Identity authentication method and identity authentication system
An identity authentication and authenticator technology, applied in the field of identity authentication methods and identity authentication systems, can solve the problems of lack of security protection mechanism, difficult application of cryptography, and difficulty in multi-platform compatibility, so as to improve the abnormal risk processing mechanism, The effect of reducing the difficulty of integration and deployment and improving the security protection mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] Embodiment 1. Taking fingerprint verification as an example to illustrate the identity authentication method
[0045] 1. The user activates the certificate function, the steps are as follows:
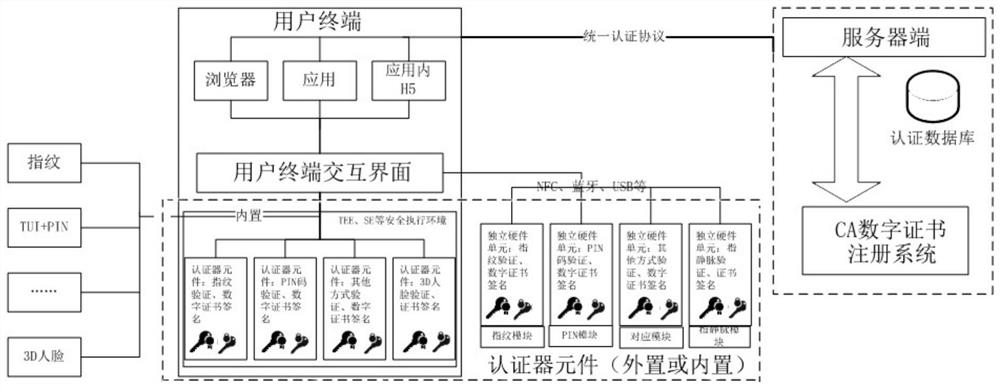
[0046] Precondition: The user has enabled the fingerprint verification function on the user terminal, that is, the terminal device has the function of the authenticator component to collect, store and match fingerprints, and the user can already use the fingerprint to log in to the terminal device (unlock).
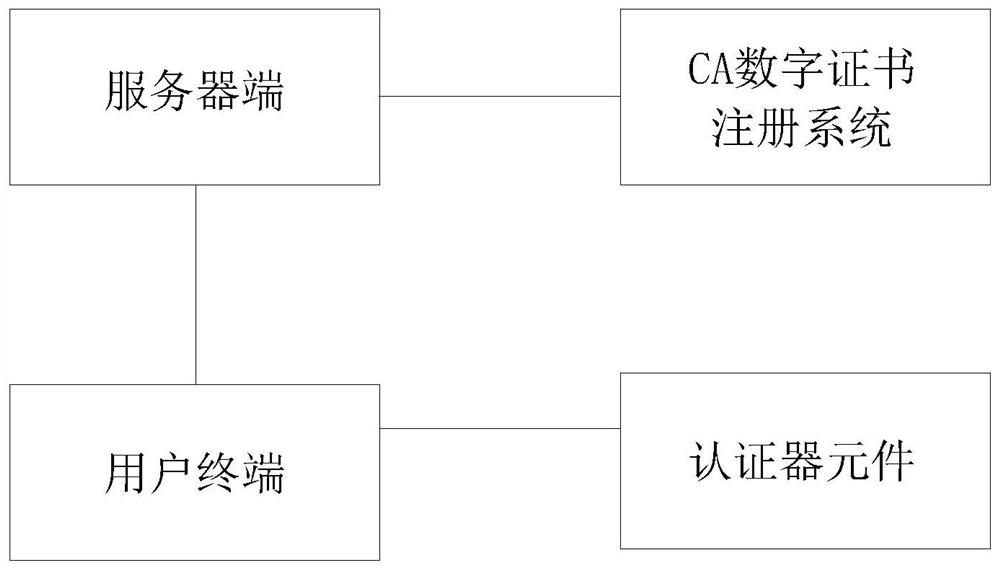
[0047] (1) After the user creates a user name and completes the necessary identity verification, the server sends a registration request message to the user terminal, including user ID, random number, security policy, etc.
[0048] (2) After the user performs corresponding security verification on the registration request message received by the user terminal, the user terminal then sends an instruction to the authenticator component (or independent hardware unit) to require...
Embodiment 2
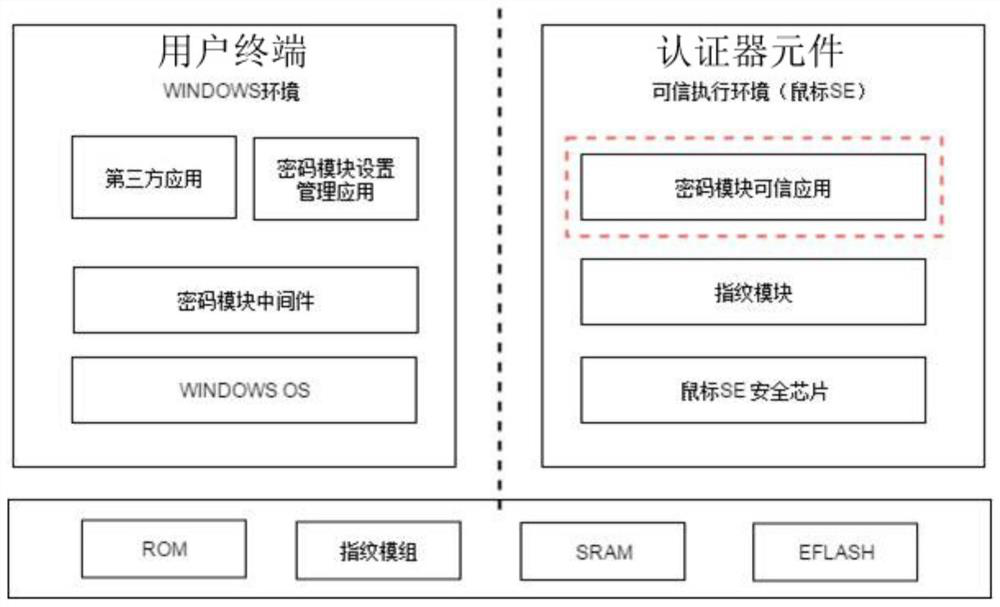
[0072] Embodiment 2, fingerprint mouse FIDO combined with PKI certificate for authentication
[0073] Explanation of terms:
[0074] PKI: An infrastructure system that supports public key management and can support authentication, encryption, integrity, and accountability services.
[0075] FIDO: Fast Identity Online, an online fast identity verification alliance, provides a completely open FIDO unified authentication protocol.
[0076] COS: The execution program written in the mouse security chip, in this example, includes fingerprint, FID authenticator and PKI related content.
[0077] Most of the current PC-side login, application login, and application transaction processing are still processed by PIN codes. With the popularization of biometric devices, biometric devices such as fingerprint KEY and binocular cameras have emerged. Biometric devices have Quick authentication, without password, allows users to quickly log in and authenticate through biometric features such ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com