Network topology construction method and device
A network topology and network technology, applied in the field of network security, can solve the problems of high consumption, inability to guarantee security, inability to obtain configuration information such as device interfaces and routes, and achieve the effect of shielding differences and low cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
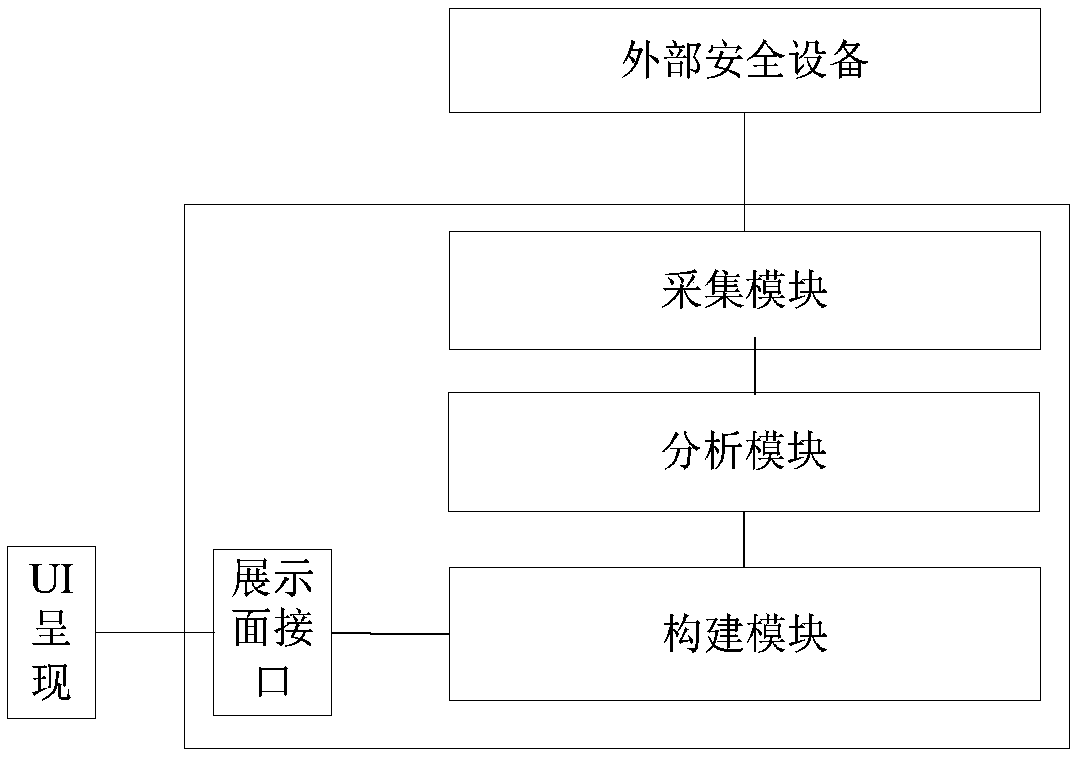
[0109] According to different triggering methods, the collection of configuration information of specified devices in the network can be divided into active trigger configuration collection, scheduled task trigger configuration collection, and log server trigger network topology system configuration collection.
[0110] 1. By selecting an online connectable device, manually trigger online collection, click the configuration collection button to collect the latest information; or manually trigger offline collection, upload a configuration file to update the configuration information of an offline non-connectable device, and actively collect and update configuration information;
[0111] 2. Set the timing task configuration module in the system, such as Figure 8 As shown, the configuration information of the security device can be collected by configuring the timing task cycle to trigger the acquisition sub-module, for example, the configuration information can be collected duri...
