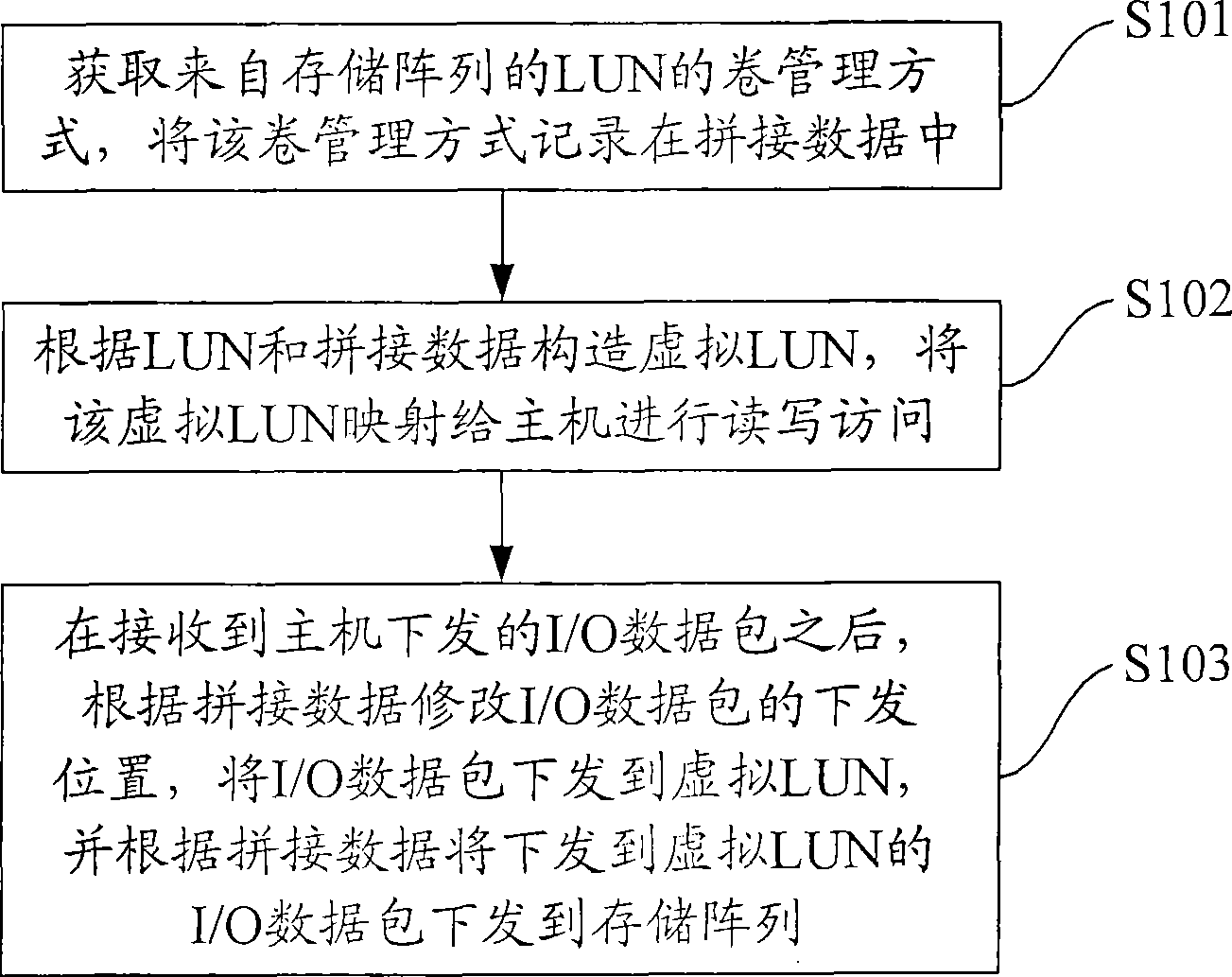
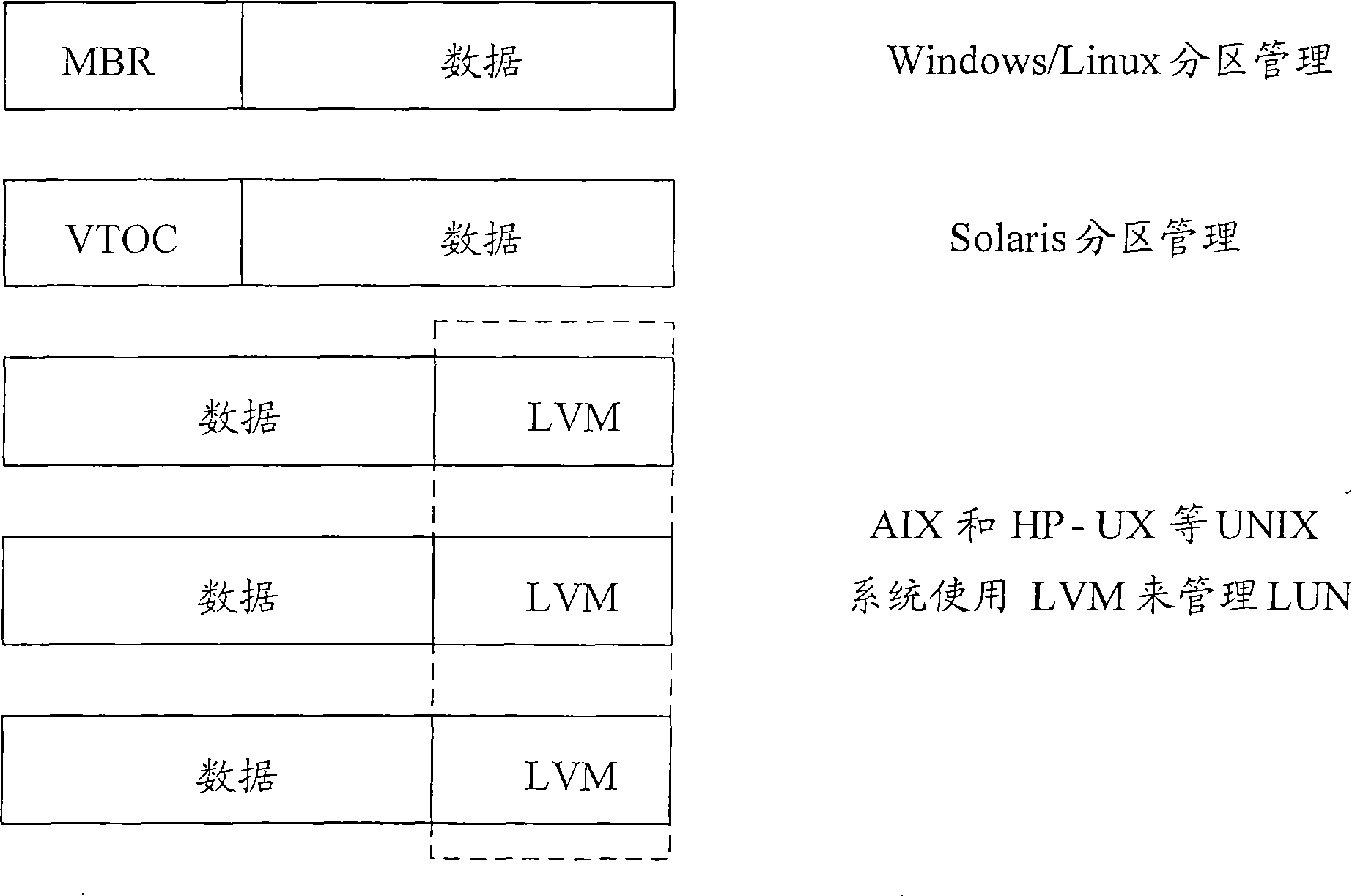
Virtual memory method and apparatus
ActiveCN101477444AAchieving Storage ConvergenceShielding differencesInput/output to record carriersVirtual memoryNetwork packet
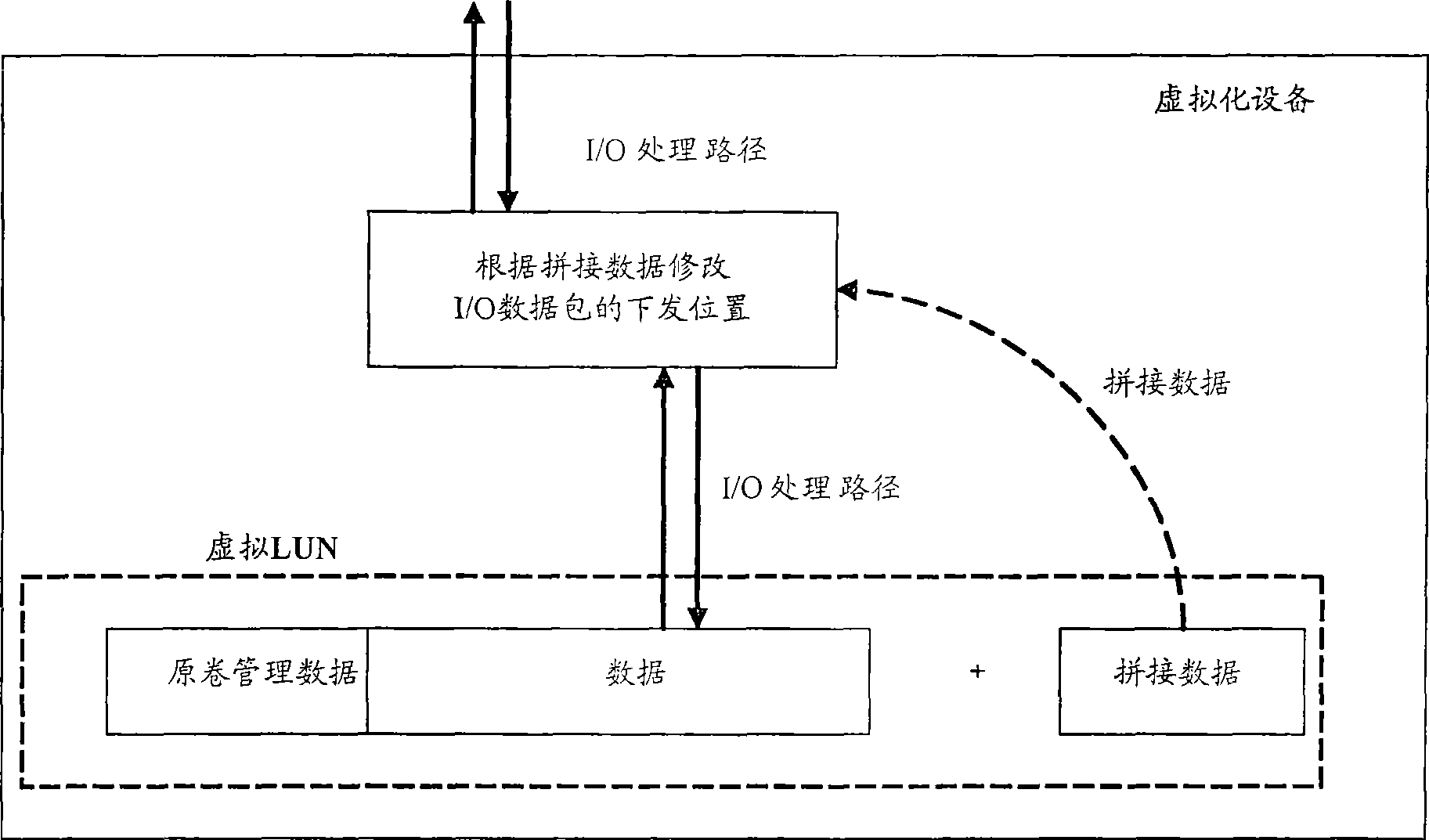
The embodiment of the invention discloses a method and a device for the virtual memory. The method comprises the following steps: acquiring a volume managing manner of a logic unit LUN of a memory array, and recording the volume managing manner in splicing data; constructing a virtual LUN according to the LUN and the splicing data, and mapping the virtual LUN onto to the host for being read, written and accessed; modifying the destination address of the I / O data packet according to the splicing data after the receipt of an input I / output O data packet delivered by the host, delivering the I / O data packet to the virtual LUN, and delivering the I / O data packet delivered to the virtual LUN to the memory array according to the splicing data. In addition, the position for the delivery of I / O data packet to the memory array is the same as the destination address of the I / O data packet, which is not modified. The embodiment of the invention realizes the memory integration, and shields the difference caused by different hosts and volume managing manners coming from different system platforms.
Owner:CHENGDU HUAWEI TECH
Set-top-box-based triple play system and implementation method
InactiveCN102710647AShield network differencesRealize triple playTransmissionSelective content distributionWeb Services Description LanguageService content
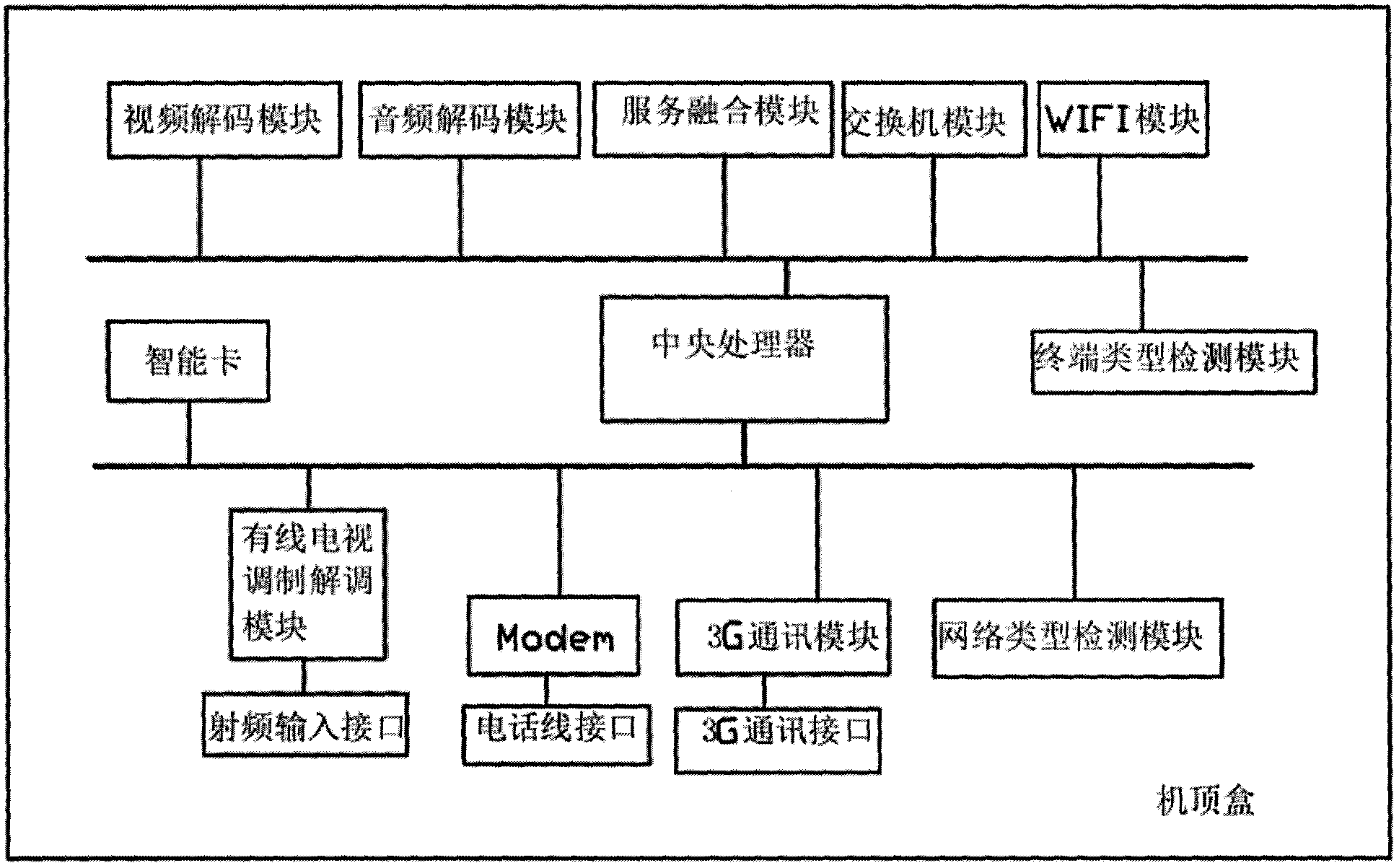
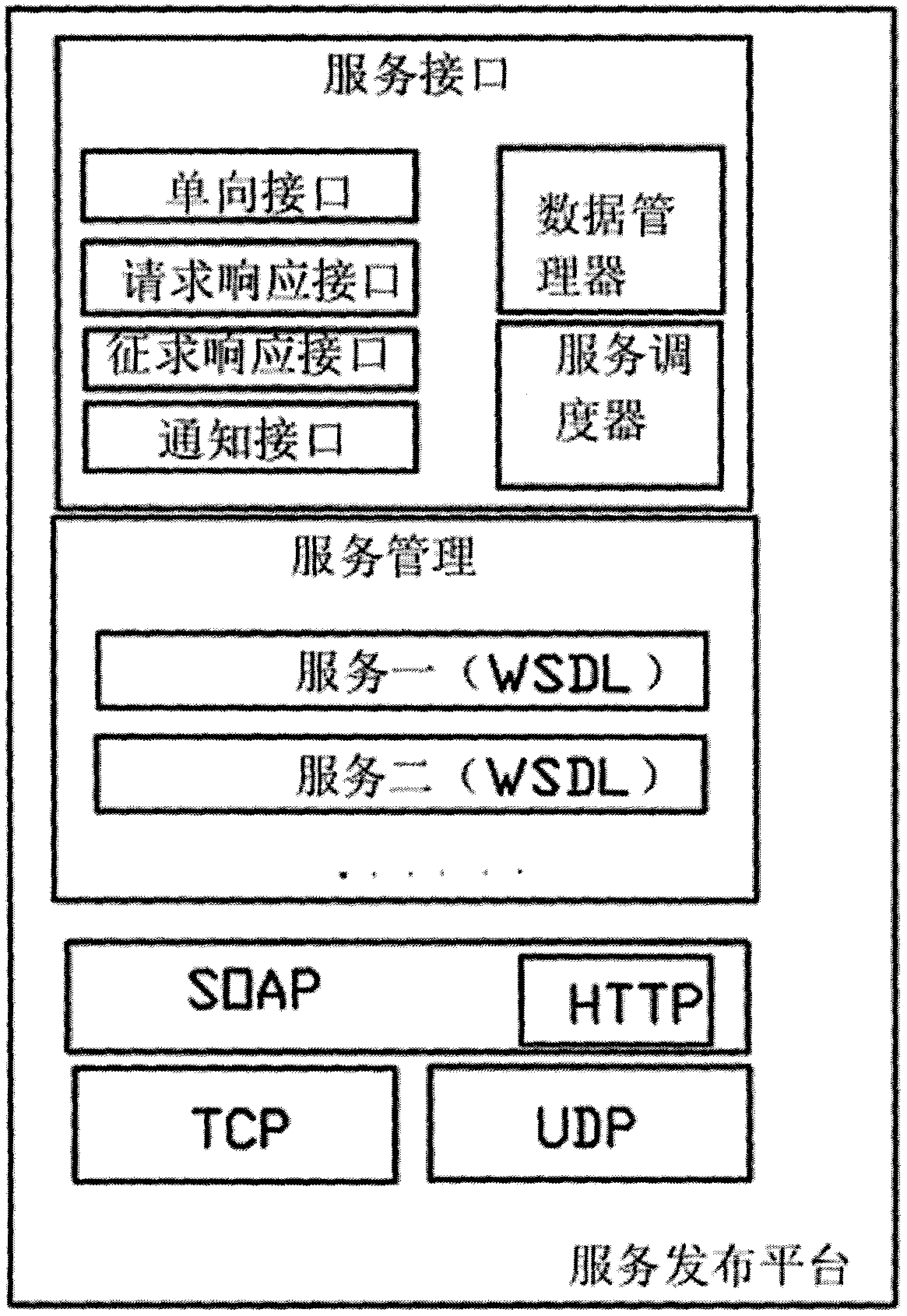
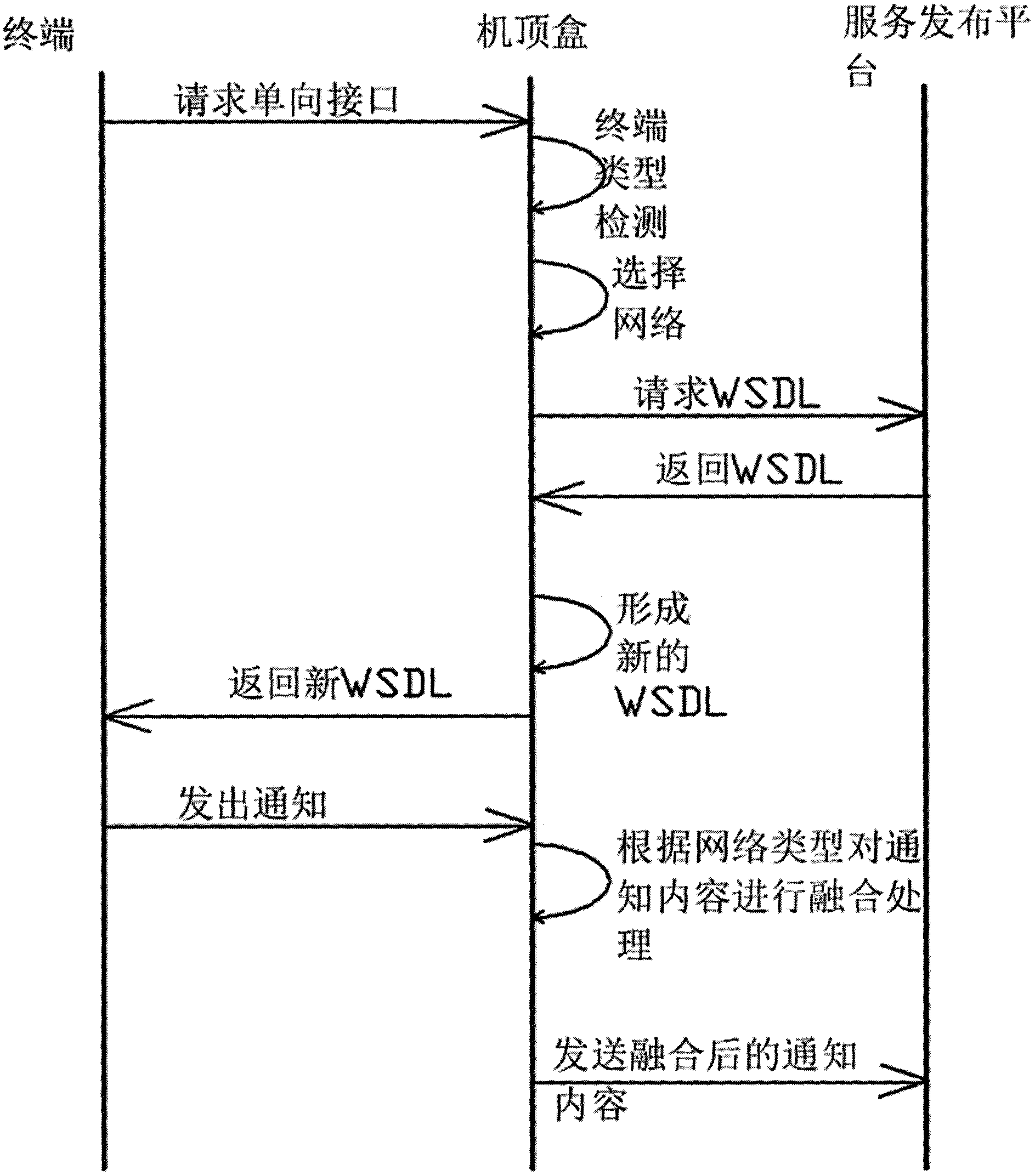
The invention discloses a set-top-box-based triple play system, which comprises one or more than one terminal, a set-top box and a service publication platform. Different terminals acquire service published by the service publication platform from different networks through the set-top box. The system is characterized in that the set-top box comprises a terminal type detection module, a network type detection module and a service fusion module, wherein the terminal type detection module is used for detecting and identifying the types of the terminals connected to the set-top box; the network type detection module is used for detecting the types of available networks, selecting one from the available networks as an interaction network for the terminals and the service publication platform, and identifying the types of the networks used for the terminals or the service publication platform to transmit requests; and the service fusion module is used for disintegrating a web services description language (WSDL) from the service publication platform, selecting proper sub-WSDLs according to detection results of the terminal type detection module and the network type detection module, combining the sub-WSDLs into a new WSDL, performing compression, transcoding, cutting and rendering on service contents by calling the other modules of the set-top box or chip resources, generating optimized service contents, and outputting the optimized service contents to different terminals.
