Data operation method and data management server
A data operation and data management technology, applied in the database field, can solve the problems of complex data reading and writing, data not physically isolated, hidden dangers of data security, etc., and achieve the effect of improving data operation efficiency, avoiding rewriting process, and preventing data interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The technical solutions in the embodiments of the present invention will be described below with reference to the drawings in the embodiments of the present invention.
[0044] In order to facilitate the understanding of the embodiments of the present invention, the terms involved in the description of the embodiments of the present invention are firstly introduced:
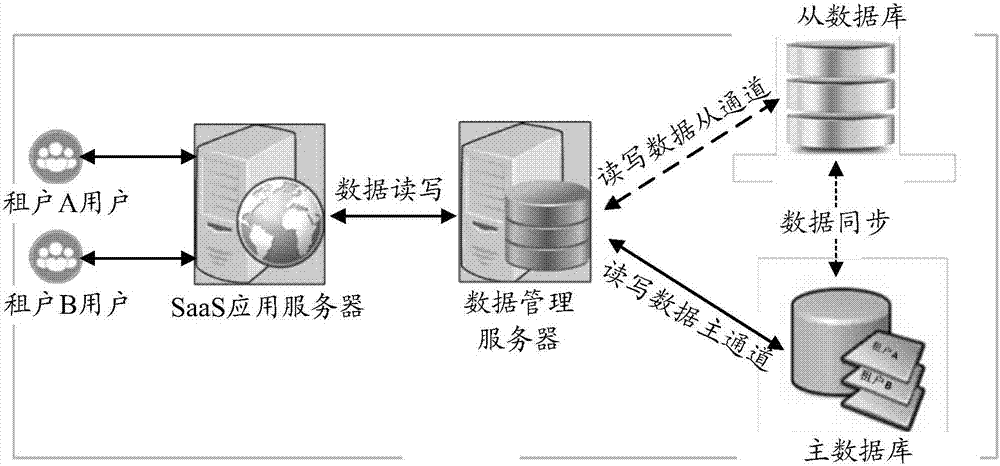
[0045] The metadata of the baseline table (Baseline Table): define the information description of the baseline table, including but not limited to table name, field name (Field Name), field type (Field Type), index, primary key, foreign key, etc.;
[0046] Metadata of custom fields: define the information description of custom fields, including but not limited to field names, field types, indexes, etc.;
[0047] Metadata of the custom table: define the information description of the custom table, including but not limited to table name, field name, field type, index, primary key, foreign key, etc., where t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com