M2M communication access control optimizing method for emergency event of LTE network
A technology for emergencies and optimization methods, which is applied in access restrictions, machine-to-machine/machine-type communication services, wireless communication, etc. It can solve the problems of unsmooth and unreliable M2M communication access, and improve latency performance. , high reliability, smooth access effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
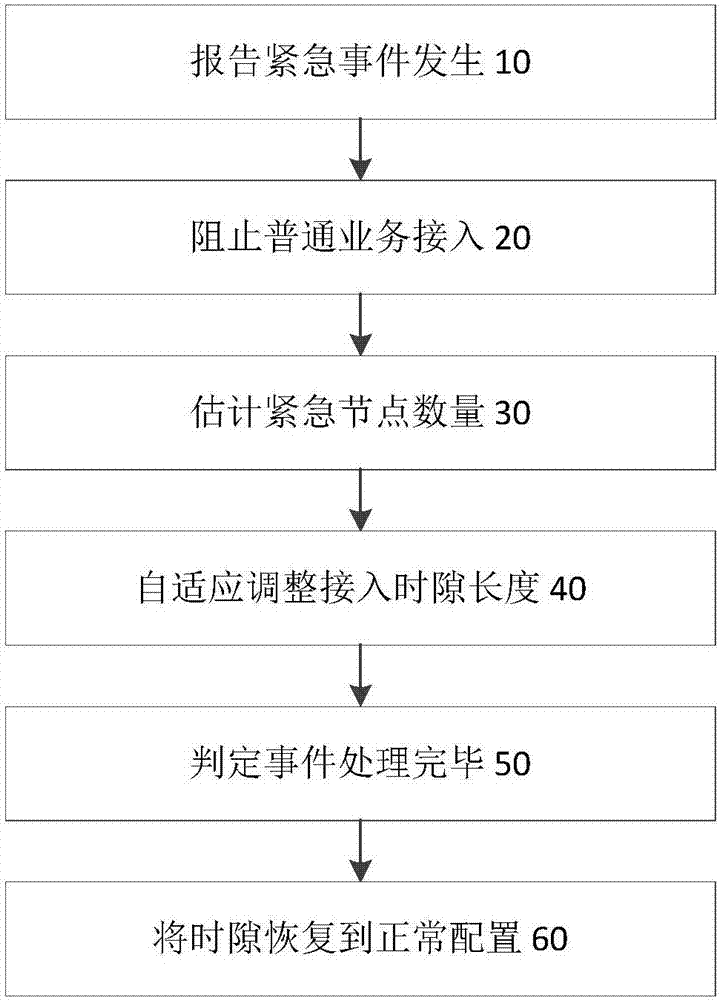
[0027] Such as figure 1 As shown, the present invention responds to the M2M communication access control optimization method of the LTE network emergency, including the following steps:
[0028] (10) Report the occurrence of an emergency: the machine node sends a specific preamble to the base station, the specific preamble is reserved by the base station for an emergency, can only be sent by the machine node, and is used to report the occurrence of an emergency;
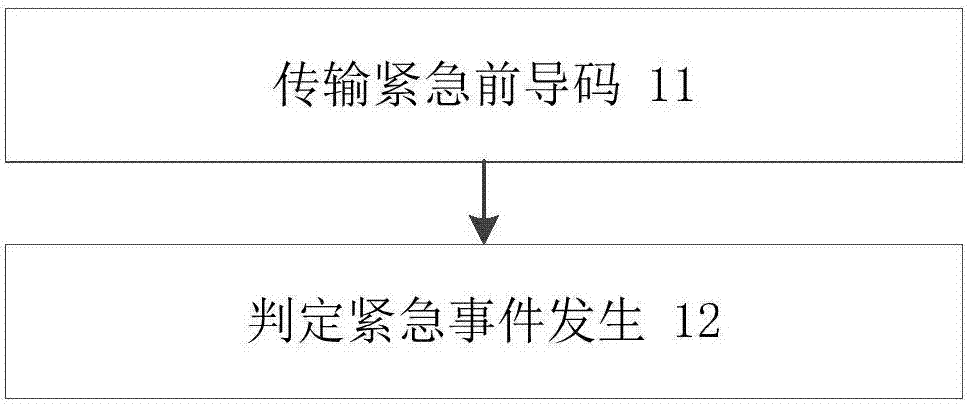
[0029] Such as figure 2 As shown, the (10) reporting emergency occurrence steps include:
[0030] (11) Transmission of emergency preamble: After an emergency event occurs, the emergency node transmits a special emergency preamble to the base station, which is specially reserved by the base station for the emergency node;
[0031] (12) Determine the occurrence of an emergency event: after receiving the emergency preamble, the base station determines that an emergency event occurs and prepares to make corresponding ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com