Owner:GUANGDONG IKER DIGITAL TECH
Access protocol transfer method and system for multi-source heterogeneous remote sensing data system
InactiveCN103198137AMeet the data needs of multiple applicationsShielding differencesTransmissionSpecial data processing applicationsSensing dataIntelligent city
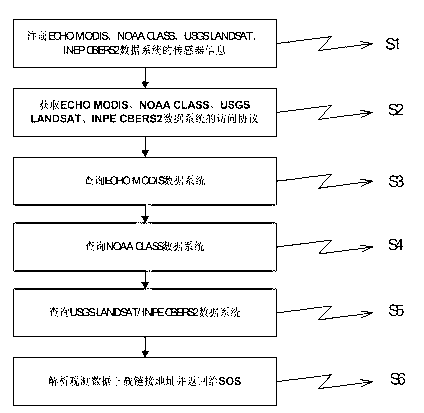
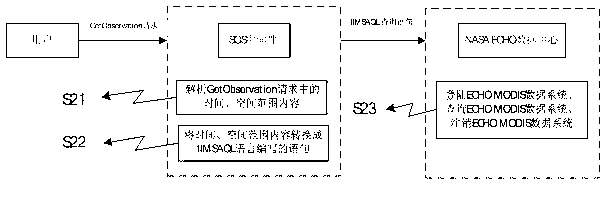
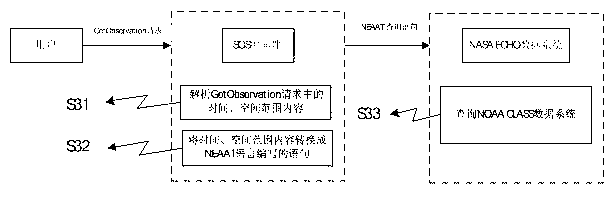
The invention discloses access protocol transfer method and system for a multi-source heterogeneous remote sensing data system and belongs to the technical field of intelligent city geographic information services. By establishing a sensor observation service middleware, the sensor observation service middleware can be connected with the remote sensing data system and access metadata information of the remote sensing data system in real time, can provide space-time range satisfying with customization and data of the remote sensing data system corresponding to special subjects for users, carry metadata information of the data system and feeds and displays to client sides in a regular coding formats. By the established sensor observation service middleware, difference of access interfaces of the multi-source heterogeneous remote sensing data system is eliminated, problems caused by protocols of the remote sensing data system are avoided, and protocols of data discovery of the multi-source heterogeneous remote sensing data system is normalized into external access protocols complied with sensor observation service standards.
Owner:WUHAN UNIV
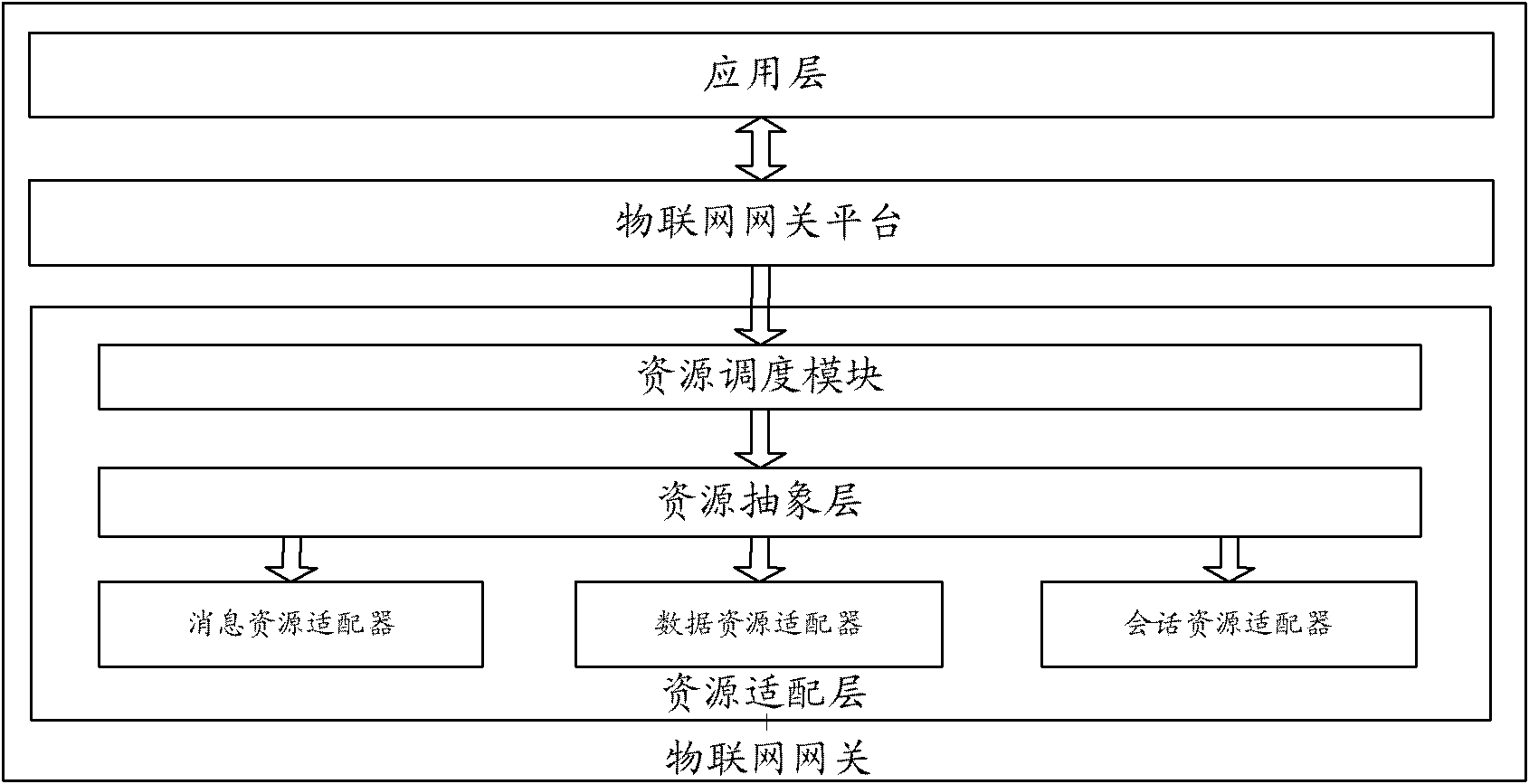
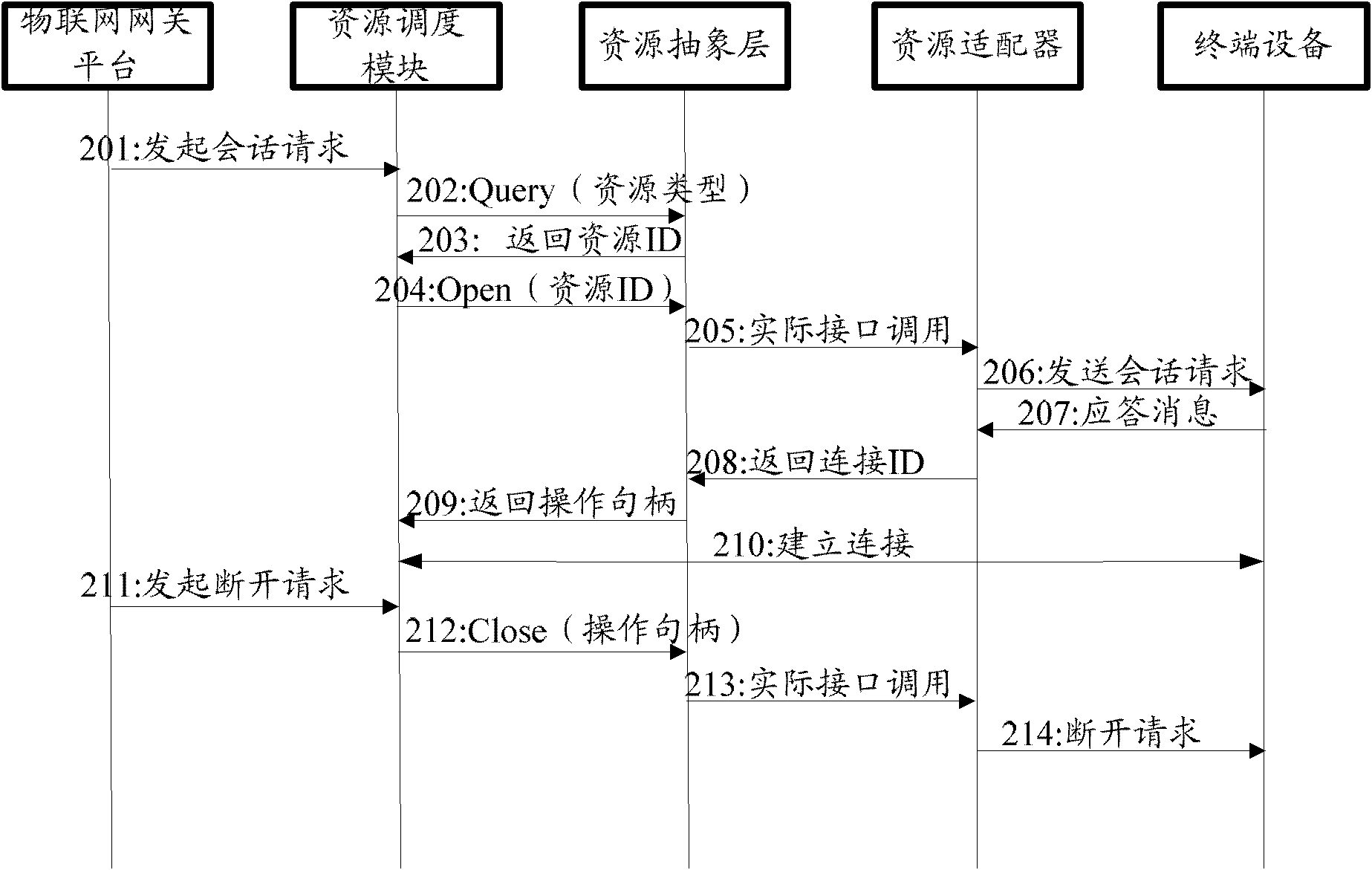
Method for carrying out operation on resource in Internet of things and apparatus thereof
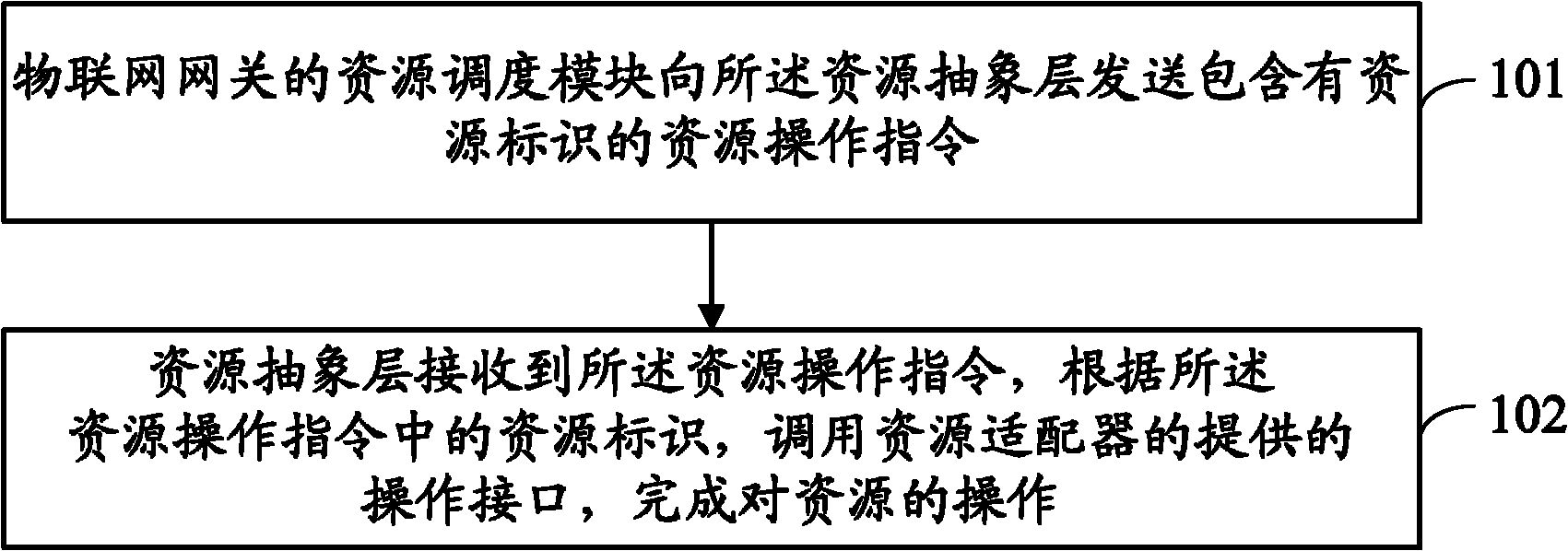
ActiveCN102740466ARealize the operationShielding differencesWireless communicationAbstraction layerIot gateway
The invention discloses a method for carrying out an operation on a resource in Internet of things. A resource abstraction layer and a resource scheduling module are added in an Internet of things gateway of the Internet of things. The method comprises the following steps that: the resource scheduling module in the Internet of things gateway sends a resource operation instruction comprising resource identification to the resource abstraction layer; the resource abstraction layer receives the resource operation instruction, calls operation interfaces provided by a resource adapter in the Internet of things gateway according to the resource identification in the resource operation instruction and completes the operation to the resource. The invention also discloses the Internet of things gateway used to operate the resource in the Internet of things. By using the method of the invention, differences between various kinds of resource operations are shielded and uniform operation management to the resource is realized.
Owner:ZTE CORP
Network topology construction method and device
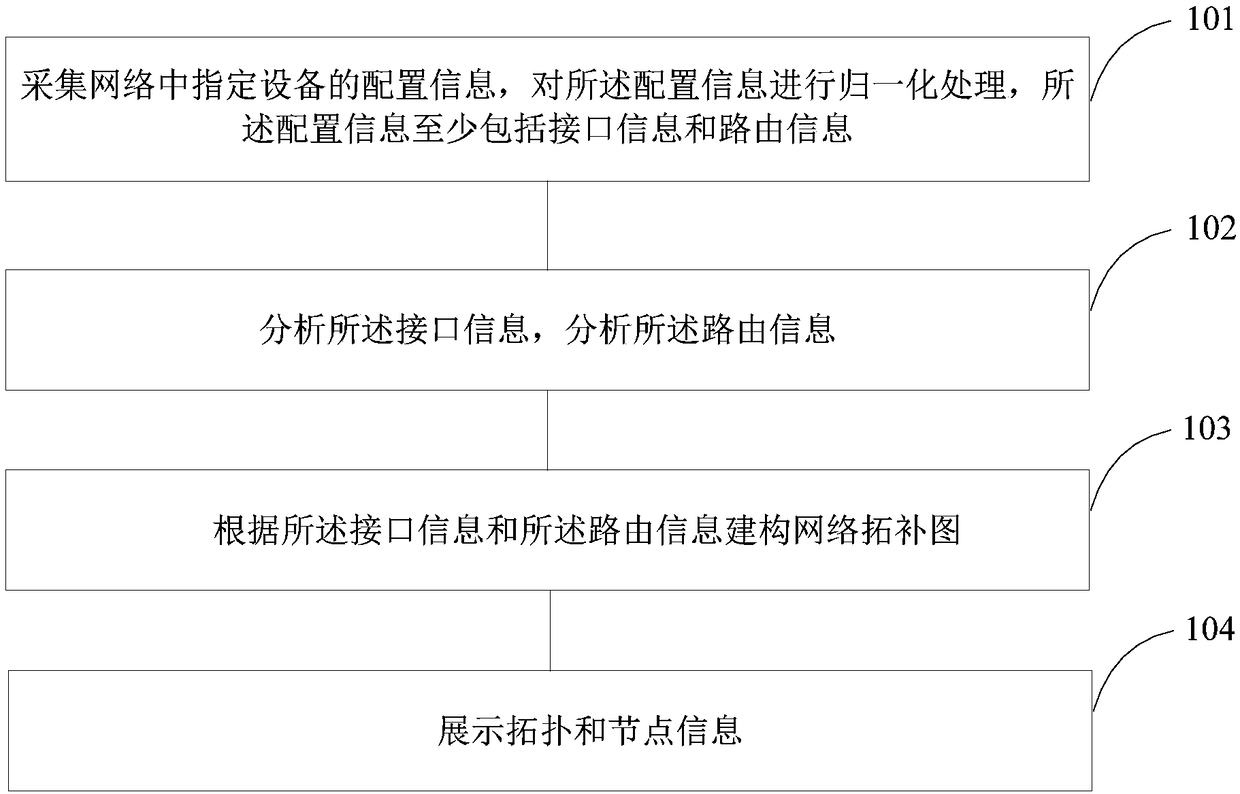
ActiveCN108880844ALow costShielding differencesData switching networksResource consumptionDistributed computing
The present invention discloses a network topology construction method comprising: collecting configuring information of a specified device in a network, and normalizing the configuring information, the configuring information at least including interface information and routing information; analyzing the interface information, and analyzing the routing information; and constructing a network topology map according to the interface information and the routing information. The present invention discloses a network topology construction device. The technical scheme can shield differences betweenmanufacturers' versions to reduce resource consumption.
