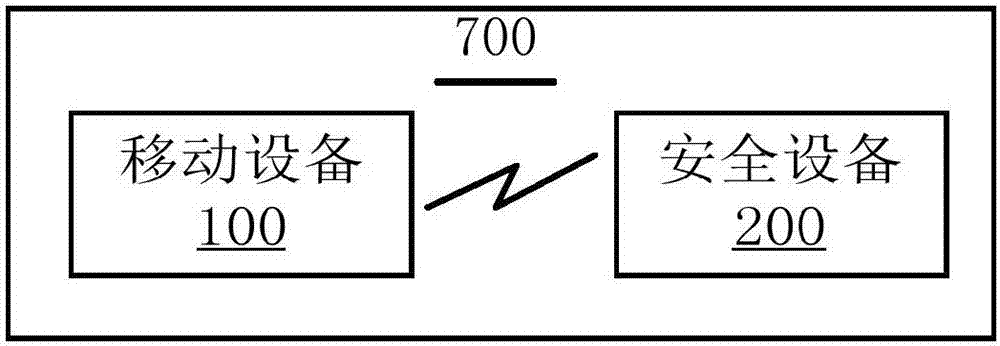
Safety certificate method, device and system
A technology of security authentication and security equipment, applied in digital data authentication, telephone communication, electrical components, etc., can solve the problem that passwords cannot effectively identify information owners, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
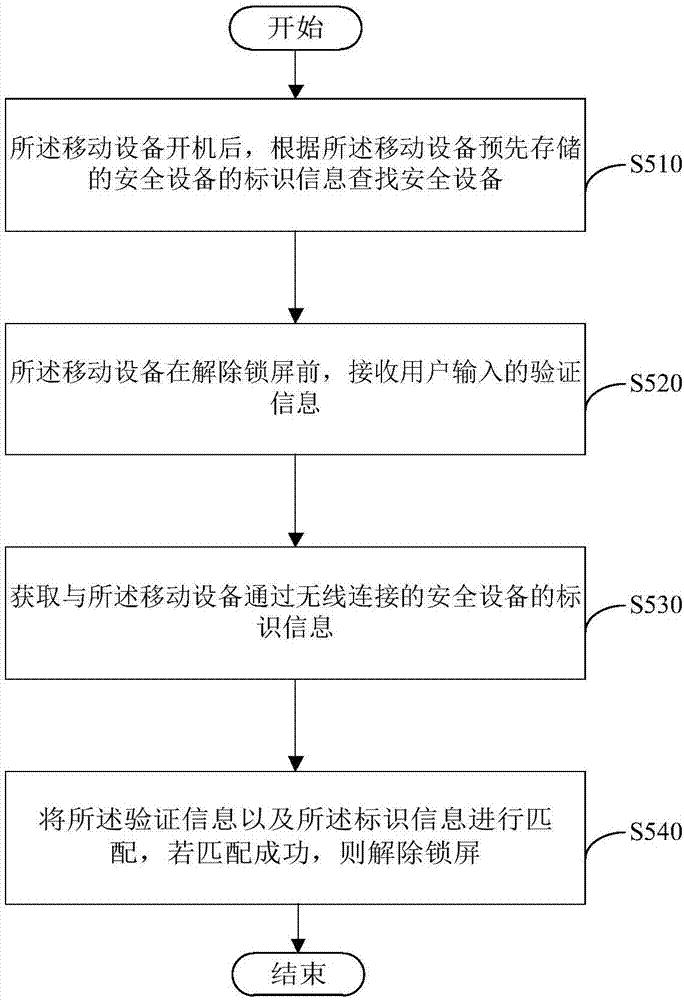
[0032] See image 3, a flow chart of the steps of a security authentication method provided by an embodiment of the present invention, which is applied to a mobile device, and the method includes:
[0033] Step S510, after the mobile device is turned on, search for the security device according to the identification information of the security device stored in advance in the mobile device.
[0034] If a security device corresponding to the stored identification information of the security device is found within a preset time, a wireless connection is performed with the found security device.
