Authentication method and device for subscriber identity module card
A customer identification module and authentication technology, applied in the field of biometric identification, can solve the problem of counterfeiting users, and achieve the effect of avoiding theft, ensuring the security of the authentication process, and improving the security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] The embodiment of the present invention provides an authentication method of a customer identification module card, which is applied to the card writer side of setting SIM card information, such as figure 1 As shown, the processing flow of the method of this embodiment includes the following steps:
[0053] Step 101. Collect biometric information of a user, and extract biometric details from the biometric information.
[0054] When a user signs a SIM card, the card writer needs to first collect some biological features of the user to obtain the user's biological feature information, and then extract the details of the biometric features from the biological feature information. The minutiae of the biological feature can uniquely identify the biological feature information.
[0055] For example, the fingerprint information of the user can be collected by a fingerprint collector as the biometric information of the user; then the minutiae points of the fingerprint can be e...
Embodiment 2
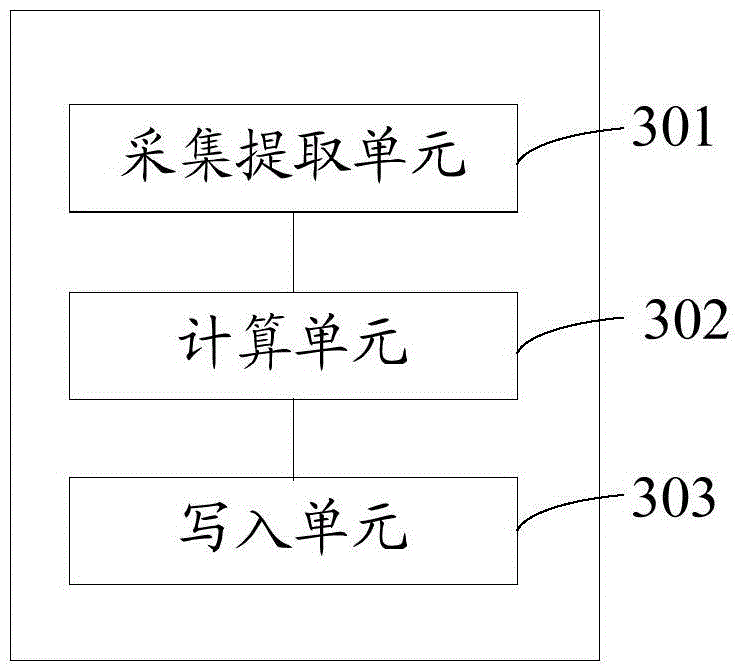
[0093] The embodiment of the present invention provides a card writer, such as image 3 As shown, the card writer includes: a collection and extraction unit 301, a calculation unit 302, and a writing unit 303, wherein,
[0094] The collection and extraction unit 301 is configured to collect and obtain biometric information of the user, and extract minutiae points of biometric characteristics from the biometric information;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com