Owner:ZTE CORP
Method and device for identifying access attacks
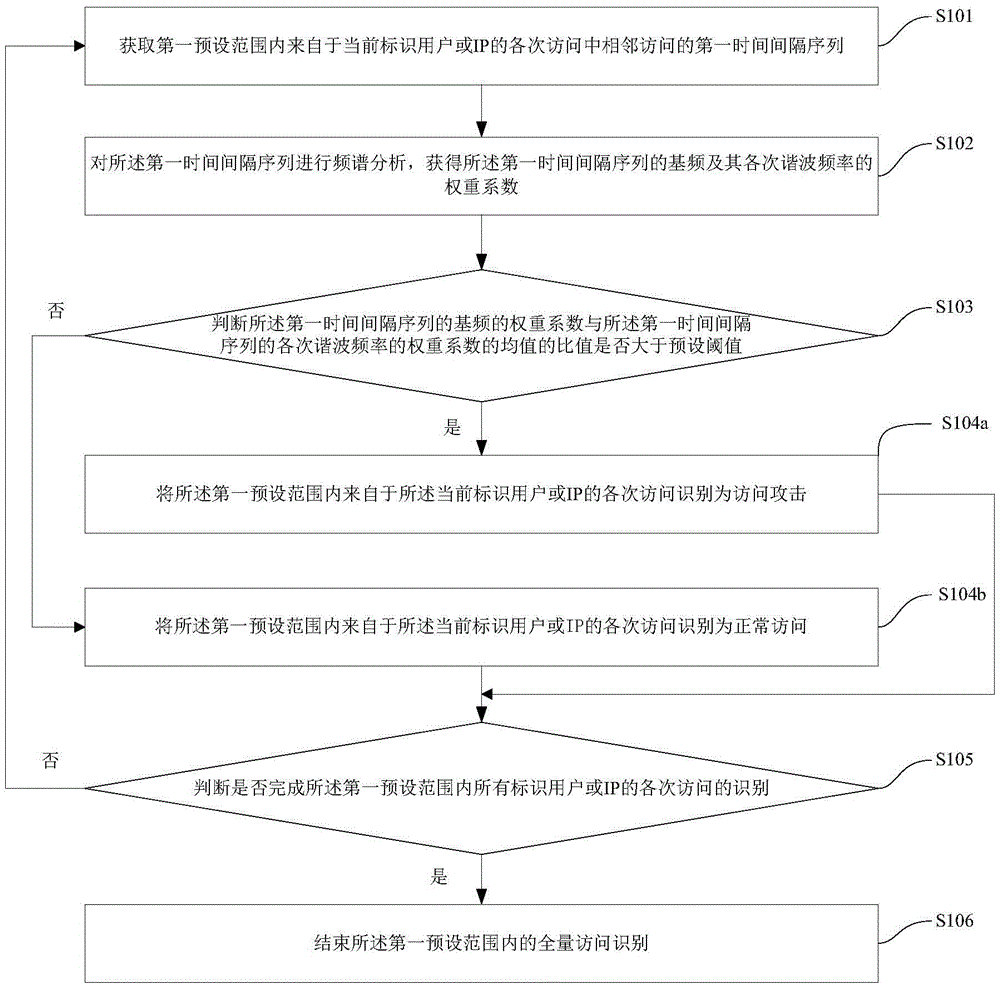
ActiveCN106850511AShielding differencesEfficient identificationTransmissionFrequency spectrumTelecommunications
The embodiment of the application provides a method and device for identifying access attacks. The method comprises the following steps: acquiring a first time interval sequence of the adjacent access in each access from the current identification user or IP in a first preset range; implementing spectrum analysis on the first time interval sequence to obtain the weight coefficients of the fundamental frequency and each subharmonic frequency of the first time interval sequence; judging whether the ratio of the weight coefficient of the fundamental frequency of the first time interval sequence to the average value of the weight coefficients of each subharmonic frequency of the first time interval sequence is greater than the preset threshold value; and if the ratio is greater than the preset threshold value, identifying each access from the current identification user or IP in the first preset range as the access attack. According to the method and device provided by the embodiment of the application, the identification is processed based on the time interval sequence of the adjacent access in each access from the same identification user or IP, and thus the diversity of various access can be shielded, the various access can be effectively identified, and relatively good universality can be achieved.
Owner:ADVANCED NEW TECH CO LTD
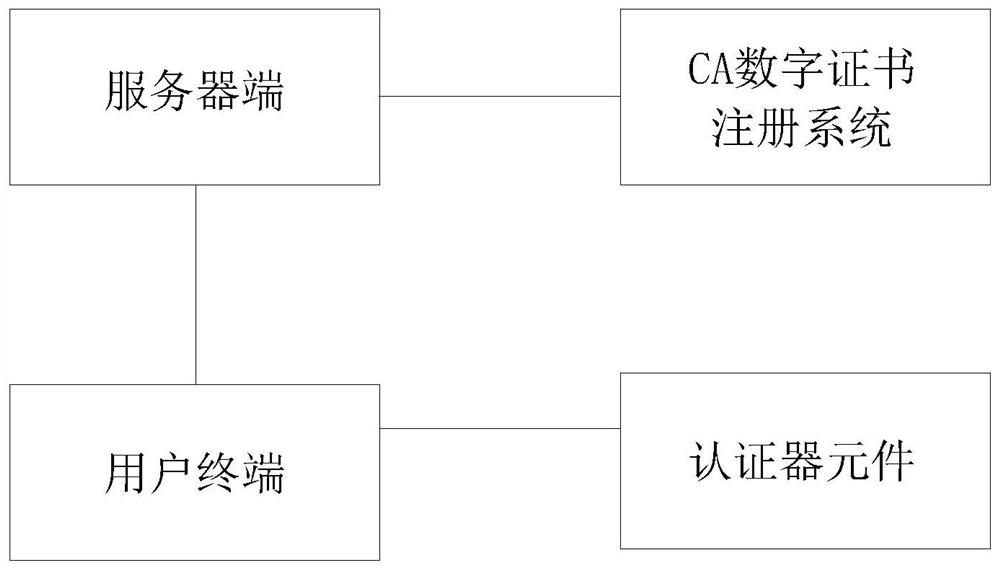
Identity authentication method and identity authentication system
ActiveCN112953970AShielding differencesImprove compatibilityUser identity/authority verificationAuthentication systemUser privacy
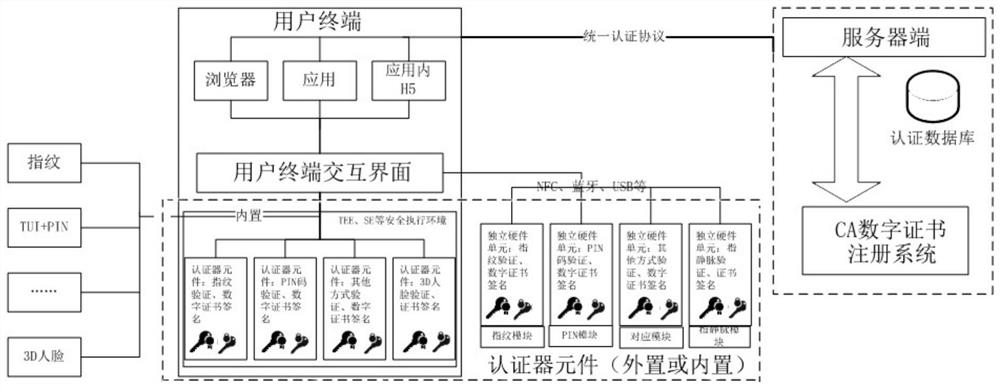
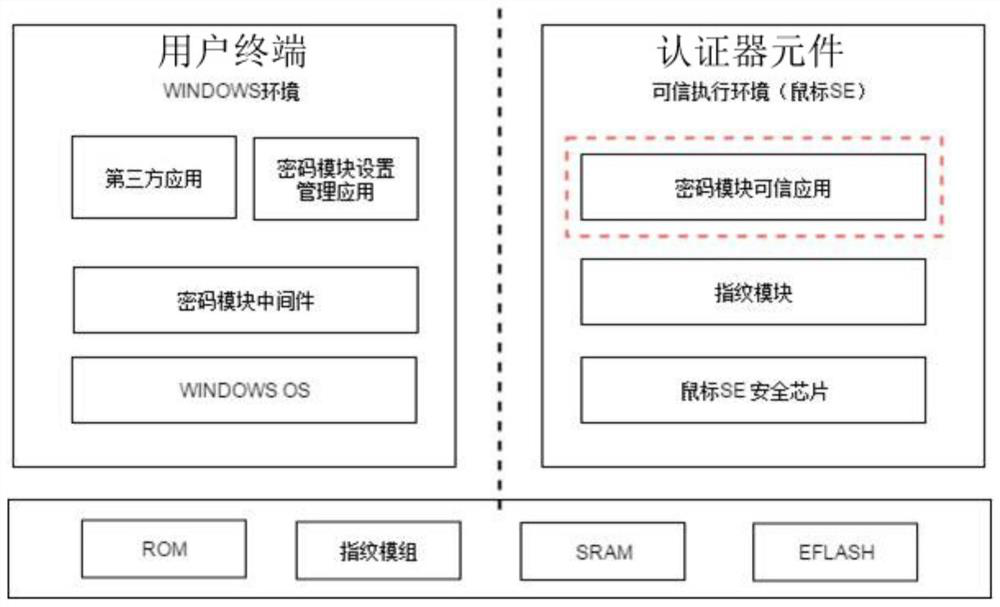
The invention discloses an identity authentication method and an identity authentication system. A unified authentication protocol is adopted for communication between a server side of the system and a user terminal, and the user terminal is connected with an authenticator element. The authentication method comprises the following steps that after receiving an authentication request, a server side issues an authentication request message to a user terminal and waits for an authentication response message; after receiving an authentication response message generated by the user terminal, the server side performs message verification, performs digital signature verification of the digital certificate and issues an authentication result, wherein the authenticator element is a terminal authentication device capable of realizing identity feature acquisition, extraction, storage and matching. The system and the method are based on a digital certificate security application mechanism of a unified protocol, are compatible with a PKI system, provide unified authentication service for services, reduce integration deployment difficulty, are good in user experience and high in security, and also protect user privacy.
Owner:GUOMIN RENZHENG TECH BEIJING CO LTD
Network log management method and system based on Syslog
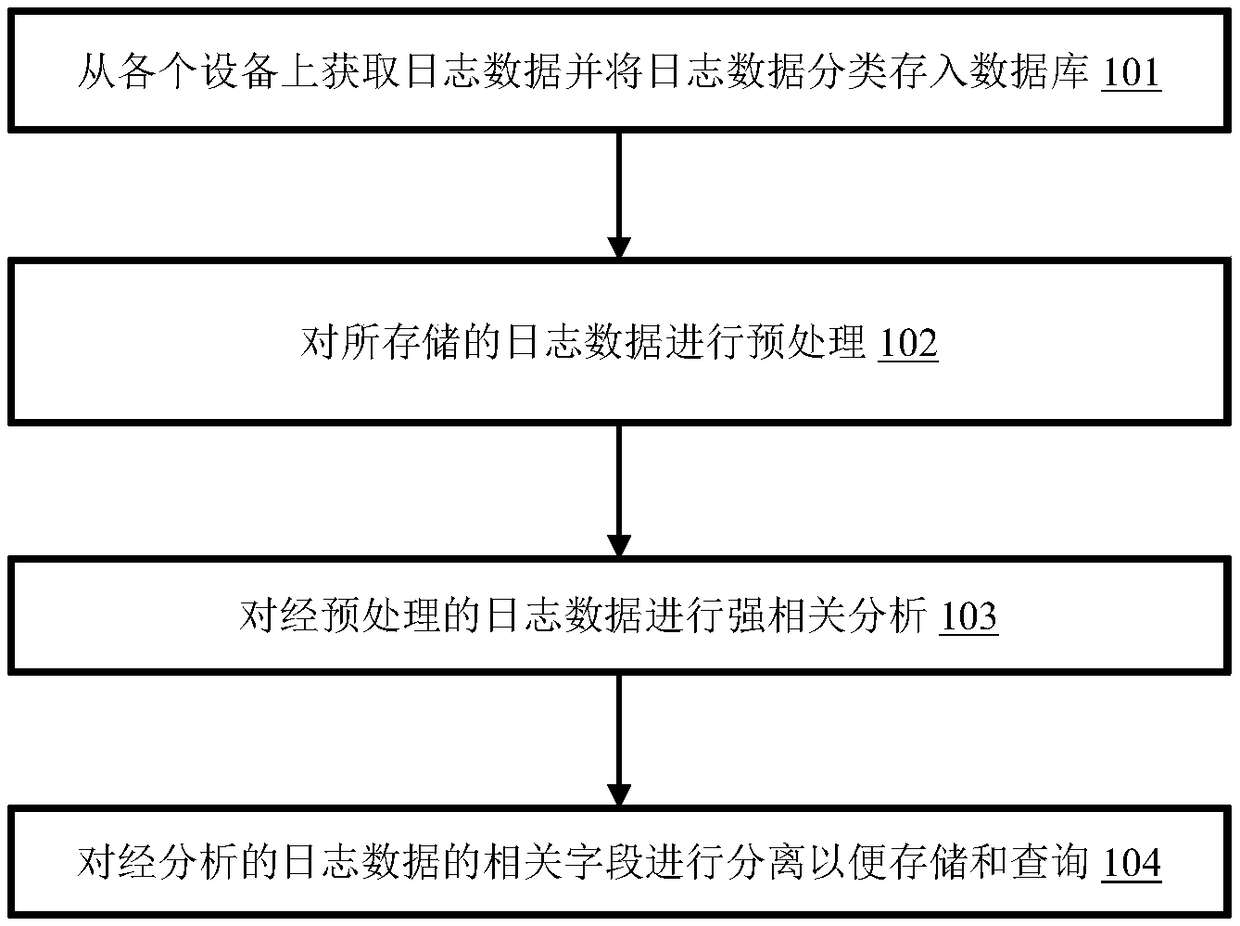
InactiveCN109510721AShielding differencesImprove troubleshooting efficiencyData switching networksLog managementCorrelation analysis
The invention provides a network log management method based on Syslog. The method comprises the following steps: acquiring log data from each set of equipment, and saving the log data in a database;preprocessing the stored log data; performing strong correlation analysis on the preprocessed log data; and separating a related field of the analyzed log data so as to store and query. The inventionprovides a method for managing the Syslog network log in a unified way, the log message difference between the equipment is shielded, and the troubleshooting efficiency of the network administrator isimproved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
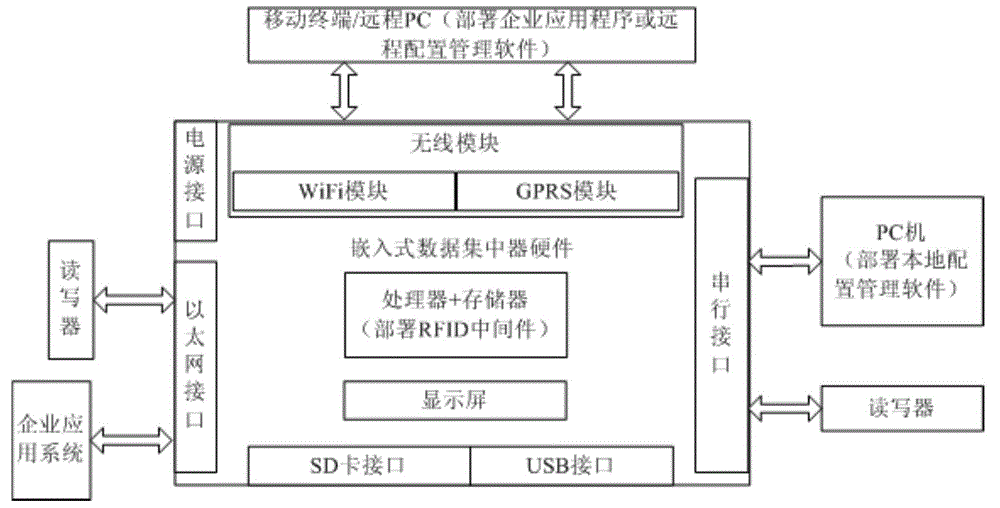
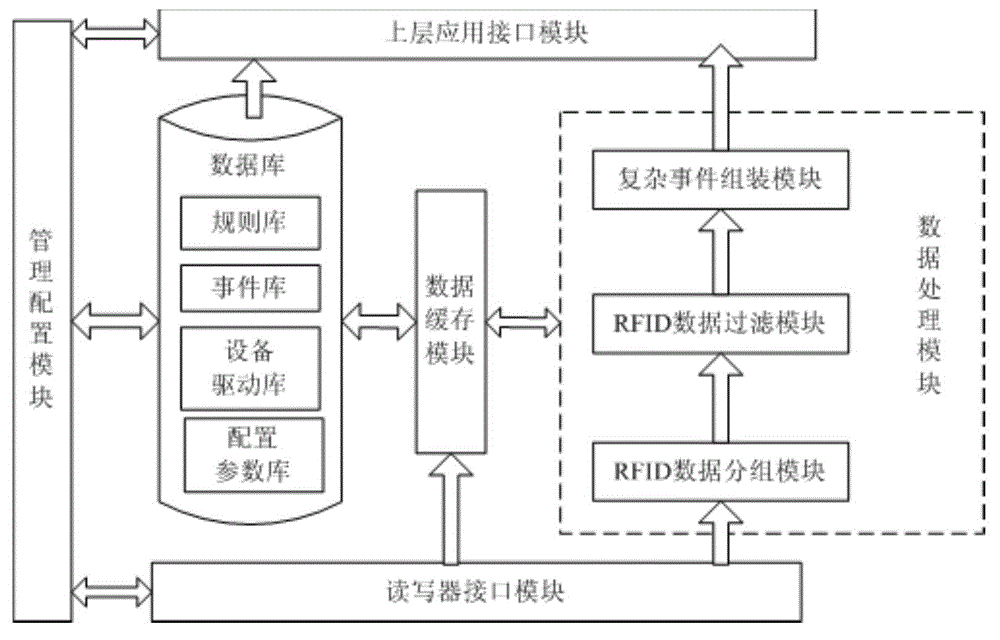
Embedded data concentrator based on RFID middleware
InactiveCN104091187AStrong flexibilitySolve Maintenance ComplexityCo-operative working arrangementsHybrid integrated circuitIntegrated circuit
The invention relates to an embedded data concentrator based on RFID middleware and belongs to the technical field of the radio frequency identification technology. The embedded data concentrator comprises embedded data concentrator hardware and configuration management software. The embedded data concentrator hardware works in an embedded hardware environment based on an ARM and comprises a processor, a memory, a wireless module, a display screen and a universal input / output interface, and the hardware is integrated on two double-layer hybrid integrated circuit boards, wherein one hybrid integrated circuit board integrates the processor, the memory and the display screen, and the processor is connected with the memory through a main memory bus and connected with the display screen through an I / O bus; the other hybrid integrated circuit board integrates the wireless module and the universal input / output interface, the wireless module and the universal input / output interface are respectively connected with an I / O bus of the circuit board, and the two circuit boards are in the mode of a master and a slave and are connected through a UART bus. The embedded data concentrator has the advantages that the RFID data integration problem is solved; an RFID system generates a large amount of data, the data are processed through the RFID middleware, valuable RFID data are transmitted to an enterprise, and thus the RFID technology and an enterprise resource information system can be combined.