Embodiment 2
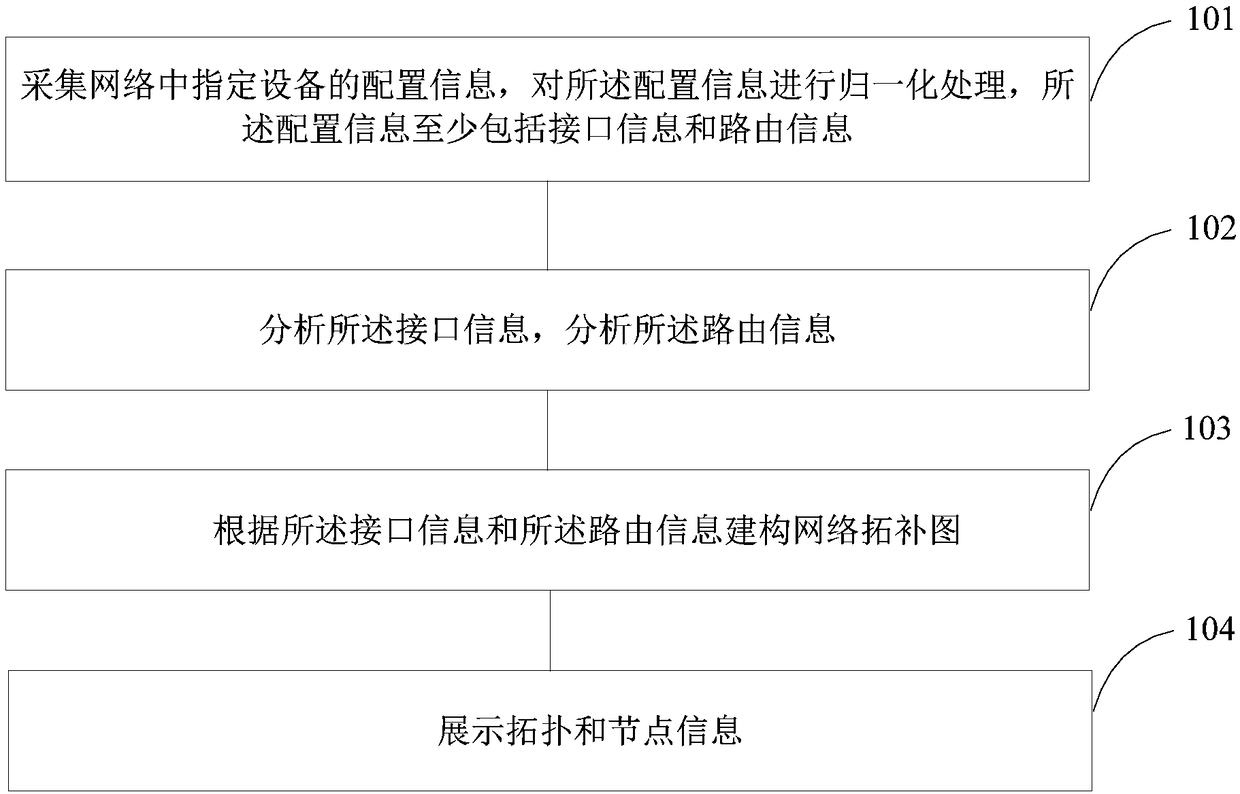
[0114] In this embodiment, analyze the interface information of the device, filter invalid interface information, and determine which interfaces are activated and available, such as Figure 9 As shown, the specific steps are as follows:
[0115] Step 801, traversing the latest configuration of the external security device to collect normalized interface information;
[0116] Step 802, extracting the interface configuration and interface hardware status to obtain a list of all interface information, and judging which interfaces are not operating normally according to the link status of the interface hardware status;
[0117] Step 803, extracting routing information, traversing all routing information;
[0118] Step 804, according to the interface fields in the direct route and the destination route, judge whether the interface is used, if the interface is not used, then turn to step 805, when the interface is not in normal operation and there is an interface through which the ...
Embodiment 3
[0124] This embodiment describes that when the destination of a certain direct route is a public IP address (segment), it is determined that the network connected to the corresponding interface is an external network (Internet). For example: the firewall information of device 1620 has been configured, and the topology map is initialized, and the device node is generated:
[0125] ,
[0126] After collecting the configuration information, obtain the interface information (including the specific information of the interface eth0 / 1.0), routing information, and the direct connection routing information is as follows:
[0127] Type Network Address Path Length Path Cost Gateway Interface
[0128] Direct connection 158.123.18.56 0 0 158.123.18.1eth0 / 1.0
[0129] The network address of this directly connected route is a public IP address (segment), and in the embodiment of the present invention, the public IP address (segment) is regarded as an external network (Internet), which w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com