Pseudo base station recognition method and terminal
A pseudo base station and base station technology, applied in the field of identification of pseudo base stations, can solve the problems of high cost and missed detection, achieve accurate identification and reduce the cost of implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
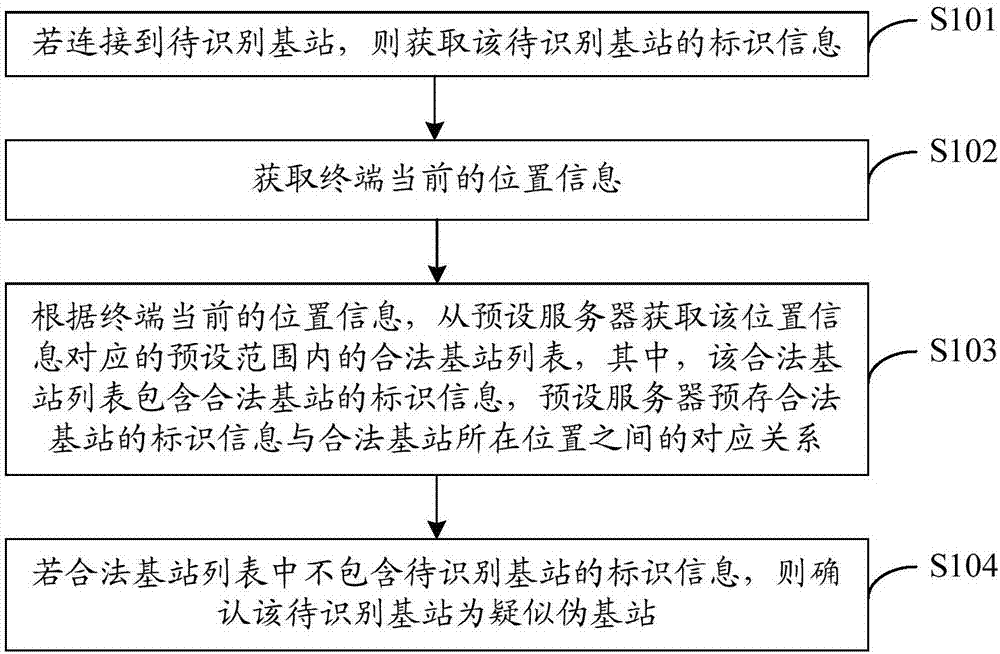
[0033] see figure 1 , figure 1 It is a schematic flow chart of a method for identifying a fake base station provided in Embodiment 1 of the present invention. The execution subject of this embodiment is a terminal, which may be a mobile phone or other smart terminal or other equipment. figure 1 The shown method for identifying a false base station may include the following steps:
[0034] S101. If connected to a base station to be identified, acquire identification information of the base station to be identified.
[0035] Specifically, the terminal periodically scans the surrounding base station signals, and selects the base station with the strongest signal for connection. If the terminal is connected to the base station to be identified with the strongest current signal, the identification information of the base station to be identified is obtained.
[0036] The identification information is an identification code that uniquely identifies the base station to be identifi...
Embodiment 2
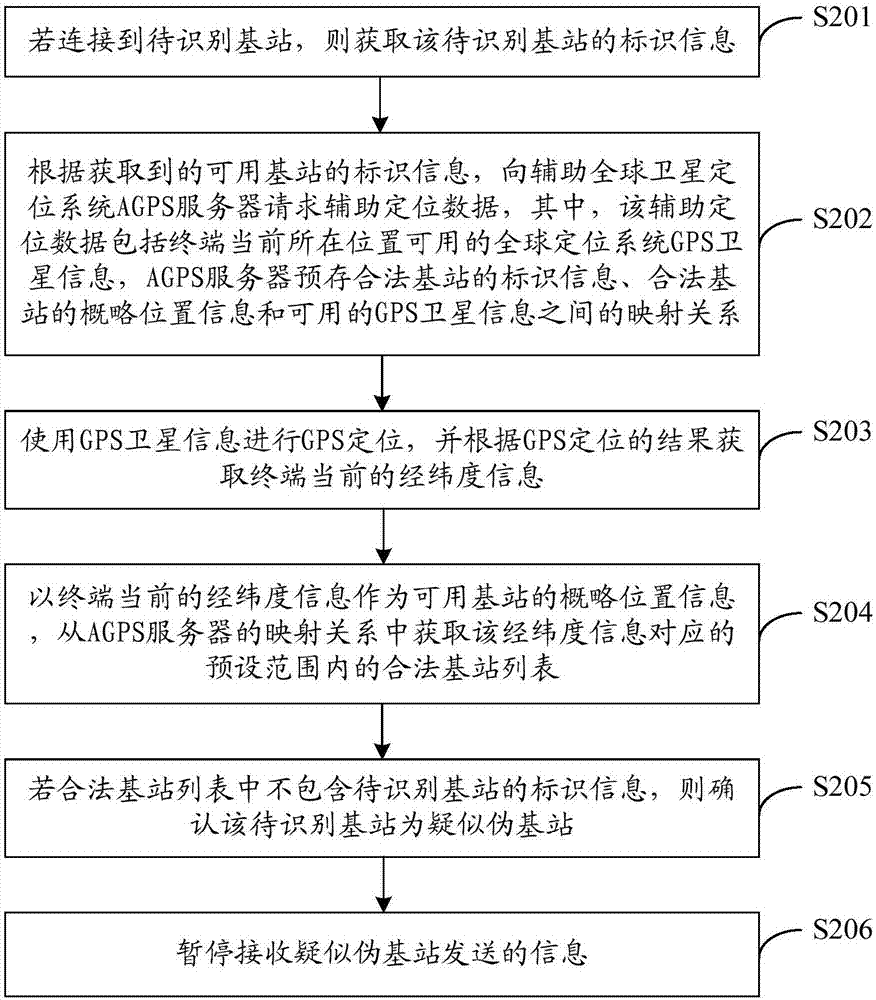
[0050] see figure 2 , figure 2 It is a schematic flow chart of a method for identifying a fake base station provided in Embodiment 2 of the present invention. The execution subject of this embodiment is a terminal, and the terminal may be a mobile phone or other smart terminal or other equipment. figure 2 The shown method for identifying a false base station may include the following steps:
[0051] S201. If connected to a base station to be identified, acquire identification information of the base station to be identified;
[0052] Specifically, the terminal periodically scans the surrounding base station signals, and selects the base station with the strongest signal for connection. If the terminal is connected to the base station to be identified with the strongest current signal, the identification information of the base station to be identified is acquired.
[0053] The identification information is an identification code that uniquely identifies the base station ...
Embodiment 3
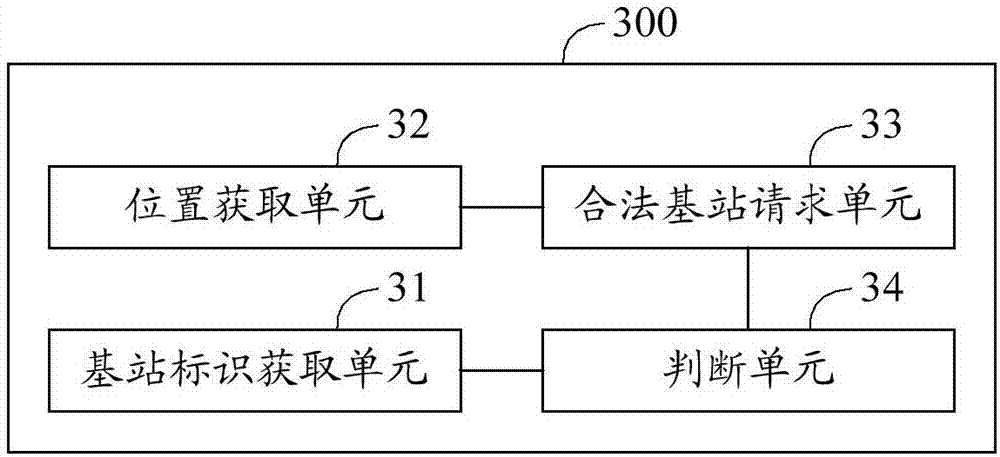
[0089] see image 3 , image 3 It is a schematic block diagram of a terminal provided by Embodiment 3 of the present invention. For ease of description, only parts related to the embodiments of the present invention are shown. image 3 The example terminal 300 may be the subject of execution of the method for identifying a pseudo base station provided in Embodiment 1 above. image 3 The exemplary terminal 300 mainly includes: a base station identification obtaining unit 31 , a location obtaining unit 32 , a legal base station requesting unit 33 and a judging unit 34 . The details of each unit are as follows:
[0090] The base station identification obtaining unit 31 is used for obtaining the identification information of the base station to be identified if connected to the base station to be identified;
[0091] A location acquisition unit 32, configured to acquire current location information of the terminal;
[0092] The legal base station request unit 33 is configured...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com