Owner:AUTOMATION RES & DESIGN INST OF METALLURGICAL IND
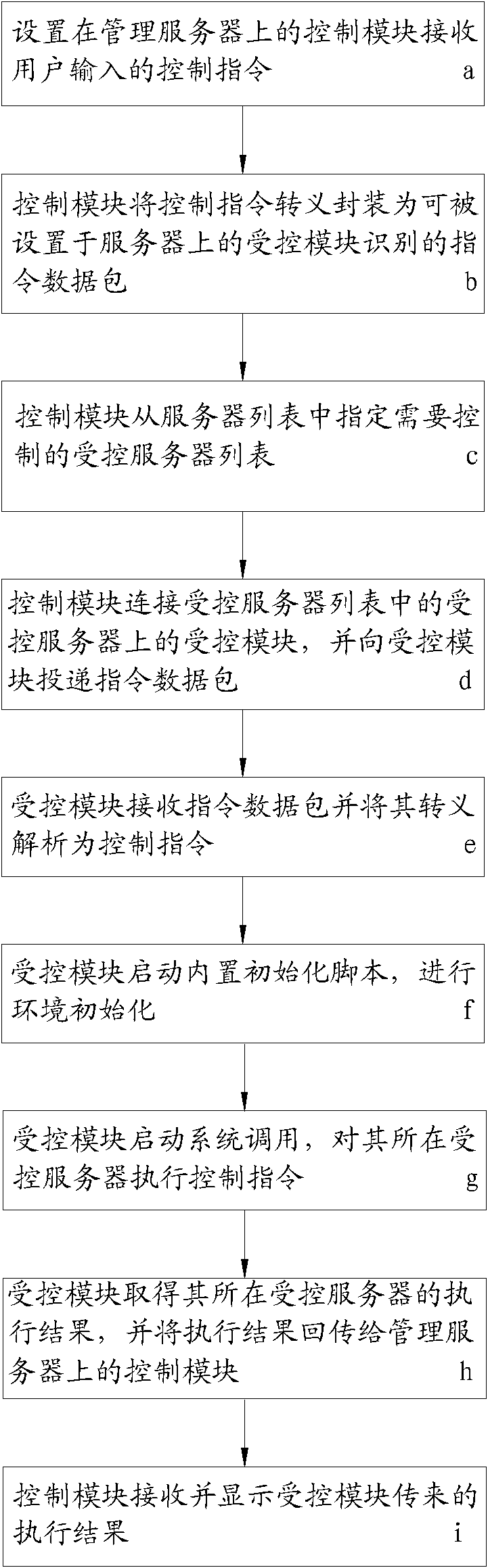
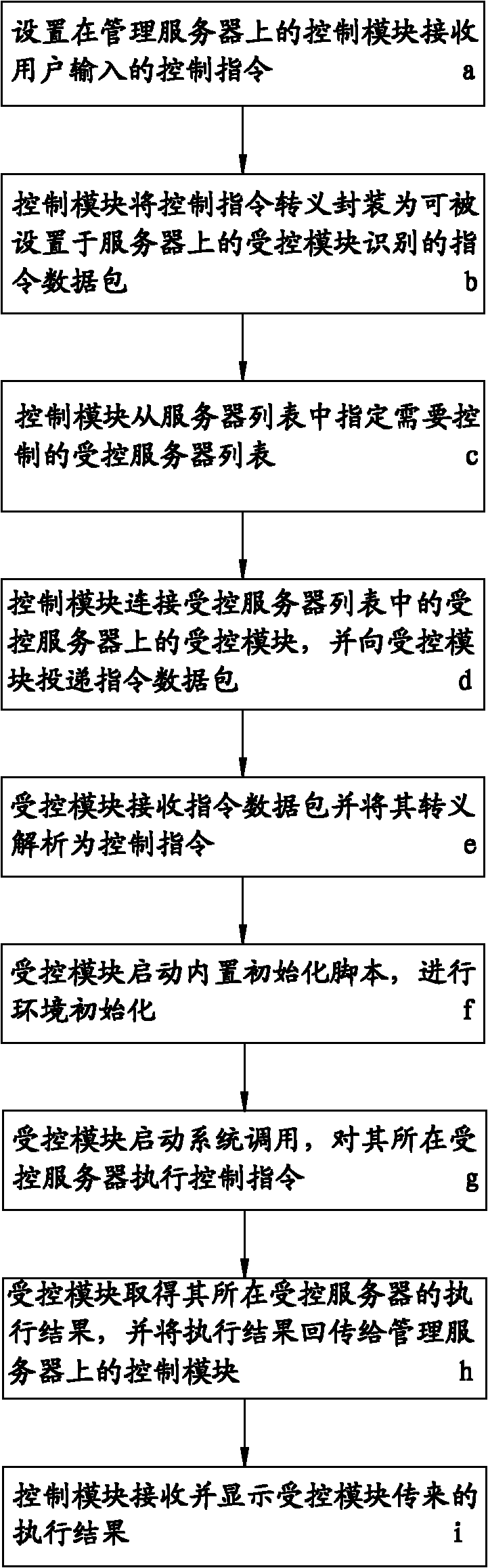
Unified control method of large-scale server cluster
The invention discloses a unified control method of a large-scale server cluster; the unified control method comprises the following steps: a control module arranged on a management server receives control commands input by users; the control module carries out transferred meaning on the control commands and encapsulates the control commands into command data packets; the control module appoints a controlled server list from a server list; the control module is connected with a controlled module on a controlled server and delivers the command data packets to the controlled module; the controlled module receives the command data packets, carries out transferred meaning on the command data packets and analyzes the command data packets into the control commands; the controlled module starts a built-in initialization script and carries out environment initialization; and the controlled module starts system calls and carries out the control commands. The unified control method has the advantages of shielding differences among different operating systems by carrying out unified transferred meaning on the control commands, having very good portability, and being capable of conveniently and freely carrying out unified control on one or multiple servers by appointing the controlled server list needing to be controlled, thereby realizing the high efficiency control on the large-scale server cluster.
Owner:东莞市正欣科技有限公司
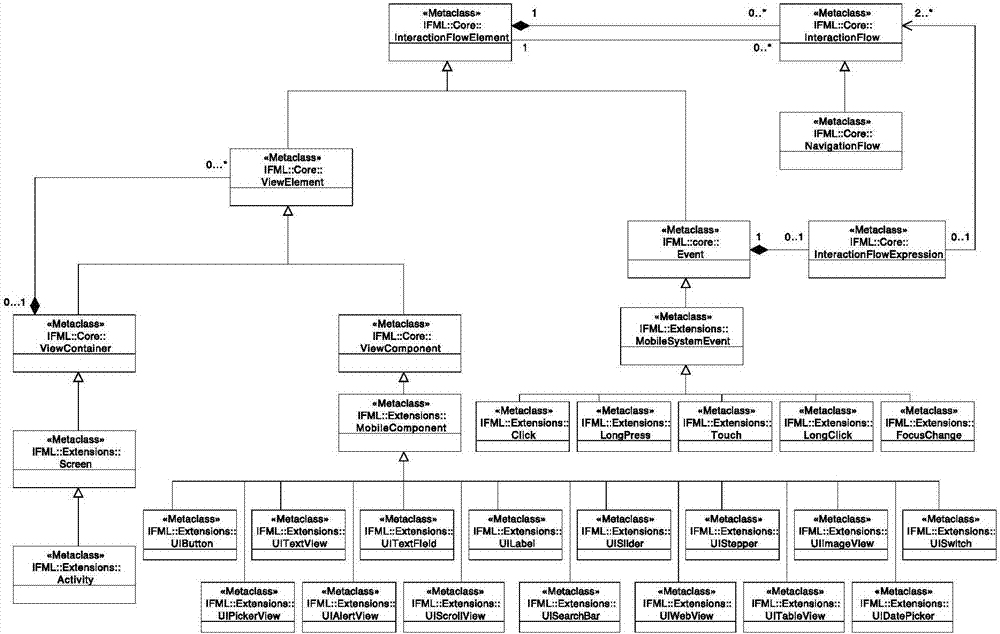
IFML-based (interaction flow modeling language) iOS development modeling method
InactiveCN107133042AShielding differencesModel driven codeSpecific program execution arrangementsSimulationHuman language
The invention relates to an IFML-based (interaction flow modeling language) iOS development modeling method, comprising the steps of I, allowing IFML to extend further for the iOS platform based on the extension of a mobile platform, and determining and abstracting an integral operation process of an iOS platform application; II, using the IFML to perform initial interaction flow modeling for the integral operation process of the iOS application in step I according to the extension of the mobile platform; III, performing further extension for the iOS application platform based on the extension of the mobile platform by the IFML, and using the IFML oriented to the extension of the iOS application platform to perform reality-oriented interaction flow modeling; IV, completing application development for an interaction flow model of the iOS application platform in step III in conjunction with project demands and iOS version information. In the method, iOS mobile applications are abstracted to obtain interaction flow models based on the model driving mode, and the IFML for iOS platform extension is used to perform modelling for the model.
Owner:NANJING UNIV
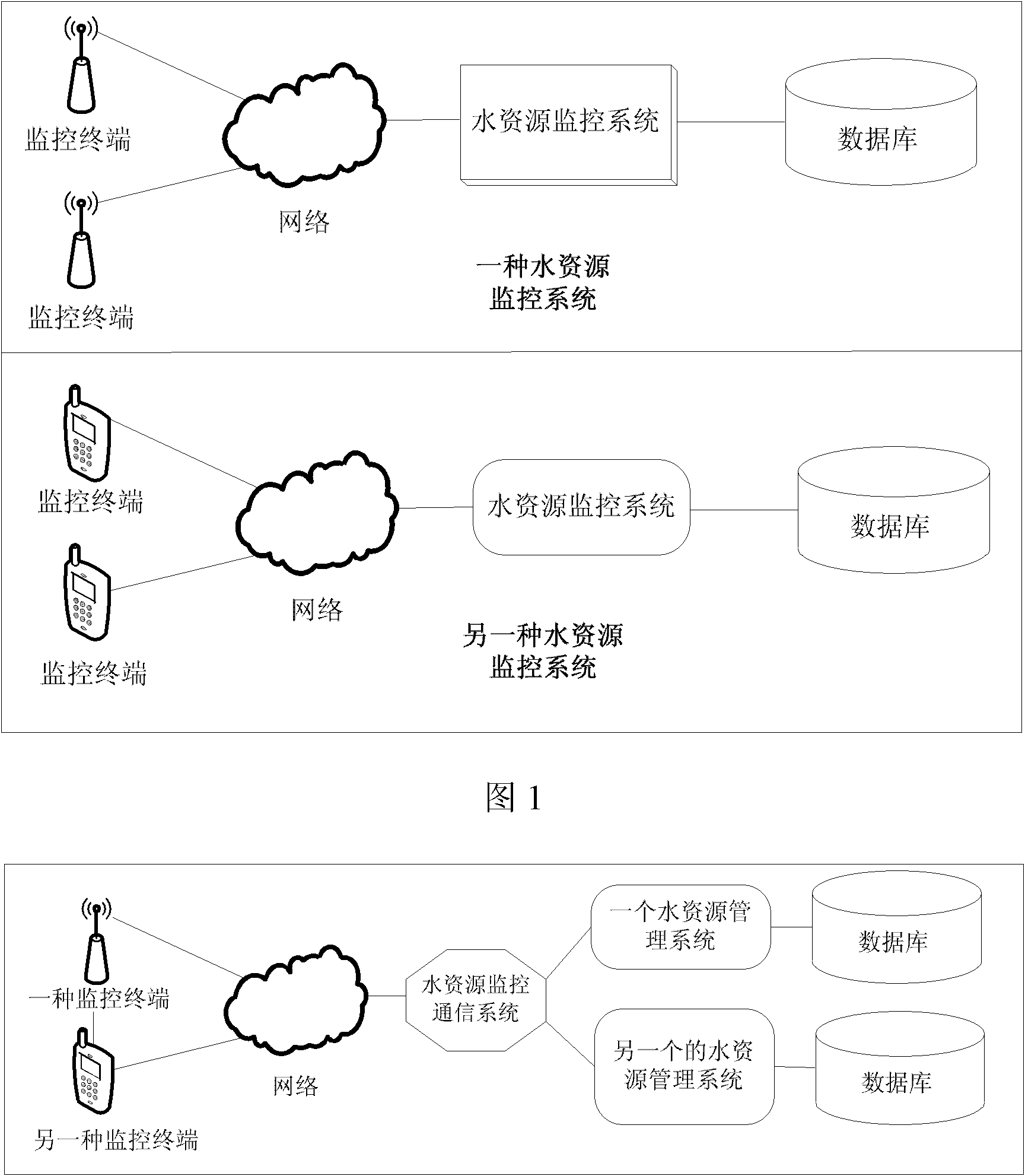
Water resource monitoring communication system and method
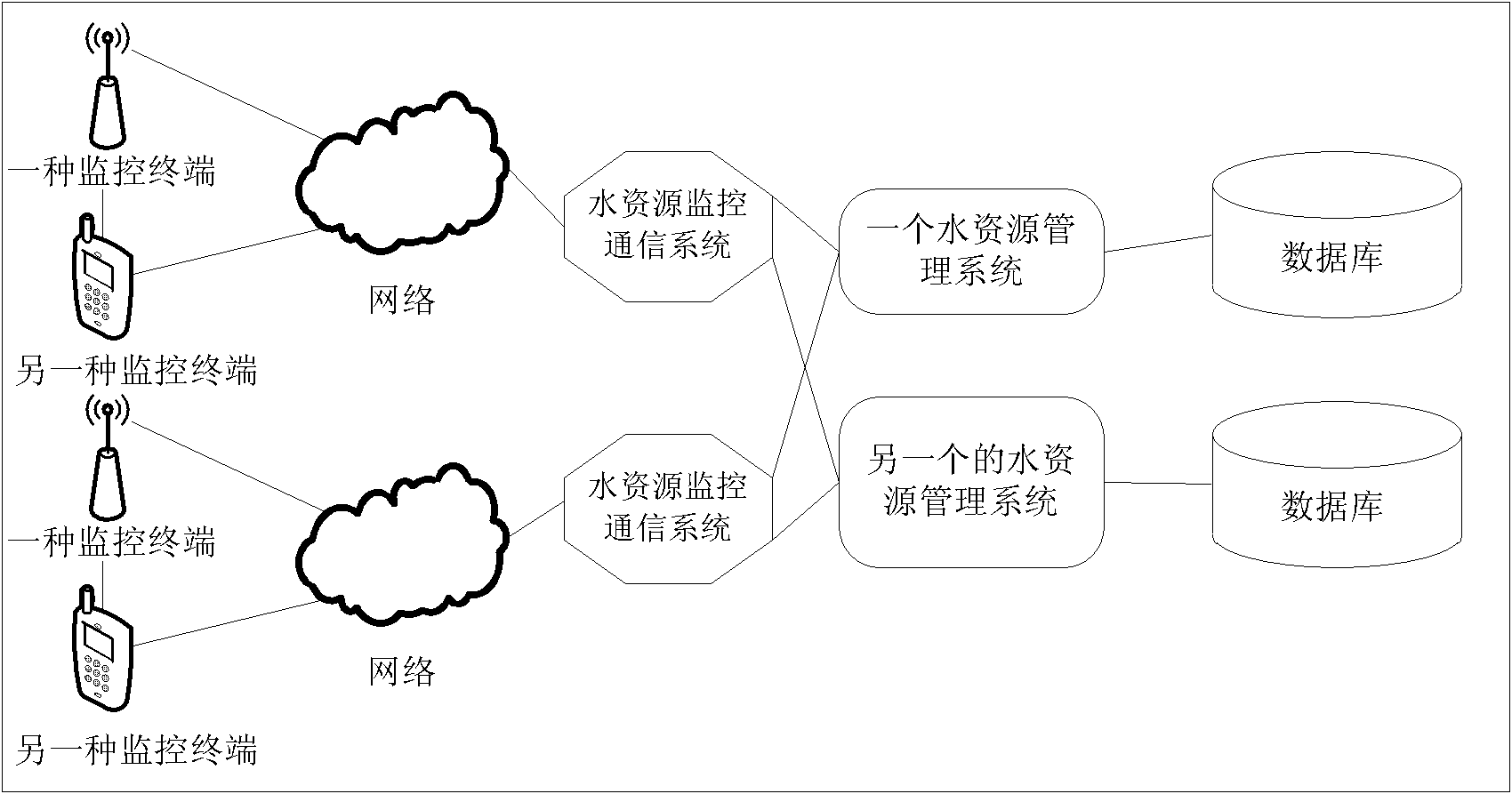
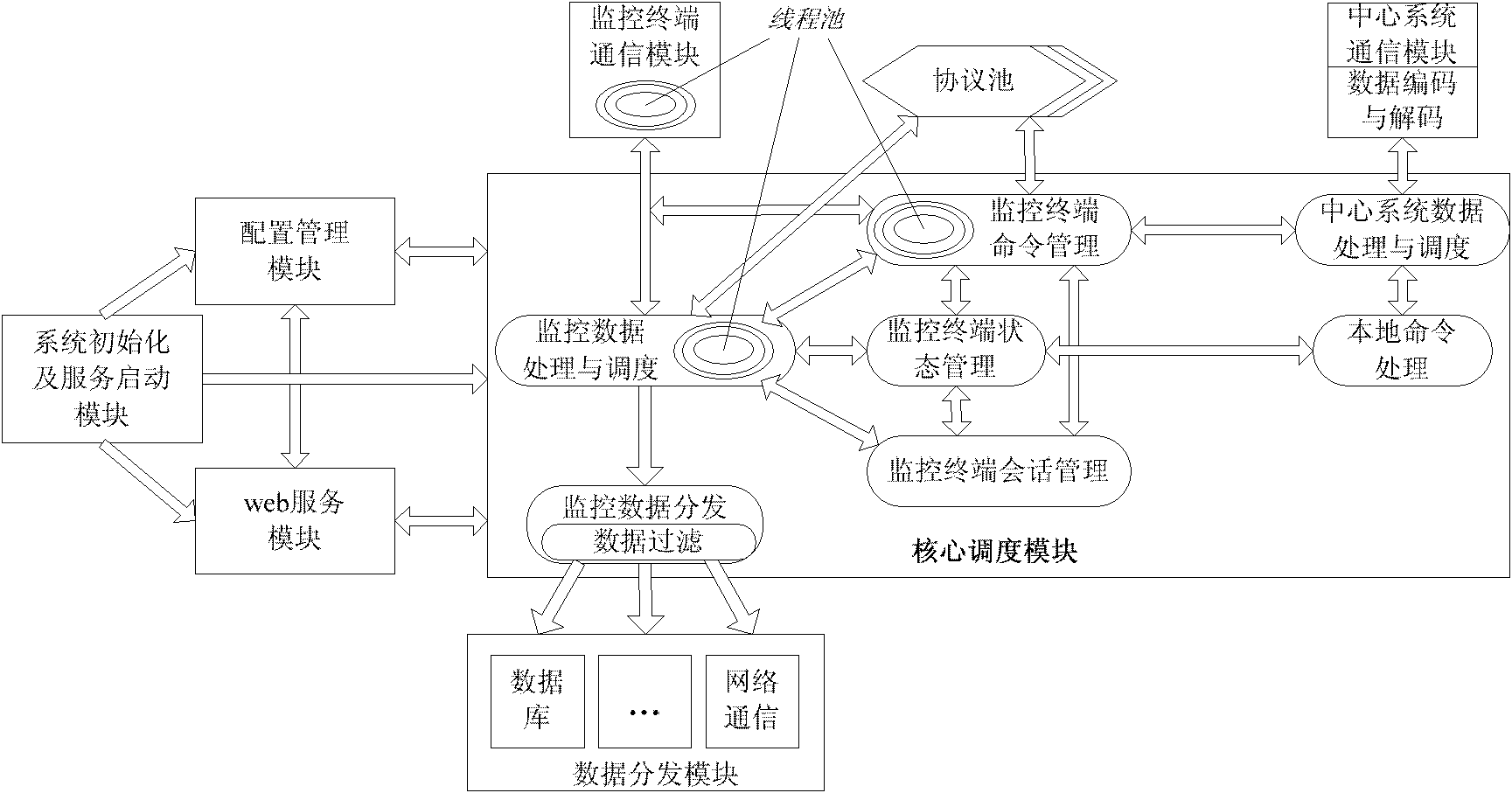
InactiveCN102130968AImprove scalabilityImplement concurrent processing functionsTransmissionCommunications systemWater resources
The invention relates to a water resource monitoring system and provides a water resource monitoring communication system which is characterized in that the system is arranged between various water resource monitoring terminals and multiple water resource management systems and can be deployed in a distributed manner; and the system can be connected to the water resource monitoring terminals of various communication modes and multiple water resource monitoring communication protocols, and can distribute data to the multiple water resource management systems, receive the monitoring commands of the water resource management systems at the same time and forward the commands to the water resource monitoring terminals. The system provided by the invention can effectively implement the water resource monitoring work.