[0035] If no security device corresponding to the stored identification information of the security device is found within a preset time, the mobile device enters a screen-locked state.
[0036] The application software pre-stores identification information of the security device and account information bound to the identification information. Wherein, the identification information ma...
Embodiment 2
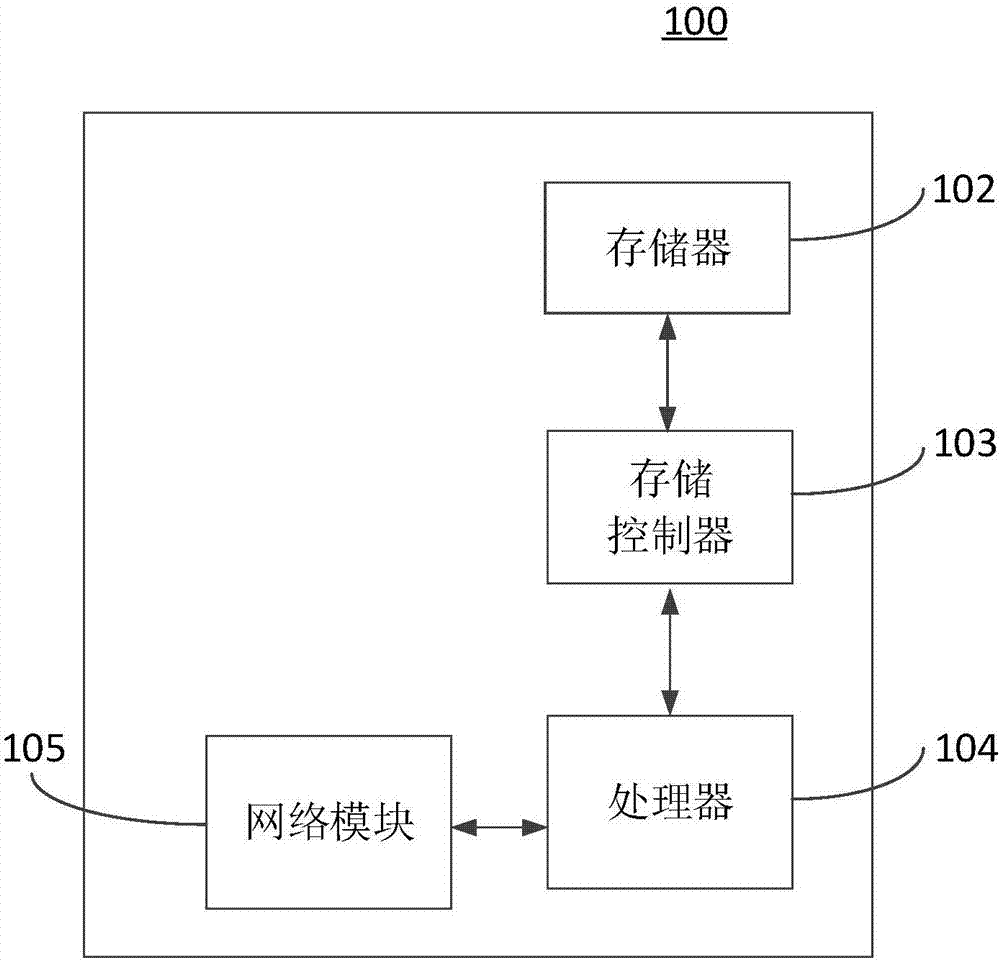
[0068] See Figure 6 , is a structural block diagram of a security authentication device provided by a preferred embodiment of the present invention. The security authentication apparatus 600 is applied to the mobile device 100 . The devices include:
[0069] The first search unit 610 is configured to search for a security device according to the identification information of the security device stored in advance in the mobile device after the mobile device is turned on.
[0070] If a security device corresponding to the stored identification information of the security device is found within a preset time, a wireless connection is performed with the found security device.
[0071] If no security device corresponding to the stored identification information of the security device is found within a preset time, the mobile device enters a screen-locked state.
[0072] The second search unit 611 is configured to find multiple security devices on the mobile device according to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com