Method and system for defending ddos attacks
A transfer server and second-level domain name technology, which is applied in a method of defending ddos attacks and its system field, can solve the problems of ddos attack defense, increased costs, limited server bandwidth, etc., and achieves significant defense effects and reduced costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
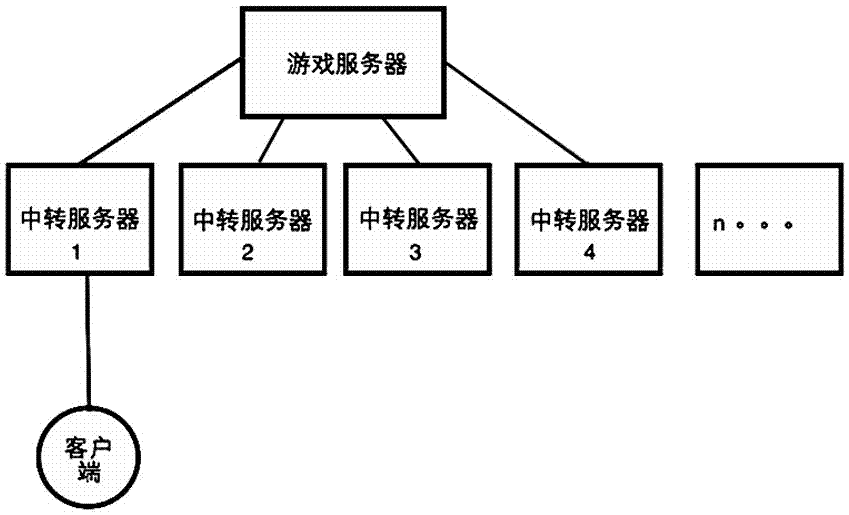
[0018] A kind of method of defense ddos attack of the present invention is characterized in that comprising the following steps:
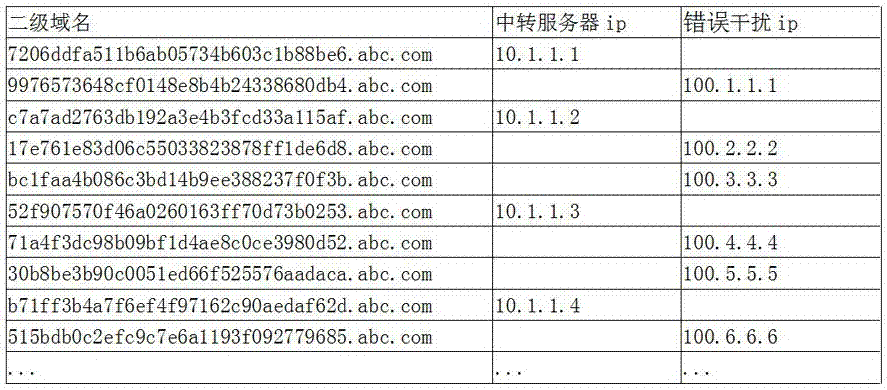
[0019] Step 1: Generate a second-level domain name in a specific sequence, and bind the second-level domain name to b transit server IPs, where a≧b;
[0020] The second-level domain name is generated by seed random number, MD5 or SHA algorithm.
[0021] After b second-level domain names are bound to b transit servers one by one, the remaining a-b second-level domain names are set with wrong interference ip addresses.
[0022] Step 2: The client starts from the nth second-level domain name and visits the transfer server to request services in the specific order of finding the second-level domain name. If it fails, it accesses the next transfer server until the request for service succeeds, where n
[0023] The transit server receives the request from the client, judges the identity information of the client and decides whether to respond to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com