Owner:北京奥特美克科技股份有限公司
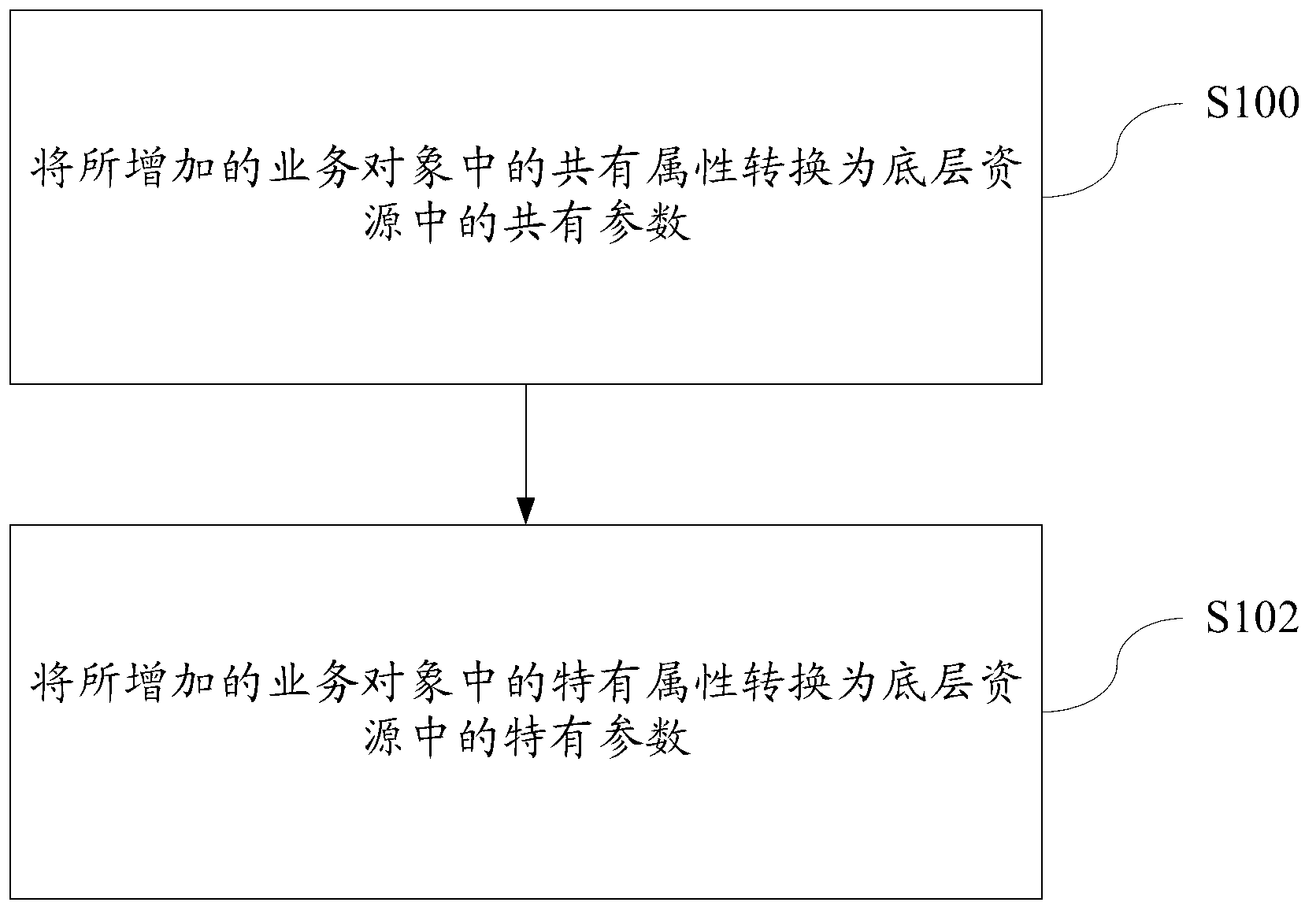
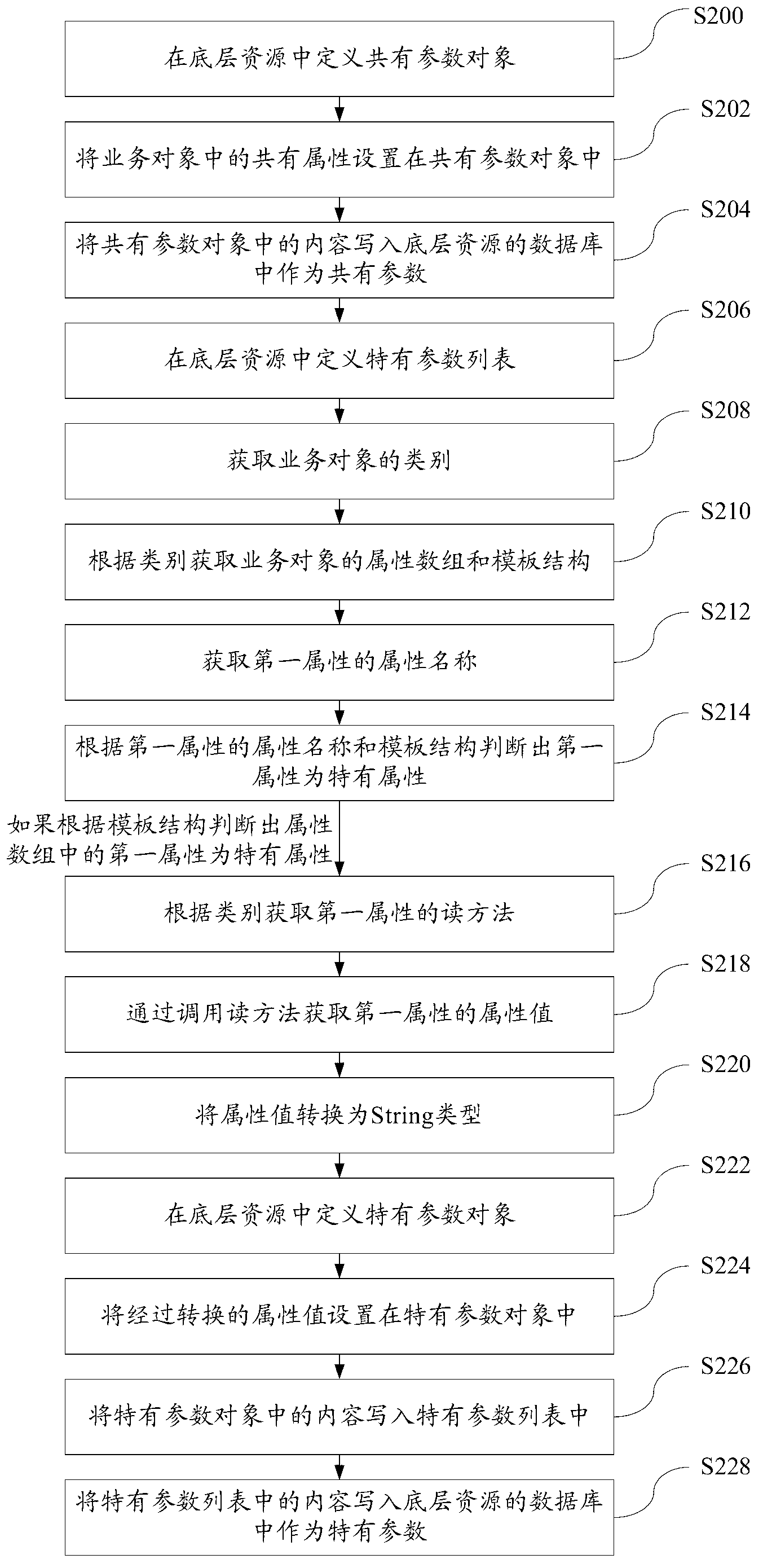
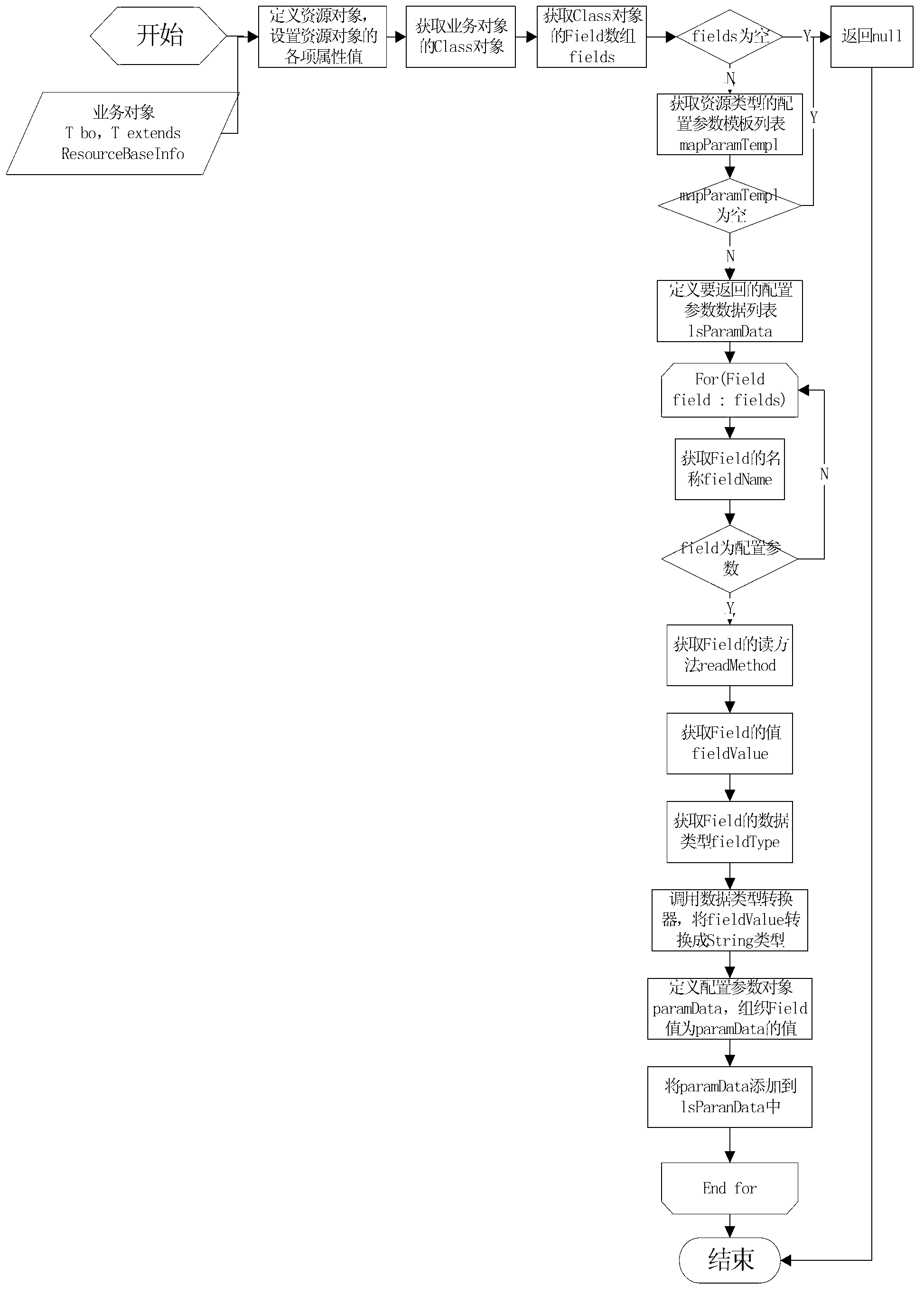
Method of reading bottom layer resources in cloud computing environment
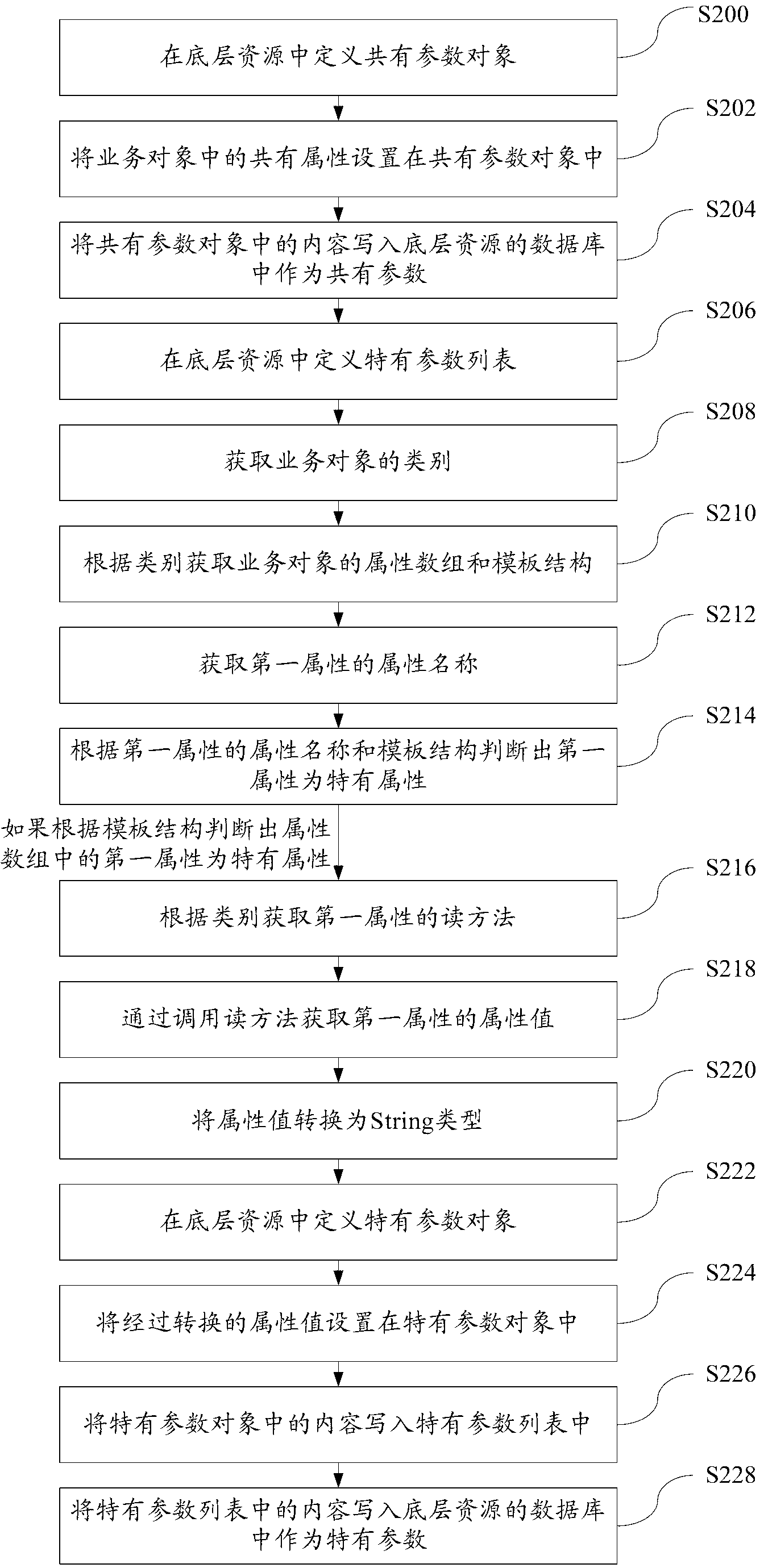
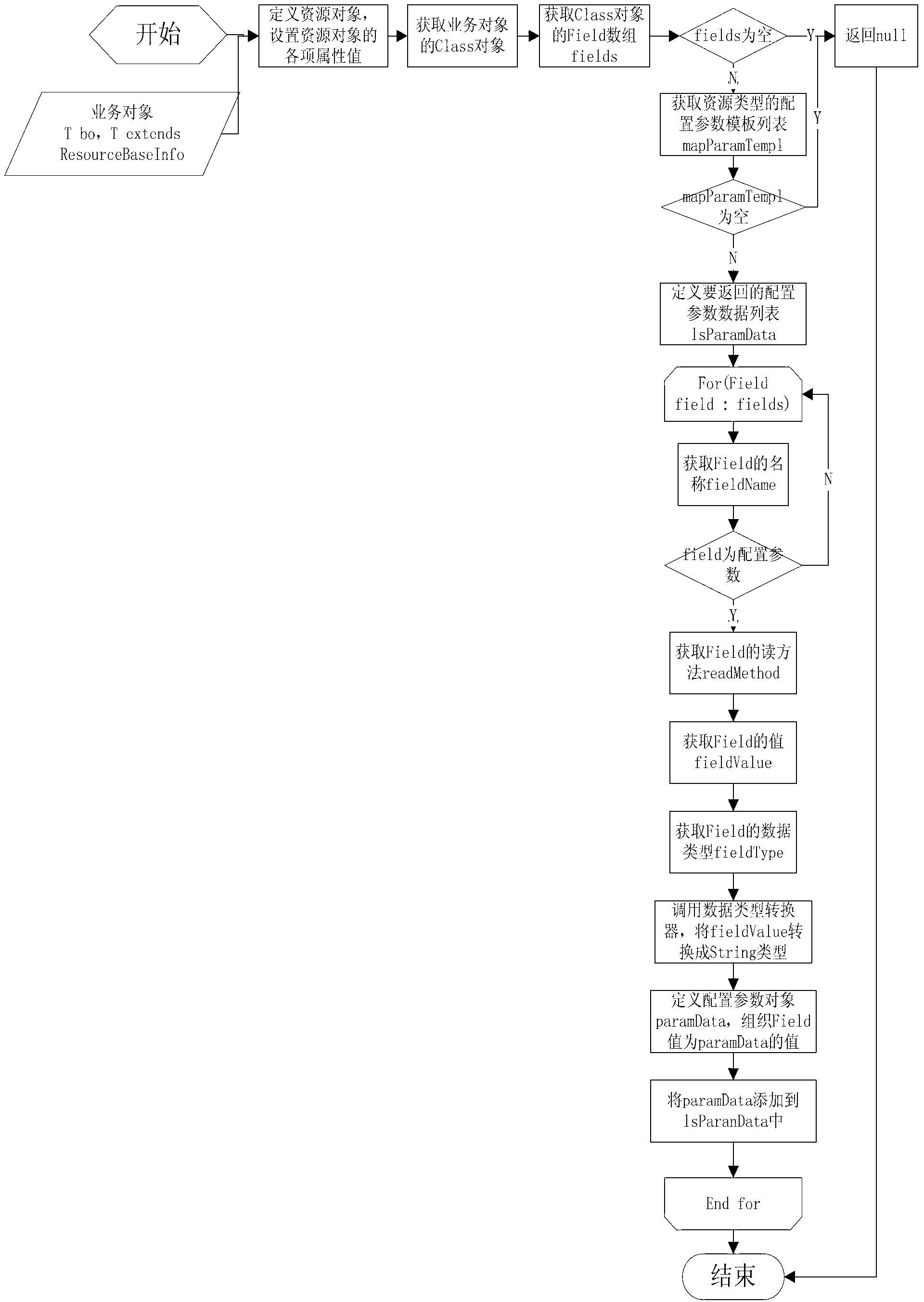
ActiveCN102981831AAchieve conversionShielding differencesSpecific program execution arrangementsBusiness objectCloud computing
The invention discloses a method of reading bottom layer resources in a cloud computing environment. The method comprises that the common parameters of bottom layer resources are converted to common properties of business objects, and the specific parameters of the bottom layer resources are converted to the specific properties of the business objects. According to the technical scheme of the method of reading the bottom layer resources in the cloud computing environment, the method of increasing business objects in a cloud computing environment is provided, and the problems that a plurality of business objects of a plurality of business systems need unified storage in the cloud computing environment, while object-oriented business objects are needed on an upper layer are solved. The method of reading the bottom layer resources in the cloud computing environment achieves the conversion between the bottom layer resources and upper layer business objects, and the otherness of different business objects is shielded. When the business objects change, only the upper layer business objects need to be modified, the bottom layer storage and interfaces can not be affected, and good expansibility of a system is guaranteed.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
Gatekeeper adaptation module and data transmission system
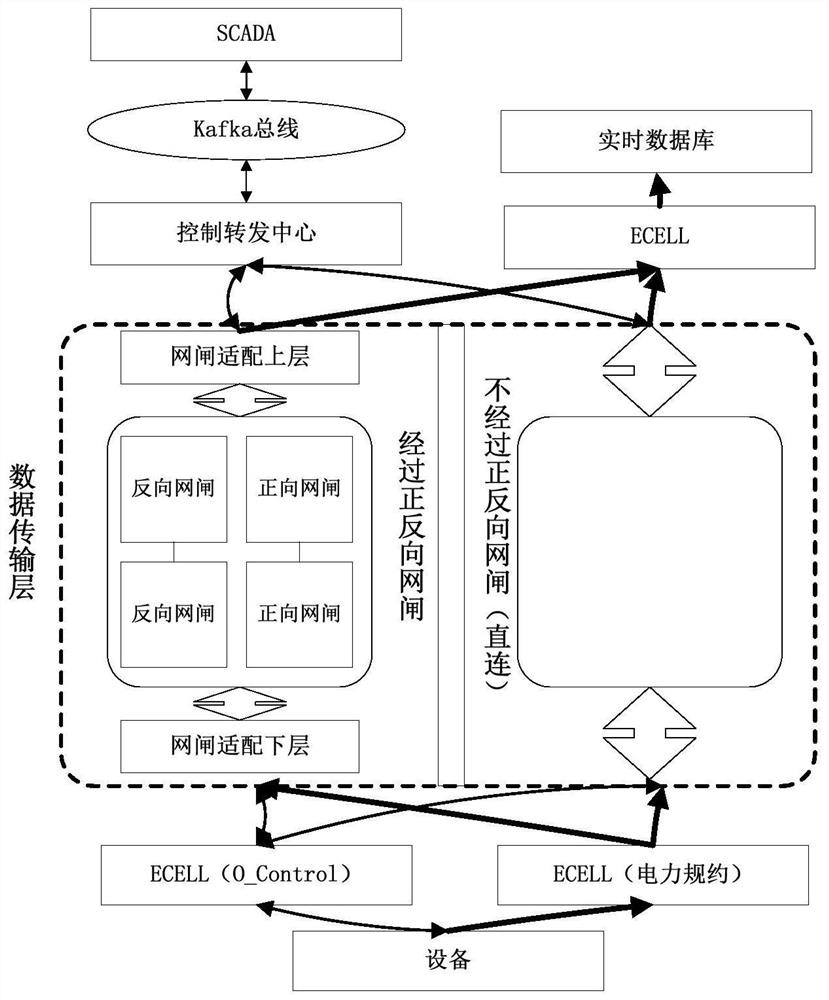
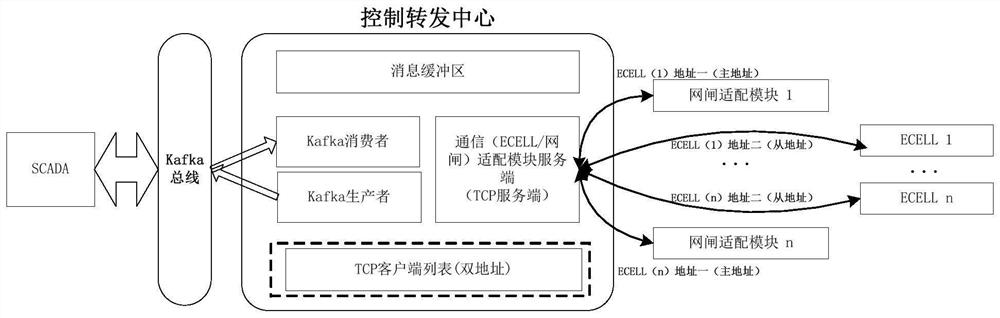
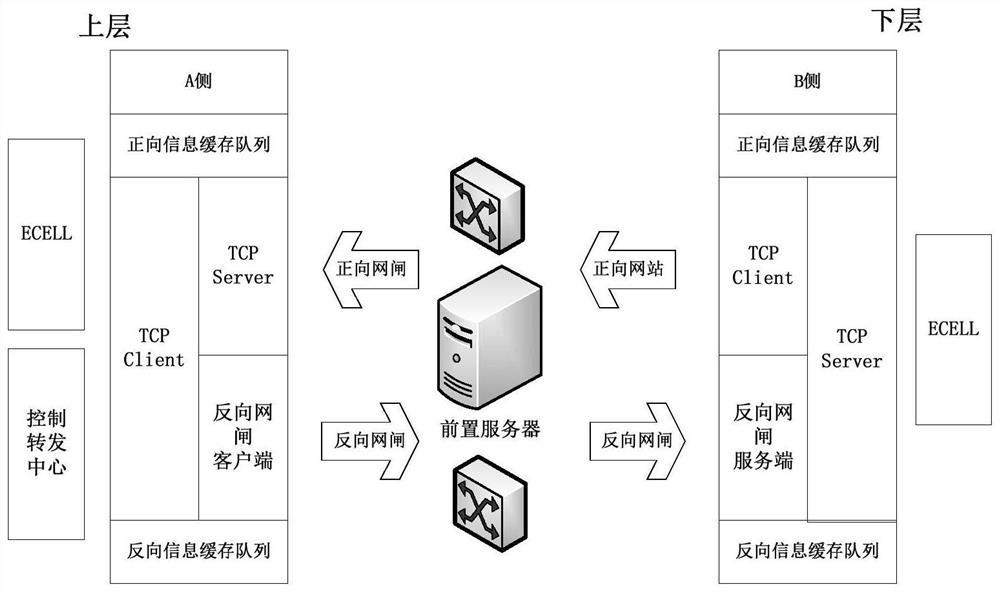
ActiveCN111865715AShielding differencesAchieve loose couplingData switching networksEmbedded systemData transmission systems
The invention discloses a gatekeeper adaptation module and a data transmission system suitable for information interaction between a production control area and a management information area of a power I area. The data transmission system comprises a control forwarding center, an acquisition client, an isolation gatekeeper and a gatekeeper adaptation module, wherein the gatekeeper adaptation module comprises an upper layer adaptation unit and a lower layer adaptation unit, the control forwarding center is connected and communicated with the upper adaptation unit and / or the acquisition client in the gateway adaptation module through a communication adaptation module based on a TCP protocol, the acquisition client is connected and communicated with the lower-layer adaptation unit in the gateway adaptation module based on the TCP protocol, and the control forwarding center stores communication addresses respectively corresponding to each acquisition control end and each gatekeeper adaptation module. When the gateway adaptation module is applied, data interaction with upper-layer control forwarding center software and lower-layer acquisition client software can be carried out based ona TCP protocol, a communication mode of forward and reverse gatekeepers is shielded, loose coupling of upper and lower programs is realized, and a unified TCP communication interaction mode is provided.
Owner:NANJING HUADUN ELECTRIC POWER INFORMATION SAFETY EVALUATION CO LTD
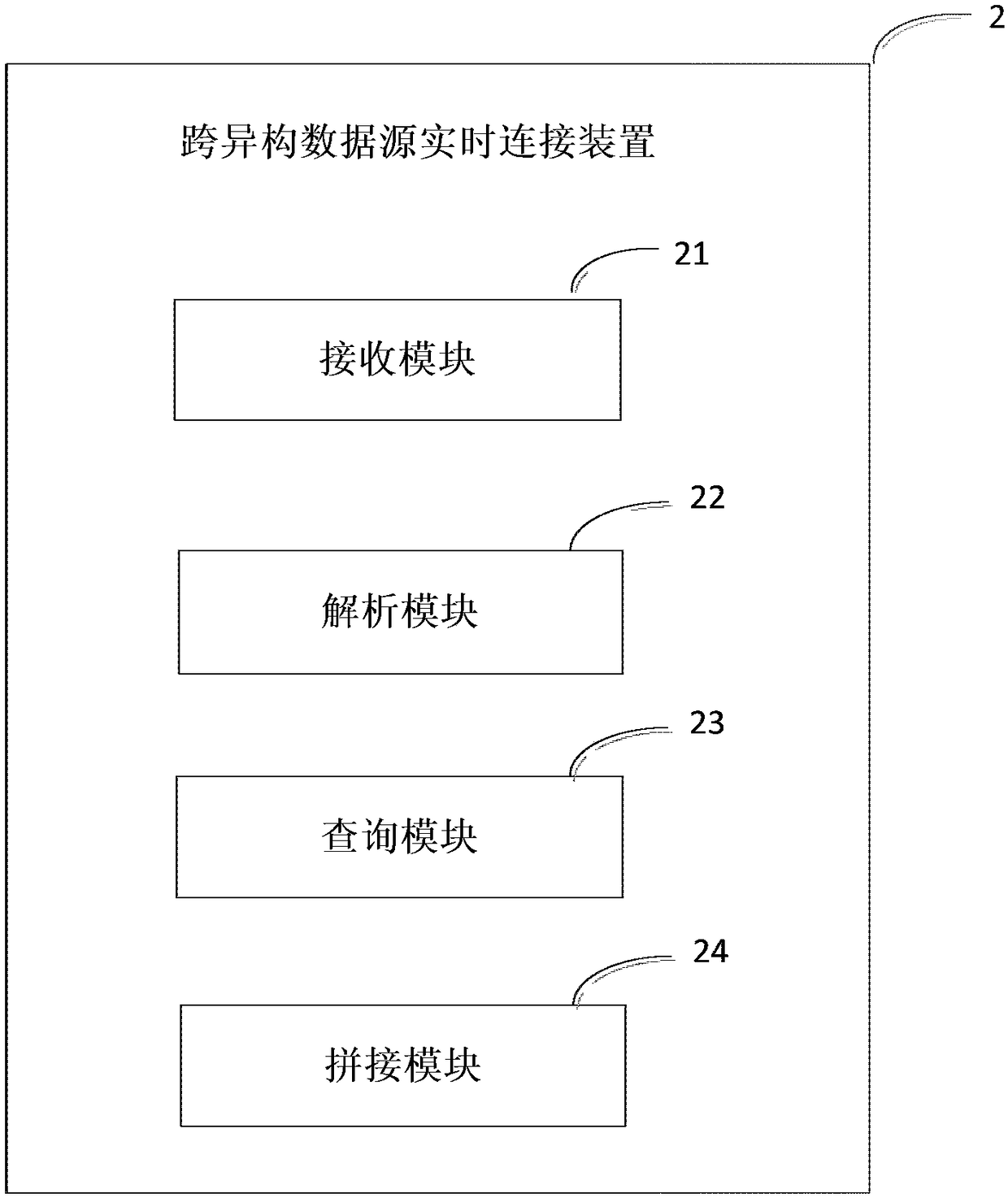
Cross-heterogeneous data source real-time connection method and apparatus
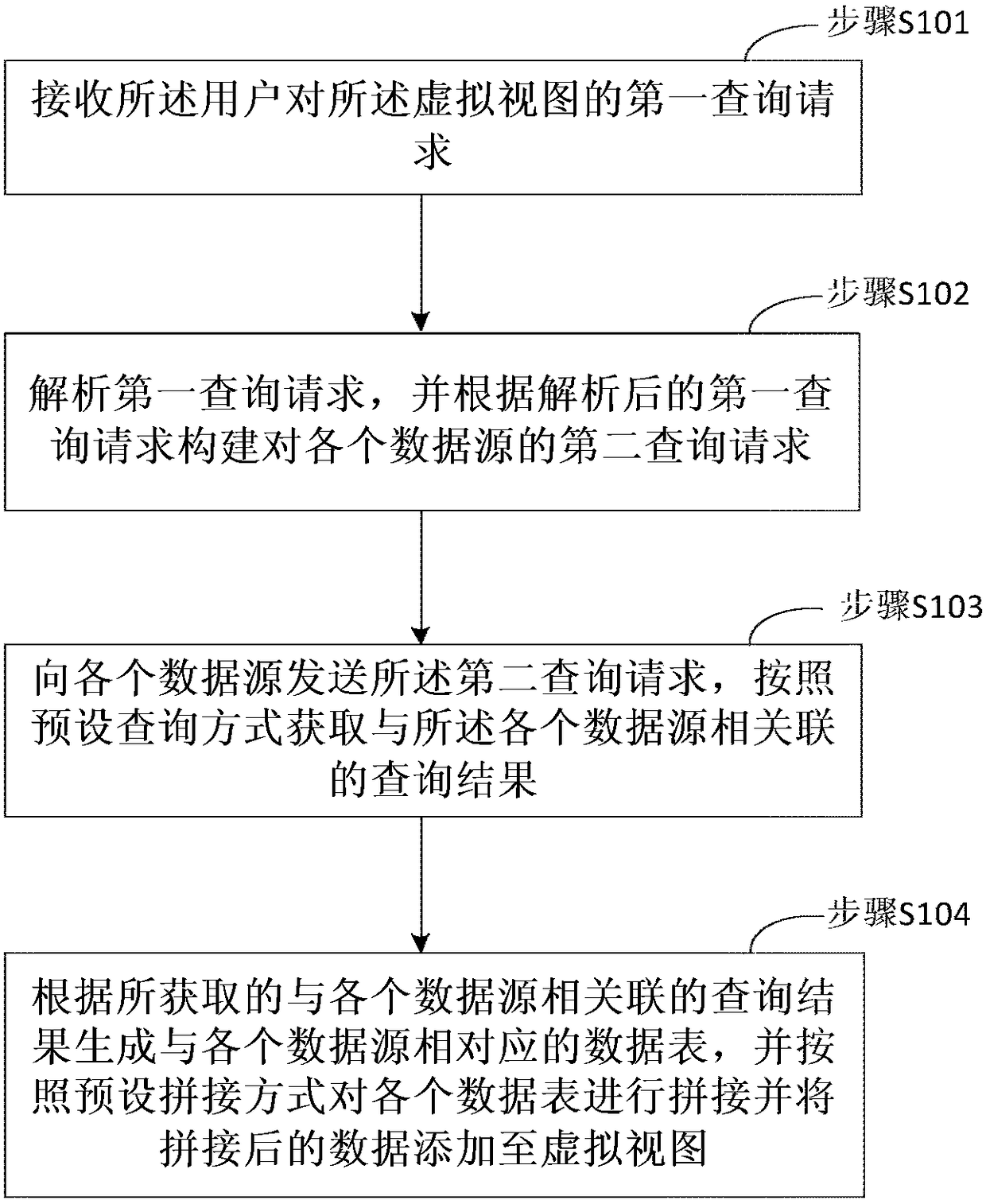
InactiveCN108733724AReal-time connection method implementedShielding differencesSpecial data processing applicationsData sourceData mining
The invention provides a cross-heterogeneous data source real-time connection method and apparatus. Before a query request of a user is received, a unified virtual view is established. When the queryrequest of the user is received, the method is implemented by the following steps of receiving a first query request of the user for the virtual view; analyzing the first query request, and constructing a second query request for each data source according to the analyzed first query request; sending the second query request to each data source, and acquiring a query result associated with each data source in a preset query mode; and generating a data table corresponding to each data source according to the acquired query result associated with each data source, splicing data tables in a preset splicing mode, and adding spliced data to the virtual view. Through the method and the apparatus, the difference between underlying databases can be completely shielded when the user analyzes and processes the data.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
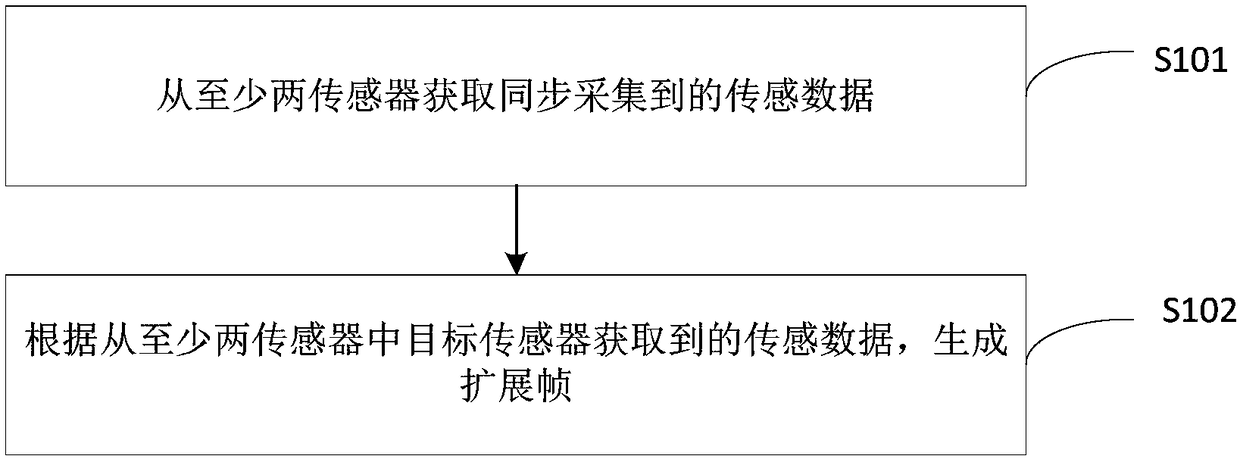
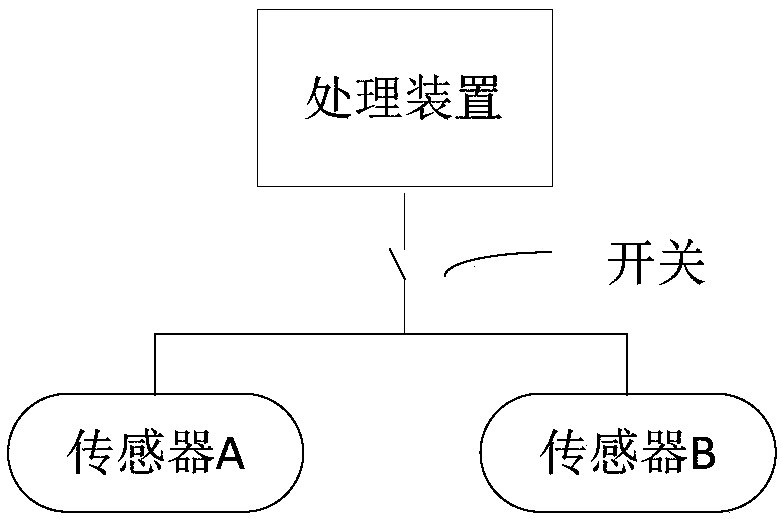
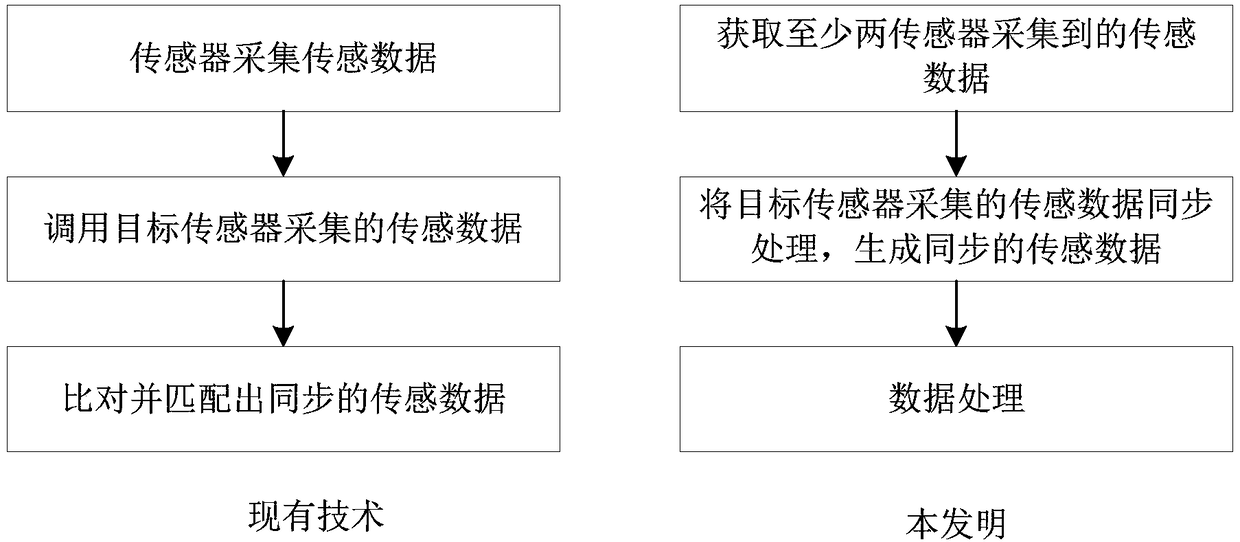
Data generation method and device based on sensors, data transmission method and device based on sensors, and data processing method, device and system based on sensors
The invention provides a data generation method and device based on sensors, a data transmission method and device based on sensors, and a data processing method, device and system based on sensors. The generation method comprises: acquiring synchronously collected sensing data from at least two sensors; and generating an extended frame according to the sensing data acquired from the target sensorin the at least two sensors, wherein the data portion of the extended frame carries data content of the sensing data of the target sensor. Therefore, a plurality of synchronous sensing data is read through an extended frame, the difference of underlying hardware is shielded, and the plurality of synchronous sensing data can be acquired by calling the extended frame for one time, thereby reducingthe extra overhead and time error of multiple times of transmission of the sensing data, improving the transmission efficiency, and further improving the data processing efficiency.
Owner:BEIJING ORION STAR TECH CO LTD
Camera model architecture method suitable for embedded system
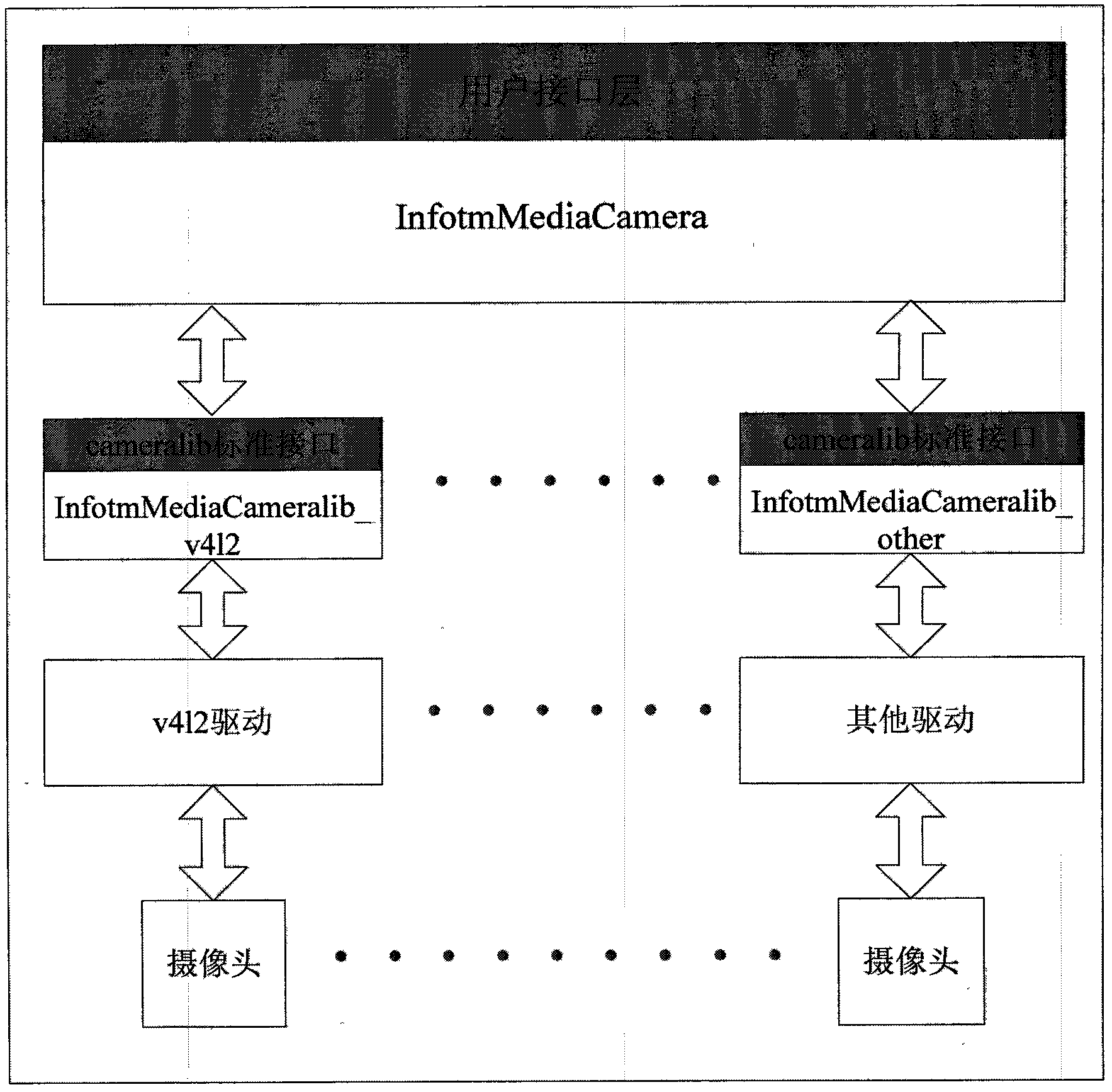
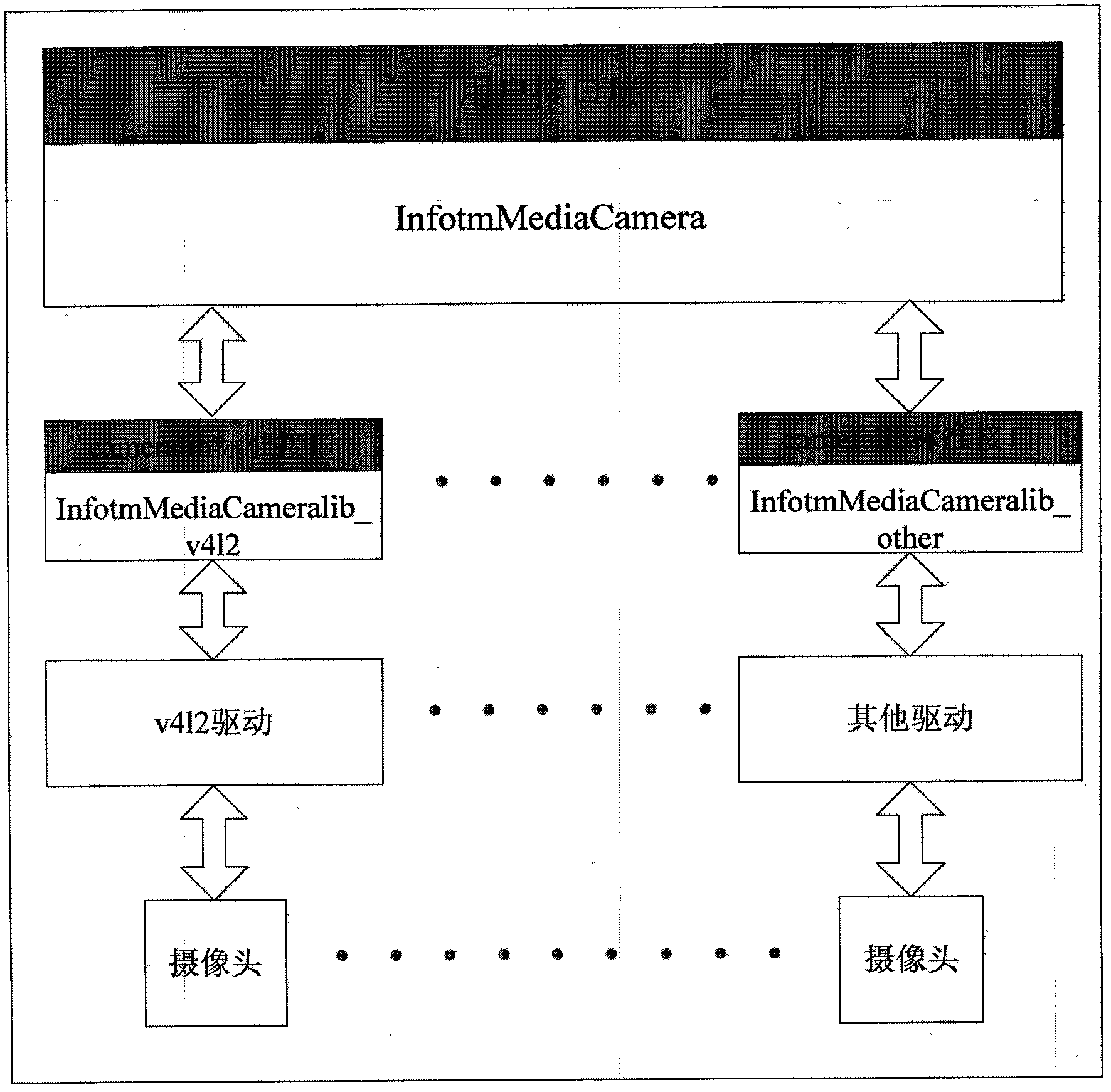
InactiveCN102368807ASecure AccessSimplify calling requirementsTelevision system detailsColor television detailsMulti cameraEmbedded system
A camera model architecture method suitable for an embedded system belongs to an architecture method supporting image acquisition equipment and a data interaction model in the embedded system. Problems needed to be solved comprises: how to support a plurality of the image acquisition equipment and how to complete the data interaction between the image acquisition equipment and the system. The method is characterized in that: an InfotmMediaCameralib module, which is taken as an intermediate interface database, integrates the image acquisition equipment of different equipment driving programs into the database and performs the interaction between an abstract unified interface with an upper layer InfotmMediaCamera; an InfotmMediaCamera module provides a complete camera data interaction function and a bidirectional control feedback function. By using the method of the invention, an application of controlling multi-cameras can be supported, and simultaneously an asynchronous demand of automatic focusing control and a synchronous demand of automatic exposure control can be supported too; a memory demand and a data bandwidth demand can be effectively minimized.
Owner:SHANGHAI INFOTM MICROELECTRONICS
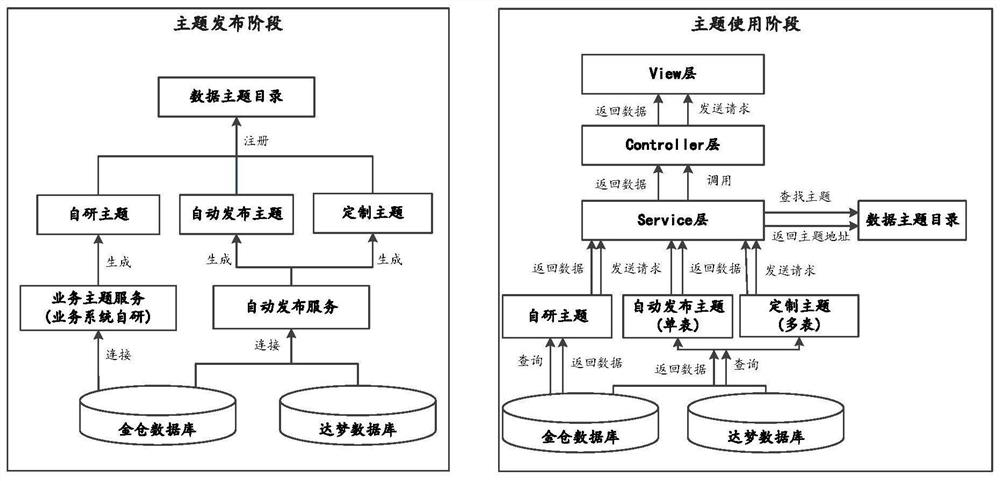
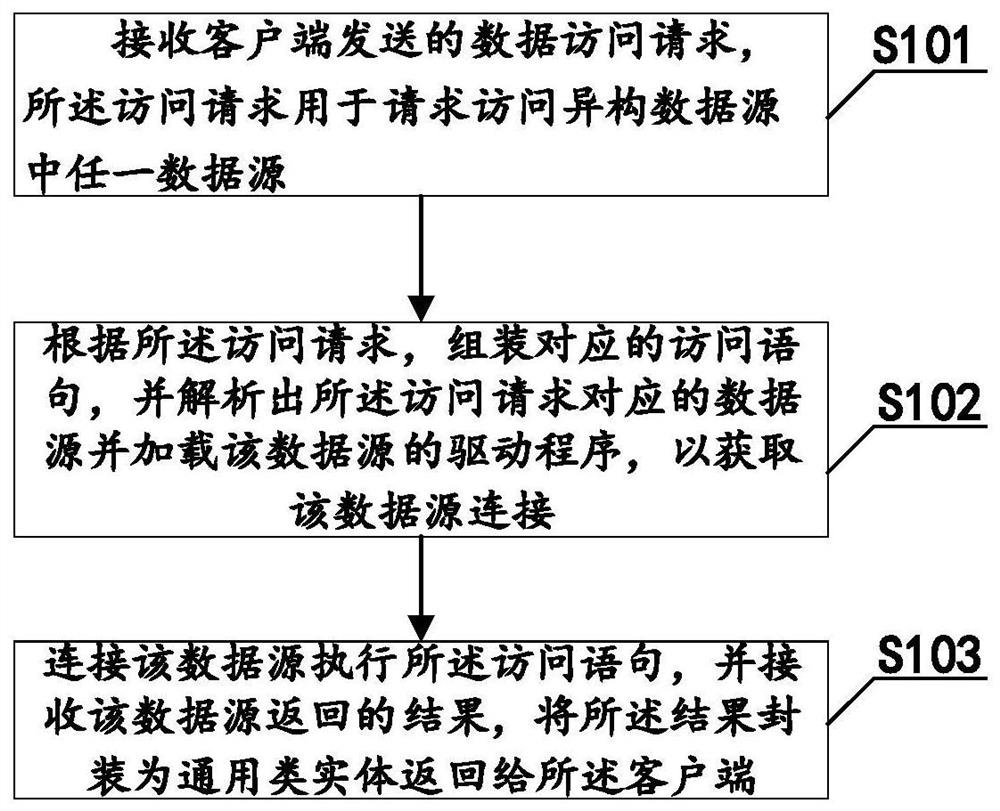
Unified access method for heterogeneous data sources
PendingCN114064684AShielding differencesRealize unified managementDatabase distribution/replicationSpecial data processing applicationsAccess methodTheoretical computer science
The invention relates to a unified access method for heterogeneous data sources, wherein the method comprises the steps: receiving a data access request sent by a client, wherein the access request is used for requesting to access any data source in heterogeneous data sources; according to the access request, assembling a corresponding access statement, analyzing a data source corresponding to the access request, and loading a drive program of the data source, to obtain data source connection; and connecting the data source to execute the access statement, receiving a result returned by the data source, packaging the result into a universal class entity, and returning the universal class entity to the client. According to the method, on the premise of ensuring the own characteristics of each database, servitization abstraction is carried out based on the access difference of the heterogeneous data sources, and integrated and unified management and access of the heterogeneous data sources are realized; and a set of universal access interfaces and access rules capable of cross-language and cross-platform heterogeneous databases are designed in a Restful mode, and a unified data access mode is provided for upper-layer applications.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP
Digital battery energy exchange system
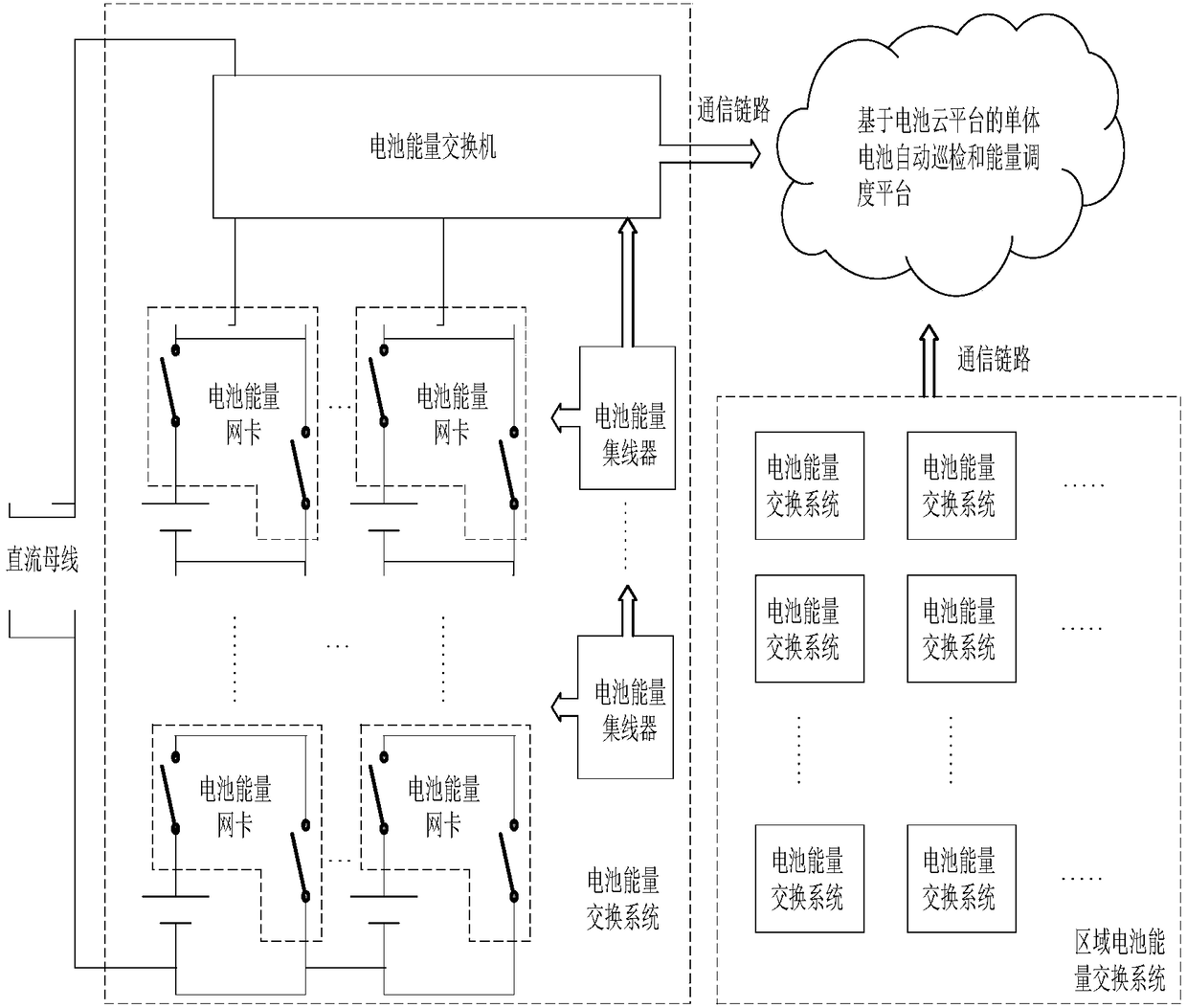
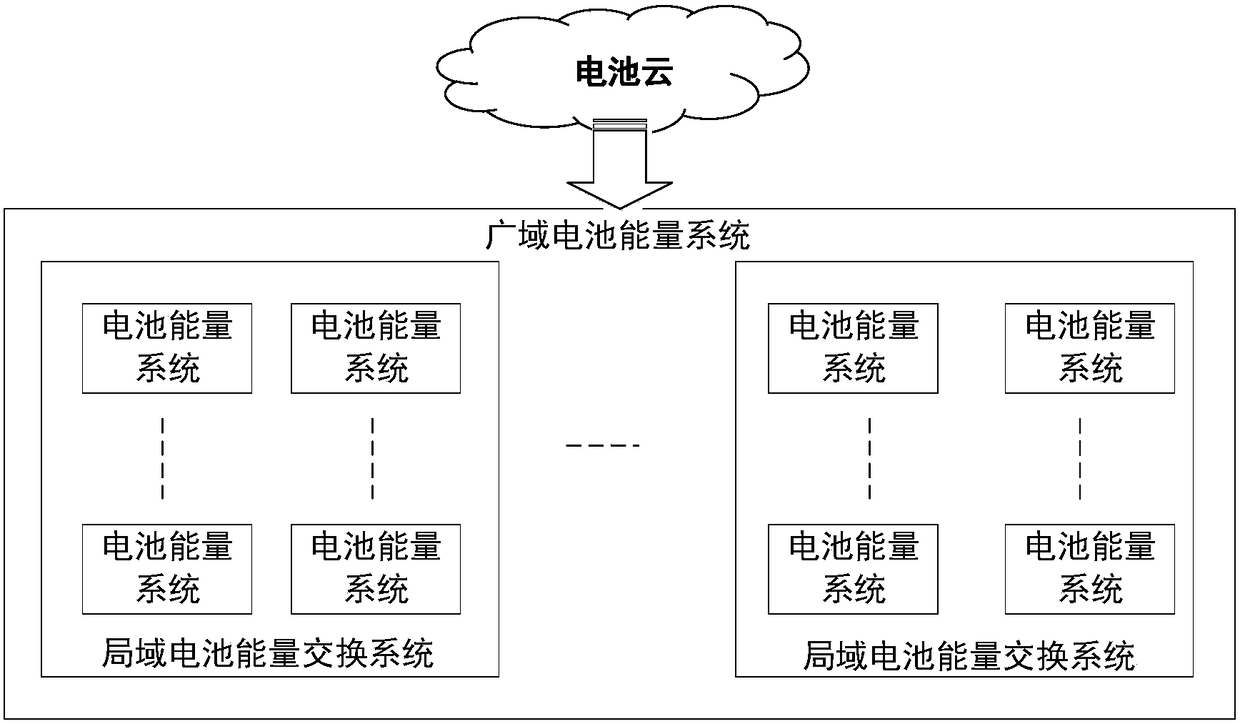
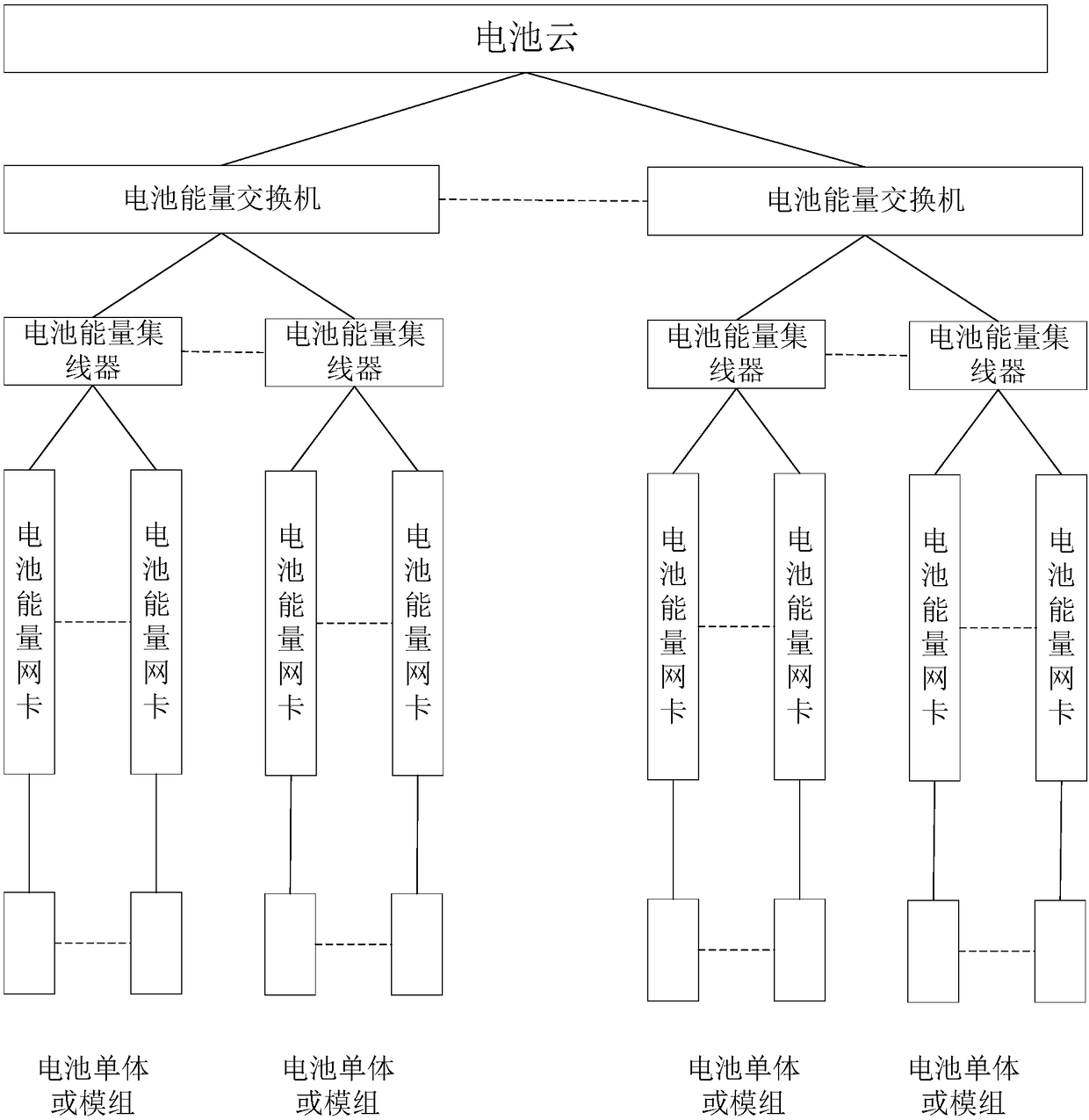
PendingCN108964159AGo digitalImplement virtualizationCharging managementElectric powerDiscretizationDigitization
The invention discloses a digital battery energy exchange system, which comprises a battery energy network card, a battery energy concentrator, a battery energy switch and a battery energy cloud platform. The system realizes the physical and chemical characteristics of the control and management system relatively independent from the battery by using the multi-level and fine-grained battery energyflow discretization digital processing and control, and dynamically adjusts the series-parallel combination between the battery cells to realize rapid distribution-type on-demand deployment; the system supports the battery energy exchange mechanism, shields the physical and chemical differences of battery cells, realizes the digitization and virtualization of the battery energy storage system, and effectively improves the flexibility and reliability of power storage and power supply.
Owner:云储新能源科技有限公司
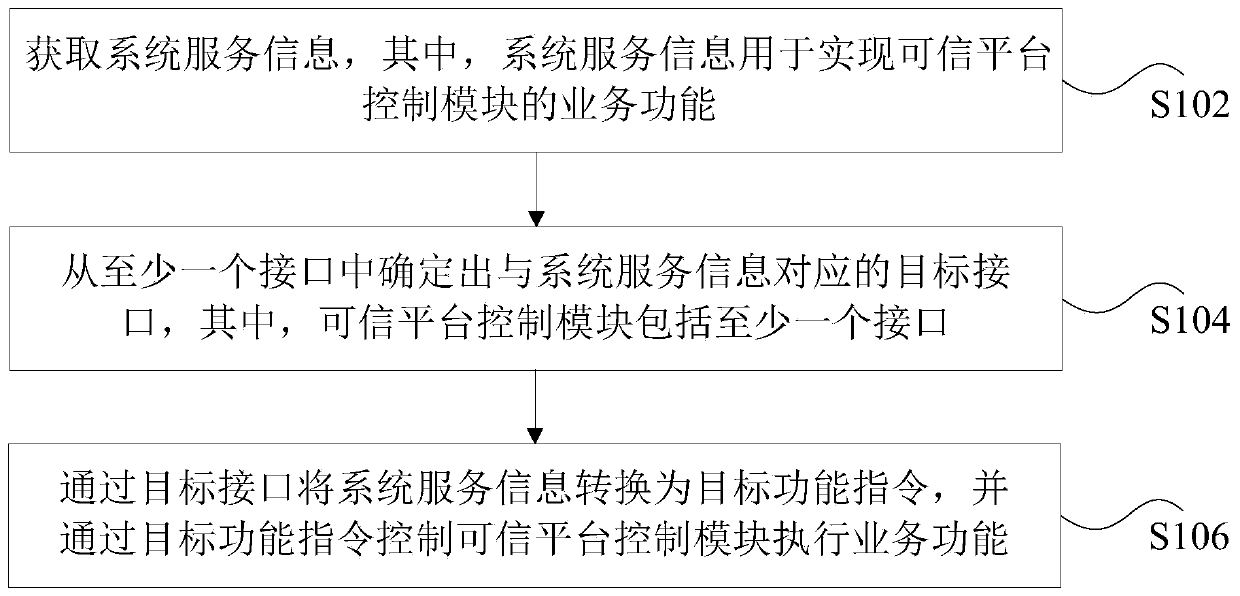
Data processing method and device, storage medium and processor
ActiveCN111310192AImprove adaptabilityRealize requirementsPlatform integrity maintainanceSystem serviceService information
The invention discloses a data processing method and device, a storage medium and a processor. The method comprises the steps that system service information is acquired, and the system service information is used for achieving a service function of a trusted platform control module; a target interface corresponding to the system service information is determined from the at least one interface, and the trusted platform control module comprises at least one interface; and converting the system service information into a target function instruction through the target interface, and controllingthe trusted platform control module to execute a service function through the target function instruction. According to the invention, the technical problem of low adaptability of the trusted platformcontrol module is solved.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
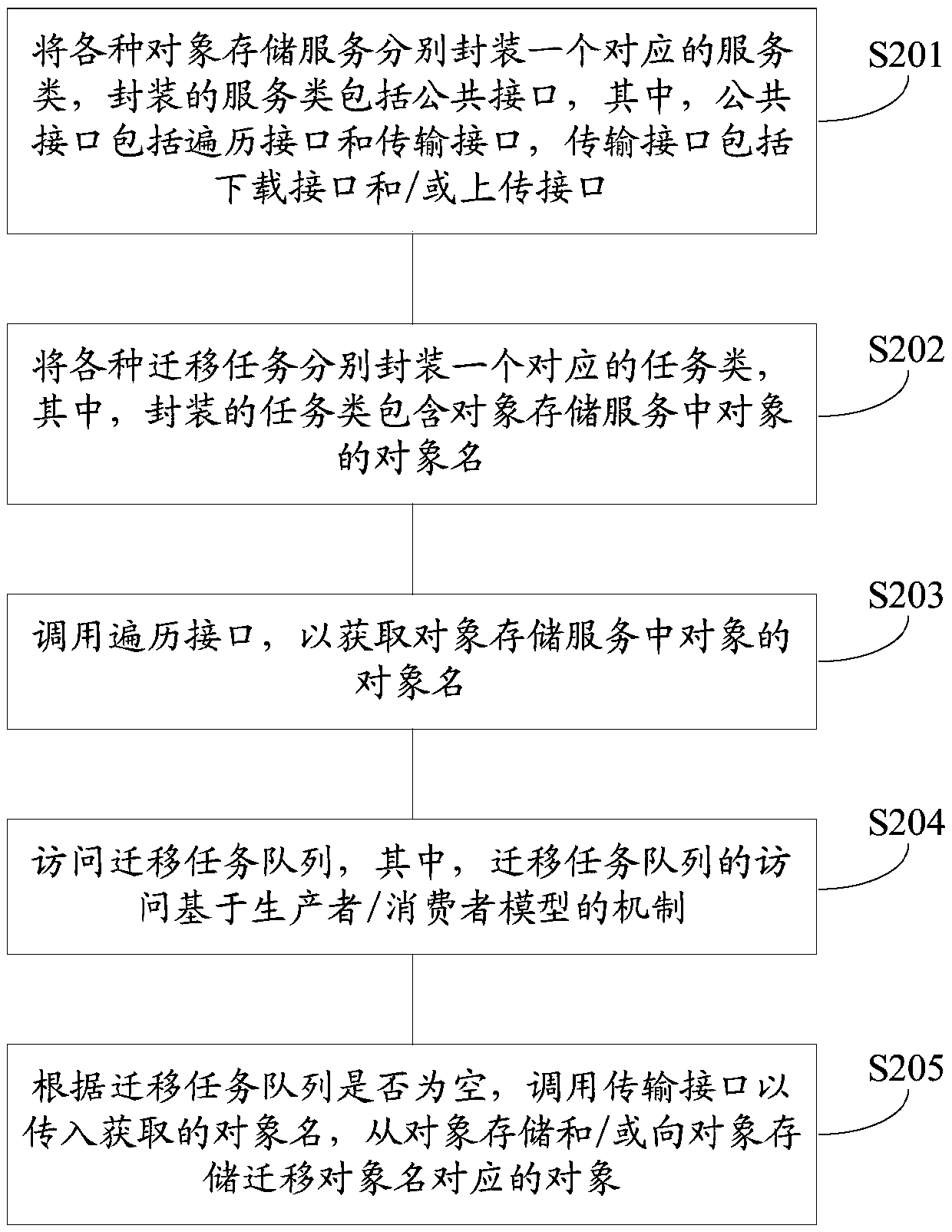
Method and device for migrating object storage and computer readable storage medium
ActiveCN110209344ARealize multiplexingLow costInput/output to record carriersPublic interfaceCloud storage
The invention belongs to the field of cloud storage / computing, and discloses a method and a device for migrating object storage and a computer readable storage medium, so as to reduce various costs when an object storage service is migrated. The method comprises the steps that various object storage services are respectively packaged with a corresponding service class, the packaged service class comprises a common interface, and various migration tasks are respectively packaged with a corresponding task class; a traversal interface is called to obtain an object name; a migration task queue isaccessed; and a transmission interface is called to input the acquired object name according to whether the migration task queue is empty or not, and the object corresponding to the migration object name is stored from the object storage and / or to the object storage. According to the technical scheme provided by the invention, on one hand, reuse of codes during development of a migration tool is realized to the greatest extent, so that the development cost is greatly reduced; and on the other hand, the cost of learning and using a migration tool by the user is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
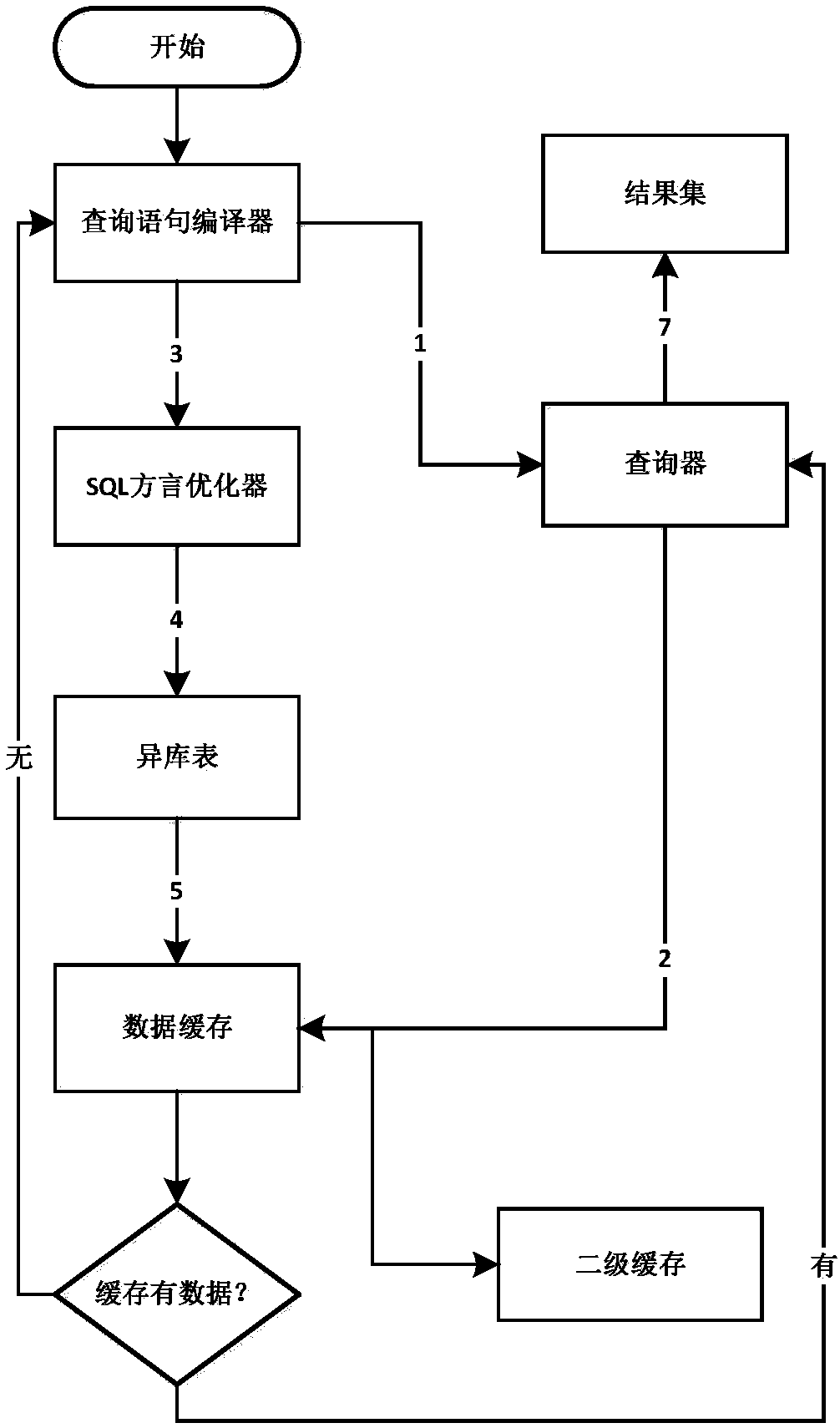
System of multi-table cross-database joint-query and realization method thereof
ActiveCN107609091AImprove execution efficiencyEasy to useStructured data retrievalSpecial data processing applicationsResult setData query
The invention relates to the field of computer application technology, and particularly to a system of multi-table cross-database joint-querying and a realization method thereof. The system comprisesa compiler, an SQL dialect optimizer, a data cache, a querier and a result set. Statements of querying tables of different databases are separated out through the compiler to form independent databasedialects, an SQL is optimized by the optimizer to improve execution efficiency thereof, finally, SQL statements are executed to respectively query the tables of the different databases, obtained query results are stored in the data cache, and finally, the query statements are executed by the querier to obtain the desired result set. Difference of the databases is masked in a whole process of thesystem, and the whole process is transparent for upper-layer operations. The system can be used in multi-table cross-database joint-data-querying of the databases.
Owner:G CLOUD TECH
Method for managing and controlling data transmission based on optical fibre
The invention relates to a method for transmitting manage control data, based on optical fiber, which comprises: the near node packs the optical fiber device into independent Ethernet device, to distribute one mac address and an IP address; the remote node packs the optical fiber devices that connecting superior and lower optical fiber devices into one Ethernet device, to only distribute one mac address and one IP address; sending the mac data pack of IP layer; receiving the data of optical fiber. With said invention, there is full-IP connection between near and remote nodes, to use mature TCP / IP protocol, with simple setting of static route and easy automatic program, while part route relation is processed at the IP device driving layer, to reduced the needed resource.
Owner:HAIAN HENGYI SLIDING BEARING
Method of increasing business objects in cloud computing environment
The invention discloses a method of increasing business objects in a cloud computing environment. The method comprises that the common properties of increased business objects are converted to the common parameters of bottom layer resources, and the specific properties of increased business objects are converted to the specific parameters of the bottom layer resources. According to the method of increasing business objects in the cloud computing environment, the method of increasing business objects in a cloud computing environment is provided, the problems that a plurality of business objects of a plurality of business systems need unified storage in the cloud computing environment, while object-oriented business objects are needed on an upper layer are solved. The method of increasing business objects in the cloud computing environment achieves the conversion between the bottom layer resources and upper layer business objects, and the otherness of different business objects is shielded. When the business objects change, only the upper layer business objects need to be modified, the bottom layer storage and interfaces can not be affected, and good expansibility of a system is guaranteed.
Owner:新疆中科曙光云计算有限公司
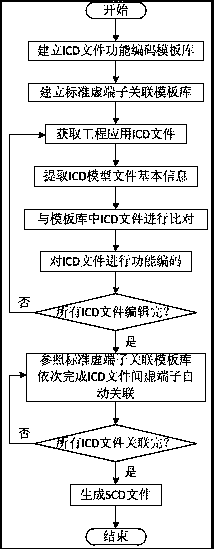
Intelligent substation virtual terminal automatic association method based on standard function coding
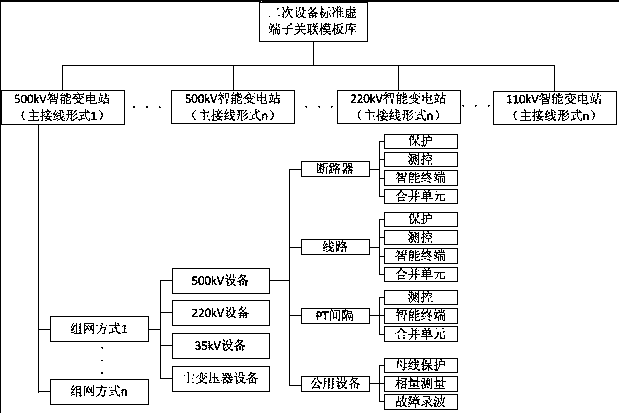
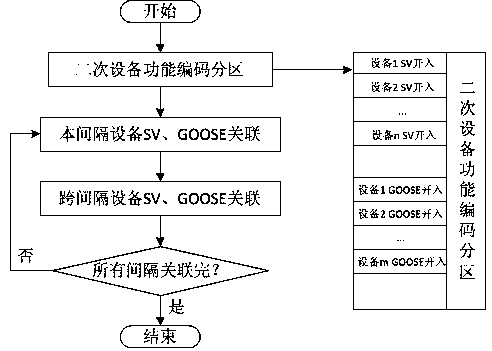
ActiveCN107563031AAvoid the problem of unifying definitionsSimplified quantitySpecial data processing applicationsVirtual terminalSmart substation
The present invention relates to an intelligent substation virtual terminal association method, in particular to an intelligent terminal substation virtual terminal automatic association method basedon the standard function coding. The method comprises the following steps that: 1) an ICD file function coding template library is established, and function coding is carried out on the device virtualterminal; 2) a standard virtual terminal template library is established; 3) the ICD file in the project is corresponded to the function coding template library to implement automatic coding; and 4)the automatically encoded virtual terminal carries out automatic association according to the standard virtual terminal template library, and the required SCD file output application is finally formed. The method disclosed by the present invention has the advantages that: the virtual terminal marking method taking the secondary system function loop as the core can effectively avoid the problem that the definitions of the virtual terminals in various domestic manufacturers are difficult to be unified, and the function coding shields the difference between virtual terminals of different manufacturers, so that the match rate of the automatic coding and the success rate of the automatic association can be significantly enhanced.
Owner:POWERCHINA FUJIAN ELECTRIC POWER SURVEY & DESIGN INST CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com